漏洞概要
关注数(24)
关注此漏洞
漏洞标题:中国移动某运维研发工具多个后台弱口令可导致多个应用数据代码泄露
提交时间:2016-01-16 12:26
修复时间:2016-03-04 13:27
公开时间:2016-03-04 13:27
漏洞类型:服务弱口令
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2016-01-16: 细节已通知厂商并且等待厂商处理中
2016-01-20: 厂商已经确认,细节仅向厂商公开
2016-01-30: 细节向核心白帽子及相关领域专家公开
2016-02-09: 细节向普通白帽子公开
2016-02-19: 细节向实习白帽子公开
2016-03-04: 细节向公众公开
简要描述:
详细说明:
中国移动某业务研发集合多个后台弱口令,涉及Review Board—在线代码审查工具,JIRA--缺陷跟踪管理工具,Jenkins--持续集成工具....可内网
(中国移动物联网公司)
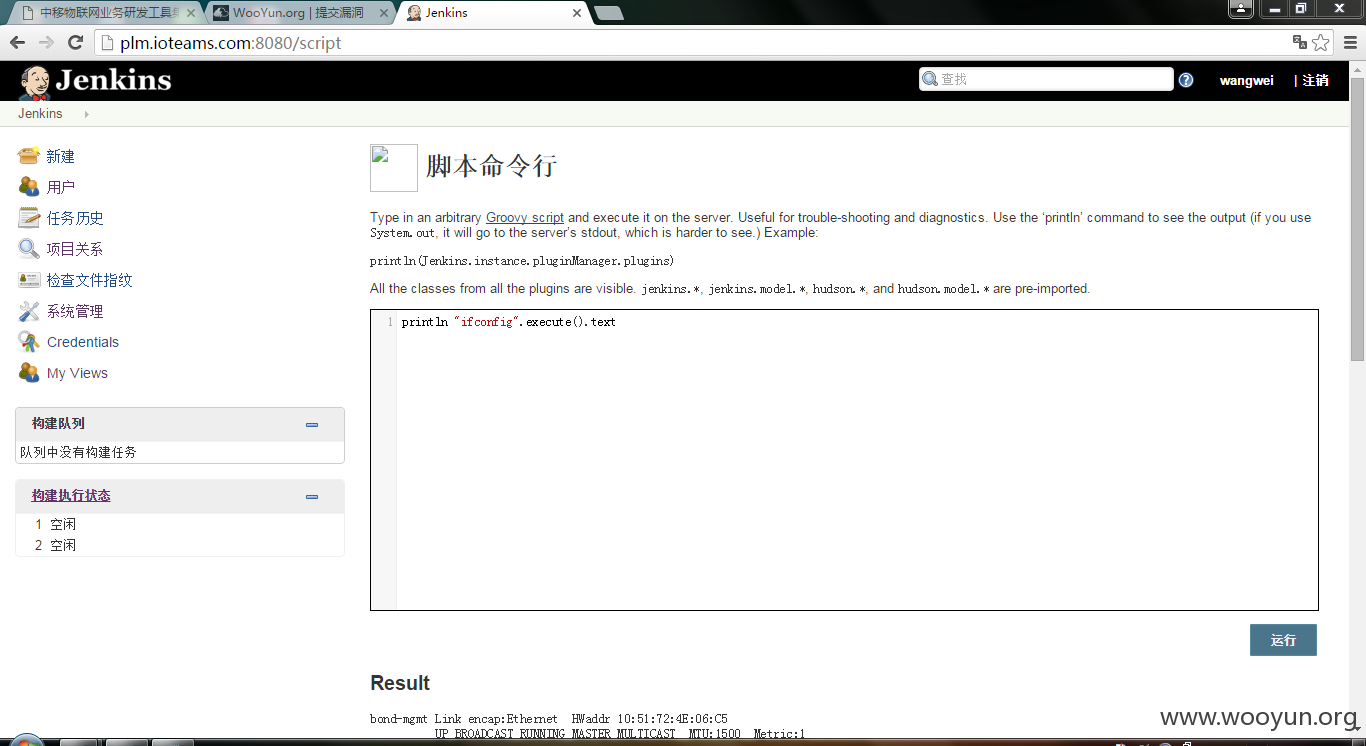
一:Jenkins持续集成工具
http://**.**.**.**:8080/login test test 登陆后查看用户 得到有弱口令权限用户:wangwei wangwei
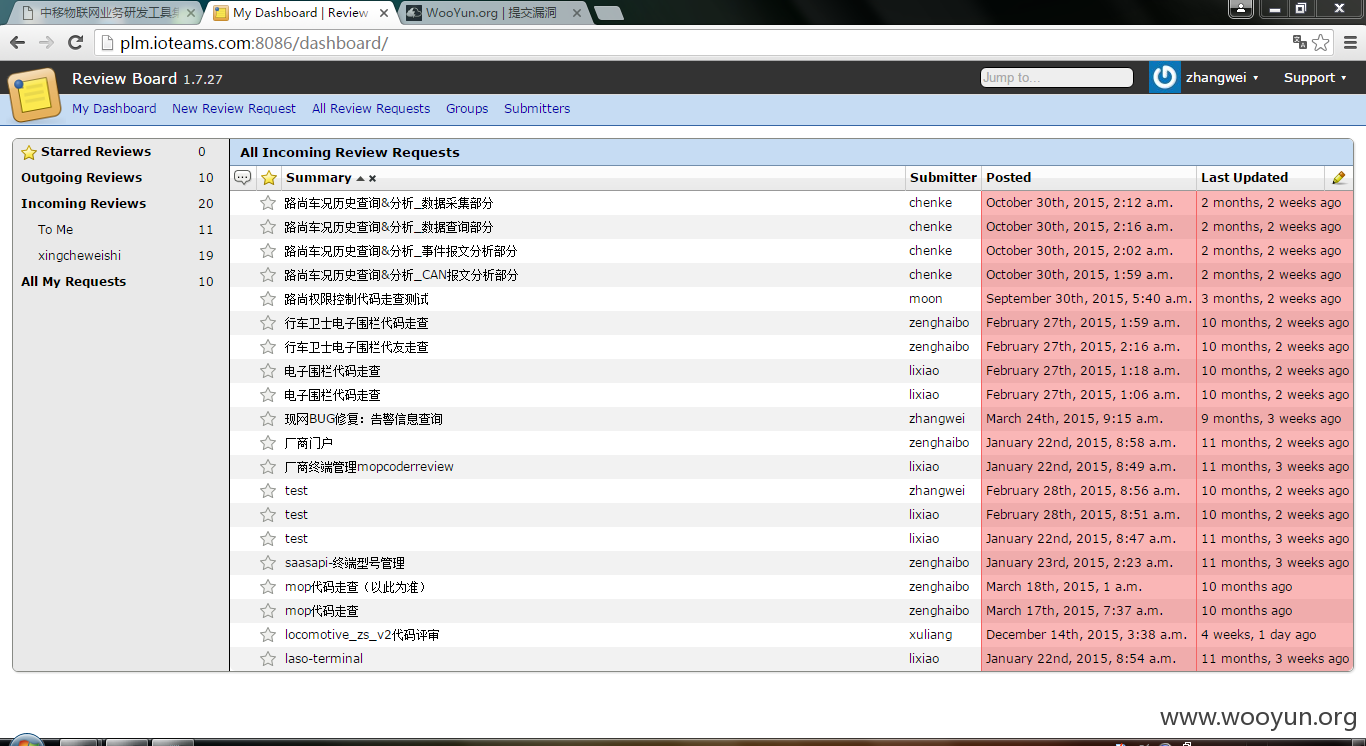
二:Review Board—在线代码审查工具
http://**.**.**.**:8086/dashboard/ zhangwei zhangwei
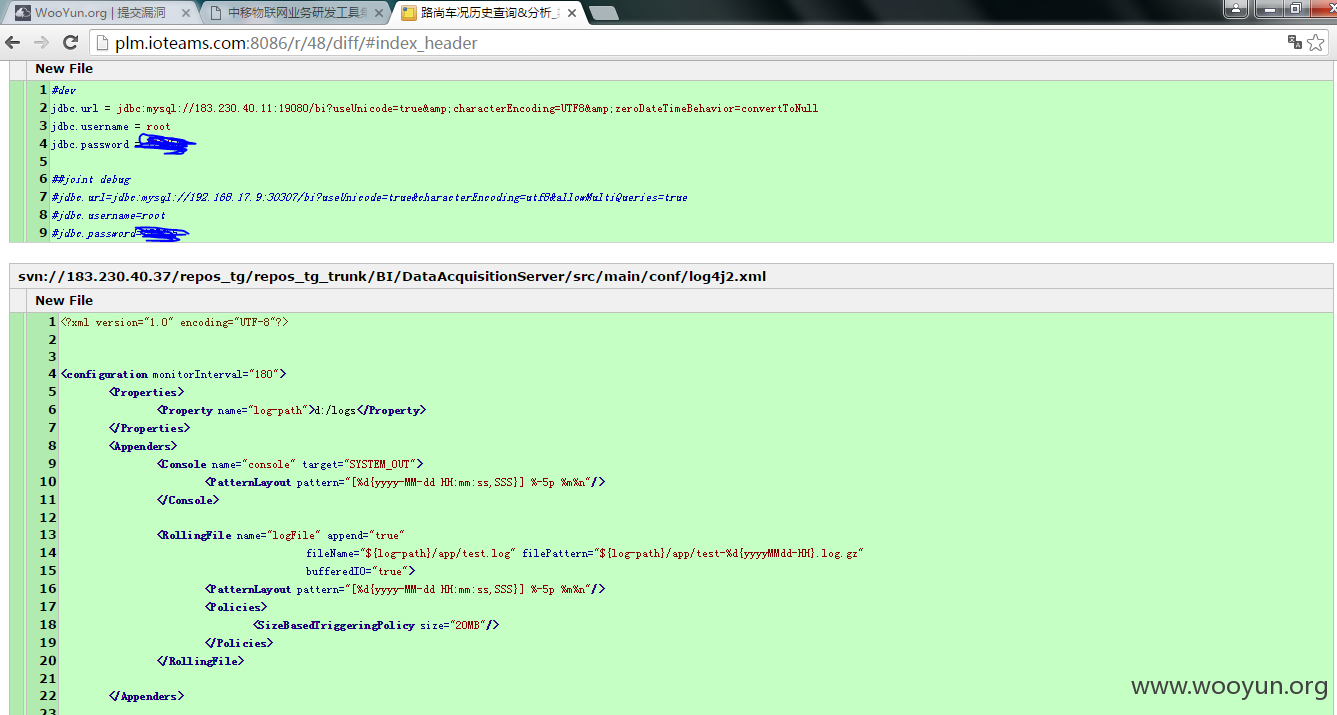
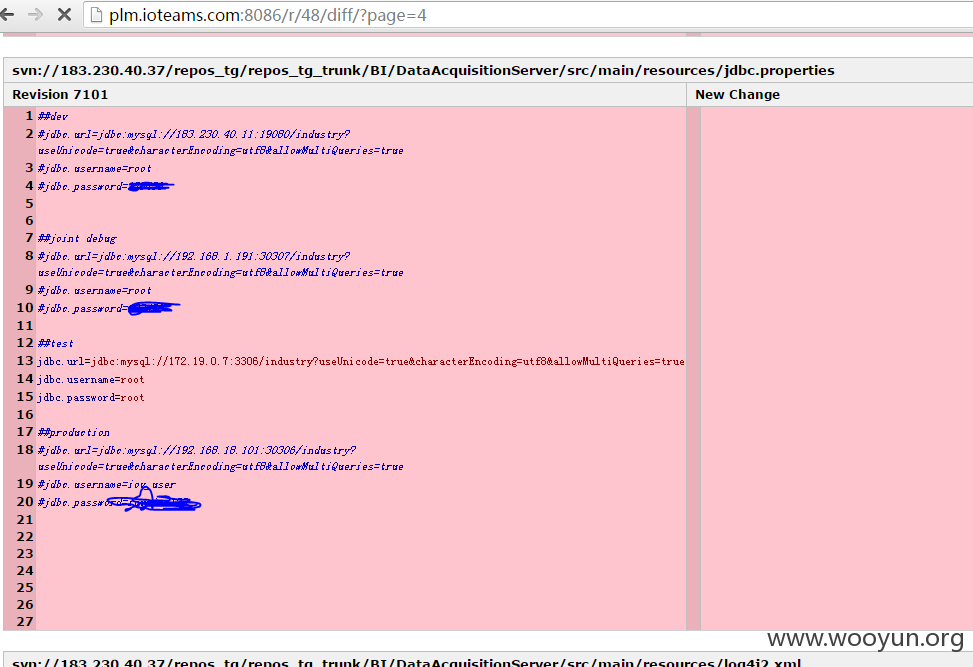
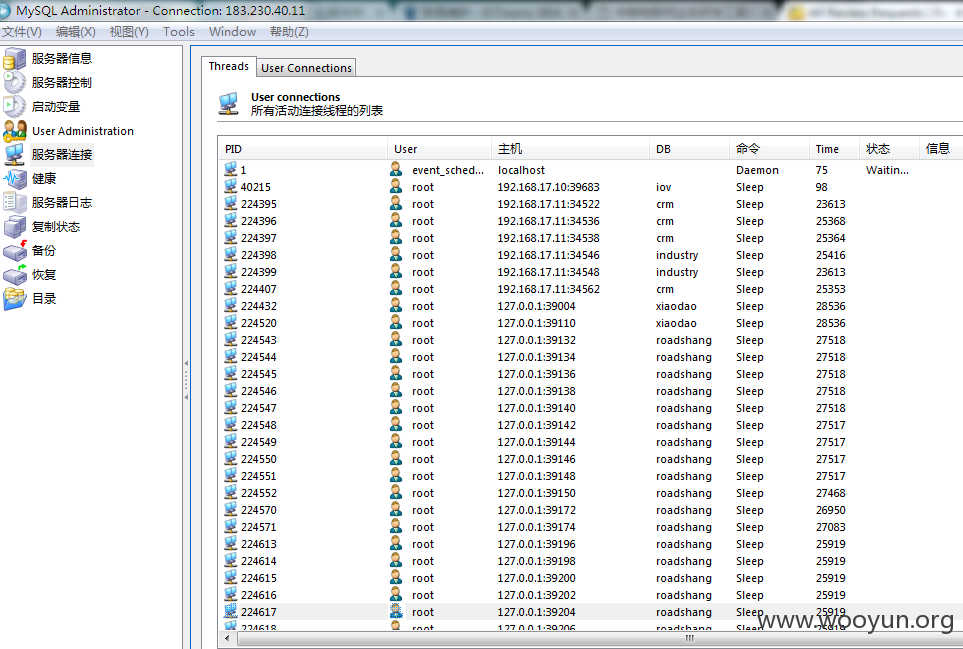
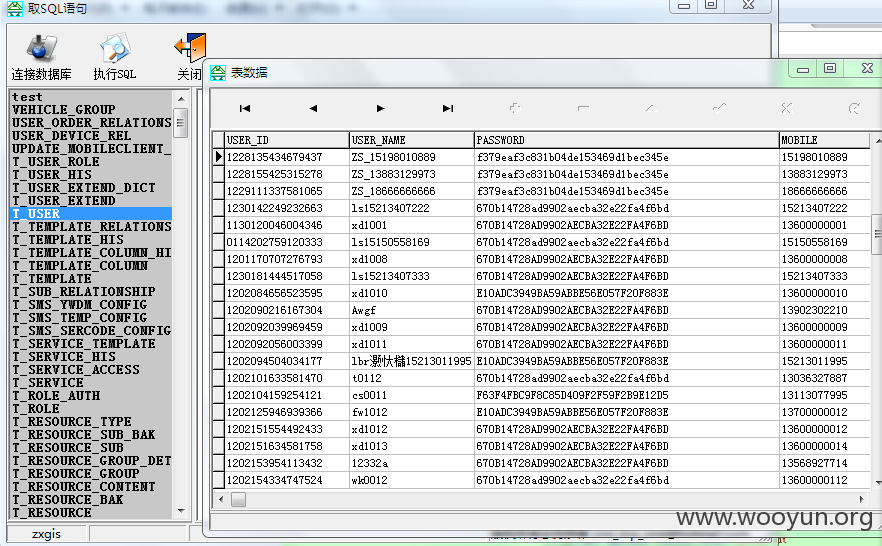
三:JIRA缺陷跟踪管理工具
http://**.**.**.**:8085/secure/Dashboard.jspa
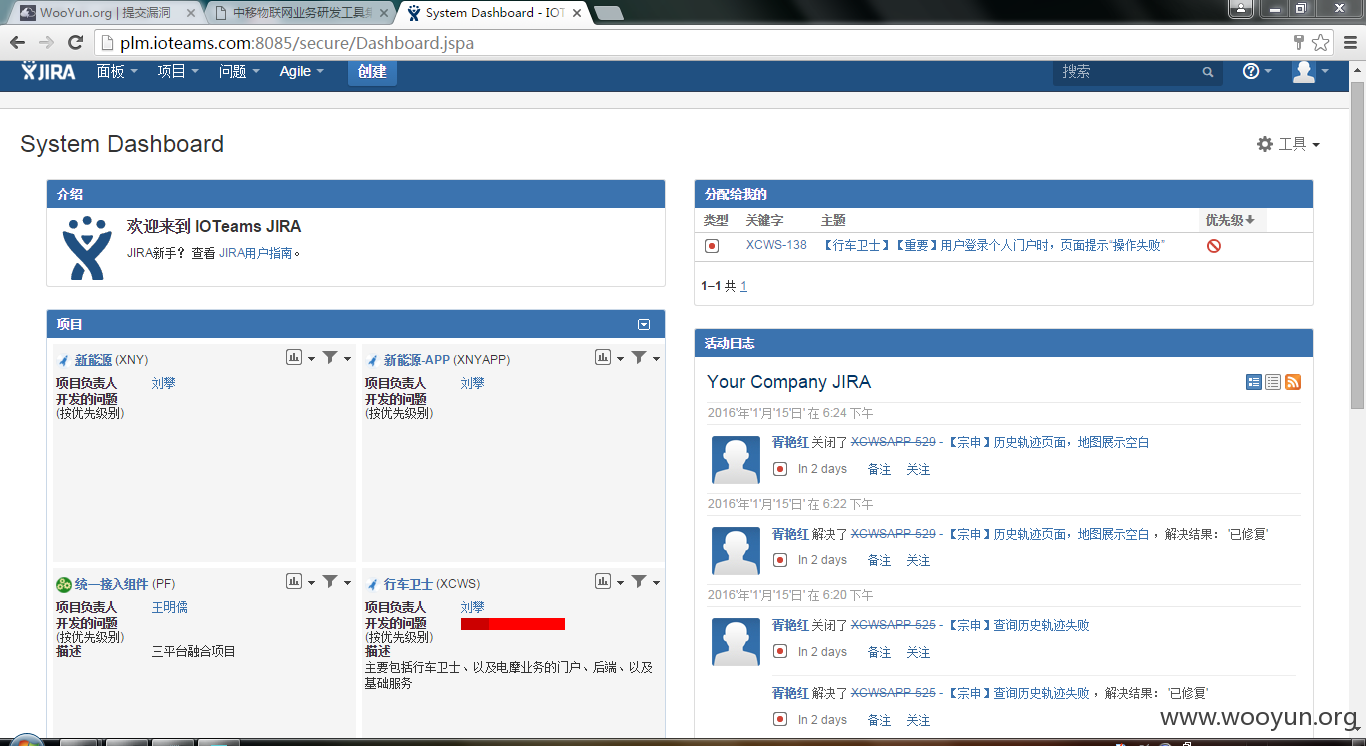
漏洞证明:
一:Jenkins持续集成工具
http://**.**.**.**:8080/login test test 登陆后查看用户 得到有弱口令权限用户:wangwei wangwei

二:Review Board—在线代码审查工具
http://**.**.**.**:8086/dashboard/ zhangwei zhangwei



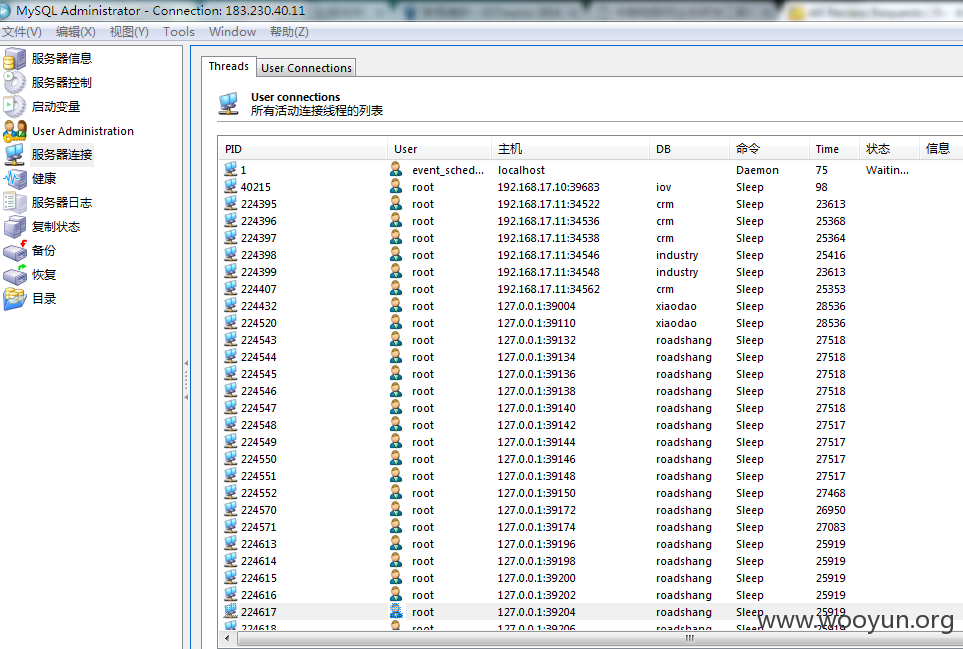
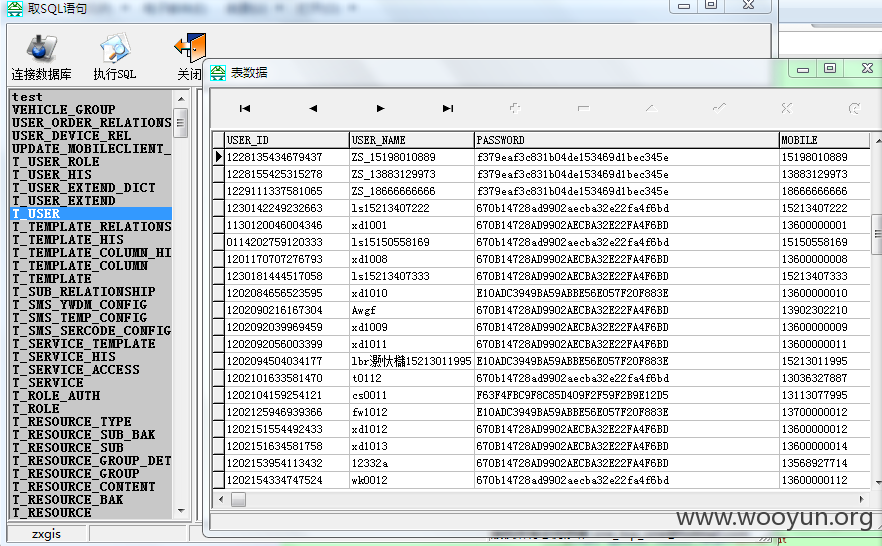
三:JIRA缺陷跟踪管理工具
http://**.**.**.**:8085/secure/Dashboard.jspa

修复方案:
版权声明:转载请注明来源 krbl@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:9
确认时间:2016-01-20 10:07
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT向中国移动集团公司通报,由其后续协调网站管理部门处置.
最新状态:
暂无











