1.清一色胡牌

2.扫描boyaa.com子域名,发现svn源代码泄露
导致整站源代码可下载
在/application/libraries/ByoaaMail.php文件中发现邮箱密码信息
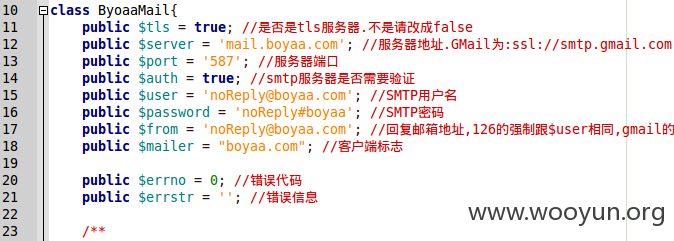
3.登录邮箱
收件箱神马都没有,先拖出通讯簿里所有用户,以便后续渗透
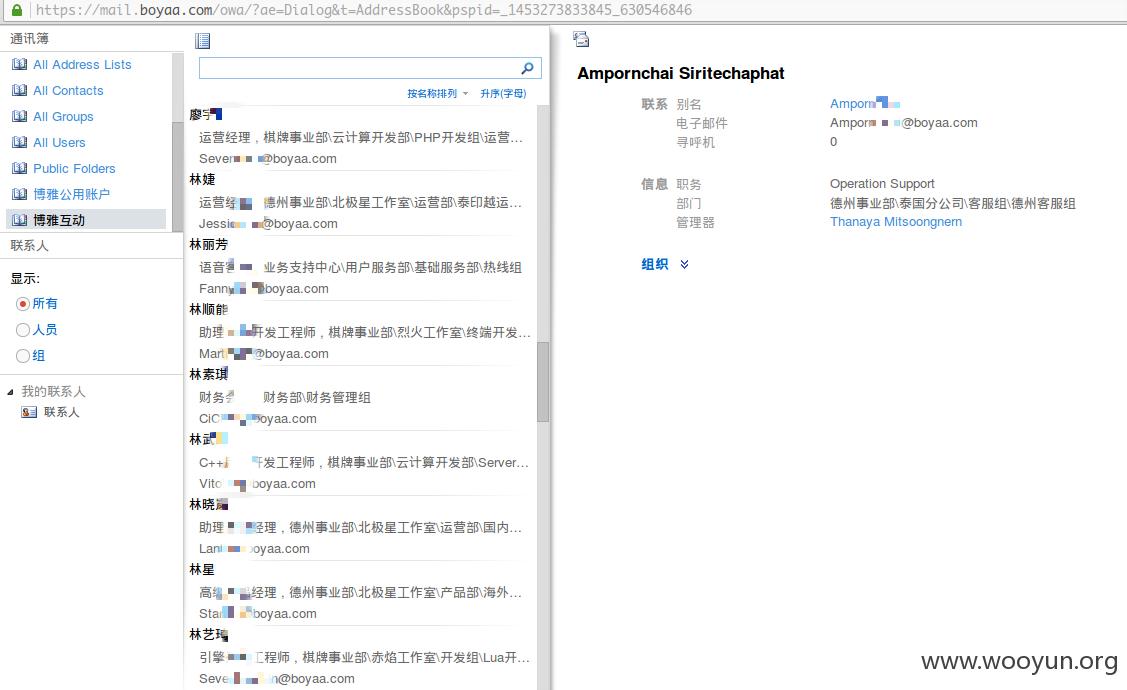
上个星期用拼音字典爆破了一下没有结果,原来贵公司用户名全英文啊,账户体系控制挺严,但是一个svn泄露就可能使内网沦陷
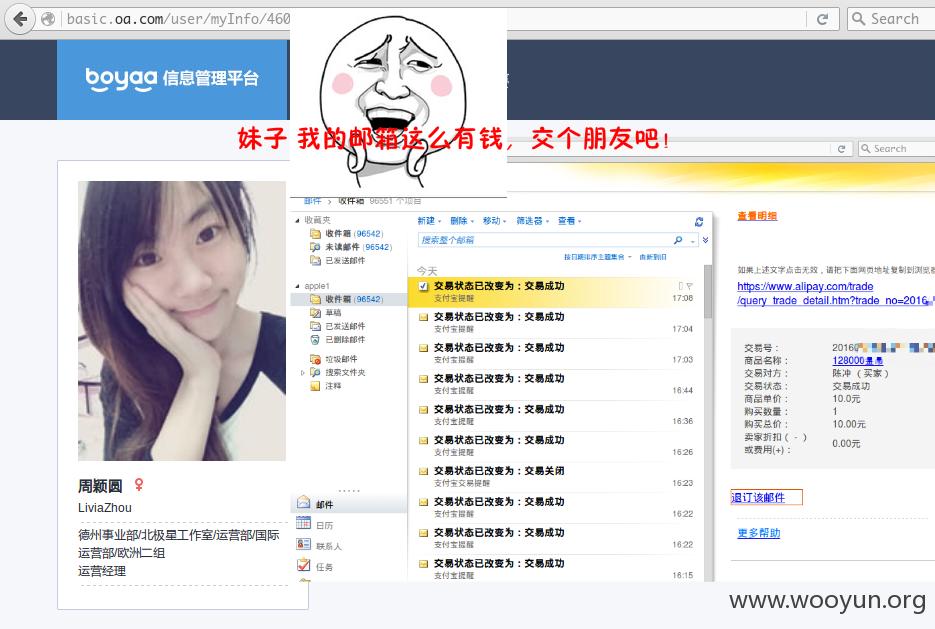
4.利用收集到的英文用户名对邮箱进行精细化fuzzing, 最后只得到一个结果
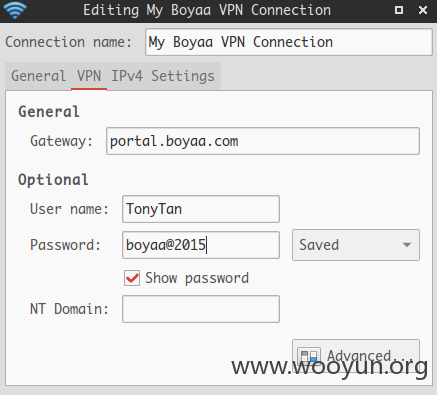
邮箱里面没找到密码信息,只找到vpn登录地址 https://sslvpn.boyaa.com
5.登录vpn,进入内网
oa系统
在个人资料页存在越权
这是我登录的个人信息http://basic.oa.com/user/myInfo/495
修改后面的id就看到了ceo的高清果照 http://basic.oa.com/user/myInfo/1
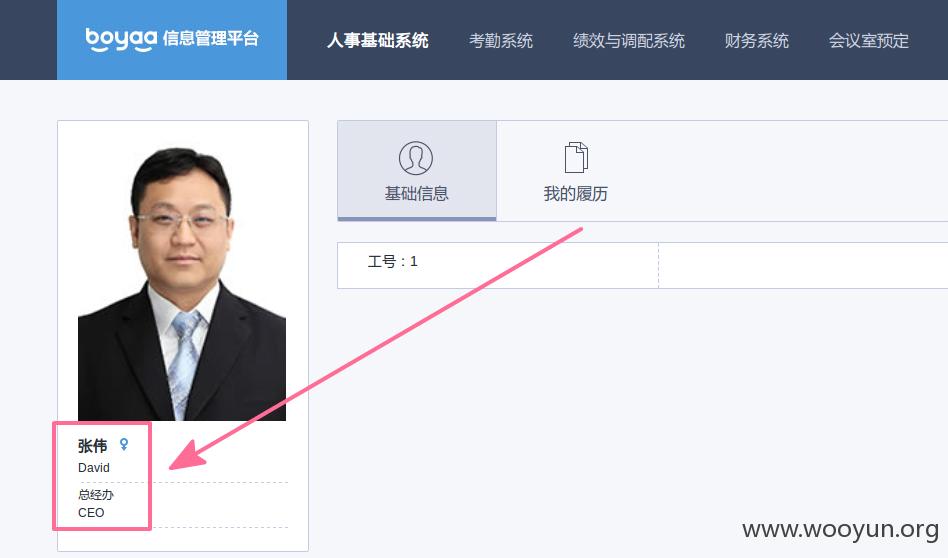
对ceo不感兴趣 然后继续改id,看看有木有漂亮的女汉子,终于找到一个
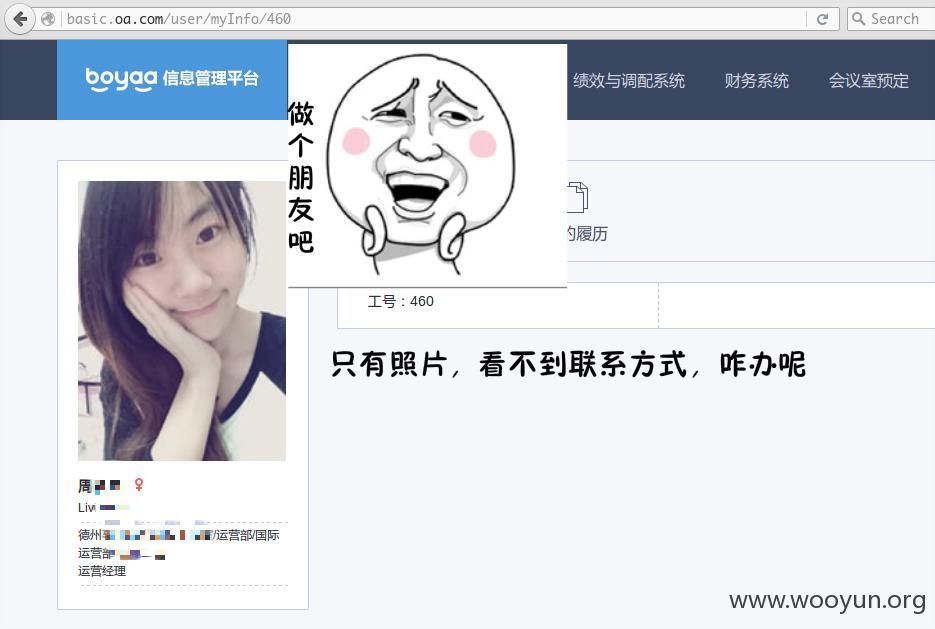
看来oa.com域名只对内网解析,接着使用挖掘机挖出了oa.com的子域名
对子域名进行扫描发现多个注入点,真是呵呵哒~
④单点登录系统存在注入,这就致命了
运维管理系统 http://sa.oa.com
这么多服务器,我一个人岂不累死?对了,这次目的是为了找妹子的联系方式
找啊找,找到一处任意文件上传
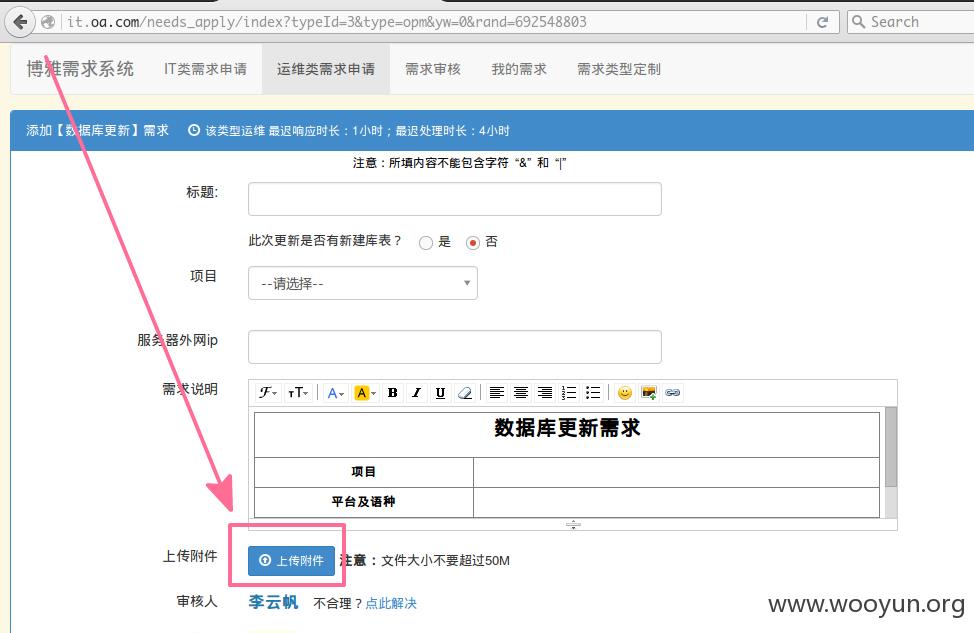
上传附件处传个php上去getshell
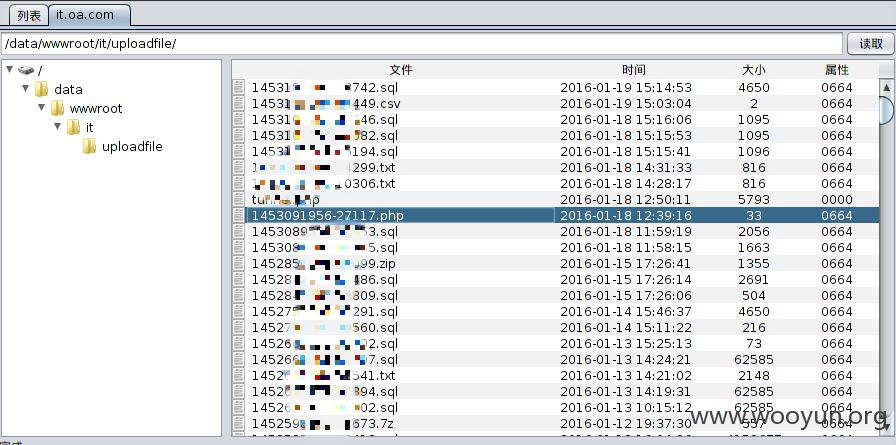
里面好多sql文件,其中这个文件保存有全公司员工的信息
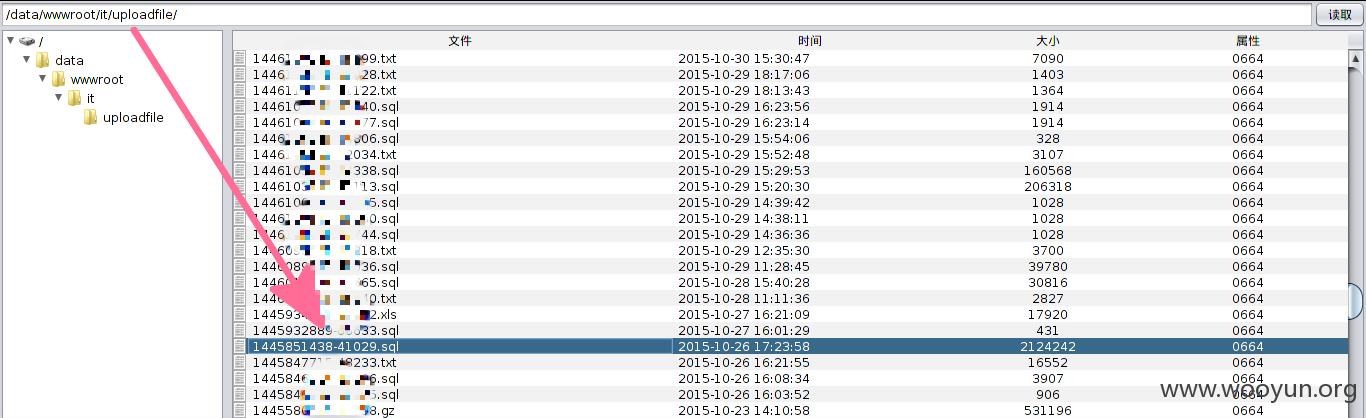
快速定位目标妹子
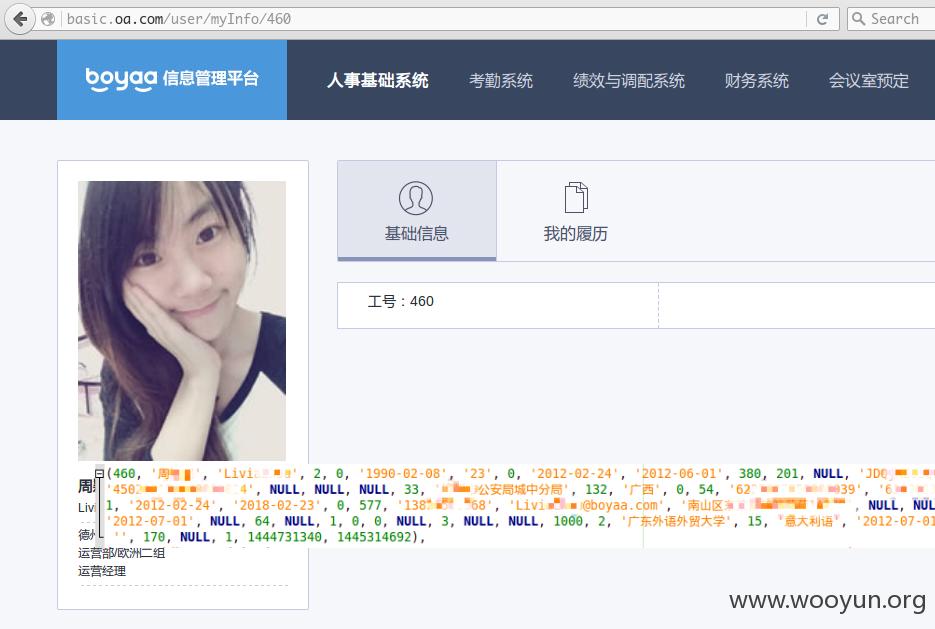
妹子的什么信息都有了,嘿嘿嘿,但是我这么穷,妹子怎么愿意和我做朋友呢?
6.整理出sql文件里面的username和先前邮箱里拖出来的用户名进行 B∪(A∩B)的运算得到总共2000多用户名,再一次对邮箱进行fuzzing得到下面这个账号
这个账号邮箱里面让我找到了贵公司的通用密码
其中
是支付宝绑定邮箱,每时每刻都有¥¥进账