漏洞概要
关注数(24)
关注此漏洞
漏洞标题:台湾新保租车网getshell(可渗透内网)(臺灣地區)
提交时间:2016-01-16 10:27
修复时间:2016-02-27 11:49
公开时间:2016-02-27 11:49
漏洞类型:命令执行
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(Hitcon台湾互联网漏洞报告平台)处理
Tags标签:
无
漏洞详情
披露状态:
2016-01-16: 细节已通知厂商并且等待厂商处理中
2016-01-17: 厂商已经确认,细节仅向厂商公开
2016-01-27: 细节向核心白帽子及相关领域专家公开
2016-02-06: 细节向普通白帽子公开
2016-02-16: 细节向实习白帽子公开
2016-02-27: 细节向公众公开
简要描述:
台湾新保租车网存在远程代码执行漏洞,获取getshell,并渗透内网
详细说明:
台湾新保租车网(http://**.**.**.**/index.php/zh/)使用模板为joomla,存在远程代码执行漏洞,可获取webshell,然后渗透内网。
漏洞证明:
webshell:
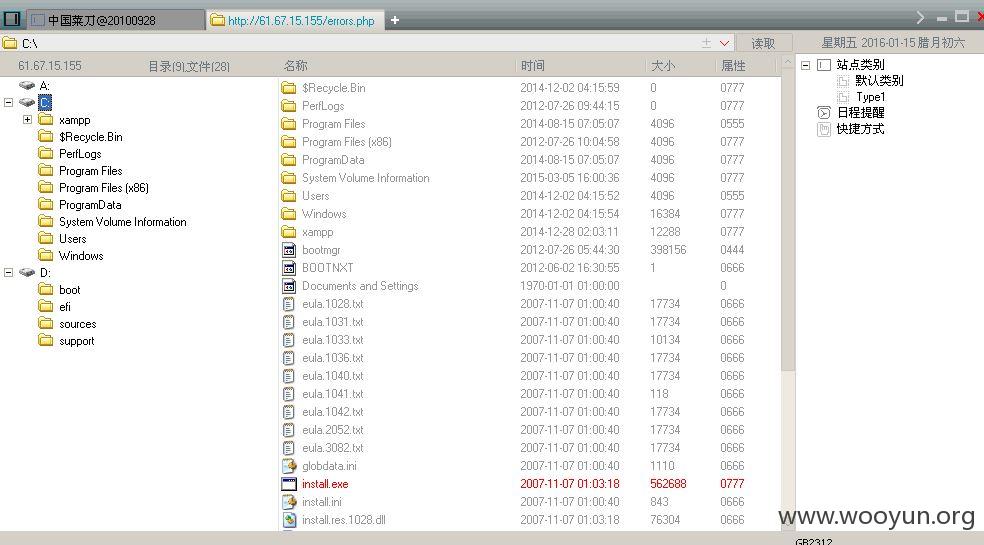
内网主机:
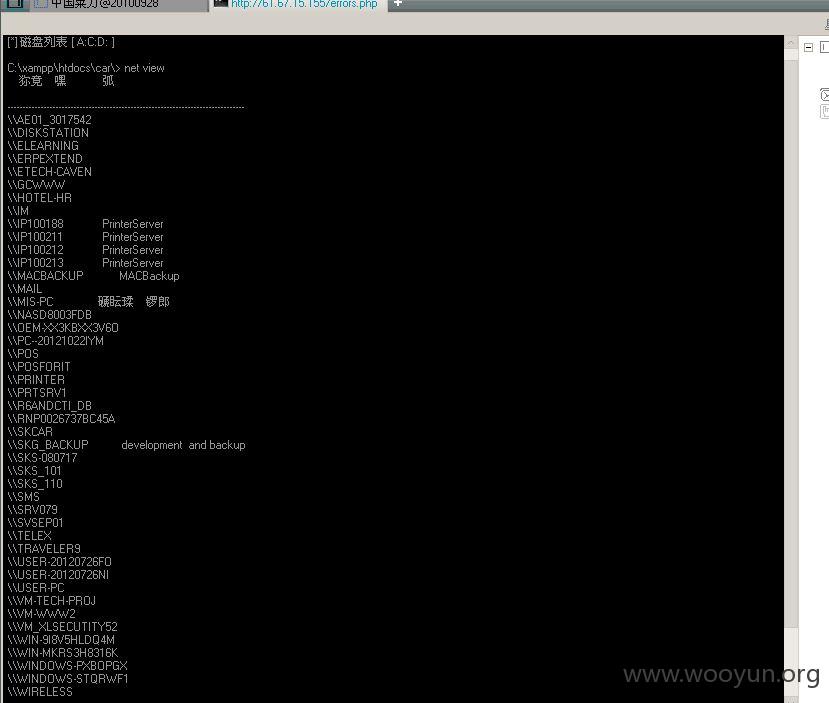
抓hash破解密码为P@ssw0rd。利用kali设置代理,远程桌面连接:
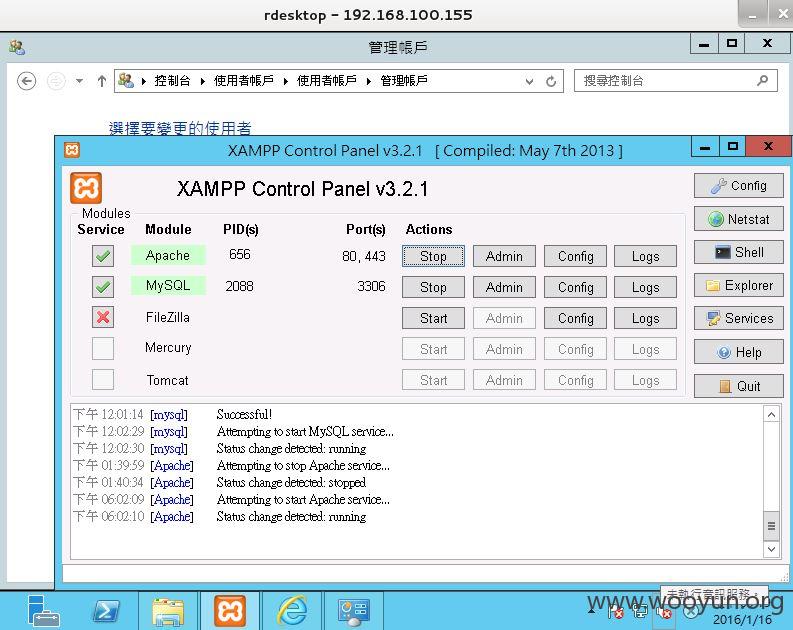
扫描内网端口:
访问内部网络:
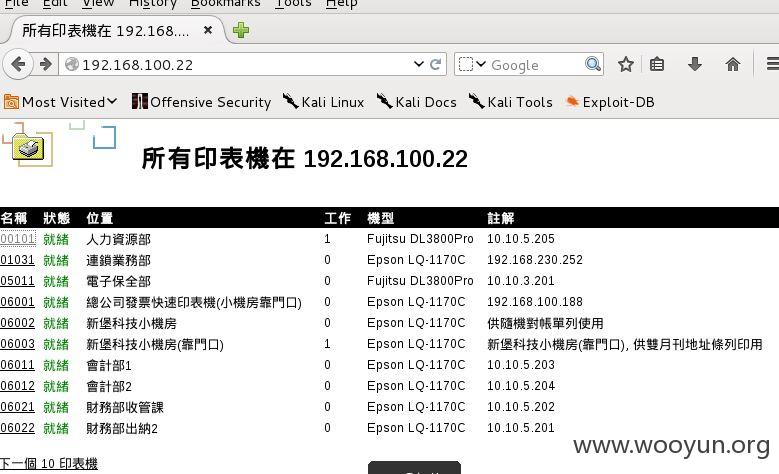
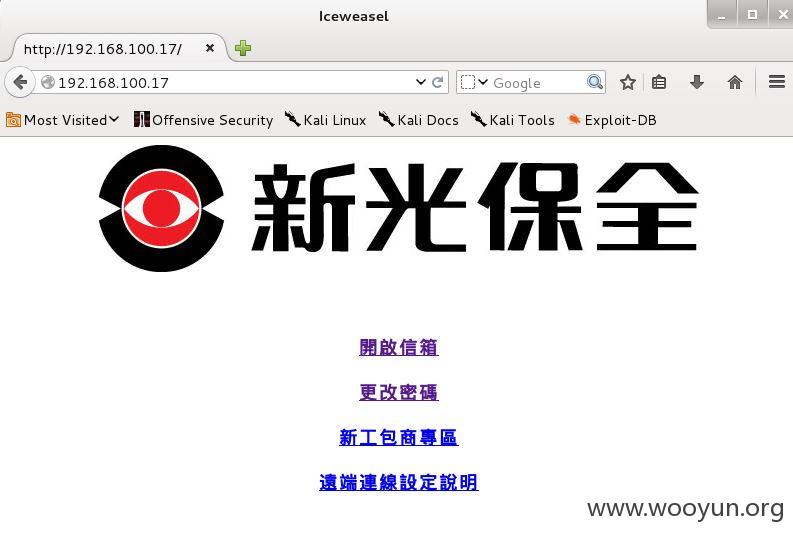
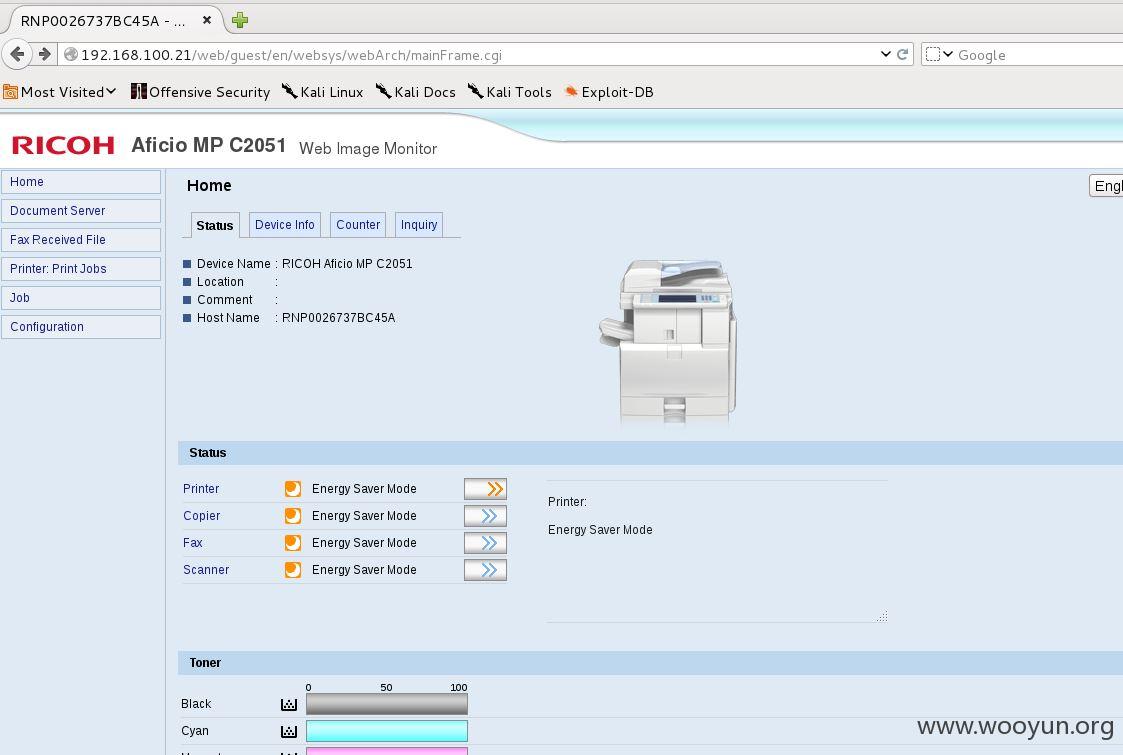
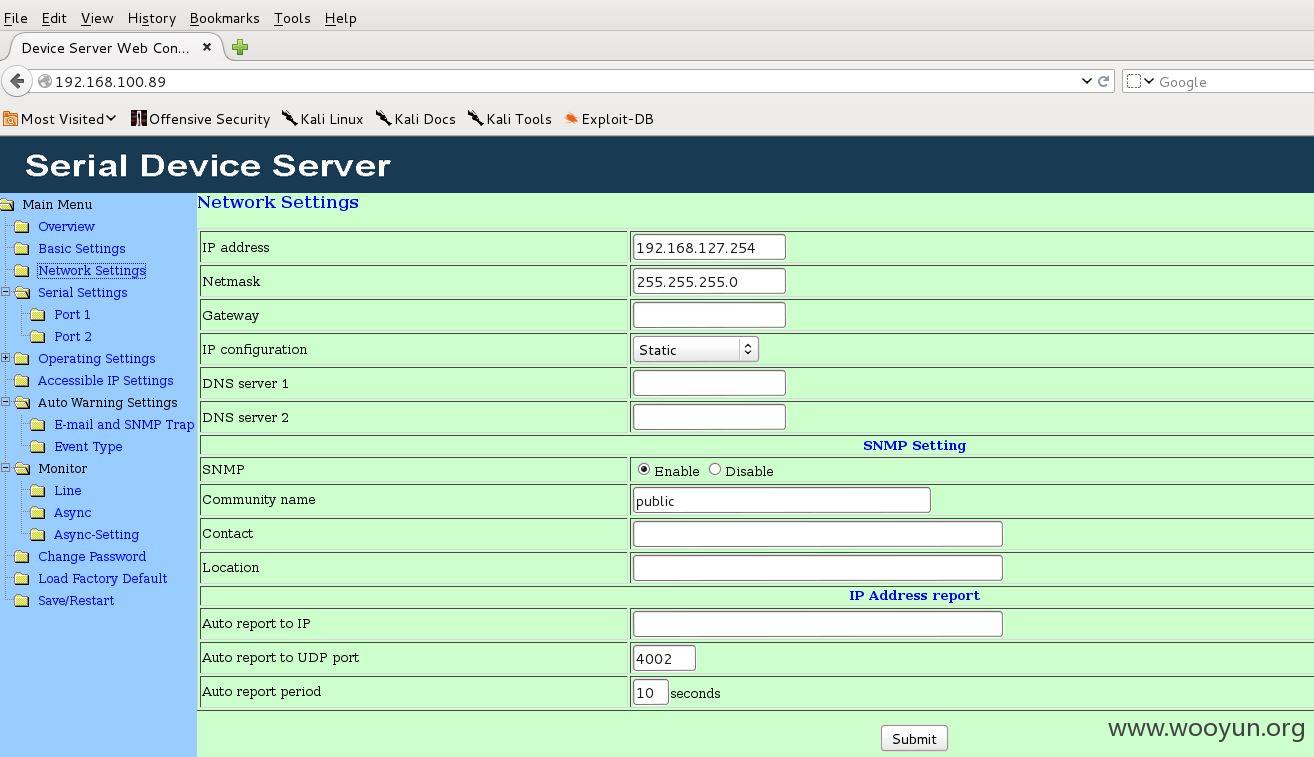
内网机器太多,这里只简单访问80端口。自己水平有限,只能渗透到这里了。
修复方案:
版权声明:转载请注明来源 lsx@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:18
确认时间:2016-01-17 18:55
厂商回复:
感謝通報
最新状态:
暂无









