1.撞库
万达百货scm供应链管理后台:
http://124.238.218.78
问题说明:
登录该系统时,如果用户名不存在会提示用户不存在,即存在用户名猜解。
研究发现登录时用户名参数为userno,于是猜测是类似员工号之类的数字帐号, 于是从1,11,111,1111,11111,111111测试,发现111111是一个合法用户,于是继续猜测userno为6位数字,于是遍历了111000~119999之间的用户,发现除了111111之外,111093,111150,112759,112983,113163也是存在的用户。
可登录的用户名遍历出了几个,进一步猜测密码。大概1w个请求左右,成功猜出一个用户:
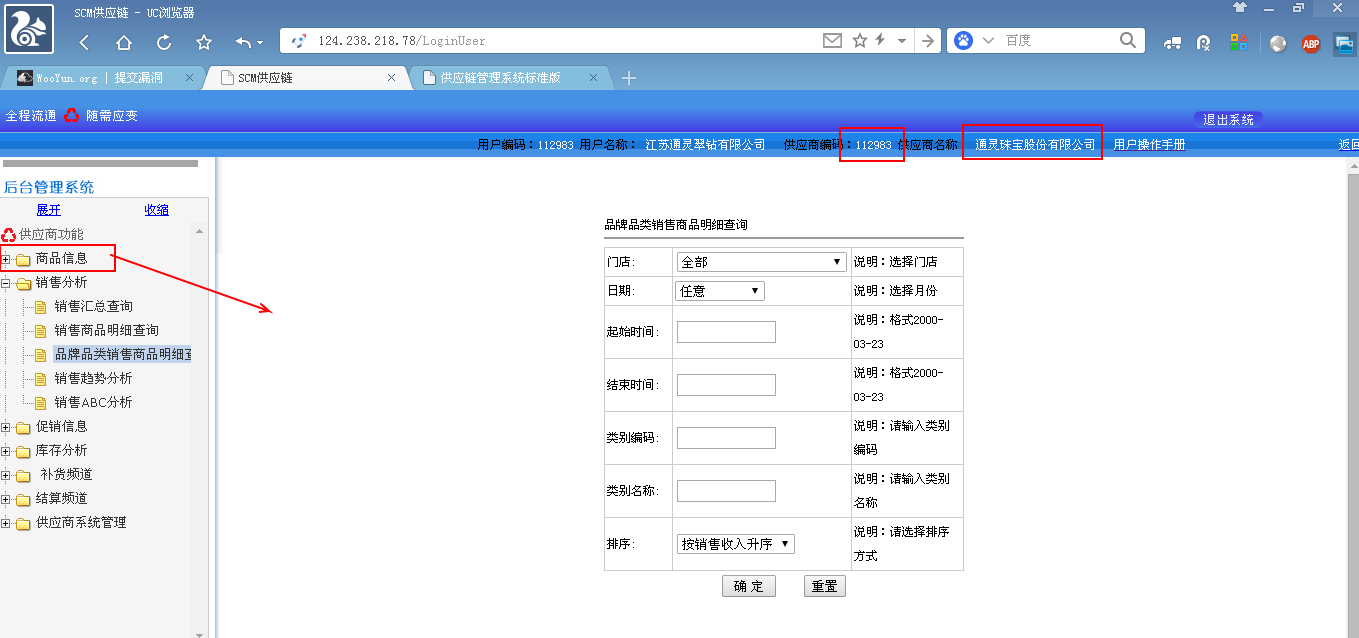
112983,密码123321。停止猜测密码。
该用户登录系统之后的截图:
2.sql注入
上面的截图中也指出,商品信息的查询功能存在sql注入。
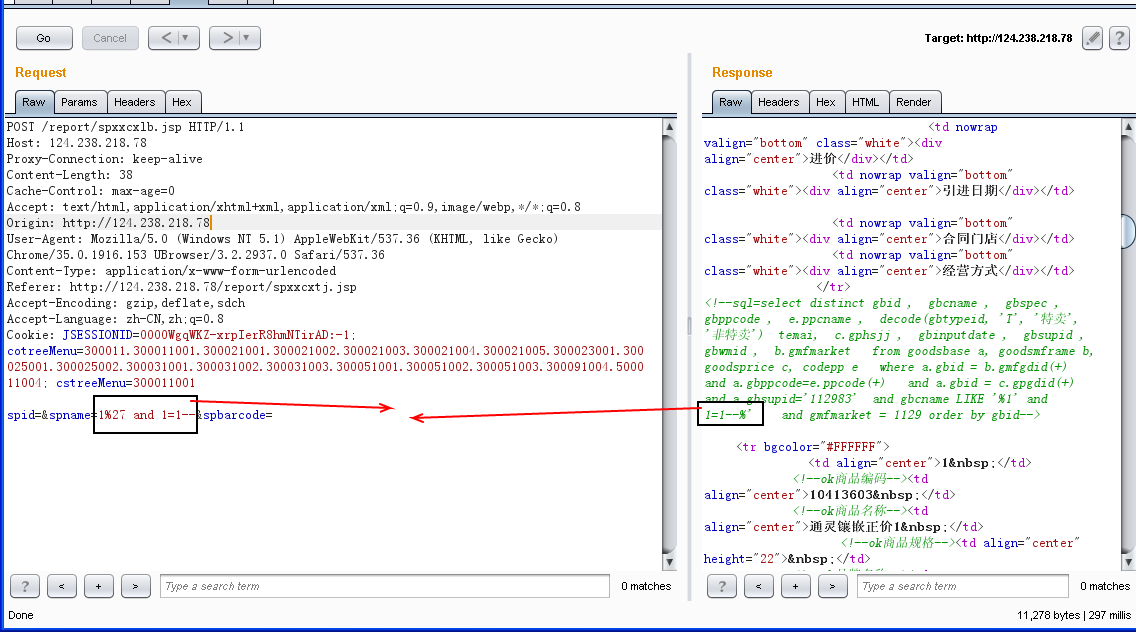
丢给sqlmap(注意*号前后以及cookie):
一百多张表,枚举了几个之后很无聊暂停了。




