001x今天看了下某IP下的C段,发现有魔秀的站点。显示的是moxiu.net。然后就用百度site:moxiu.net
这里是个后台 http://moxiu.net/mxadminv3/index.php?do=Login
整个页面没有验证码,也没有登录次数限制,而且有友好的报错提示,如下图


然后想了想,可以爆破。于是上burp,手动输入123456,在repeater里面没有看到报错信息,顿时出了一身冷汗,密码居然是123456
001x直接进入后台
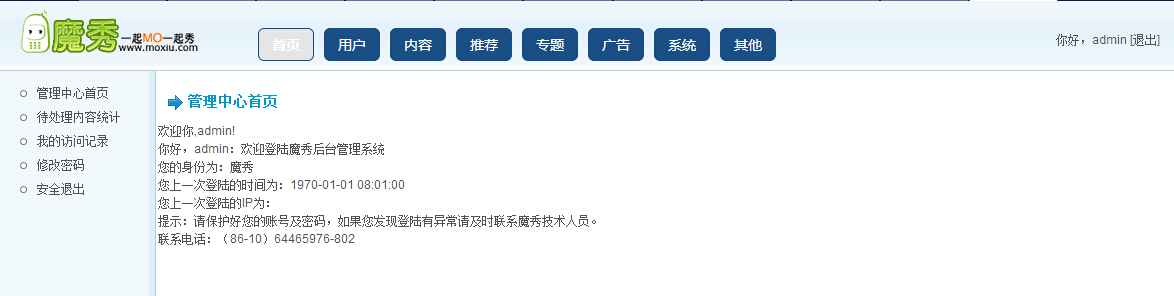
002x后台管理内容挺多的,这里是后台的管理。
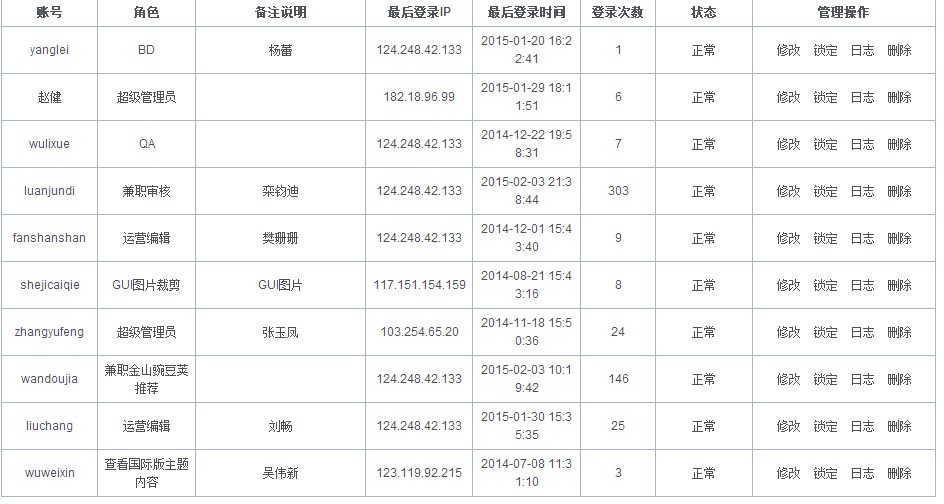
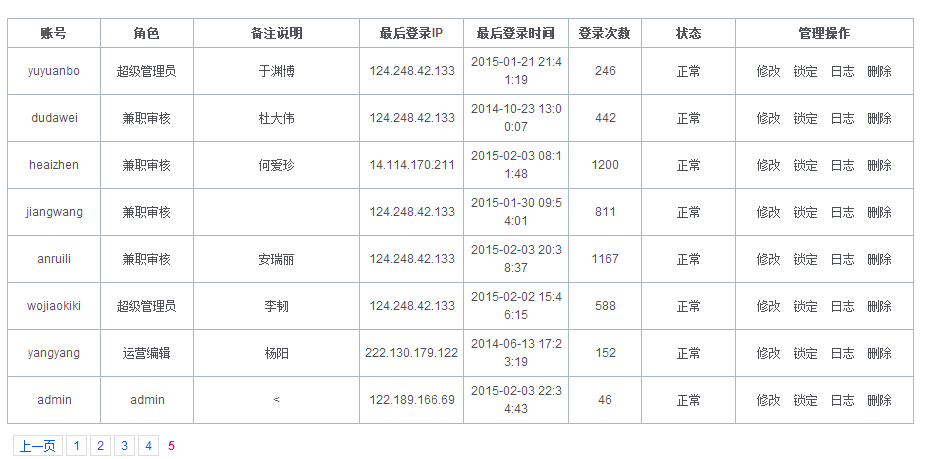
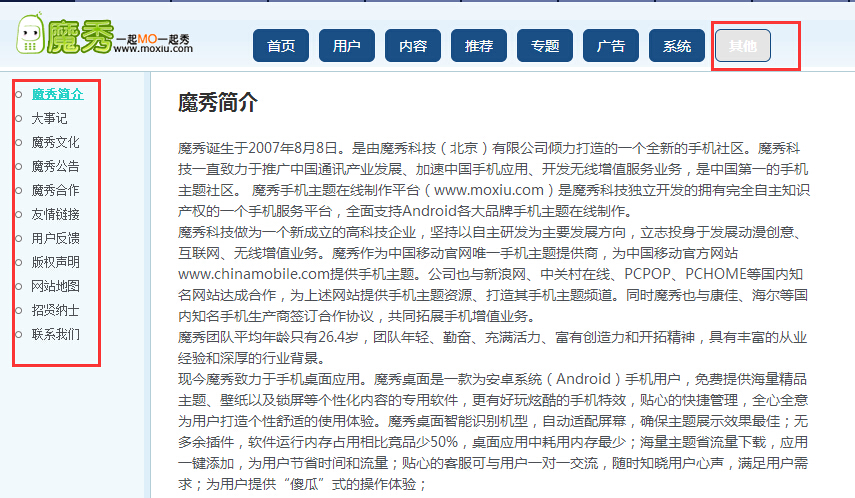
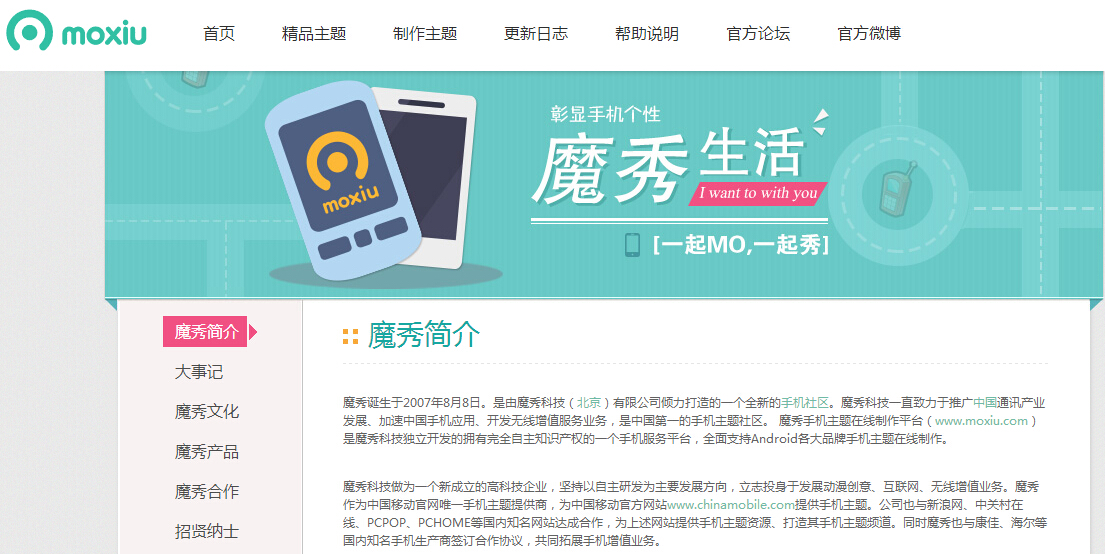
003x这里是官网的管理后台
004x最后一点是SQL注入,由于SQL注入地址是需要登录的,所以sqlmap使用时加上了cookie的值
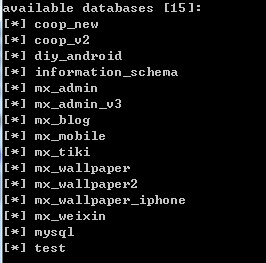
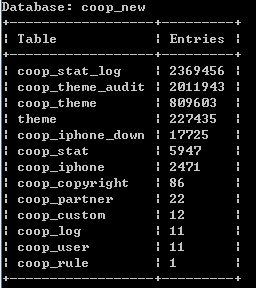
004x最后跑出的数据库如下