漏洞概要
关注数(24)
关注此漏洞
漏洞标题:试客联盟网众用助手站某处sql注入涉及45W会员信息
提交时间:2015-10-15 16:58
修复时间:2015-10-20 17:00
公开时间:2015-10-20 17:00
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
Tags标签:
无
漏洞详情
披露状态:
2015-10-15: 细节已通知厂商并且等待厂商处理中
2015-10-20: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
众用助手——国内首家补贴类应用软件分发平台
众用助手基于一站网旗下试客联盟、众划算的试用营销的理念与350万会员,颠覆互联网APP传统的推广模式,开创APP体验营销推广模式。搭建起开发者与真实用户间的分发平台,为广大应用软件开发者提供精准的用户推广和体验营销服务,帮助开发者真正实现精准、有效的推广。
详细说明:
漏洞地址:
keword参数存在注入
漏洞证明:
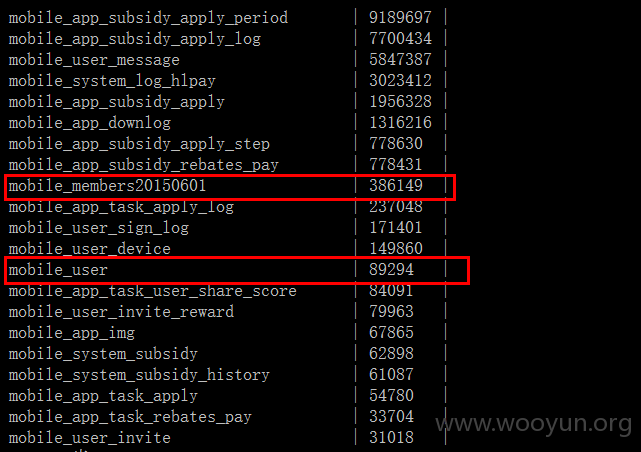
数据库:
45W+会员信息泄漏
修复方案:
版权声明:转载请注明来源 无名人@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-10-20 17:00
厂商回复:
漏洞Rank:15 (WooYun评价)
最新状态:
暂无



