漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0153086
漏洞标题:微星中国官网某处SQL注入漏洞
相关厂商:微星
漏洞作者: 染血の雪
提交时间:2015-11-11 09:32
修复时间:2016-01-11 15:32
公开时间:2016-01-11 15:32
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-11: 细节已通知厂商并且等待厂商处理中
2015-11-23: 厂商已经确认,细节仅向厂商公开
2015-12-03: 细节向核心白帽子及相关领域专家公开
2015-12-13: 细节向普通白帽子公开
2015-12-23: 细节向实习白帽子公开
2016-01-11: 细节向公众公开
简要描述:
双11基友要买笔记本,问我什么牌子好。
详细说明:
url:
post:
payload:
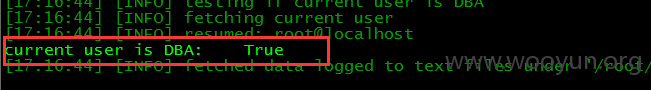
漏洞证明:
修复方案:
只要不忽略方法总是有的。
版权声明:转载请注明来源 染血の雪@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:9
确认时间:2015-11-23 11:35
厂商回复:
CNVD未复现所述情况,已经由CNVD通过网站公开联系方式向网站管理单位通报。
最新状态:
暂无



![`_T5@$XP{@@GZ2{]W1CC1`D.png](http://wimg.zone.ci/upload/201511/0917122132b3db47a7a5224683257ffd607fce5f.png)