PHPB2B某处sql注入
官网下载的最新版本
绕过全局防注入。
我们先看看全局防注入怎么写的。
以下是全局防注入用到的函数
其核心在于,对post和get传递过来的参数值进行了一次过滤
但是还是有不足的地方。
register.php
83-117行
代码比较长,其中比较关键的函数有
第96行
$memberfield->setParams();
看看setparams函数怎么写的
代码又臭又长,其实这个函数主要的功能就是把post过来的数据全部放入当前实例的params属性中,且params是一个数组。
也就是
$_POST[a]=1--->$this->params[a]=1
然后继续往下看
在第117行
调用了$member->Add()这个函数
跟踪看看。
函数代码比较长,所以我在关键地方做了注释。
总之就是会将$memberfield->params['data']['memberfield']这个参数传入到save函数中
而$memberfield->params['data']['memberfield']这个参数恰恰是由$memberfield->setParams();而得到值的,也就是我们可以直接post传入数据。
如图,为了演示方便,我把$memberfield->params['data']['memberfield']内容打印出来
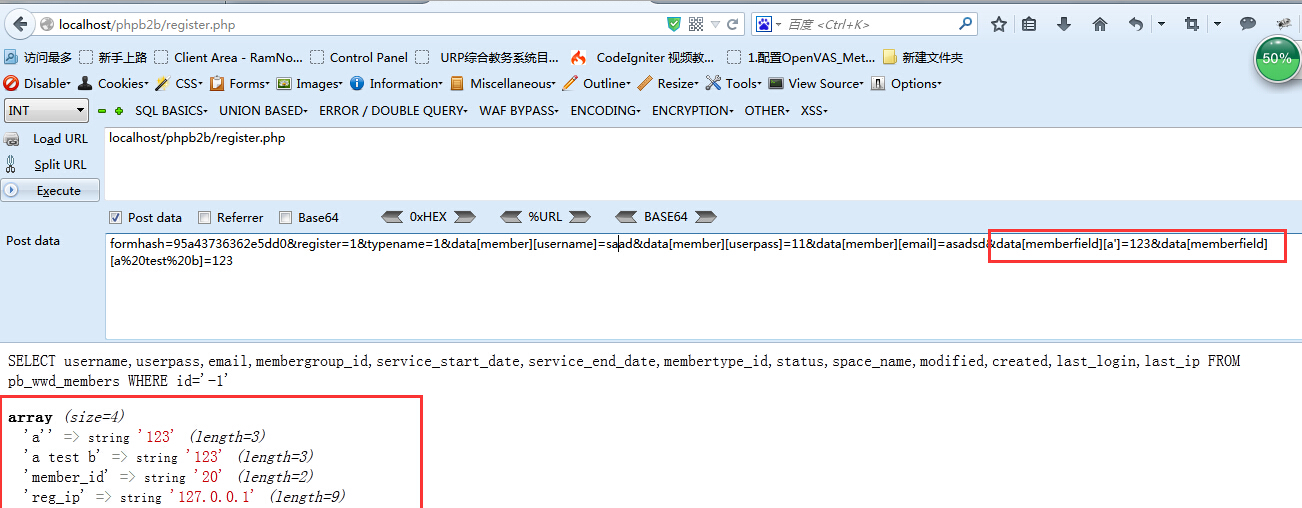
清楚了这些,我们再来看save函数究竟做了什么。
$id默认为空
所以最后拼接成的sql为
$cols是怎么来的?
原来是取出了post传递过来的参数的键名数组,然后用,分割成字符串。而键名是不在全局sql注入过滤中的,于是产生了注入。
然后我们打印出最后执行的select语句
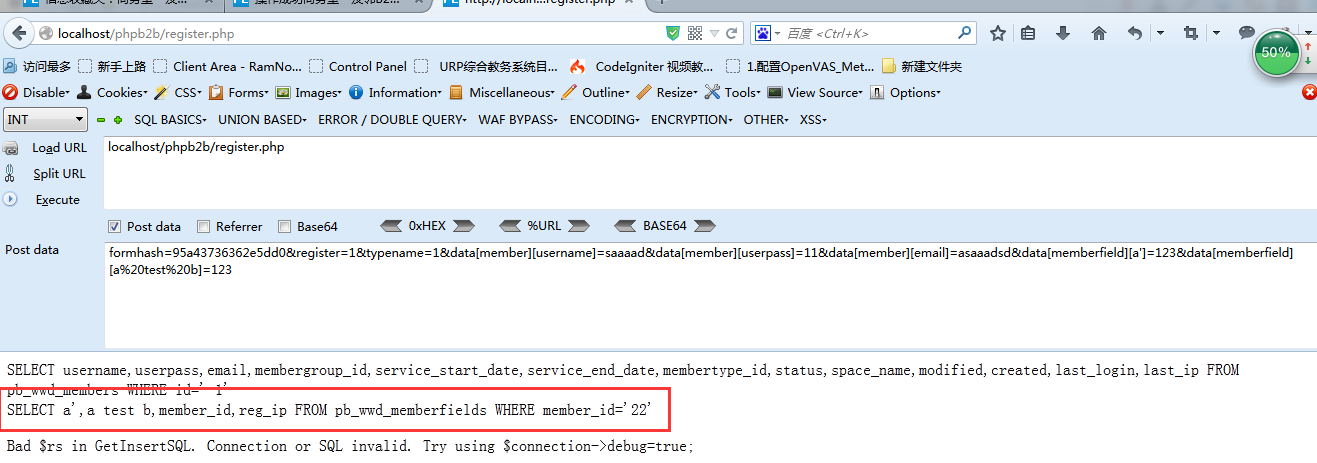
已经构成了注入了,如果要想盲注出管理员的密码,在这里就可以完成了。
但是因为程序员的疏忽,这个我们可以做得更多。
我们来看一下完整的save函数
跟着走到_adodb_getinsertsql函数
这个函数也特别长
在libraries/adodb/adodb-lib.inc.php中
762-902行
代码太长,我就不慢慢分析了。
这个函数的主要功能就是匹配出先前那个select语句中的各个字段以及表名。然后对数据库中该表做一个插入操作。
为了更直观表示,我将语句都打印出来。
我们直接来插入一条管理员数据,把自己的账号提成管理员吧。
post提交
成功添加了一条管理员记录。
账号是123dba密码是11
ps:
因为表前缀是默认随机生成的,所以必须先通过盲注information这个数据库中的tables表,拿到表前缀,而后才能拿到管理员权限。
不对对于拥有注入来说,不都是洒洒水么
PHPB2B某处sql注入
官网下载的最新版本
绕过全局防注入。
我们先看看全局防注入怎么写的。
以下是全局防注入用到的函数
其核心在于,对post和get传递过来的参数值进行了一次过滤
但是还是有不足的地方。
register.php
83-117行
代码比较长,其中比较关键的函数有
第96行
$memberfield->setParams();
看看setparams函数怎么写的
代码又臭又长,其实这个函数主要的功能就是把post过来的数据全部放入当前实例的params属性中,且params是一个数组。
也就是
$_POST[a]=1--->$this->params[a]=1
然后继续往下看
在第117行
调用了$member->Add()这个函数
跟踪看看。
函数代码比较长,所以我在关键地方做了注释。
总之就是会将$memberfield->params['data']['memberfield']这个参数传入到save函数中
而$memberfield->params['data']['memberfield']这个参数恰恰是由$memberfield->setParams();而得到值的,也就是我们可以直接post传入数据。
如图,为了演示方便,我把$memberfield->params['data']['memberfield']内容打印出来

清楚了这些,我们再来看save函数究竟做了什么。
$id默认为空
所以最后拼接成的sql为
$cols是怎么来的?
原来是取出了post传递过来的参数的键名数组,然后用,分割成字符串。而键名是不在全局sql注入过滤中的,于是产生了注入。
然后我们打印出最后执行的select语句

已经构成了注入了,如果要想盲注出管理员的密码,在这里就可以完成了。
但是因为程序员的疏忽,这个我们可以做得更多。
我们来看一下完整的save函数
跟着走到_adodb_getinsertsql函数
这个函数也特别长
在libraries/adodb/adodb-lib.inc.php中
762-902行
代码太长,我就不慢慢分析了。
这个函数的主要功能就是匹配出先前那个select语句中的各个字段以及表名。然后对数据库中该表做一个插入操作。
为了更直观表示,我将语句都打印出来。
我们直接来插入一条管理员数据,把自己的账号提成管理员吧。
post提交
成功添加了一条管理员记录。
账号是123dba密码是11
ps:
因为表前缀是默认随机生成的,所以必须先通过盲注information这个数据库中的tables表,拿到表前缀,而后才能拿到管理员权限。
不对对于拥有注入来说,不都是洒洒水么




