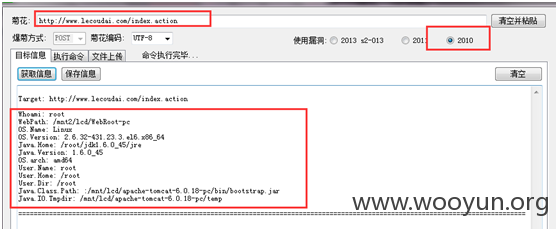
乐凑贷首家最大最安全的P2P网络投资理财、网络贷款平台,存在struts2命令执行漏洞,可任意执行命令;但平台有相关防护手段,检测到后,会将IP拉入黑名单,限制访问该网站。
漏洞链接
该服务其直接配置了外网地址182.92.97.174,且可开放了22端口服务,可外网ssh服务。
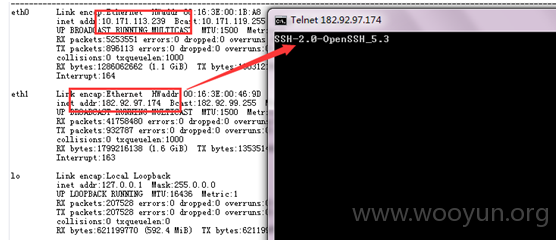
由于恶意访问,IP被限制,未能完成相关测试工作;同时,可创建账号、上传相关后门得到webshell。
请尽快确认漏洞,进行修复。。。。

该服务其直接配置了外网地址182.92.97.174,且可开放了22端口服务,可外网ssh服务。





