漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0153317
漏洞标题:锐捷网络弱口令,可重启、控制vpn、网络等,查看管理密码
相关厂商:ruijie.com.cn
漏洞作者: 莫里
提交时间:2015-11-17 23:10
修复时间:2015-11-25 09:00
公开时间:2015-11-25 09:00
漏洞类型:基础设施弱口令
危害等级:高
自评Rank:15
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-17: 细节已通知厂商并且等待厂商处理中
2015-11-25: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
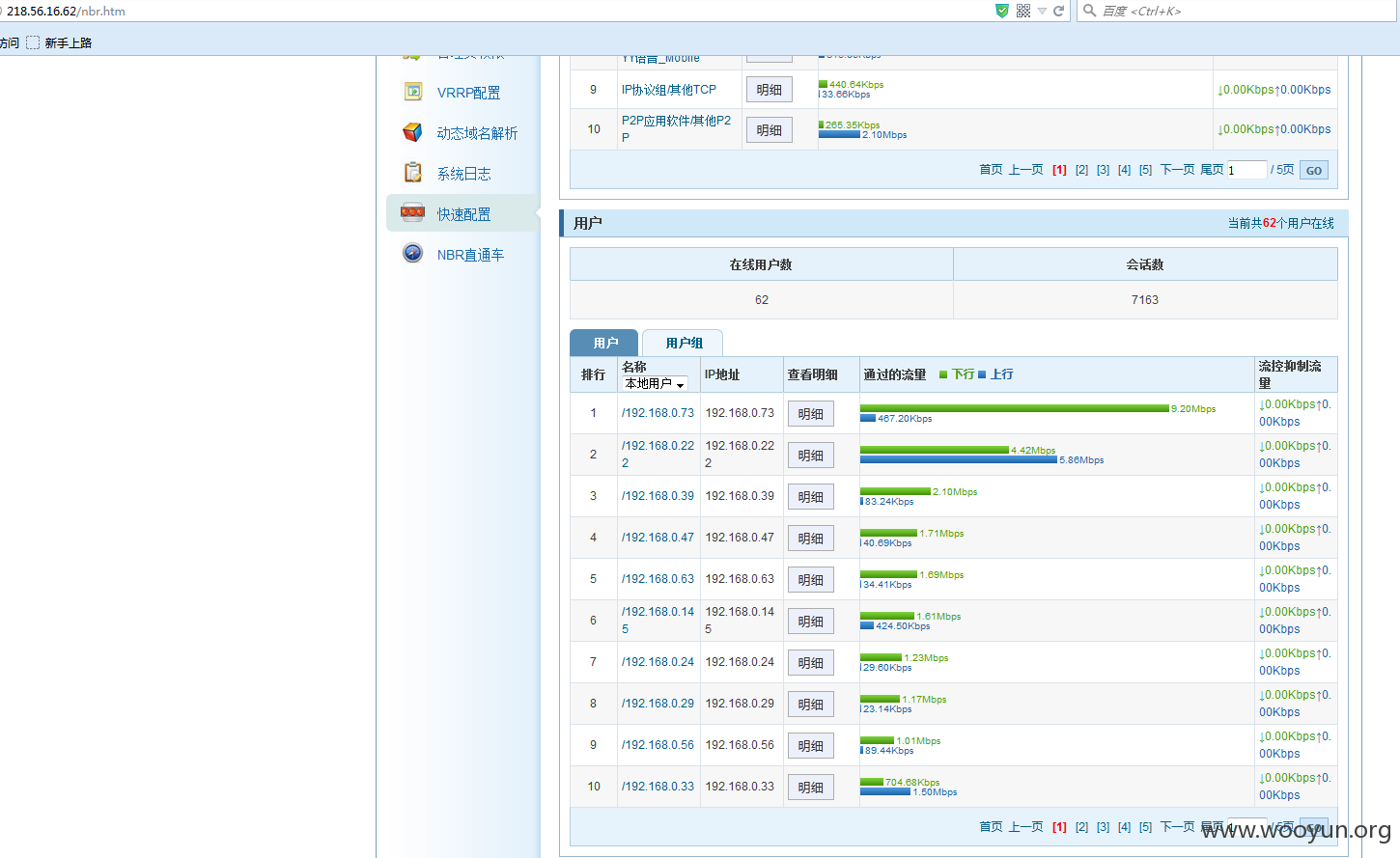
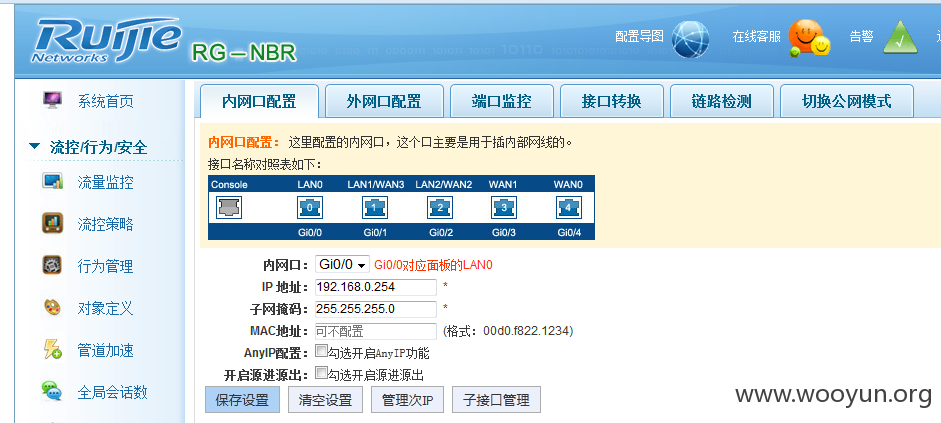
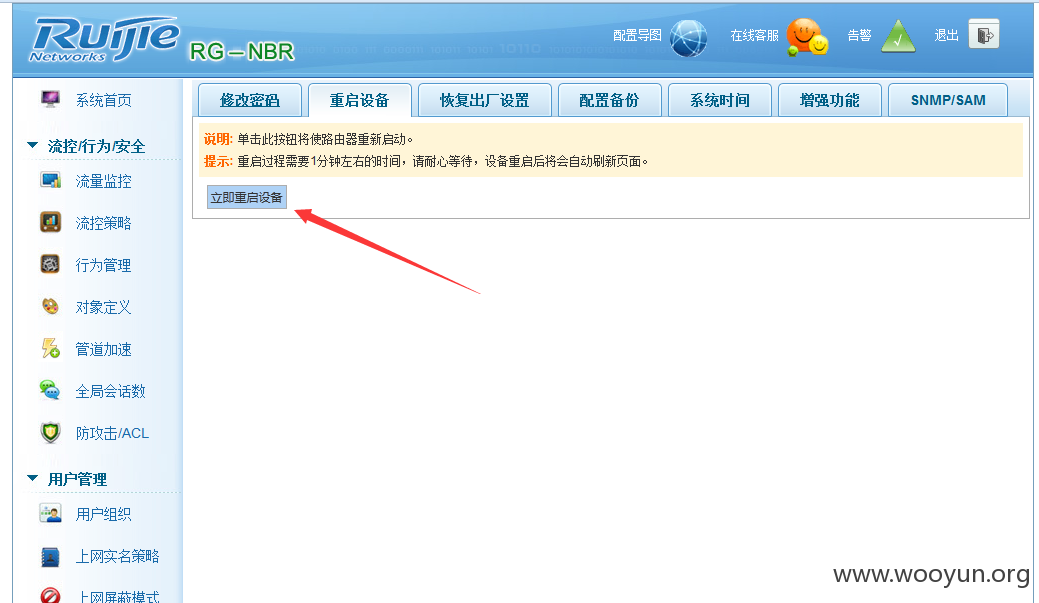
锐捷网络弱口令,可重启、控制vpn、网络等,查看管理密码,可配置vpn进入内网
详细说明:
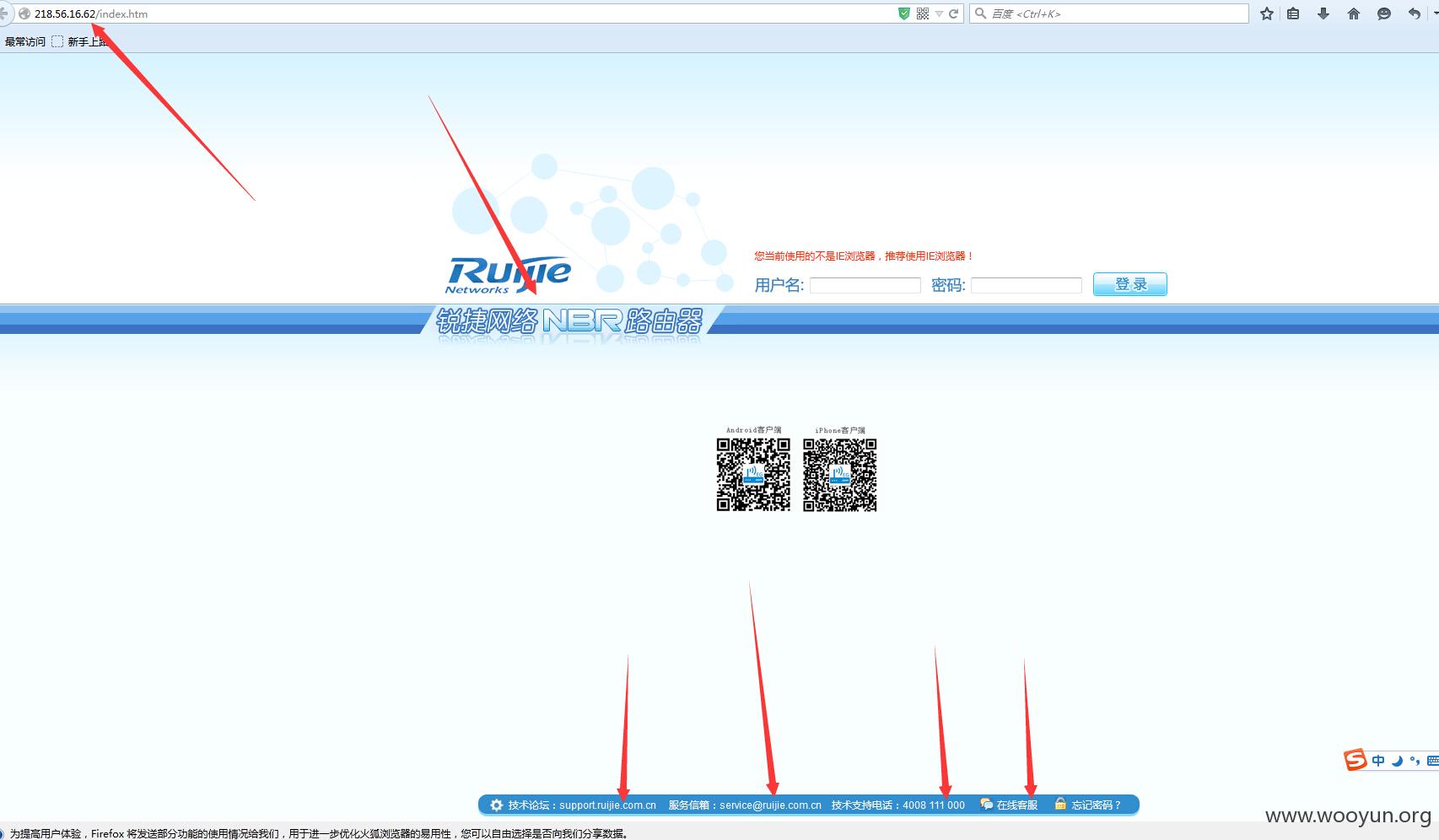
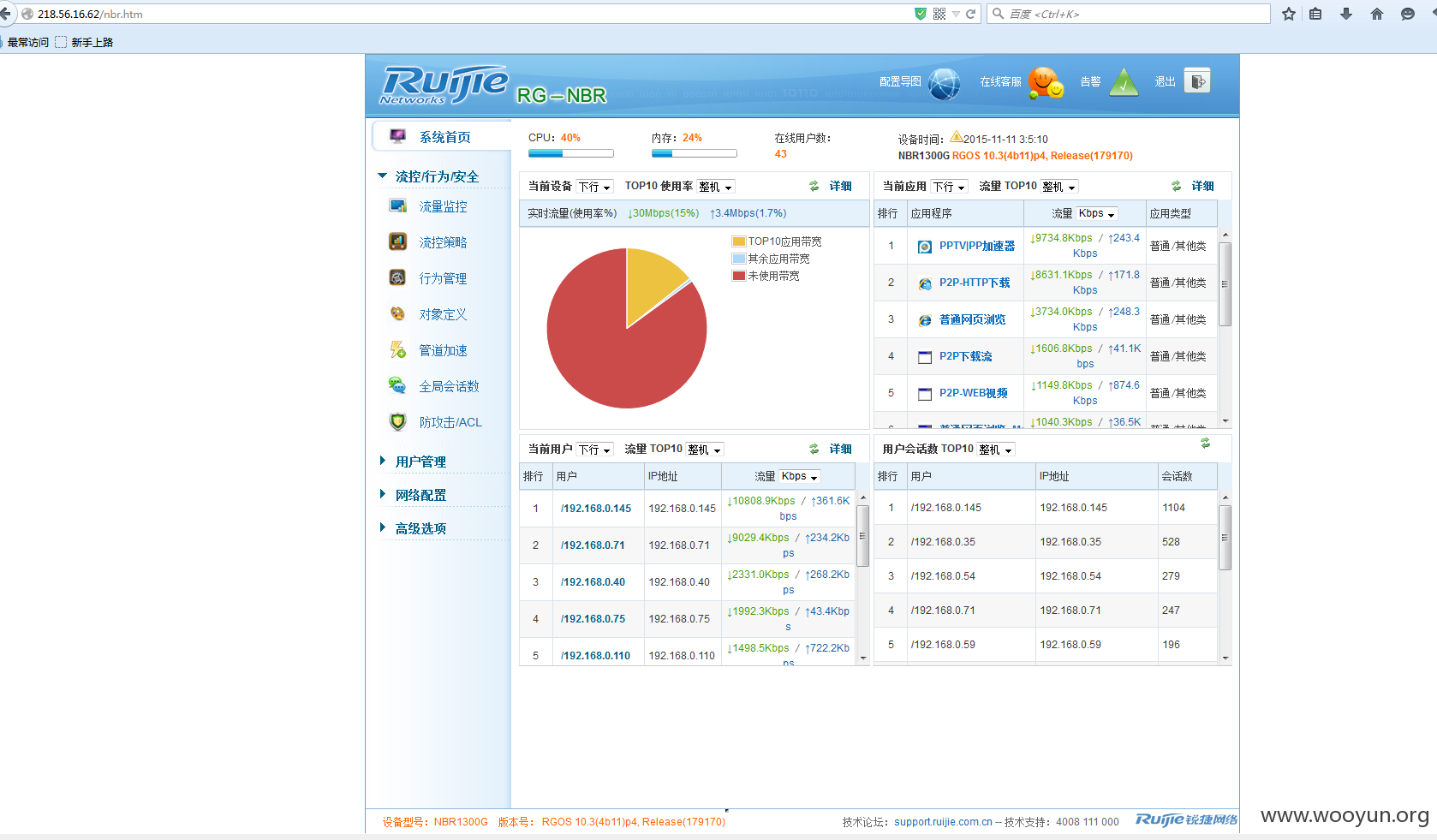
扫描ip 80端口
http://218.56.16.62
尝试了下admin amdin 还真过了
/人力资源部 张三 888 192.168.1.59 00-23-AE-86-B3-E9 Y
/财务部 李四 888 192.168.1.9-192.168.1.12 Y
/研发部/研发5部 王五 888 192.168.1.29 00-87-EF-12-4F-24 N
配置信息
!
version RGOS 10.3(4b11)p4, Release(179170)(Thu Oct 16 16:20:24 CST 2014 -ngcf61)
flow-audit enable
no attack-block enable
attack-block unblock 60
attack-block threshold drop-kbps 10000
attack-block threshold drop-pps 5000
no nat-log enable
feedback frequency 60
layer23 classify enable
identify-application enable
identify-application terminate enable
identify-application sig-rule enable
!
identify-application custom-group TC_AD_Key
app-add WEBӦ��
app-add HTTP����
app-add P2P-HTTP����
app-add ���ع���_MOBILE
!
webmaster level 0 username admin password 7 04361c0b370d
!
!
http update mode auto-update
http update server 0.0.0.0 port 80
http update time daily 22:37
http update auto-update route-db character-db url-db feedback content-db
dev-audit enable
!
time-range any
periodic Daily 0:00 to 23:59
!
mail-service enable
!
dns-proxy
!
!
route-map Gi0/0 permit 18
match ip address 18
set ip next-hop 218.56.16.61
set interface GigabitEthernet 0/4
!
!
!
!
specify interface GigabitEthernet 0/3 wan
specify interface GigabitEthernet 0/4 wan
web-coding gb2312
!
no service password-encryption
ip nat-log on
ip upload-pps-limit 0
ip new-session-limit virtual-host limit 0
ip new-session-limit real-host limit 0
ip new-session-limit start-up limit 0
!
!
!
!
!
!
ip access-list standard 1
10 permit any
!
!
ip access-list standard 18
10 permit host 192.168.0.188 time-range any
!
!
control-plane
anti-arp-spoof scan 20
attack threshold 500
!
control-plane protocol
no acpp
!
control-plane manage
no port-filter
no arp-car
no acpp
!
control-plane data
no glean-car
no acpp
!
!
vwan mss 1360
url-filter-notice display You are forbidden to visit the website, please contact webmaster!
!
!
url-audit exact-filter
!
!
!
subscriber static name Default_Group parent /
subscriber static name without_auth_user parent /Default_Group password 7 02544a2310092b17101407330d2d5a0c3201
subscriber static name Vpn_Group parent /
subscriber allow without_auth_user privilege webauth
sam-online recycle 20
sam-offline recycle 20
network-group name Out_Server parent /
route-auto-choose cnc GigabitEthernet 0/4 218.56.16.61
route-auto-choose cnii GigabitEthernet 0/3 222.175.76.149
enable secret 5 $1$TTYY$rCywC62ywCsqp4As
enable service web-server
!
!
!
!
!
!
!
!
flow-control Gi0/3
channel-tree inbound
auto-pir enable interval 1 root-rate 90
!
channel-group root parent null cir 100000 pir 100000 pri 4 fifo
channel-default root
!
channel-tree outbound
auto-pir enable interval 1 root-rate 90
!
channel-group root parent null cir 100000 pir 100000 pri 4 fifo
channel-default root
!
!
!
flow-control Gi0/4
channel-tree inbound
auto-pir enable interval 1 root-rate 90
!
channel-group root parent null cir 100000 pir 100000 pri 4 fifo
channel-default root
!
channel-tree outbound
auto-pir enable interval 1 root-rate 90
!
channel-group root parent null cir 100000 pir 100000 pri 4 fifo
channel-default root
!
!
firewall log scan
!
firewall log syn-flood
!
firewall log icmp-flood
!
firewall log udp-flood
!
firewall enable
!
interface GigabitEthernet 0/0
ip nat inside
ip policy route-map Gi0/0
no ip unreachables
no ip redirects
no ip mask-reply
ip address 192.168.0.254 255.255.255.0
!
interface GigabitEthernet 0/3
duplex auto
speed auto
ip nat outside
ip address 222.175.76.150 255.255.255.252
reverse-path
nexthop 222.175.76.149
bandwidth 100000
!
interface GigabitEthernet 0/4
duplex auto
speed auto
ip nat outside
ip address 218.56.16.62 255.255.255.252
reverse-path
nexthop 218.56.16.61
bandwidth 100000
!
!
ip nat pool nat_pool prefix-length 24
address 222.175.76.150 222.175.76.150 match interface GigabitEthernet 0/3
address 218.56.16.62 218.56.16.62 match interface GigabitEthernet 0/4
!
ip nat inside source static tcp 192.168.0.222 2000 interface GigabitEthernet 0/3 2000 permit-inside
ip nat inside source list 1 pool nat_pool overload
!
!
!
!
!
!
!
ip route 0.0.0.0 0.0.0.0 GigabitEthernet 0/3 222.175.76.149
ip route 0.0.0.0 0.0.0.0 GigabitEthernet 0/4 218.56.16.61
!
!
ref parameter 50 200
line con 0
line vty 0 4
login
password admin
!
!
end
系统日志
*Nov 10 05:48:35: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 184.105.139.67
*Nov 10 03:00:49: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 204.42.253.130
*Nov 10 02:32:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 10 01:02:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 10 00:04:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 9 22:37:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 9 08:11:12: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet 0/0, changed state to up.
*Nov 9 08:11:12: %LINK-3-UPDOWN: Interface GigabitEthernet 0/0, changed state to up.
*Nov 9 08:09:16: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet 0/0, changed state to down.
*Nov 9 08:09:16: %LINK-3-UPDOWN: Interface GigabitEthernet 0/0, changed state to down.
*Nov 9 06:37:44: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 184.105.139.67
*Nov 9 06:03:24: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 184.105.139.67
*Nov 9 02:24:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 9 00:42:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 8 23:59:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 8 22:37:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 8 12:05:41: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 202.4.34.45
*Nov 8 11:01:44: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 202.4.34.45
*Nov 8 07:46:40: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 184.105.139.67
*Nov 8 06:15:01: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 91.208.115.34
*Nov 8 06:00:25: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 91.208.115.34
*Nov 8 05:23:57: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 184.105.139.67
*Nov 8 02:42:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 8 01:20:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 8 01:19:29: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 109.235.69.202
*Nov 8 00:18:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 7 22:37:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 7 18:49:43: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 134.147.203.115
*Nov 7 07:54:43: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 5.8.66.78
*Nov 7 07:38:47: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 5.8.66.78
*Nov 7 06:24:28: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 184.105.139.67
*Nov 7 05:38:38: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 184.105.139.67
*Nov 7 02:42:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 7 02:01:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 7 00:55:28: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 134.147.203.115
*Nov 7 00:12:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 6 22:37:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 6 19:57:19: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 91.208.115.34
*Nov 6 19:53:08: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 91.208.115.34
*Nov 6 18:30:42: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 185.94.111.1
*Nov 6 17:33:06: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 185.94.111.1
*Nov 6 07:04:00: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 184.105.139.67
*Nov 6 06:27:01: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 184.105.139.67
*Nov 6 02:31:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 6 01:52:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 6 00:28:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 5 22:37:16: %HTTP-5-UPDATE: Connect to server failed!
*Nov 5 13:32:14: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 185.94.111.1
*Nov 5 12:39:18: %SNMP-3-AUTHFAIL: Authentication failure for SNMP req from host 185.94.111.1
Log Buffer (Total 4096 Bytes): have written 4096, Overwritten 3895
Trap logging: level informational, 238 message lines logged,0 fail
Count log messages: disable
Sysname log messages: disable
Sequence-number log messages: disable
Timestamp log messages: datetime
Timestamp debug messages: datetime
Standard format: false
Buffer logging: level debugging, 238 messages logged
Monitor logging: level debugging, 0 messages logged
Console logging: level debugging, 238 messages loggedSyslog logging: enabled
漏洞证明:
修复方案:
改密码
版权声明:转载请注明来源 莫里@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-11-25 09:00
厂商回复:
漏洞Rank:4 (WooYun评价)
最新状态:
暂无



![`Y)DC4~S0R9B`T)}T5ZFP]F.jpg](http://wimg.zone.ci/upload/201511/101507532f960ed347e32510e73d29ac1bf079e8.jpg)