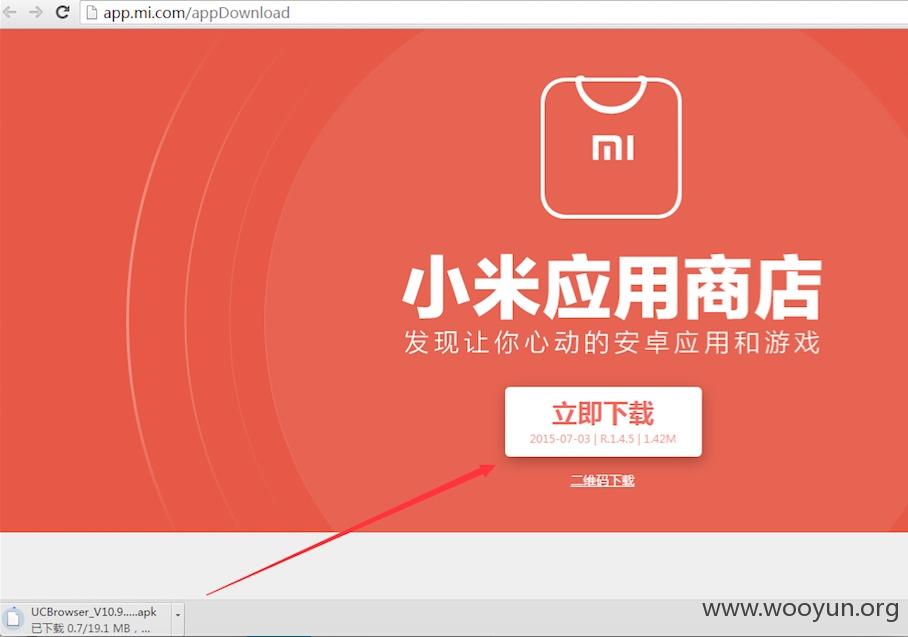
事件起源是群里有唐山的兄弟说自己下载小米商店应用,无论是手机端还是 PC 端,下载到本地都会变成了 『UCBrowserV10.9.0.703androidpf145bi800_(Build151211143335).apk』-- UC 浏览器。
在抓包过程中竟然发现了一套管理系统,所以我们就嘿嘿嘿
下载小米商店突变成 UC 浏览器,如图:
在抓包测试过程中发现了 UC 浏览器的下载链接为:
u 参数为 base64 加密字符串,解密后为小米应用商店的官方下载地址:
测试后发现上面 UC 浏览器的下载链接无论 u 参数是什么都会下载 UC 浏览器。
直接访问 **.**.**.**:81/ 是一个所谓的 『安装分发平台』,听起来像是安卓应用的分发渠道,目前看应该是这套系统搞的鬼:
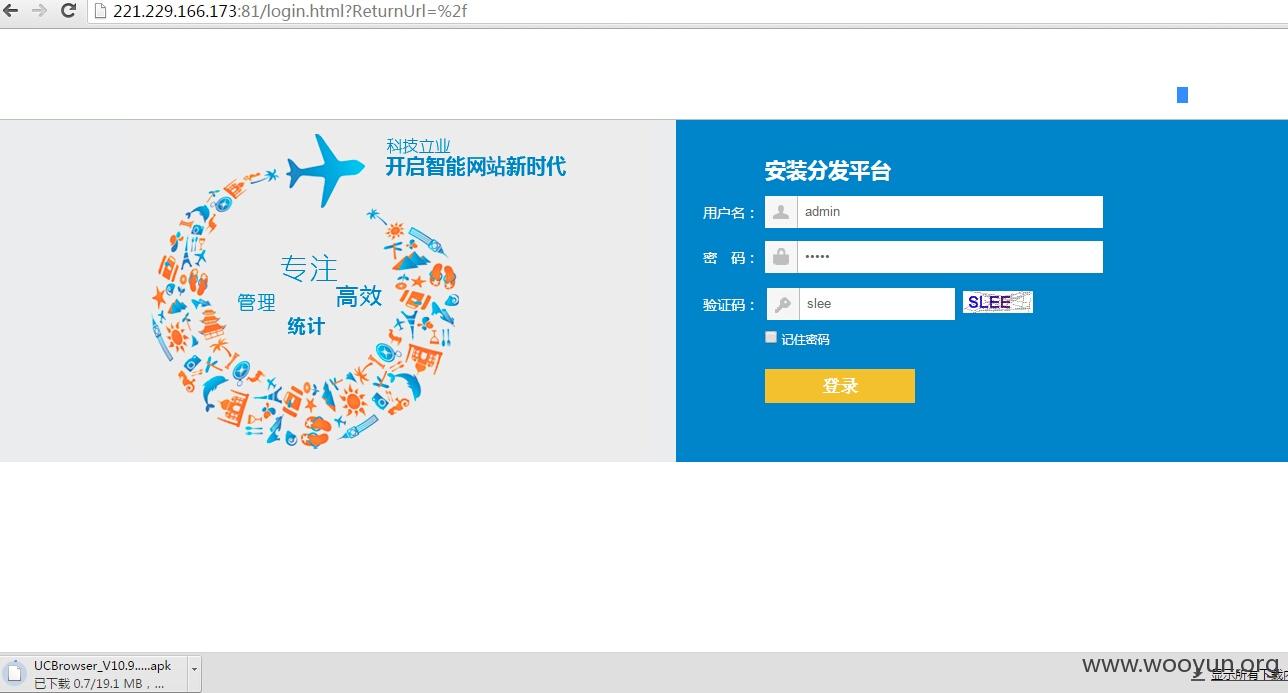
遂对该系统进行测试,发现等登录处存在 SQL 注入漏洞,并且验证码写到 Cookie 里面就可以无限使用,直接丢到 SQLMAP 里面:
但是对注入利用获取到的管理账户密码为自定义加密,暂时放弃后台,转为 getshell,虽然不是 dba 权限,但是有某颜色老师的帮助,轻松获取到 webshell。
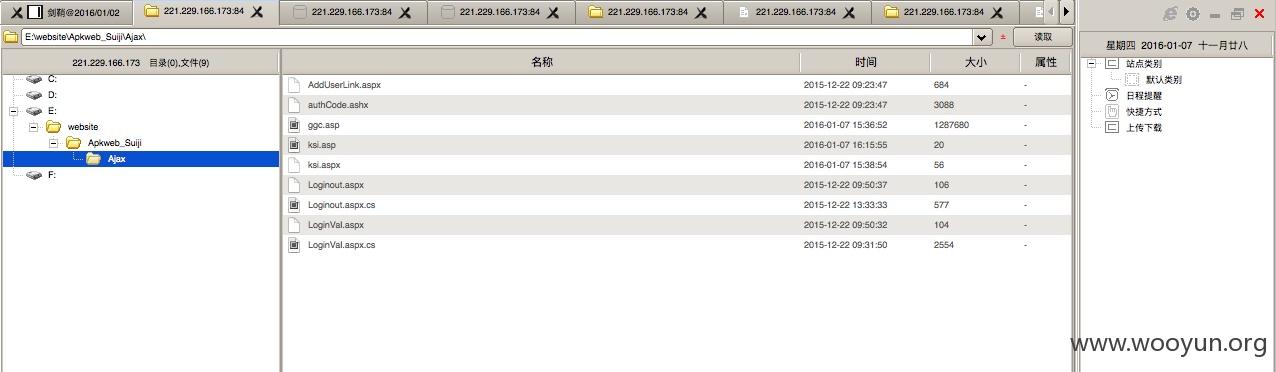
BTW:在获取权限的过程中,81 端口突然无法访问,扫描发现开放了 84 端口,跑着同样的系统,所以上图中的 webshell 为 84 端口。
对数据库结构大概浏览了下,他们把这种劫持称之为跳转,并且会把每个跳转的记录都入库,还会按照日期(每天)进行分表。
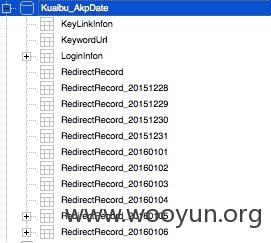
查询RedirectRecord_20160106表,记录的数据格式为:
可以看到有一些关键信息:FromUrl FromIp RedirectUrl RedirectTime 来判断这条记录是 IP 为 **.**.**.** 的用户下载 **.**.**.**/cache/**.**.**.**/download/AppStore/0c67d41f51b7b9186d776df76eb2e0e540143b1fa/%E5%BF%AB%E6%89%8B_**.**.**.**_669.apk?ich_args=5f85a51ec0dafb877cf1588864b30d0d_1048_0_0_14_b0659a6f93f4fc260ebd987cb904216b97378fd0ed64de08c1e6a5d9b0eae411_47a8607d034746fc31acb1017a36bf83_1_0&ich_ip=39-244 小米商店应用,最后被跳转下载 http://**.**.**.**/down1/gongyp/kbllq/UCBrowser_V**.**.**.**_android_pf145_bi800_(Build151211143335).apk UC 浏览器。
统计了下每个表中的记录数为:
劫持的数据每天高达百万,如果这么做的话,随便一款 APP 装机量都挺恐怖的。
通过 webshell,我们解密加密后的密码登陆到后台,后台功能比较简单:
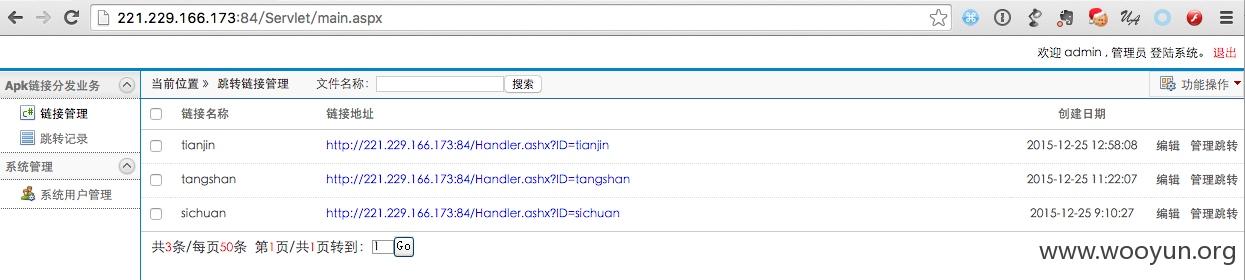
看页面显示有 tianjin tangshan sichuan,感觉应该是地区拼音,还记得我们前面说的那位唐山兄弟吗?难道是只对这些地区的 IP 进行劫持?我们从数据库中抽查部分数据,能够印证我们的推测。
对 tangshan 的这条数据进行管理跳转操作,有如下内容:
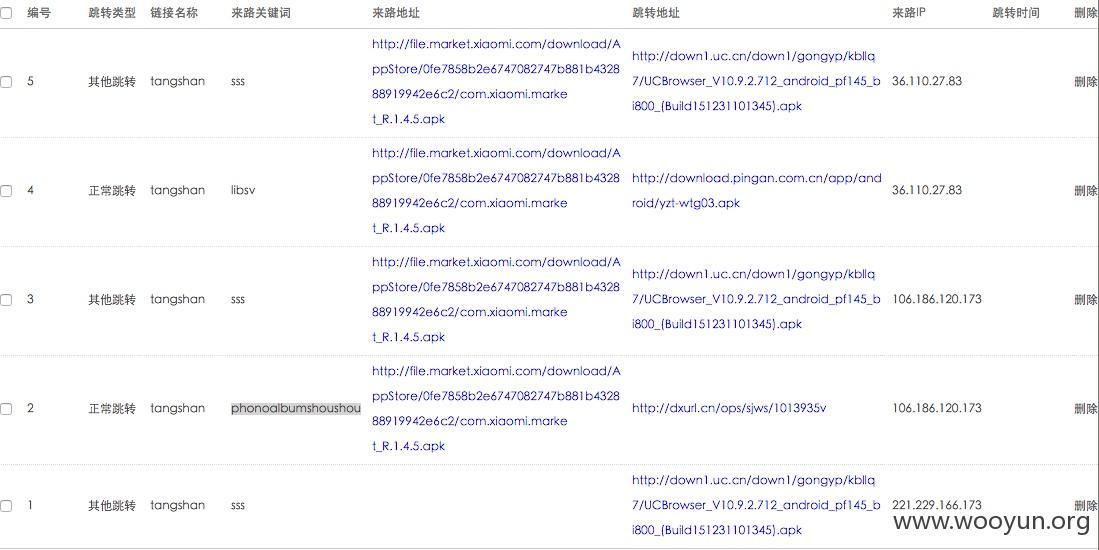
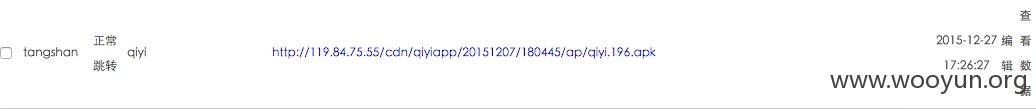
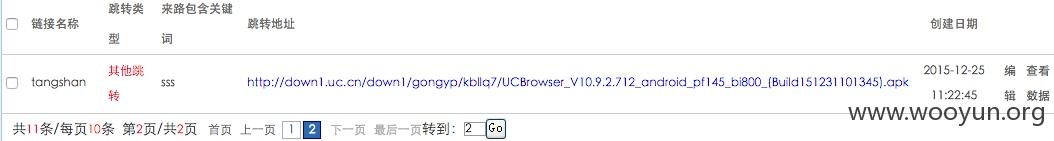
看来除了 UC 浏览器还有别家通过这套劫持系统对自家的应用做推广。比如百度手机卫士、360 安全卫士、爱奇艺等。
PS:还发现一个比较奇怪的事情,就是被劫持的链接本身就是自己的应用,最后又被劫持为自家的应用。难道是这个平台为了骗厂家劫持量?










