http://bill.bestpay.com.cn:37006
webserver代理配置不当
写了个php小脚本去遍历内网的web服务
http://172.17.16.52:8080/
http://172.17.16.9/templates/index/hrlogon.jsp
http://oa.bestpay.com.cn/loadpage.nsf?Open
http://172.17.16.7/
http://172.17.162.12:9080/ospweb/jsystem/common/login_login.do
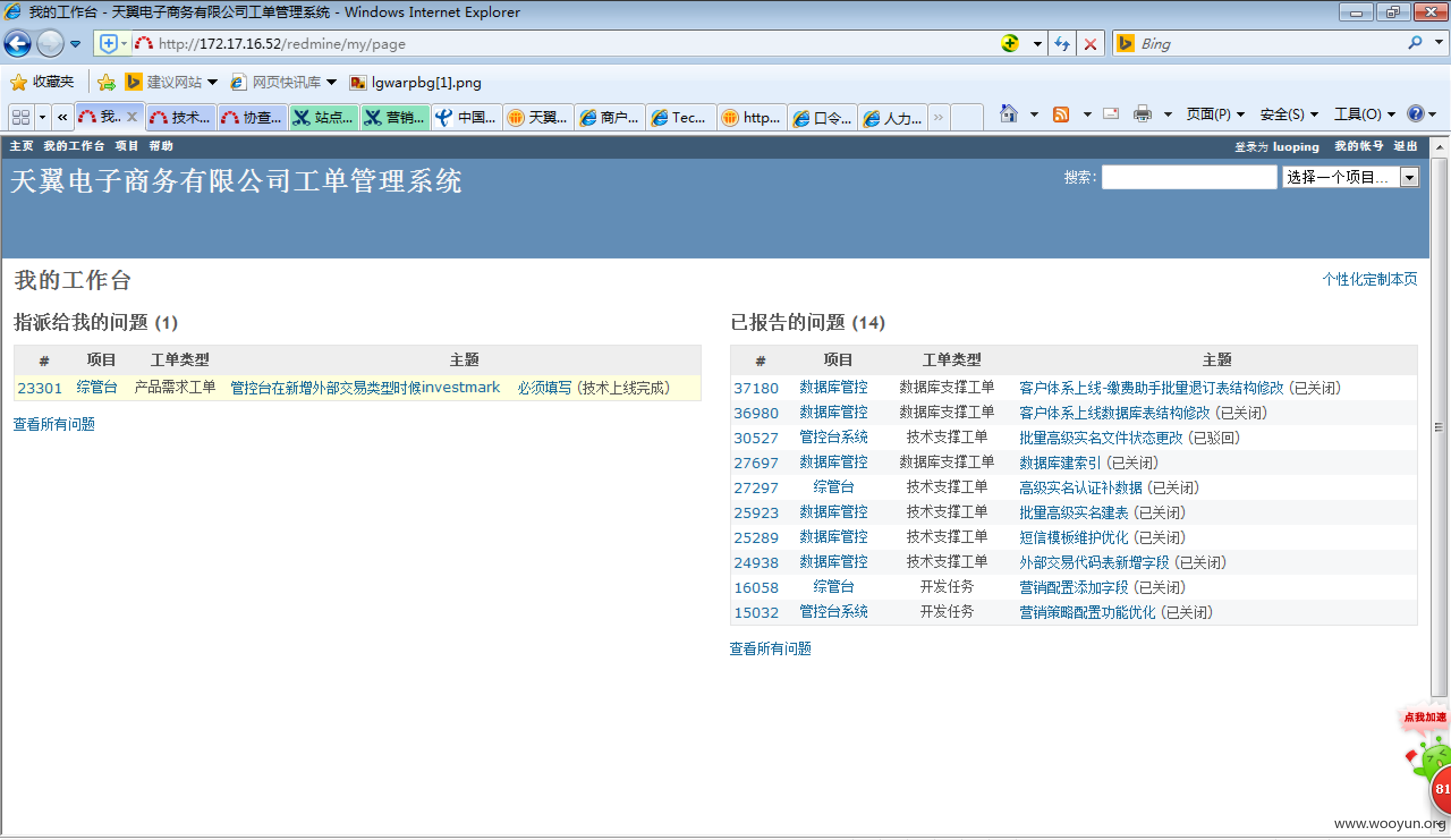
http://172.17.16.52/redmine/
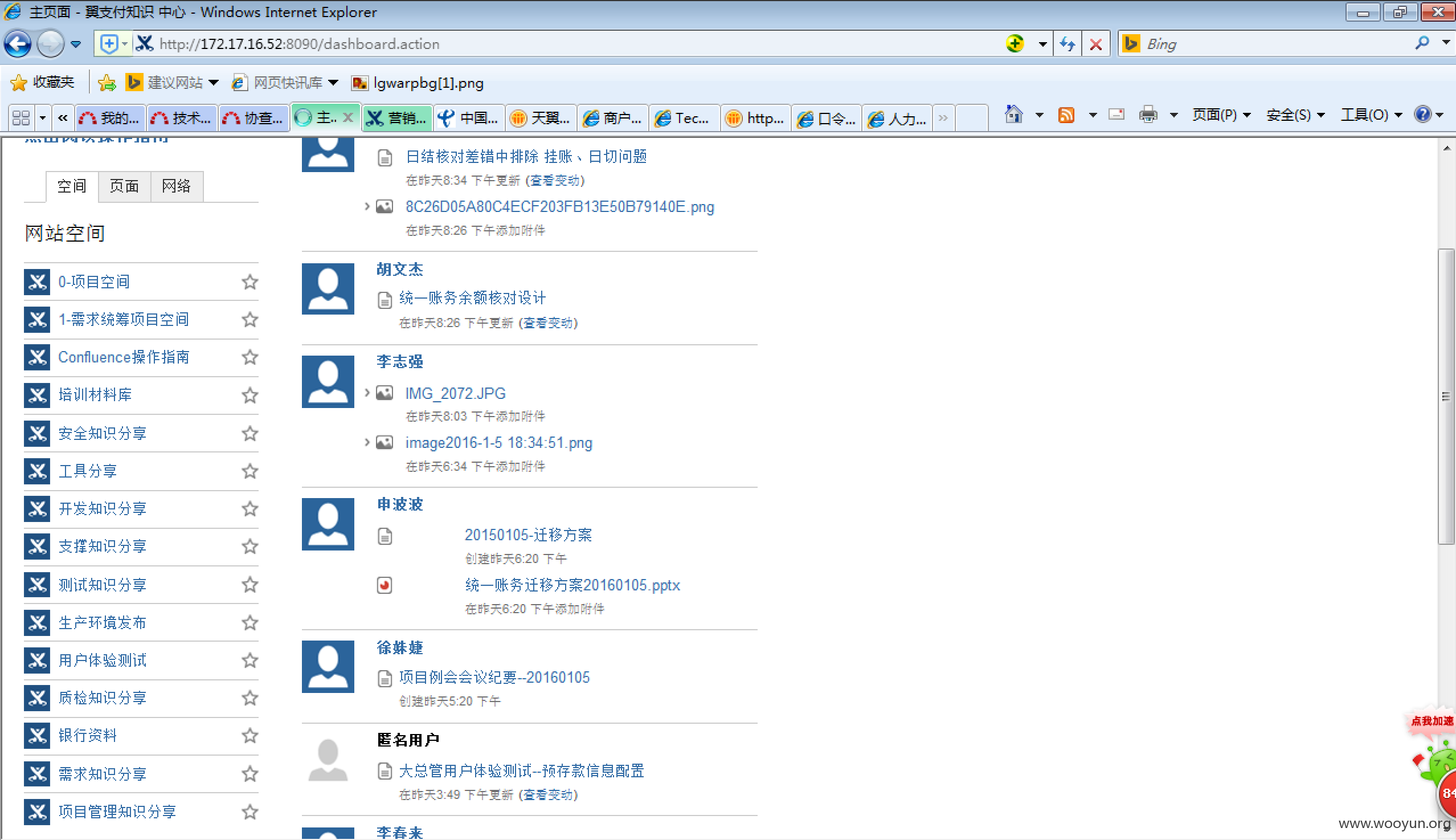
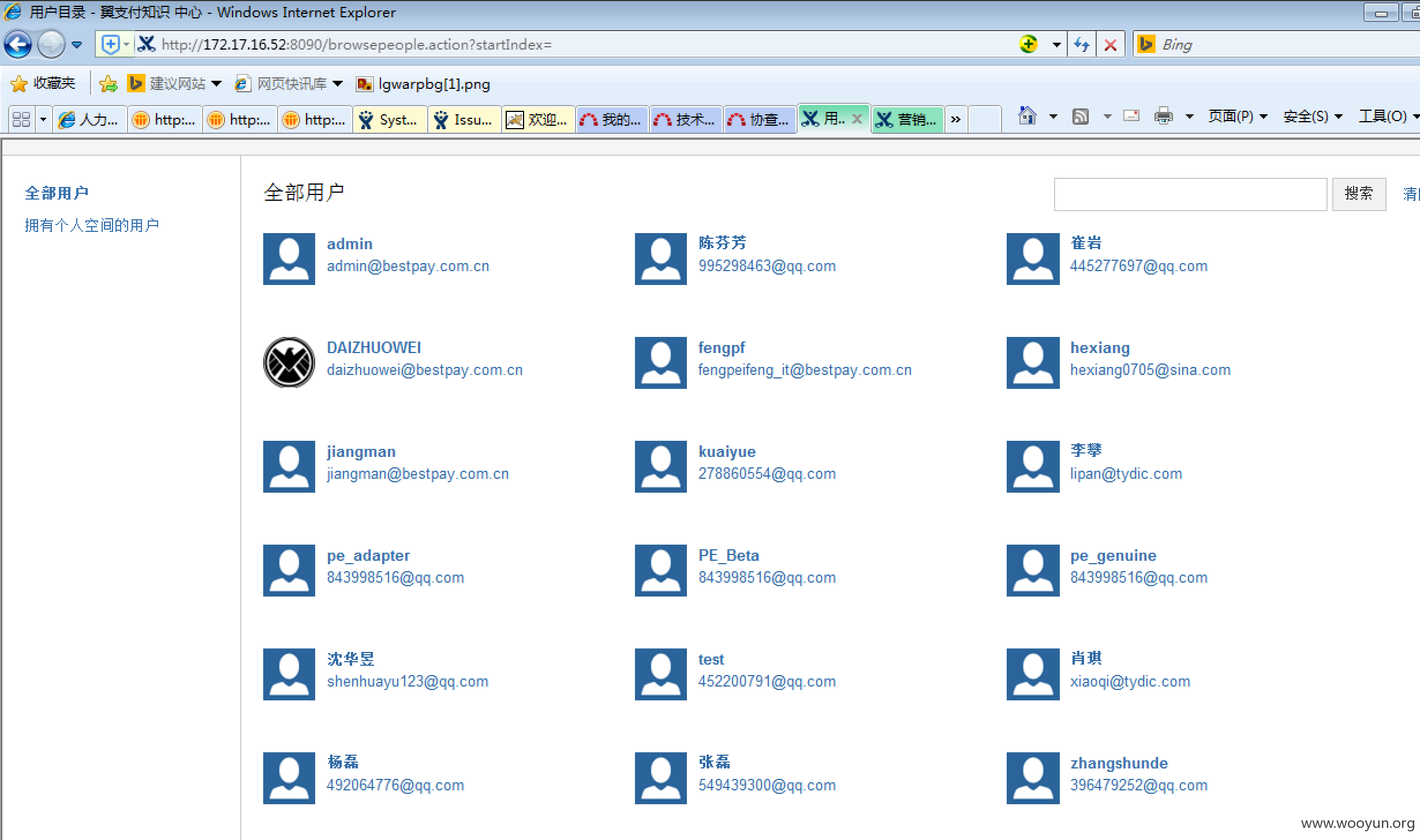
http://172.17.16.52:8090/
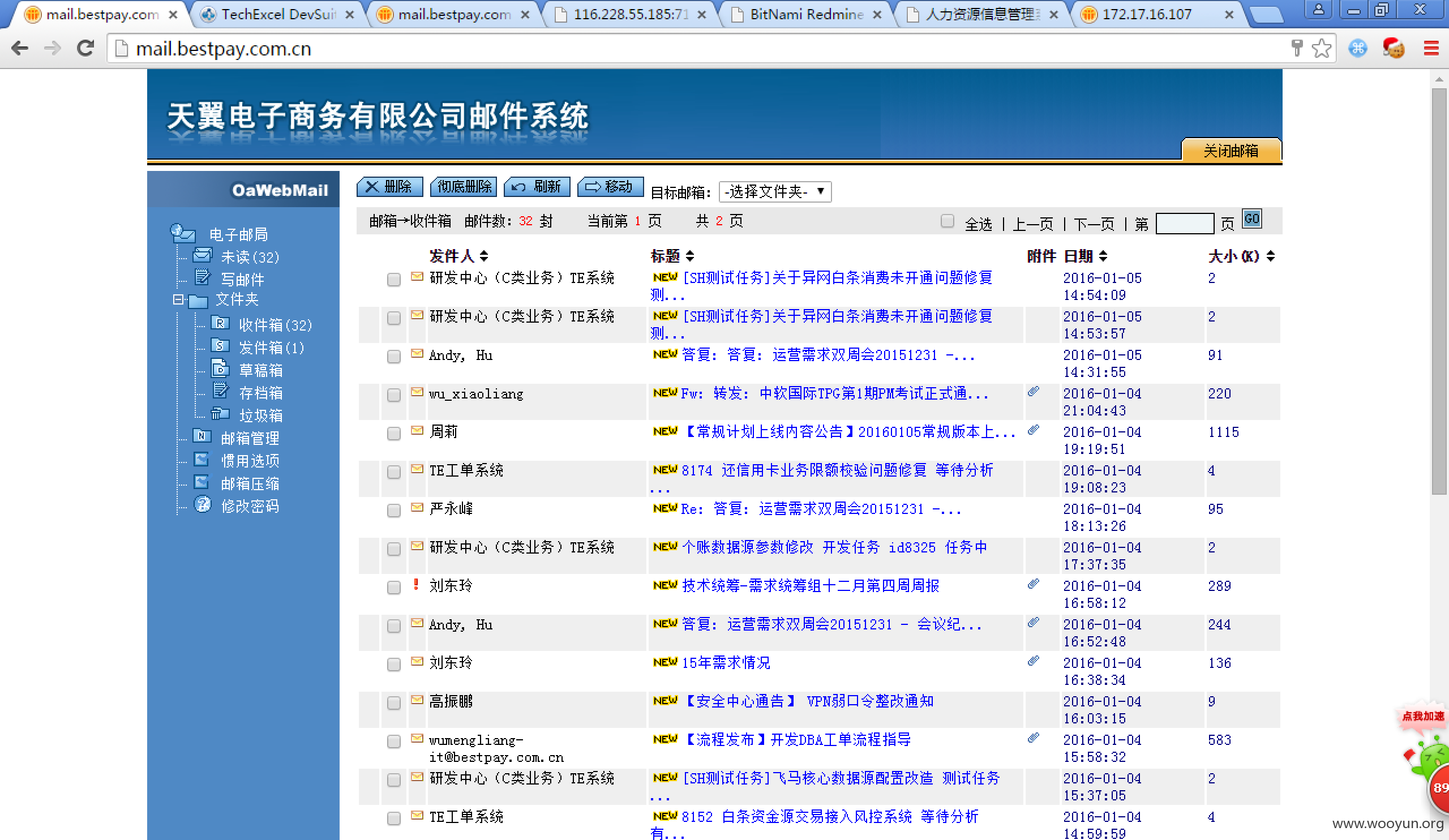
http://mail.bestpay.com.cn/names.nsf?Login
mail邮件系统爆破出几个弱口令邮箱
http://172.17.16.52:8090/
Confluence系统弱口令:
密码为用户名+123
从Confluence系统得到一个员工用户名列表并发现邮件系统存在默认密码:abcd_123
二次爆破得到大量邮箱账号密码:
继续爆破:
jira弱口令:
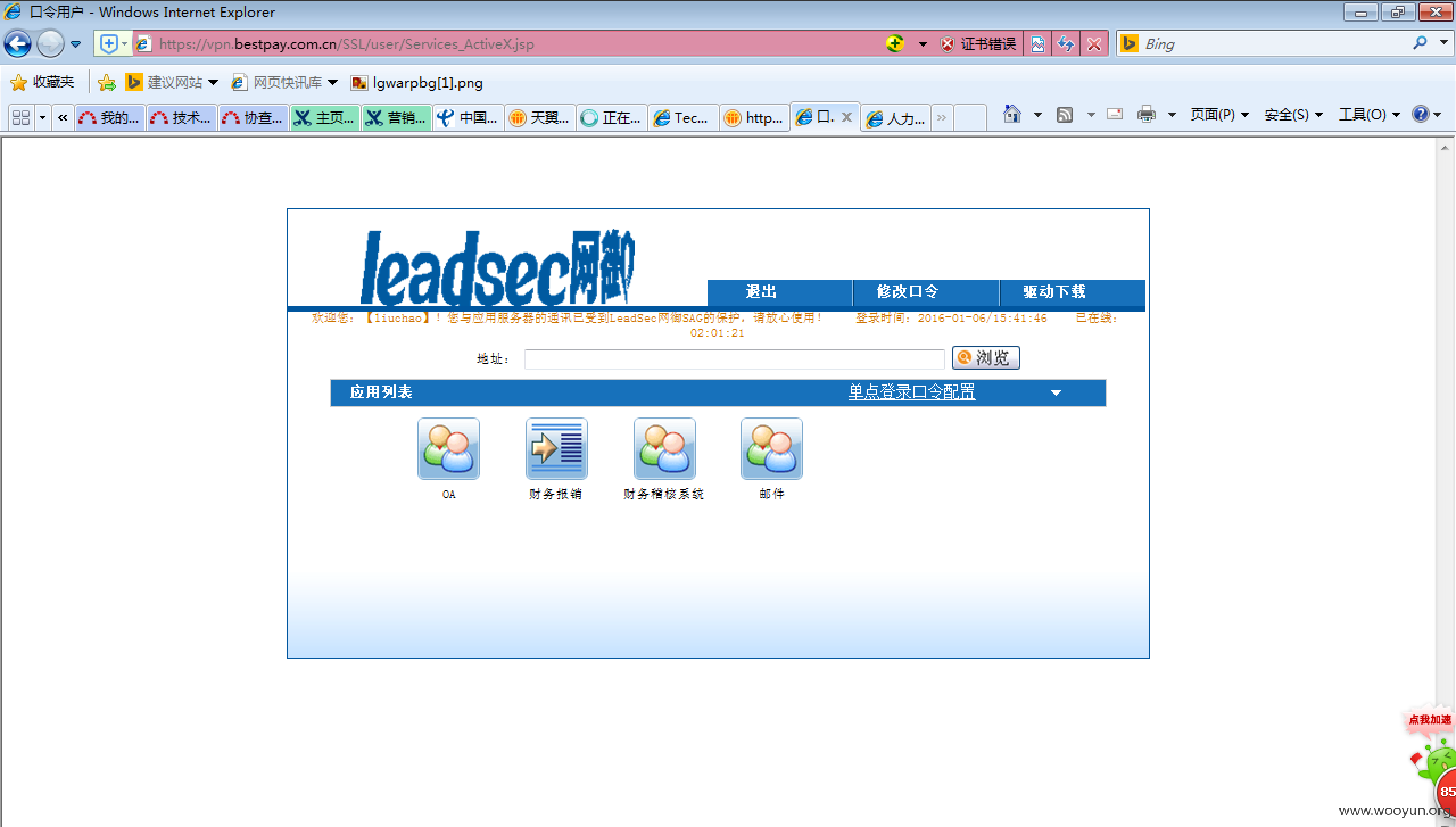
然后是vpn
https://vpn.bestpay.com.cn
base64解码后是vpn用户名,密码是abcd_123
liuchao Abcd_123
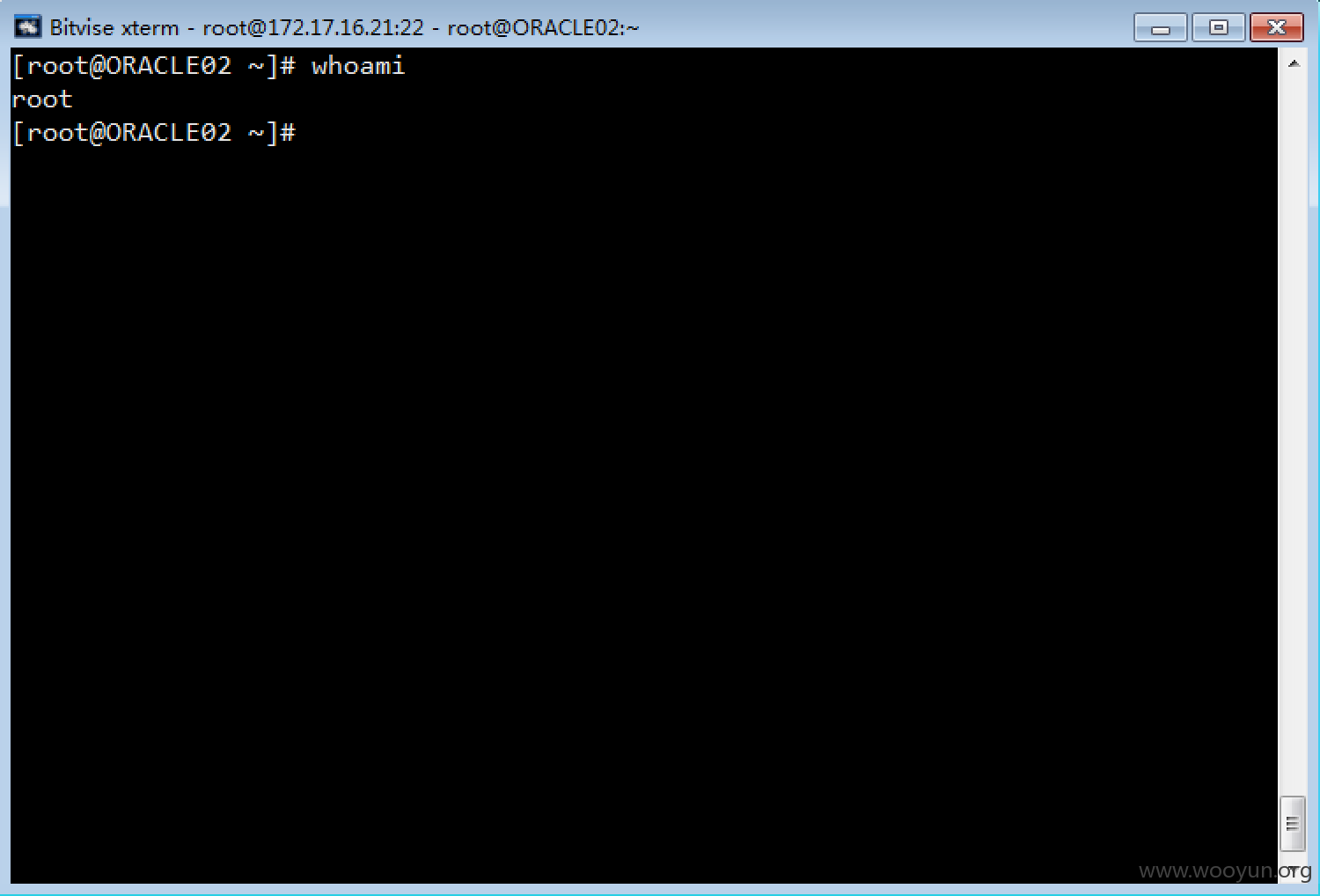
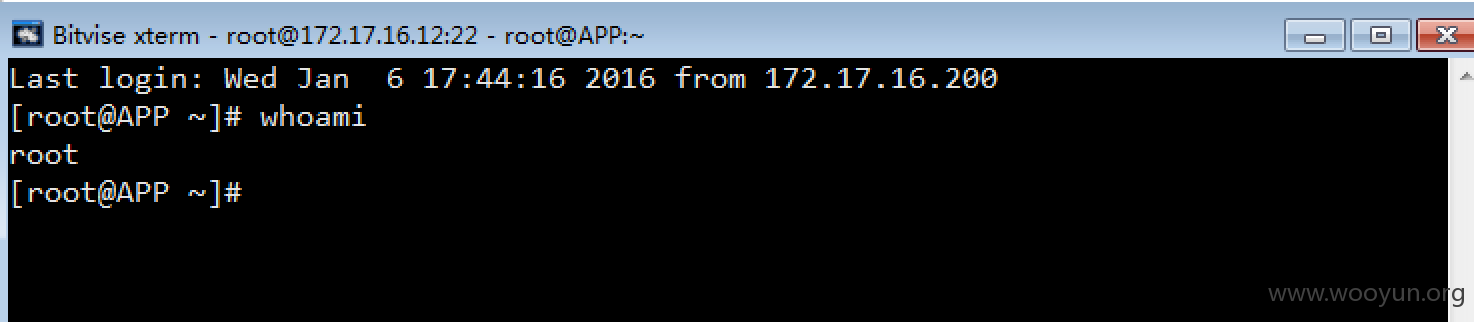
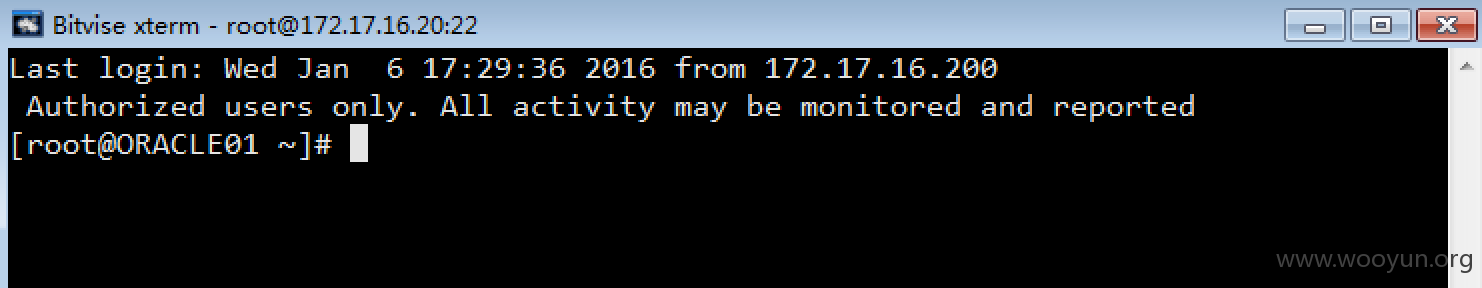
登陆vpn后收集内网信息对ssh进行爆破
四台内网机器沦陷两个oracle一个app的