漏洞概要
关注数(24)
关注此漏洞
漏洞标题:辽宁省某电子化学籍管理系统(涉及几百万学生信息/大量考试成绩信息/信息量达到几千万)
提交时间:2016-01-19 09:47
修复时间:2016-03-05 09:52
公开时间:2016-03-05 09:52
漏洞类型:命令执行
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2016-01-19: 细节已通知厂商并且等待厂商处理中
2016-01-22: 厂商已经确认,细节仅向厂商公开
2016-02-01: 细节向核心白帽子及相关领域专家公开
2016-02-11: 细节向普通白帽子公开
2016-02-21: 细节向实习白帽子公开
2016-03-05: 细节向公众公开
简要描述:
详细说明:
**.**.**.**/bin/ 辽宁省电子化学籍管理系统,存在命令执行,通过配置数据库。发现几千万的信息。主要是300W+详细的学生个人信息,还有考试成绩。在测试过程中,由于数据库执行语句的问题,导致宕机了...网站暂时无法访问。
只能出示截图以及学生信息作为证明危害程度。
影响实在巨大,在网站目录备份里有近30G学生照片压缩包。
漏洞证明:
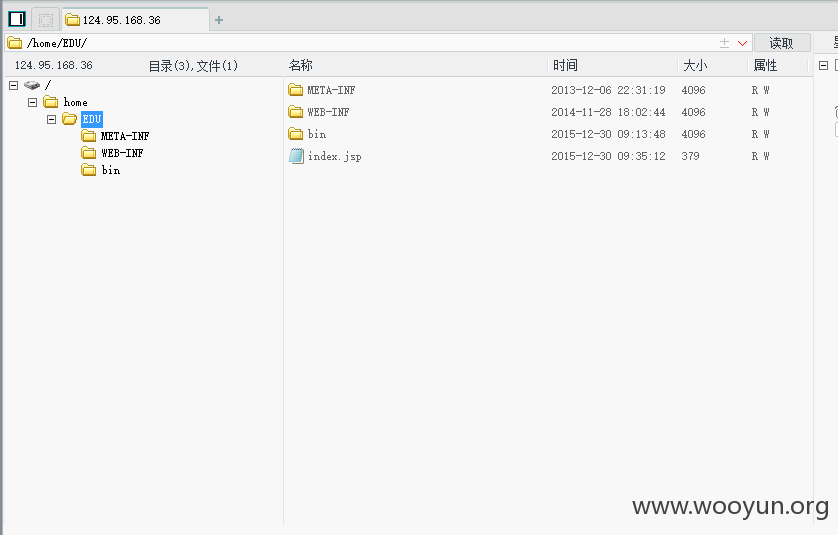
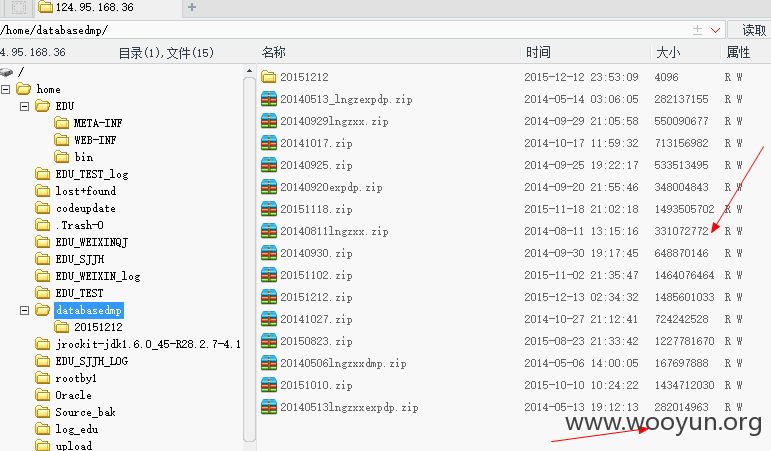
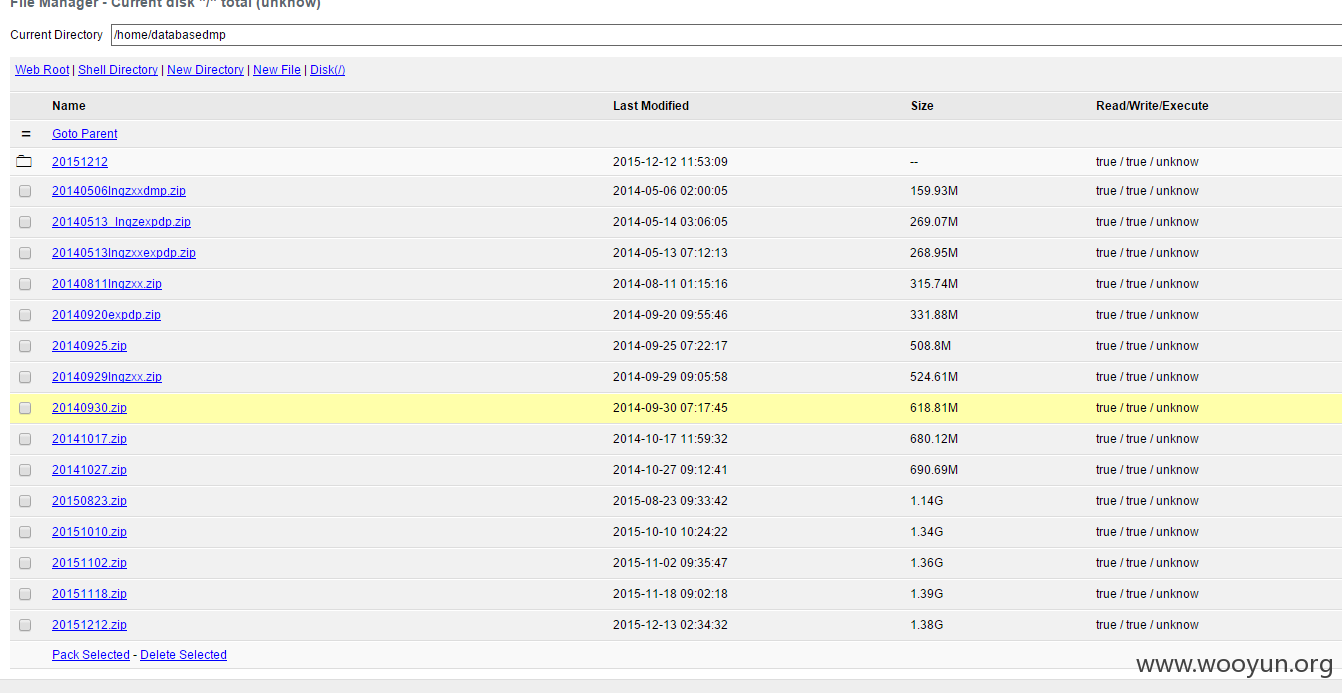
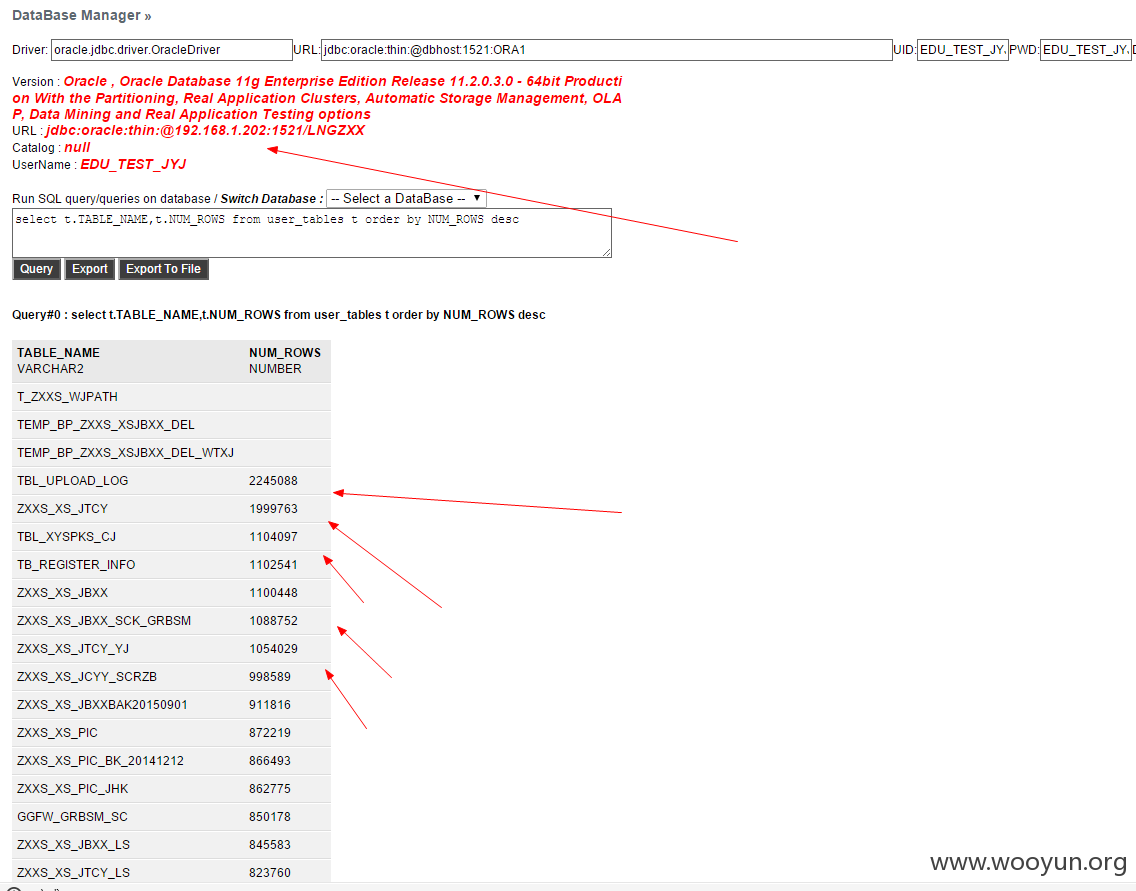
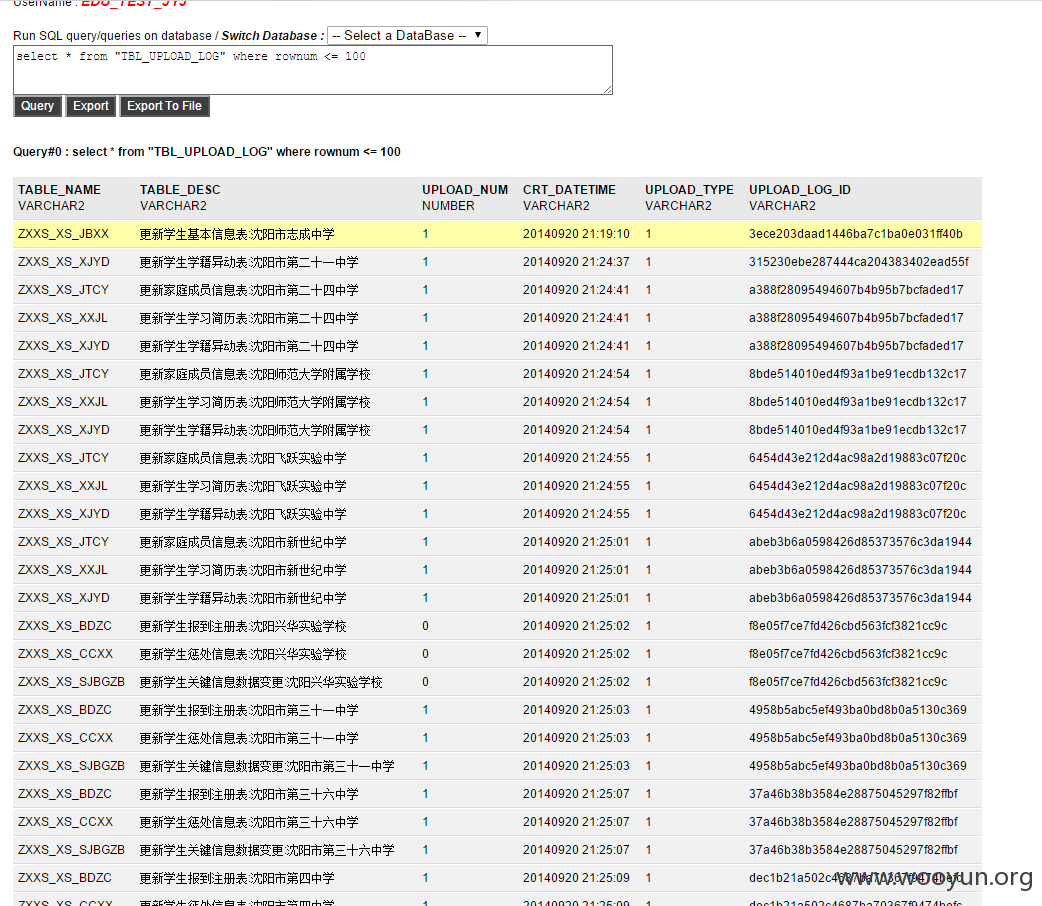
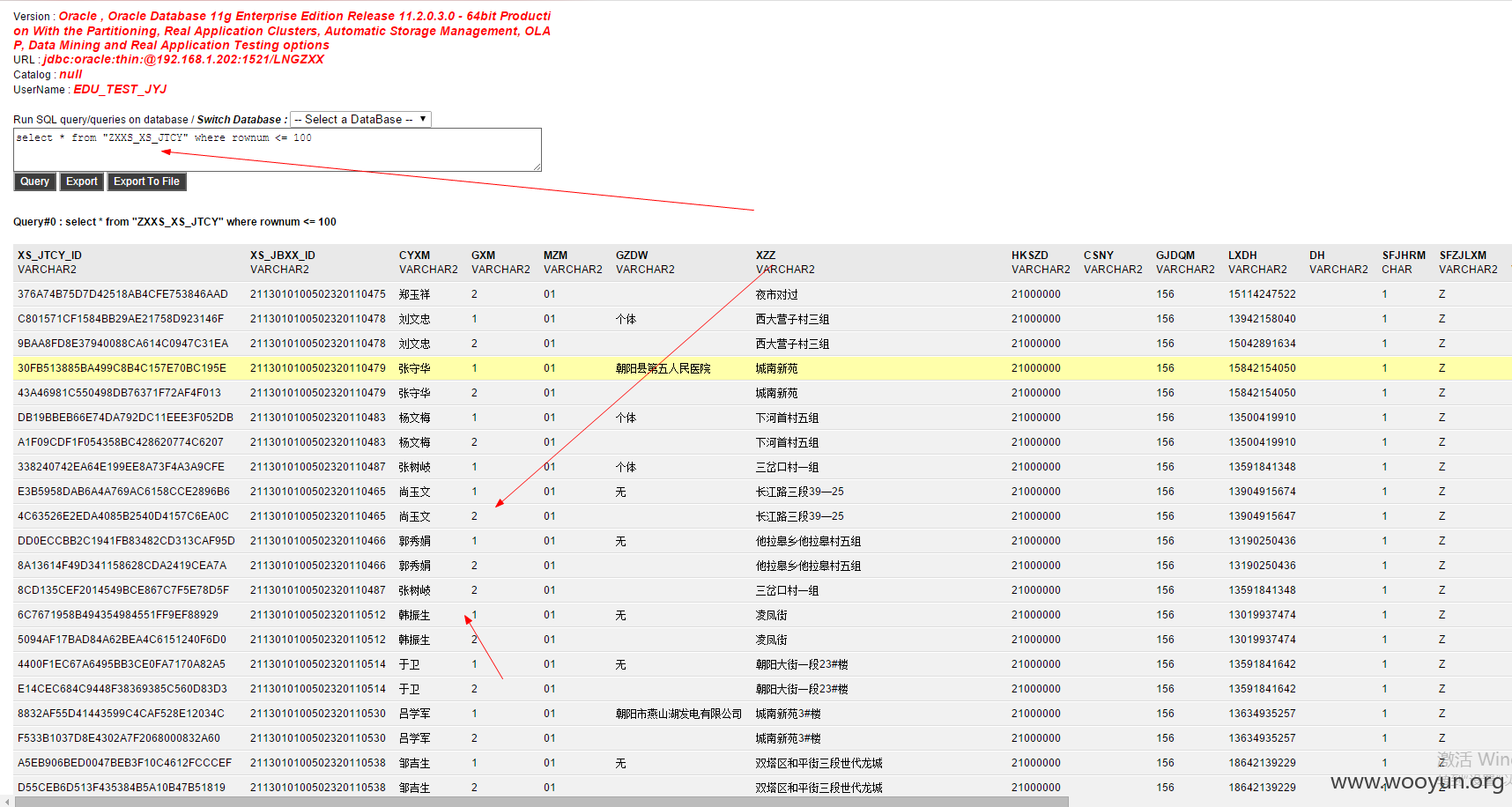
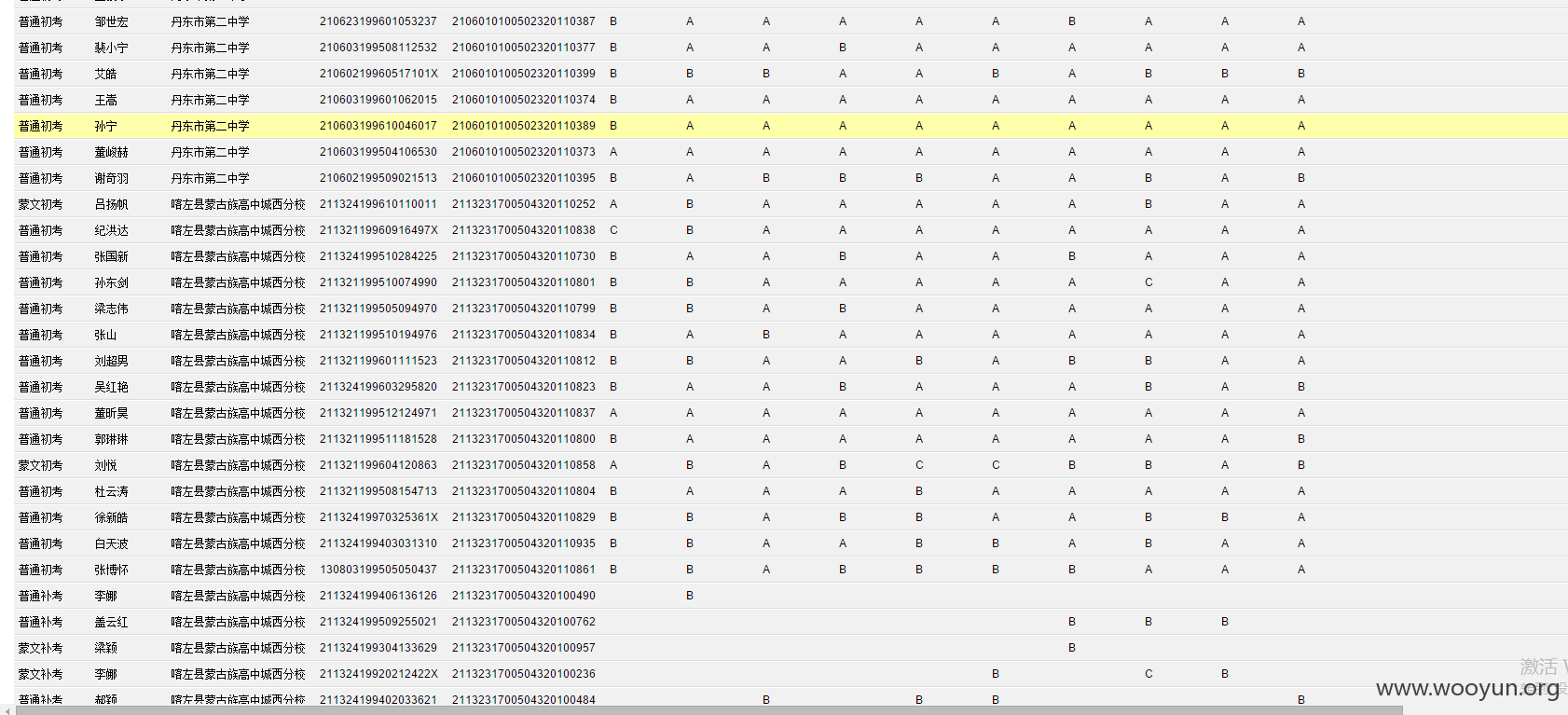
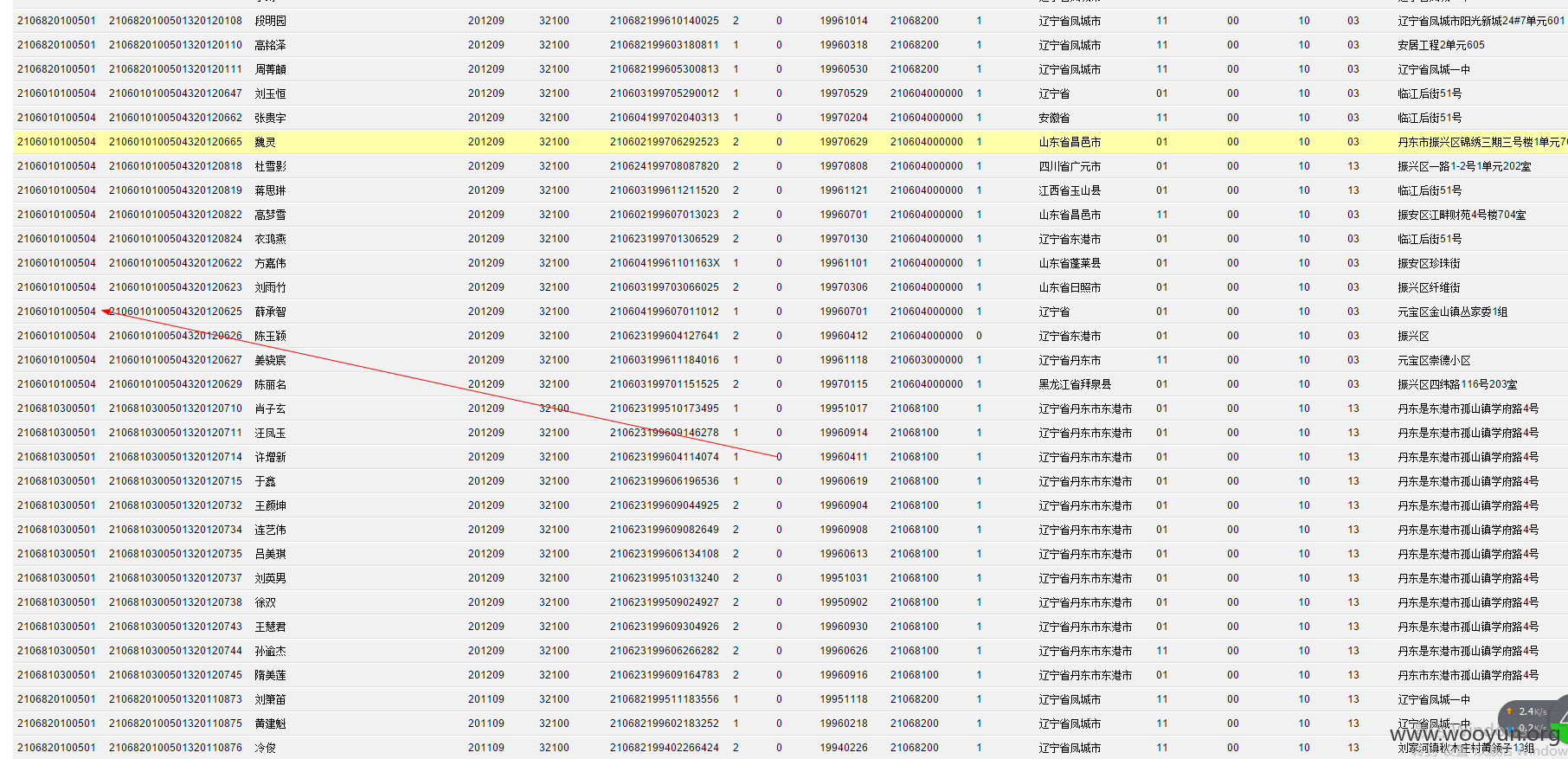
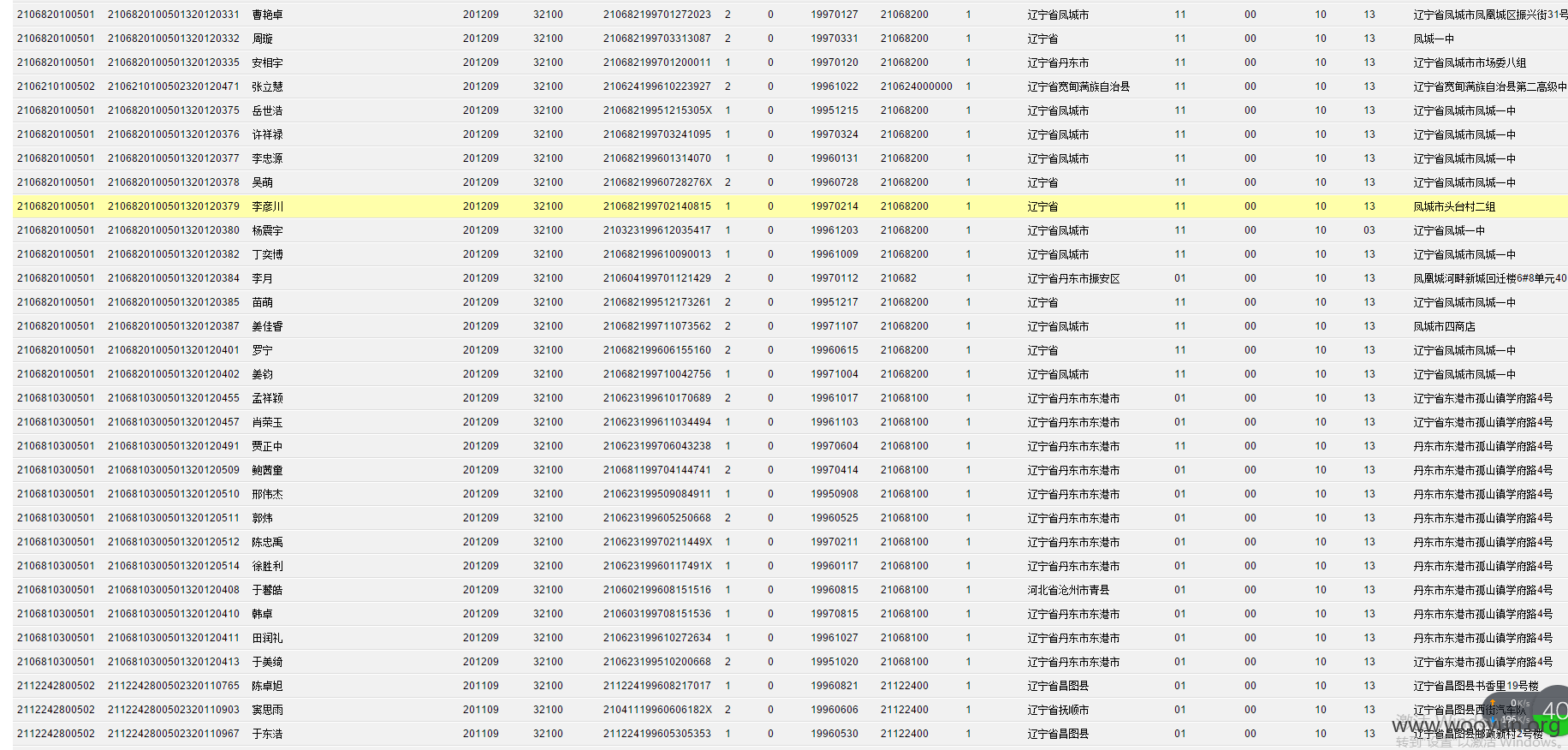
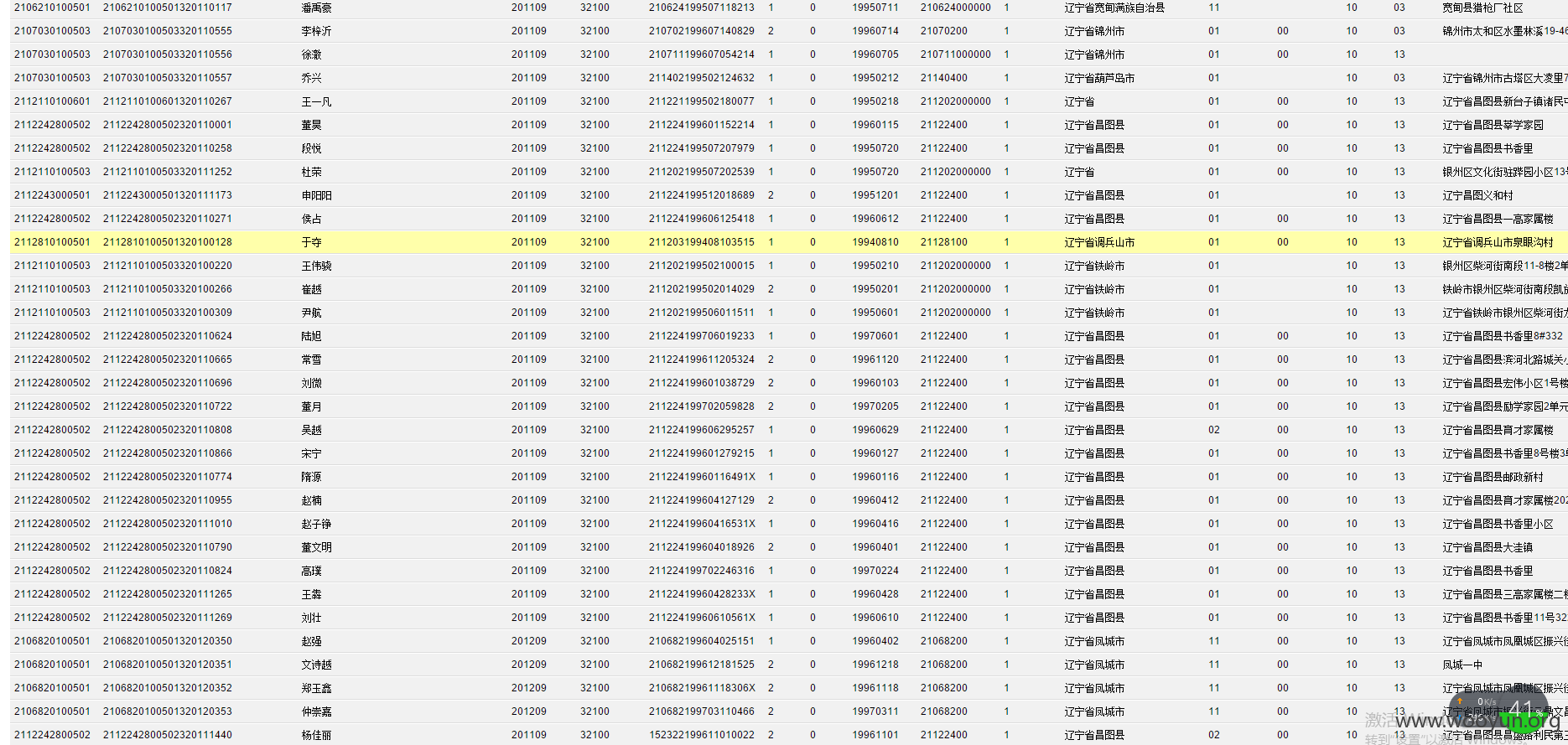

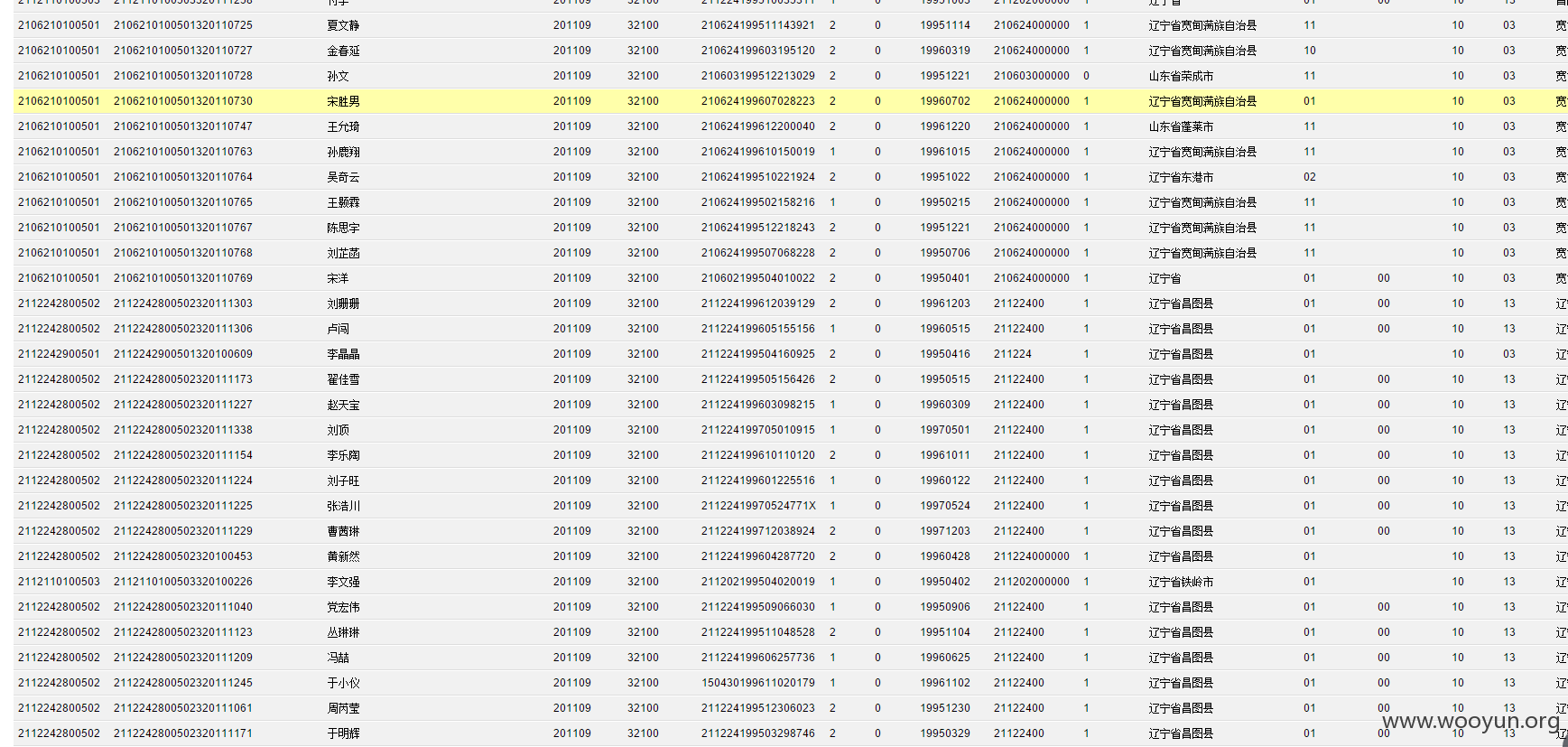
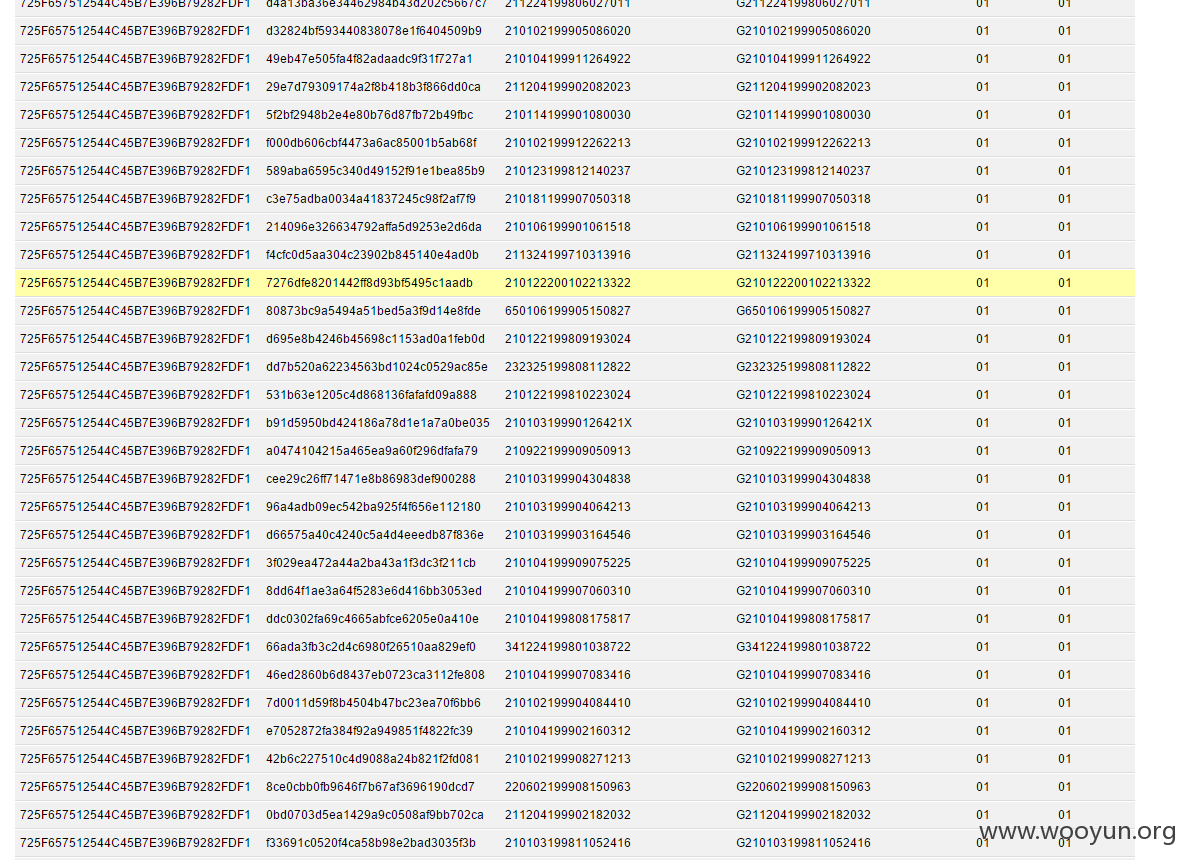
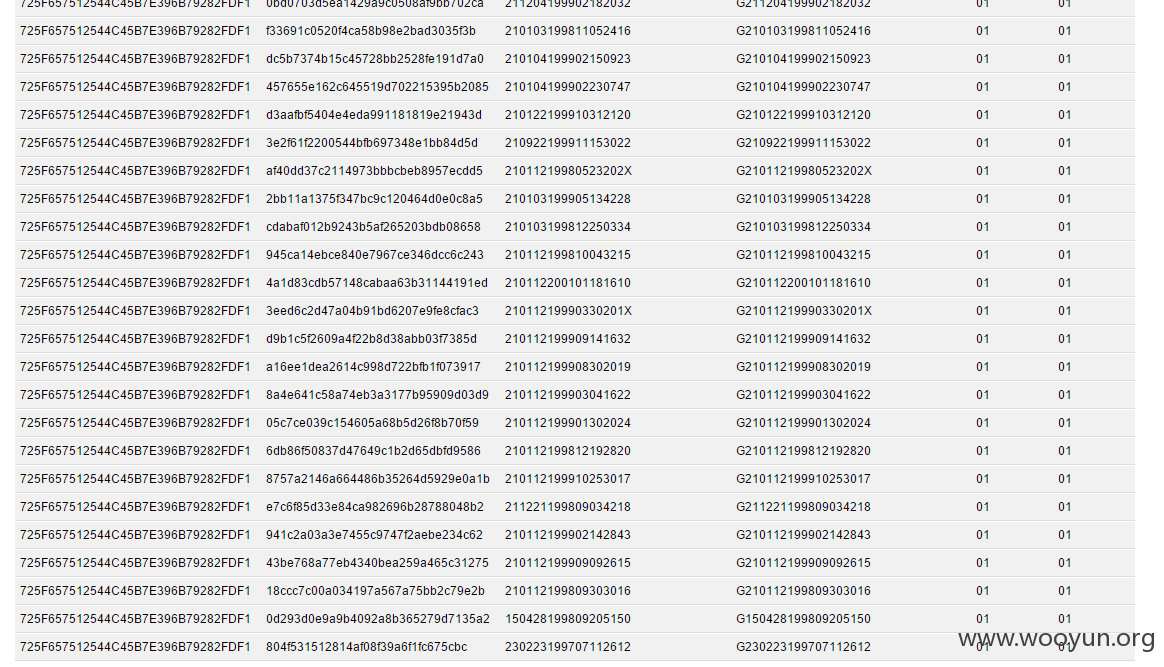
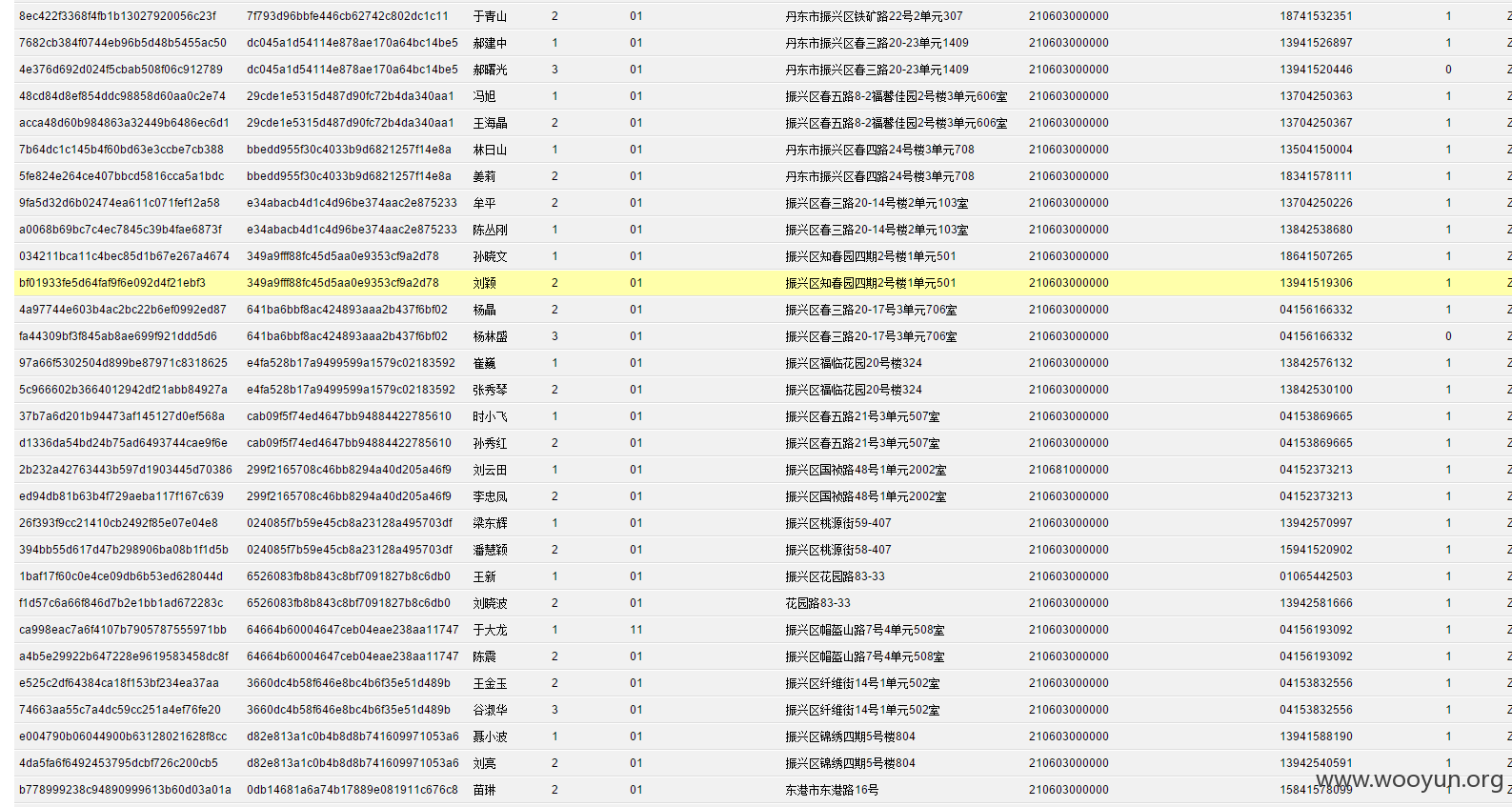
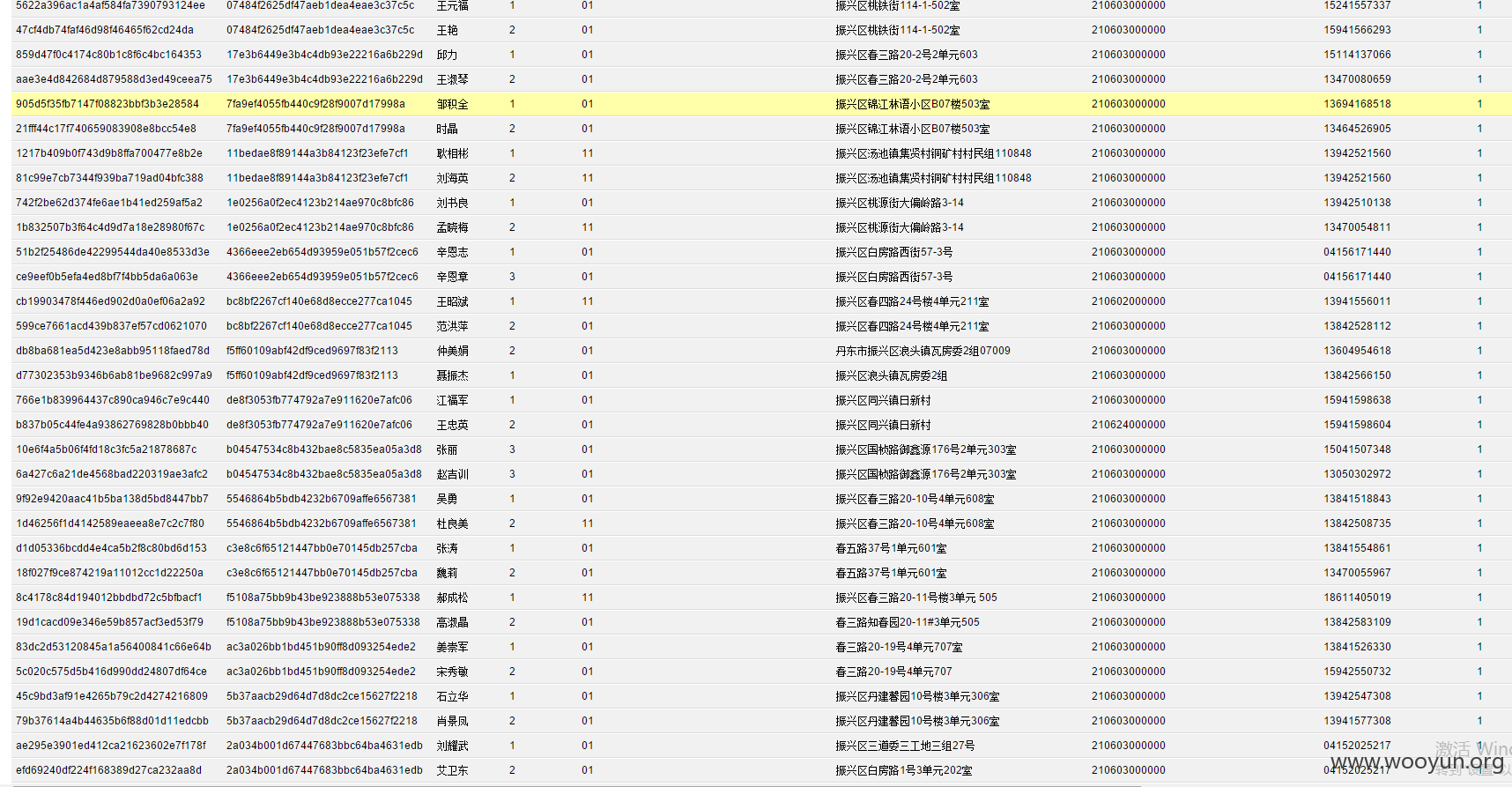
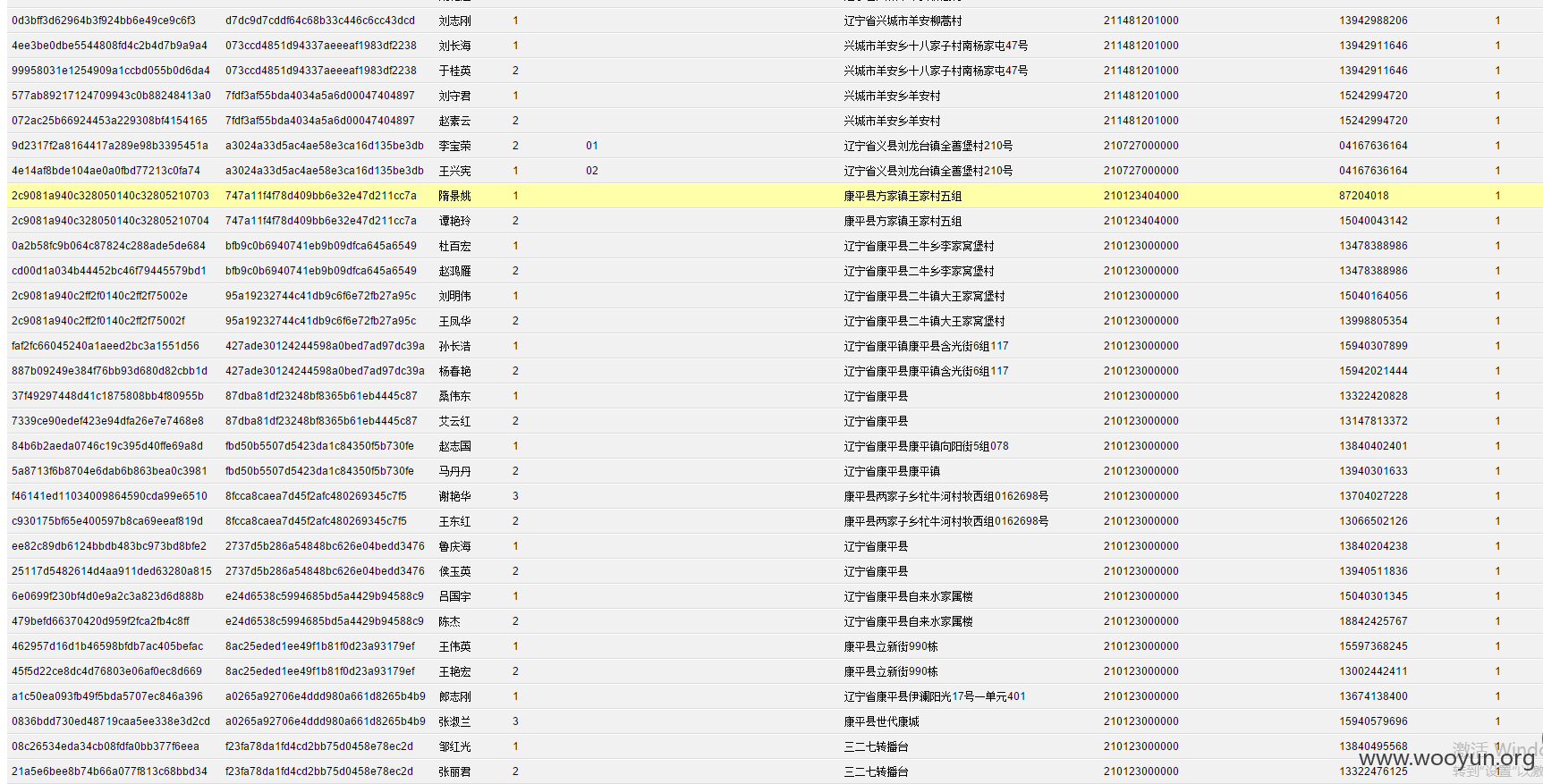
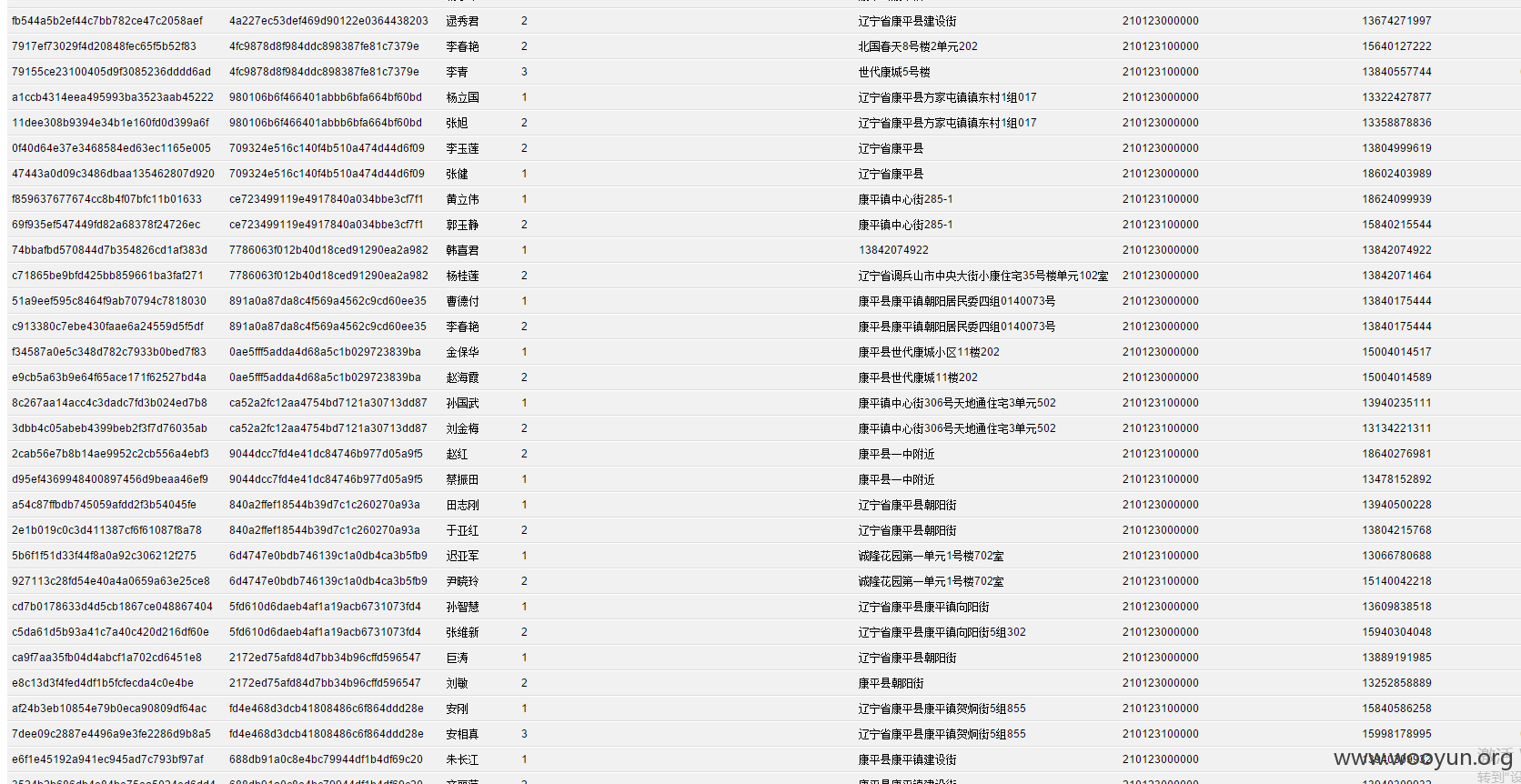
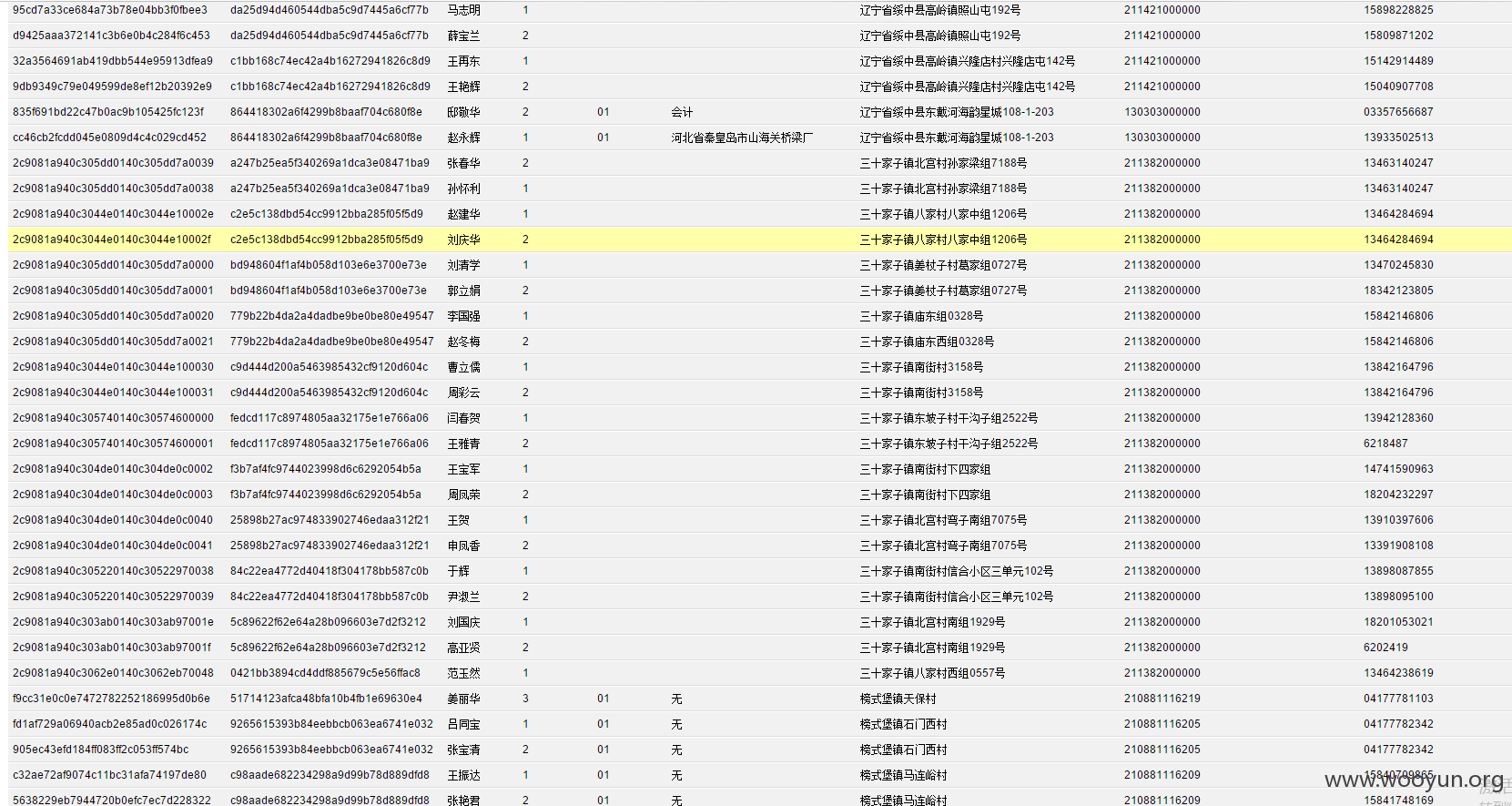
数据库配置
数据库结构。
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2016-01-22 10:36
厂商回复:
CNVD确认未复现所述情况,已经转由CNCERT下发给辽宁分中心,由其后续协调网站管理单位处置.
最新状态:
暂无





















