漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0155568
漏洞标题:游戏嘎嘎多个SQL注入导致大量用户及敏感信息泄露
相关厂商:游戏嘎嘎
漏洞作者: 路人甲
提交时间:2015-11-28 00:58
修复时间:2016-01-12 01:00
公开时间:2016-01-12 01:00
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-28: 积极联系厂商并且等待厂商认领中,细节不对外公开
2016-01-12: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
游戏嘎嘎大量用户及敏感信息泄露
详细说明:
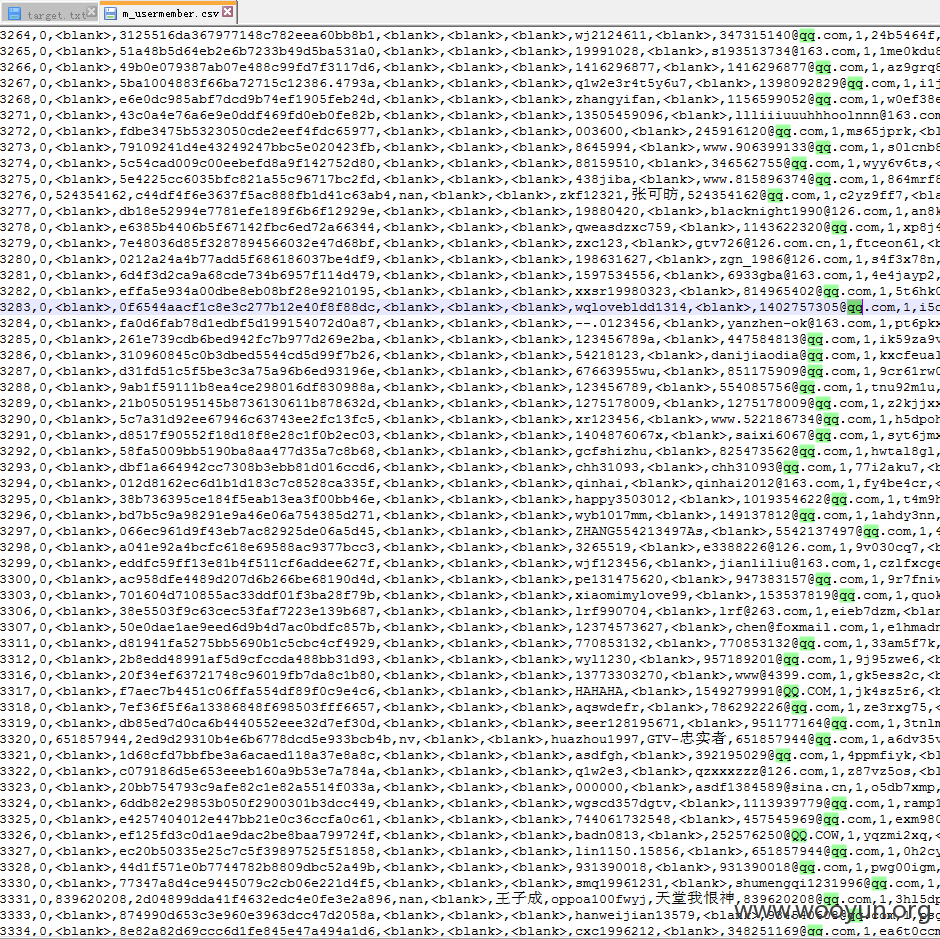
问题很严重:35万用户信息,MD5密码,其中大量默认密码,大量充值消费记录等,根本停不下来
http://www.youxigaga.com:80/ddt_login_do.php (username)
http://www.youxigaga.com:80/fast_login_do.php (username)
http://www.youxigaga.com:80/forget_do.php (username)
http://www.youxigaga.com:80/login_do.php (username)
http://www.youxigaga.com:80/register_do.php (username)
http://www.youxigaga.com:80/sub_req.php (m_id)
http://www.youxigaga.com:80/wls/list_new.php (p_id)
漏洞证明:
修复方案:
过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝