0x00 关键字
0x01 过程
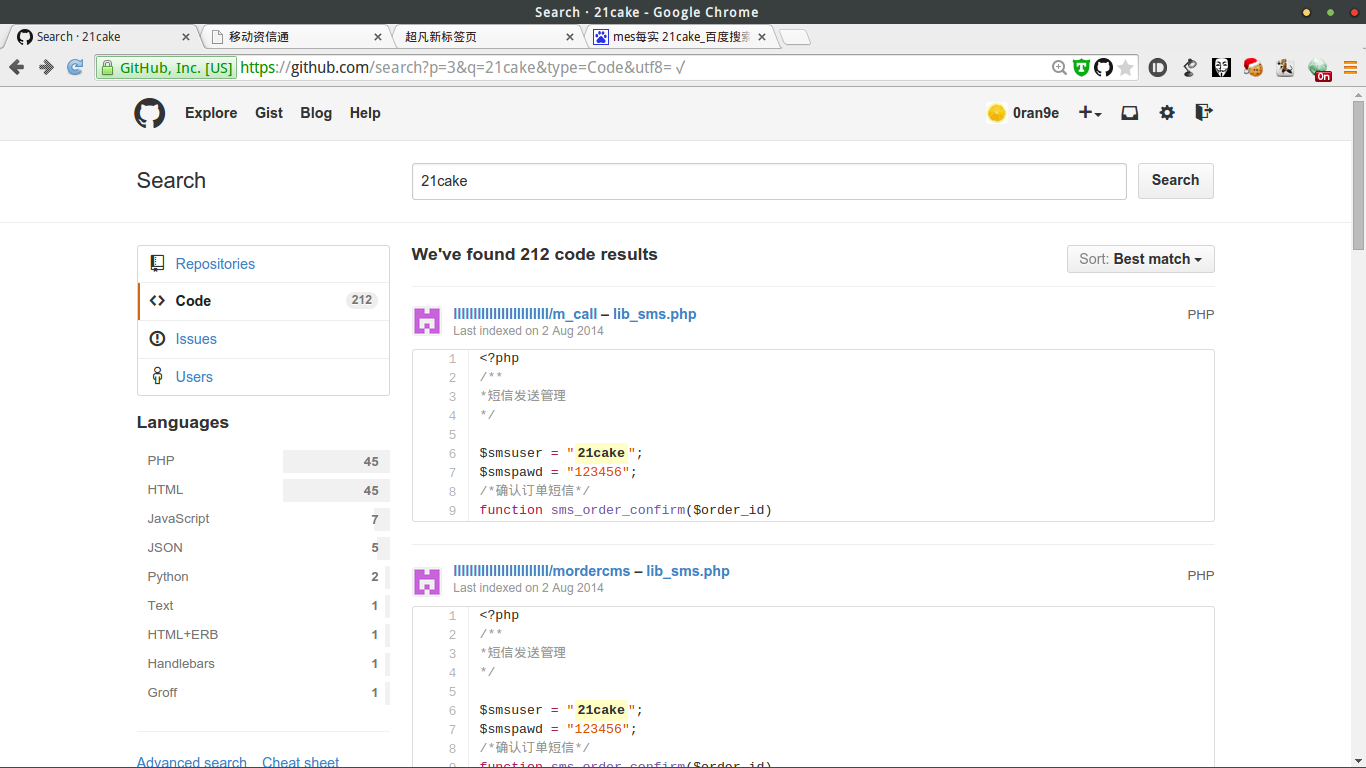
由于昨天提交了一个21cake的漏洞,出于习惯就上了一下github,搜索关键字 “21cake”
code那里好像有东西
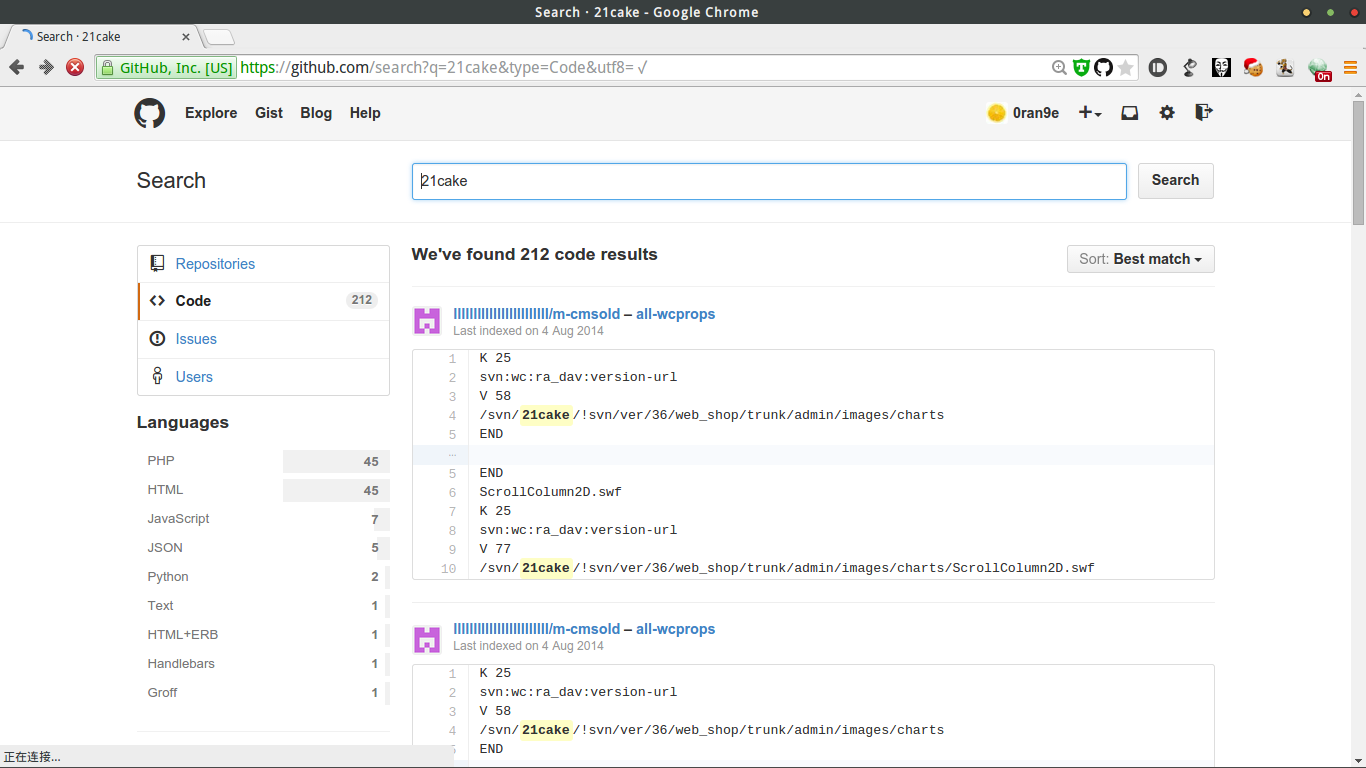
嗯?! (●′ω`●) svn,顺势看了下去
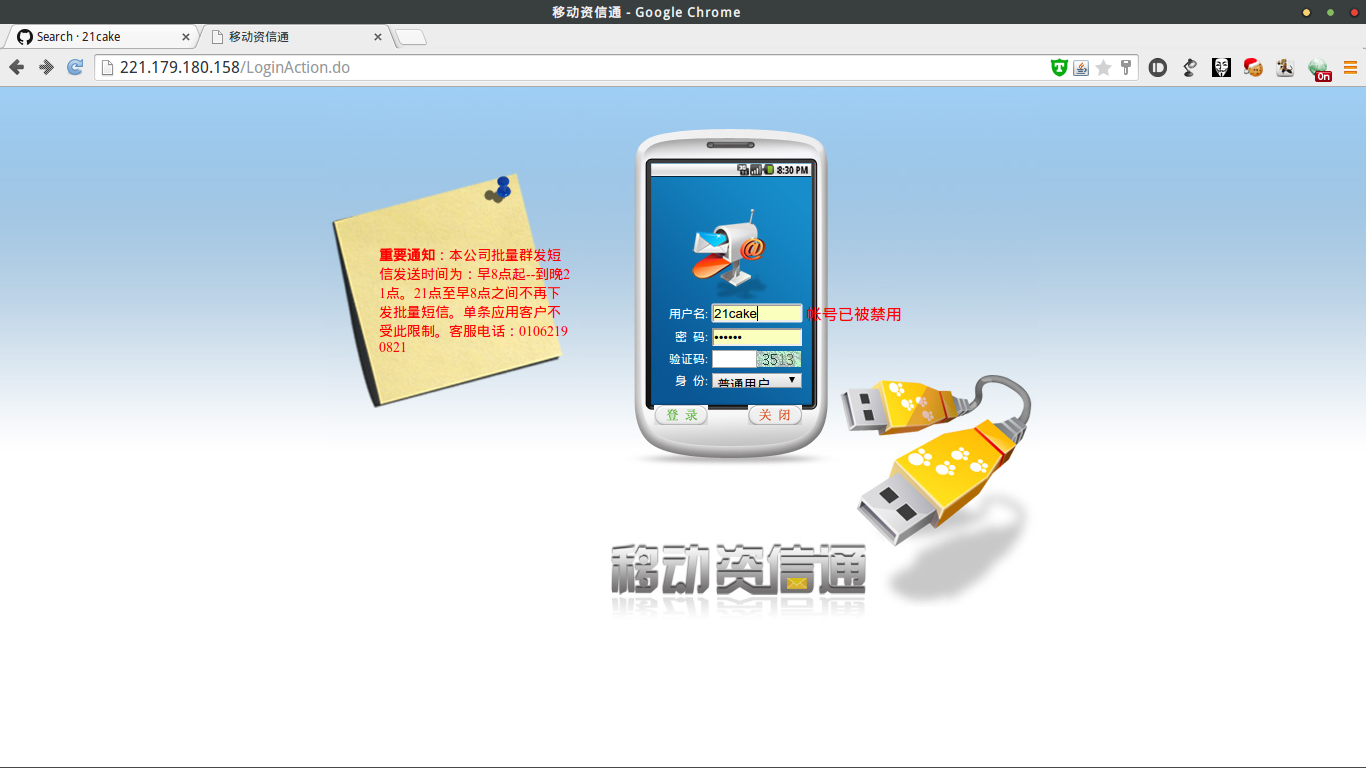
貌似是短信接口,登了一下发现账户被禁用
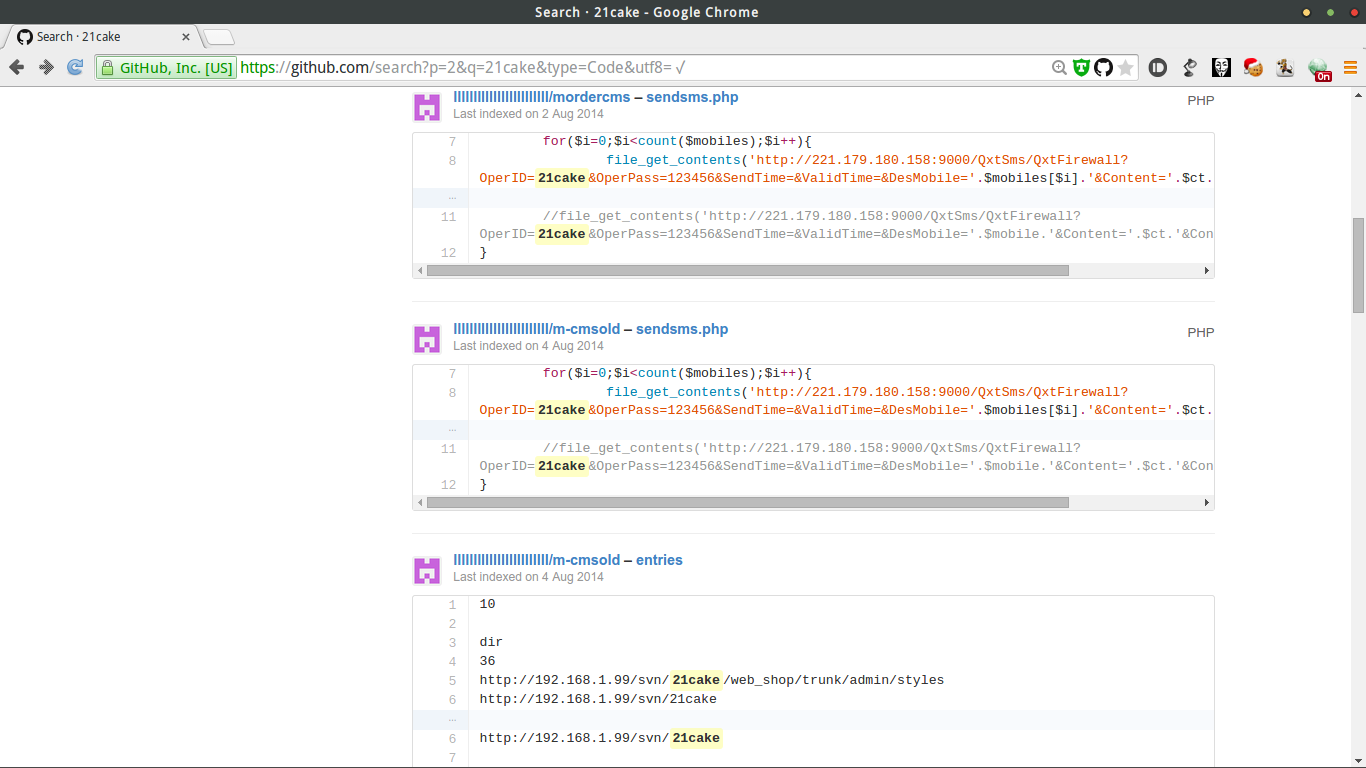
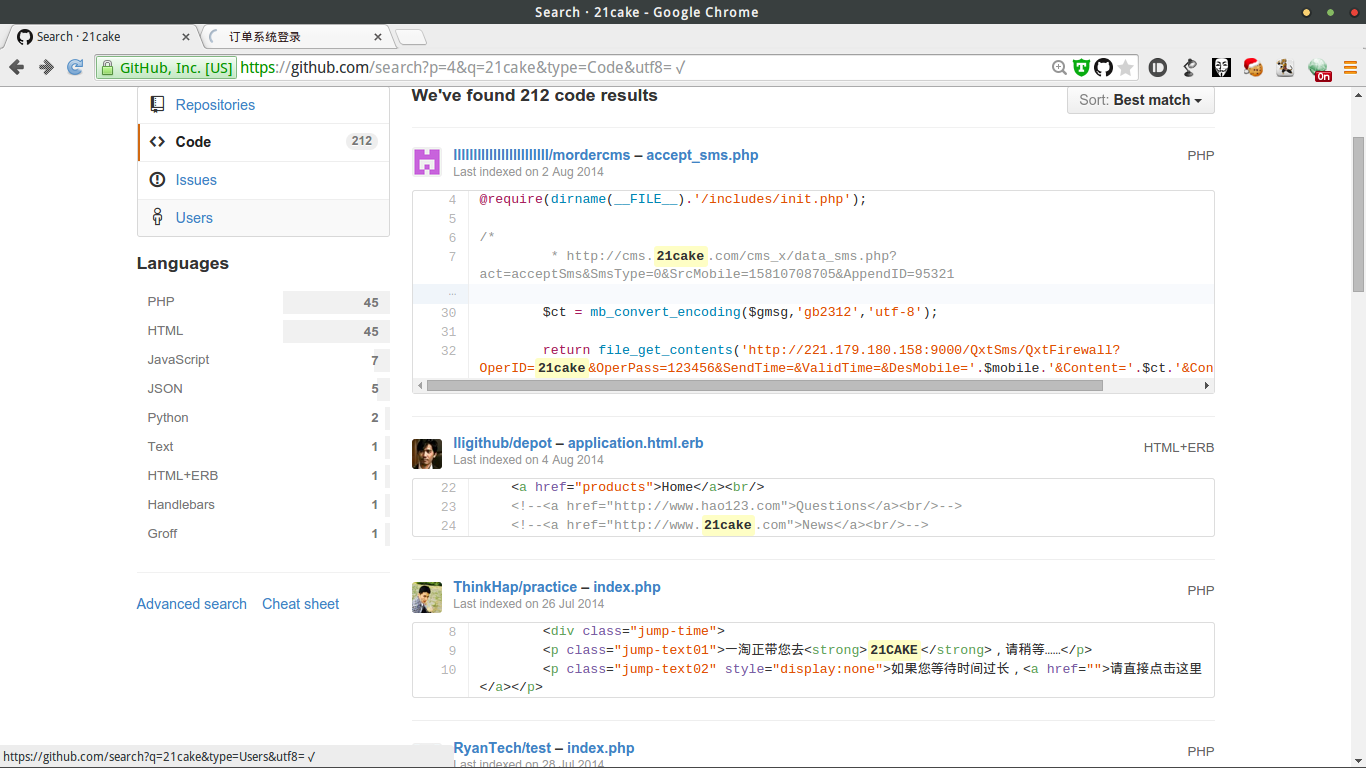
继续往下翻
直接进入作者的github主页
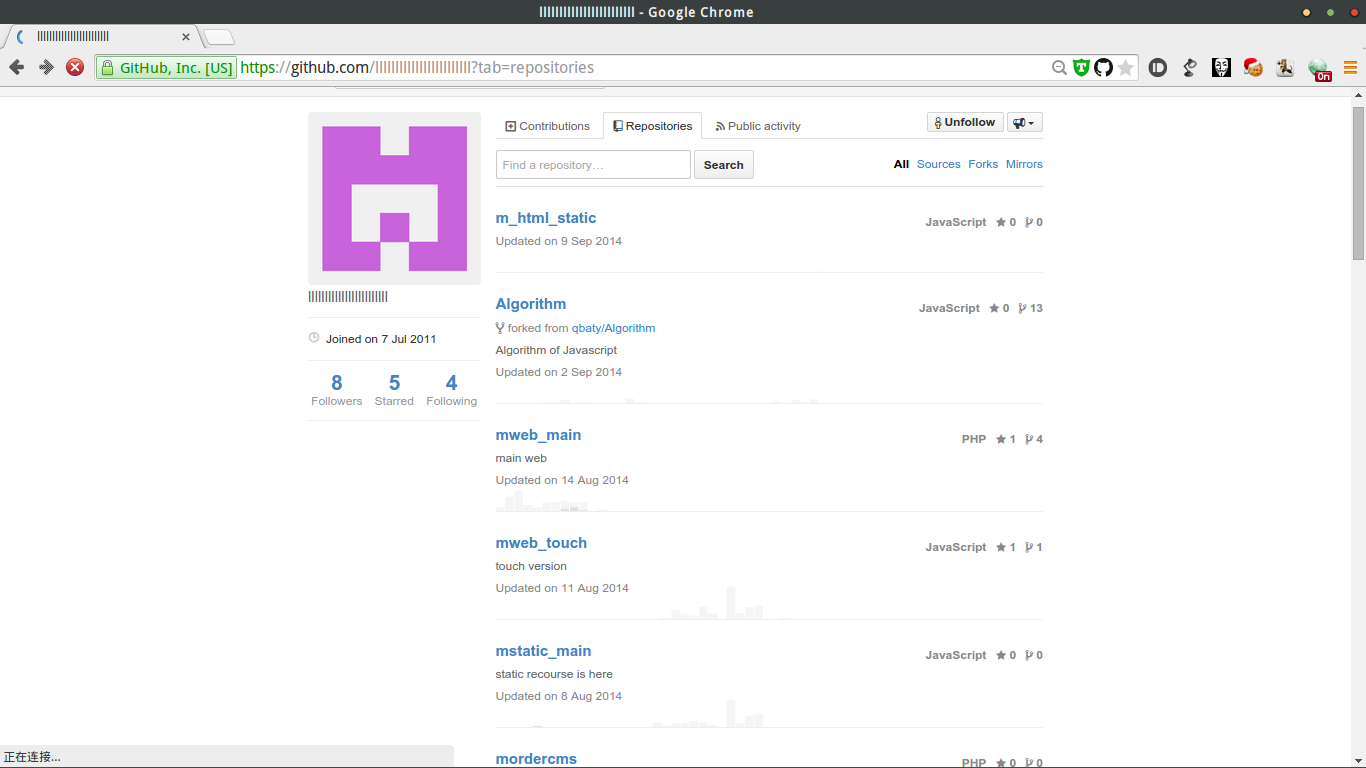
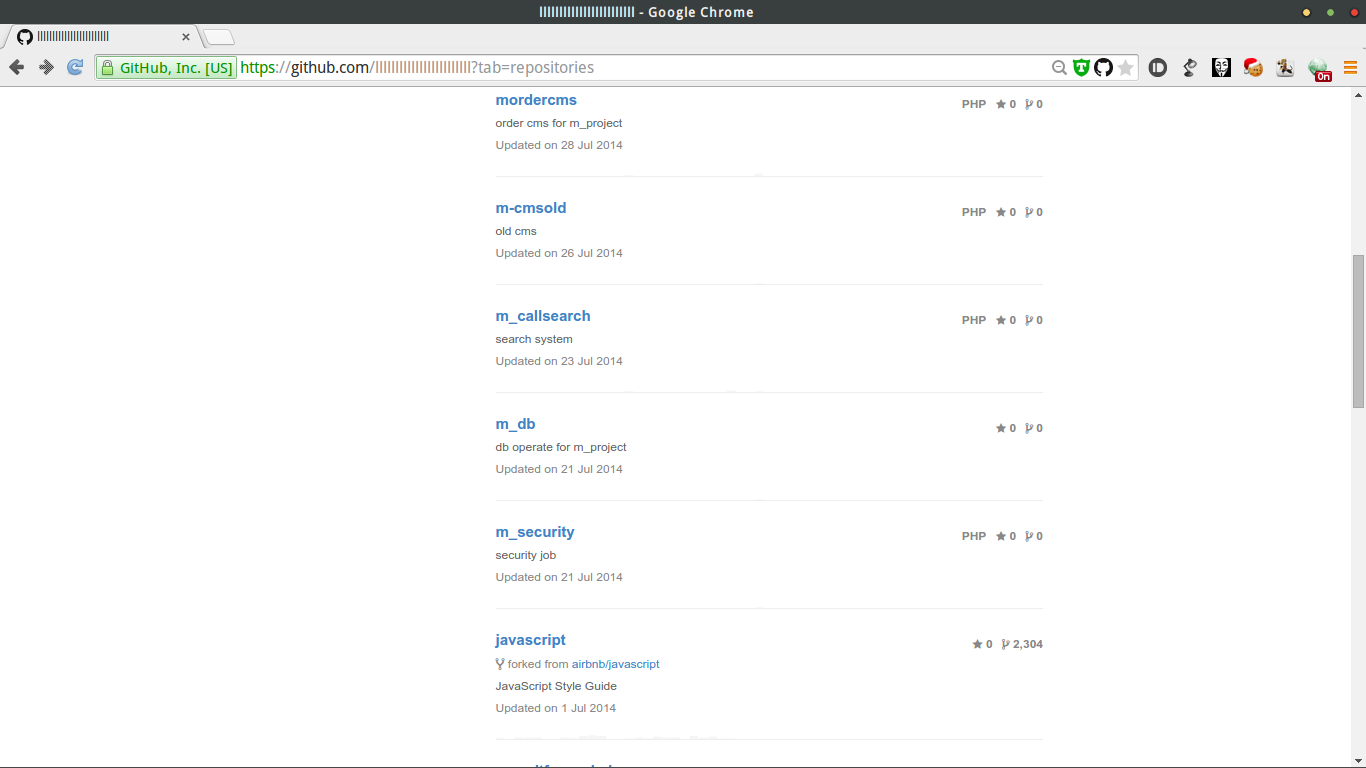
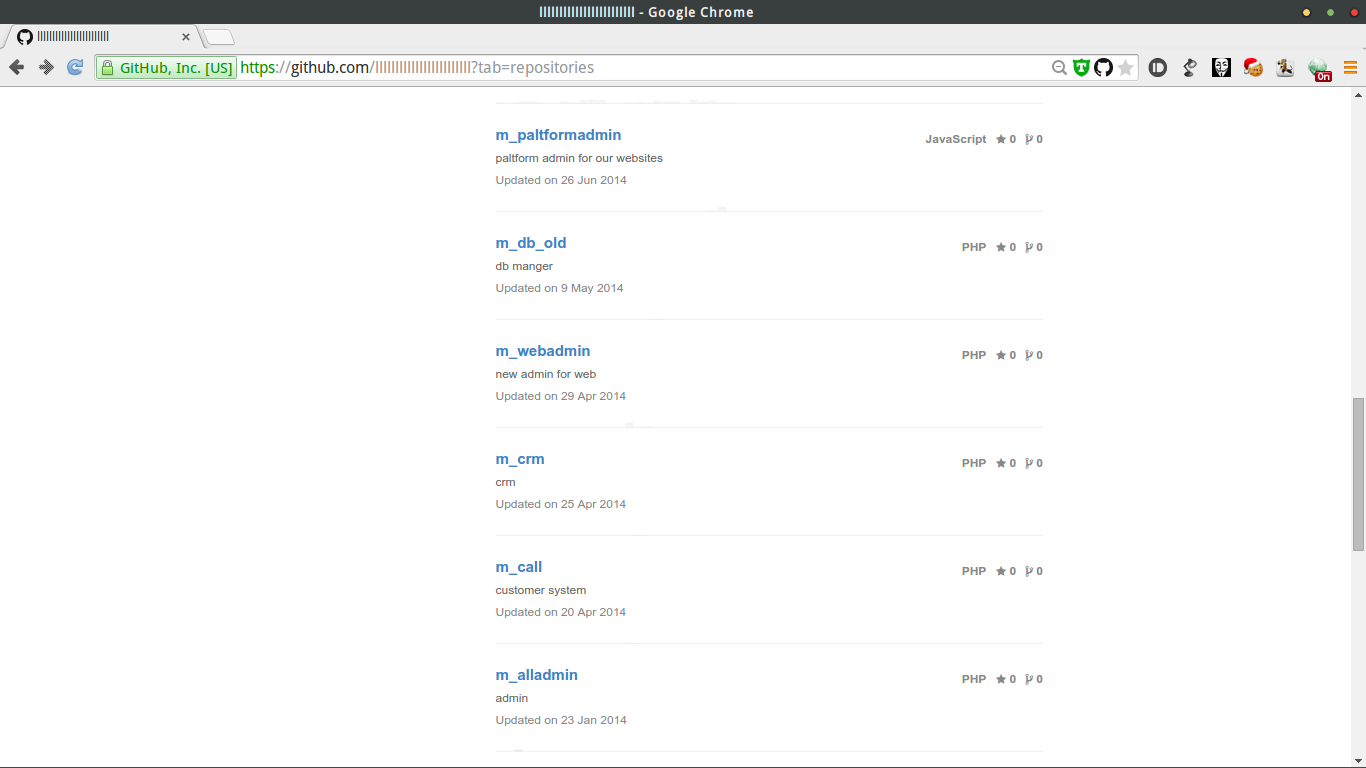
粗略看了下,源码属于www.mescake.com,加上之前看到@author 21Cake Dev Team于是就联系了一下21cake的工作人员,询问mes与21cake的联系,得知mes是他们在北京的团队
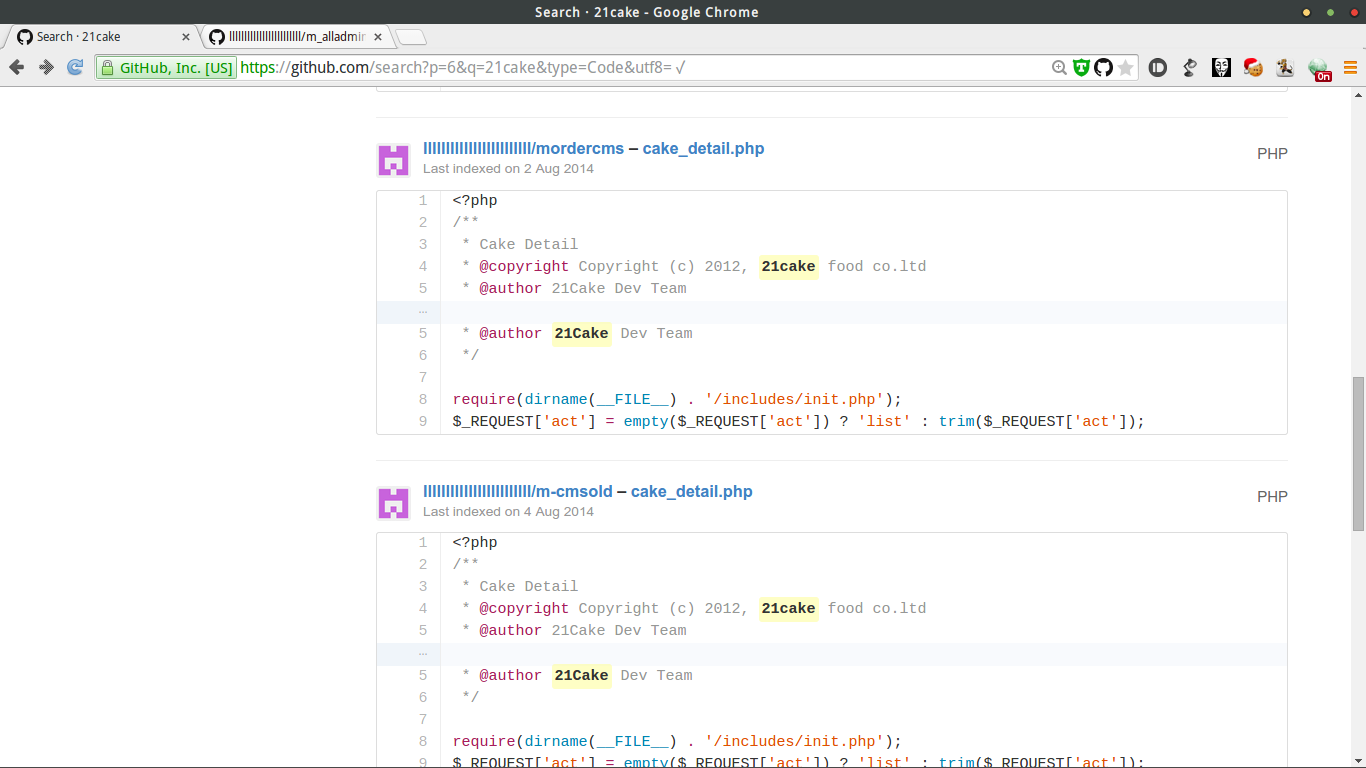
信息量略大,就用github自带的检索功能,搜索 pass, pwd ,admin,mes等关键字
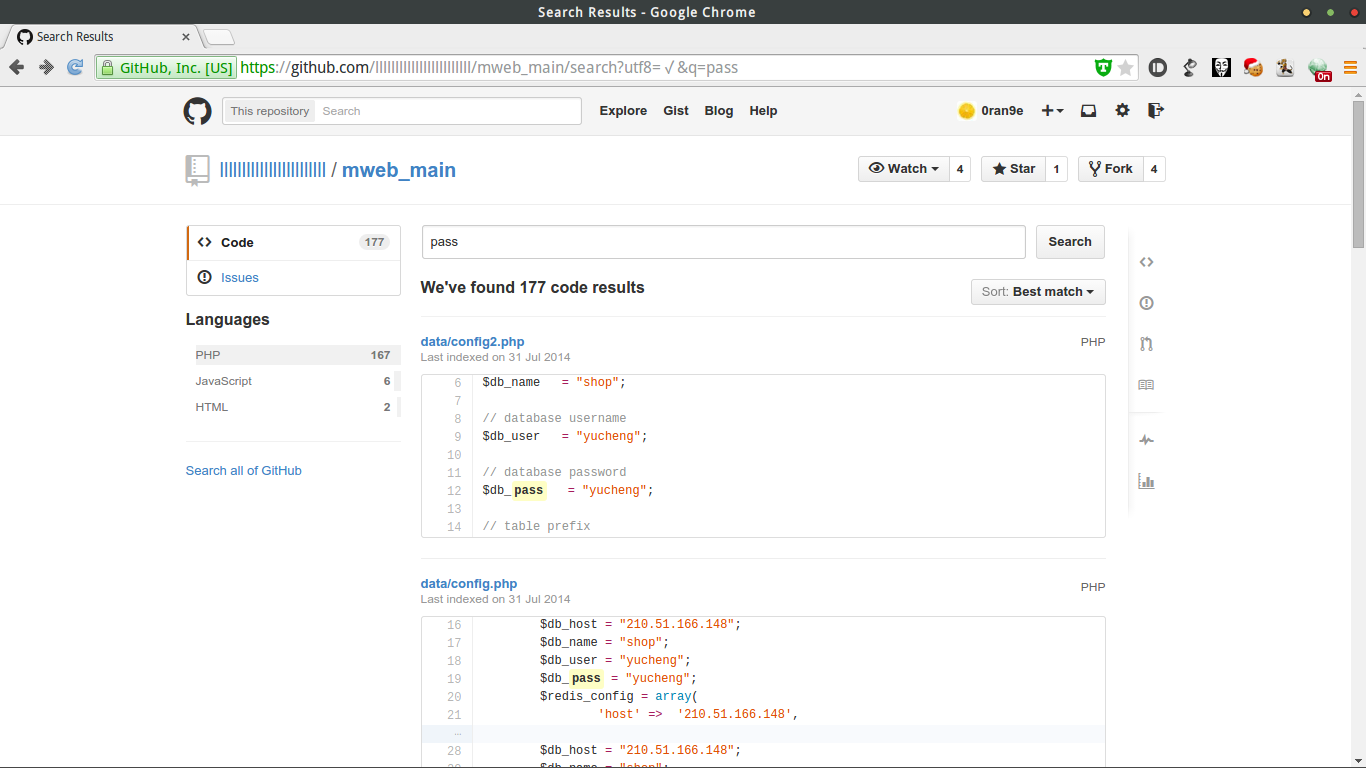
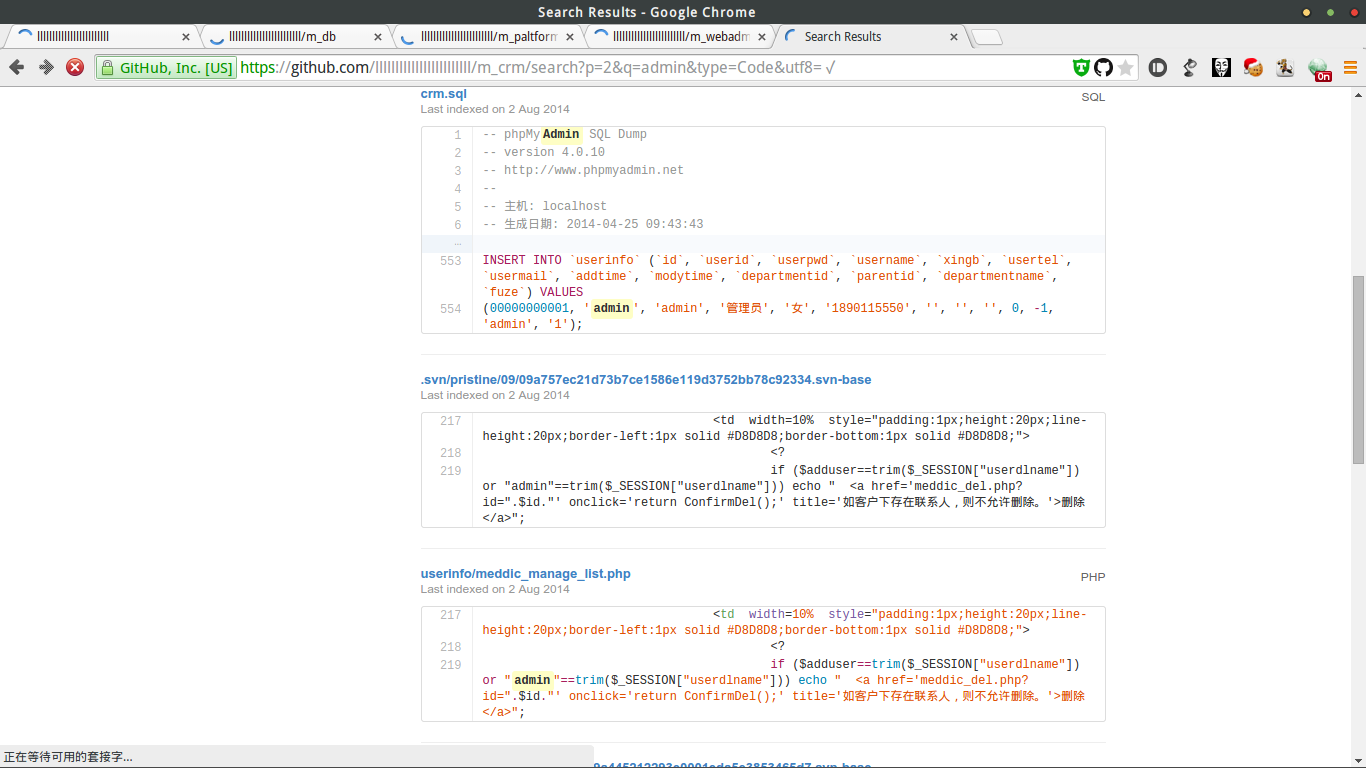
其中客服系统可以直接访问
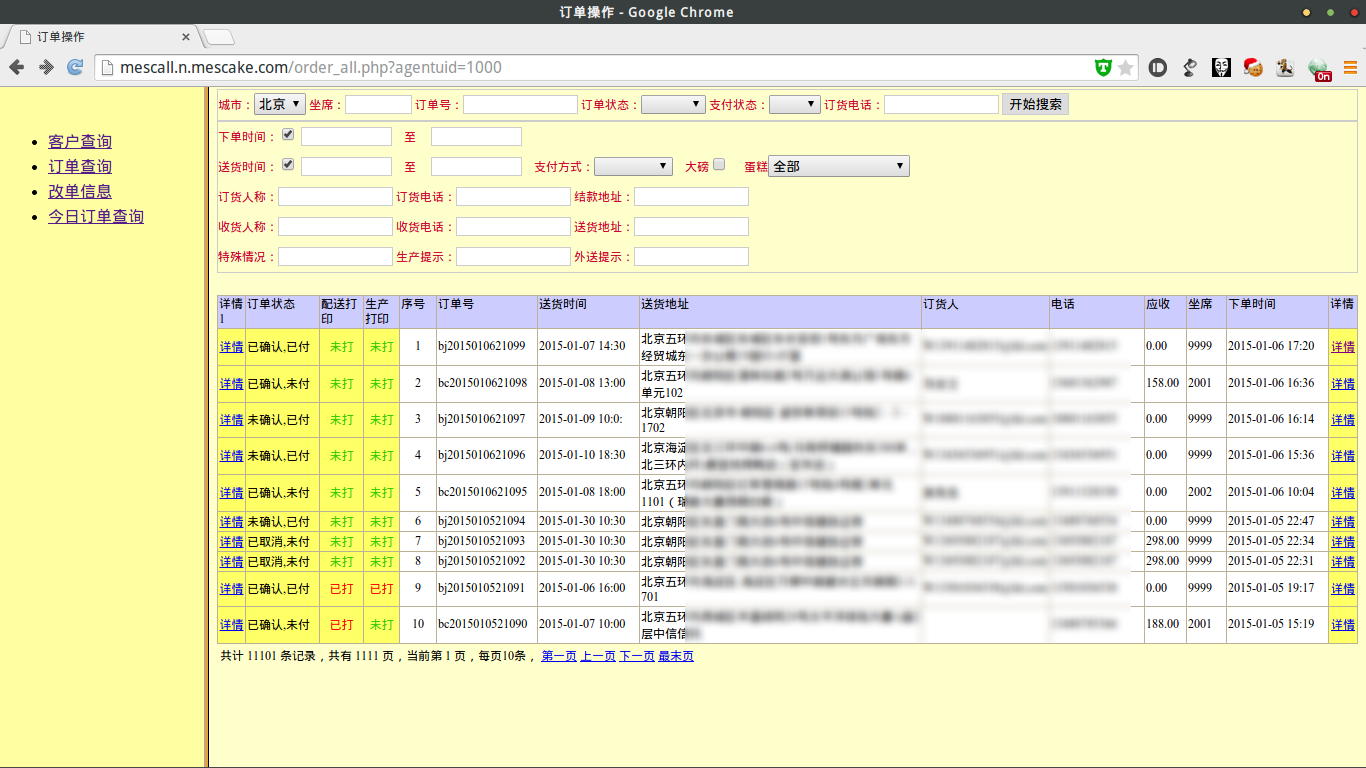
下面的好像涉及到加密算法
就贴这些吧















