注入点1:
测试
返回
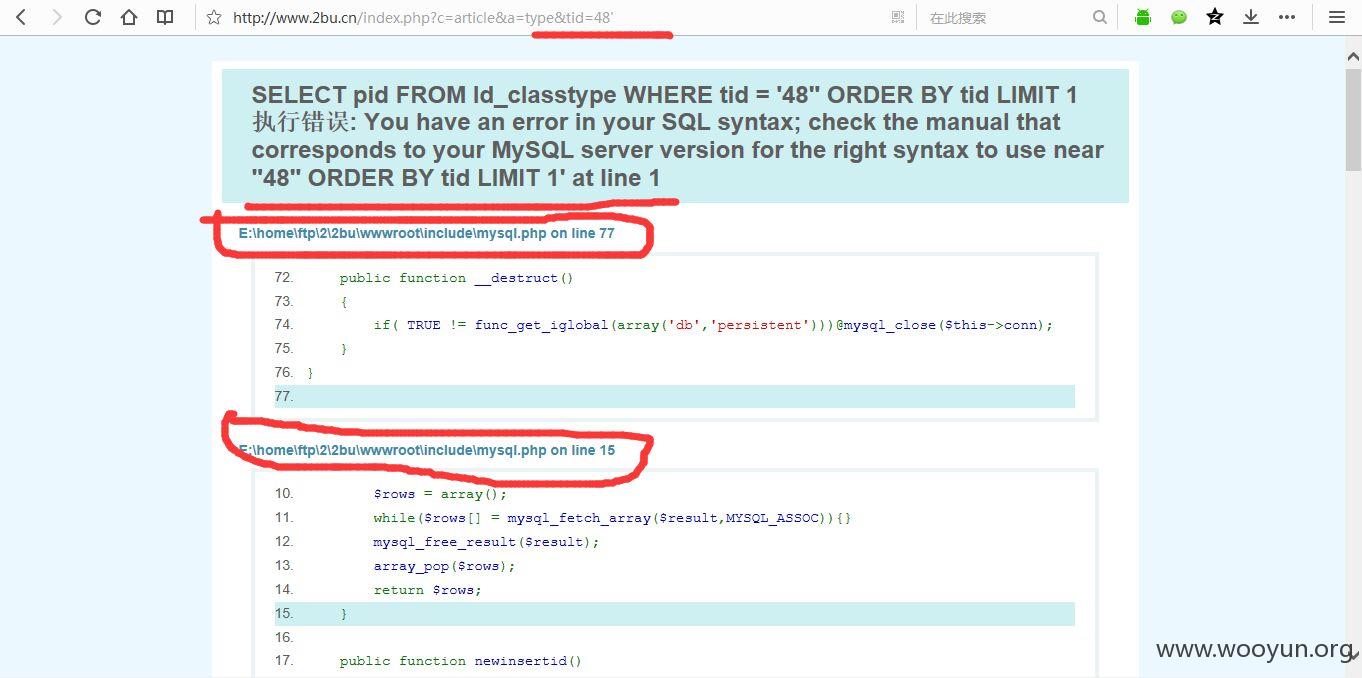
上sqlmap测试
后台地址
可通过获取的管理员帐号登楼后台,因MD5解密不了,因此并未进入后台。
注入点2:
tid存在注入已经测试
问题在于“问题咨询”处的“搜索答案”
测试搜索1'
返回
抓包
word存在注入
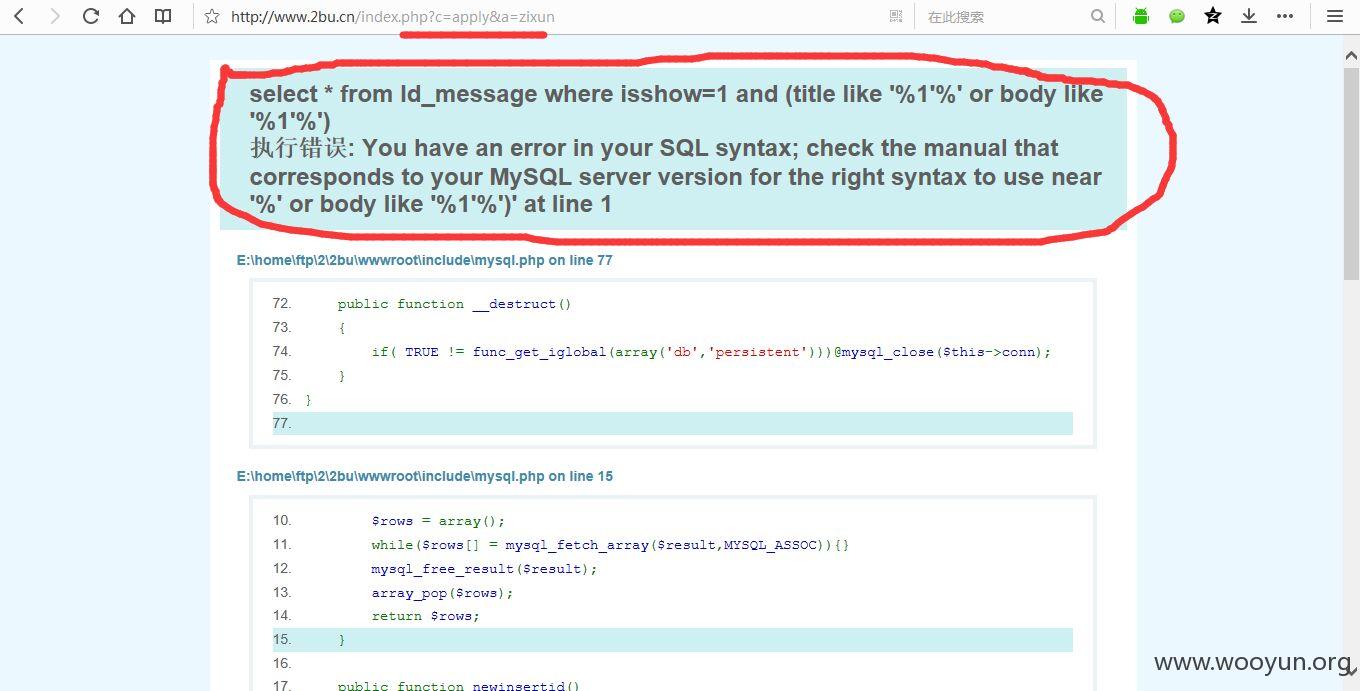
sqlmap直接测试
注入点3:
测试
很有意思的是,jd参数加了'返回错误,然后增加lx参数加'反而没有错误看到了,具体如何实现分析错误代码就知道了!~~~
五个参数均存在注入,分别是jd、lx、zb、nf、fl
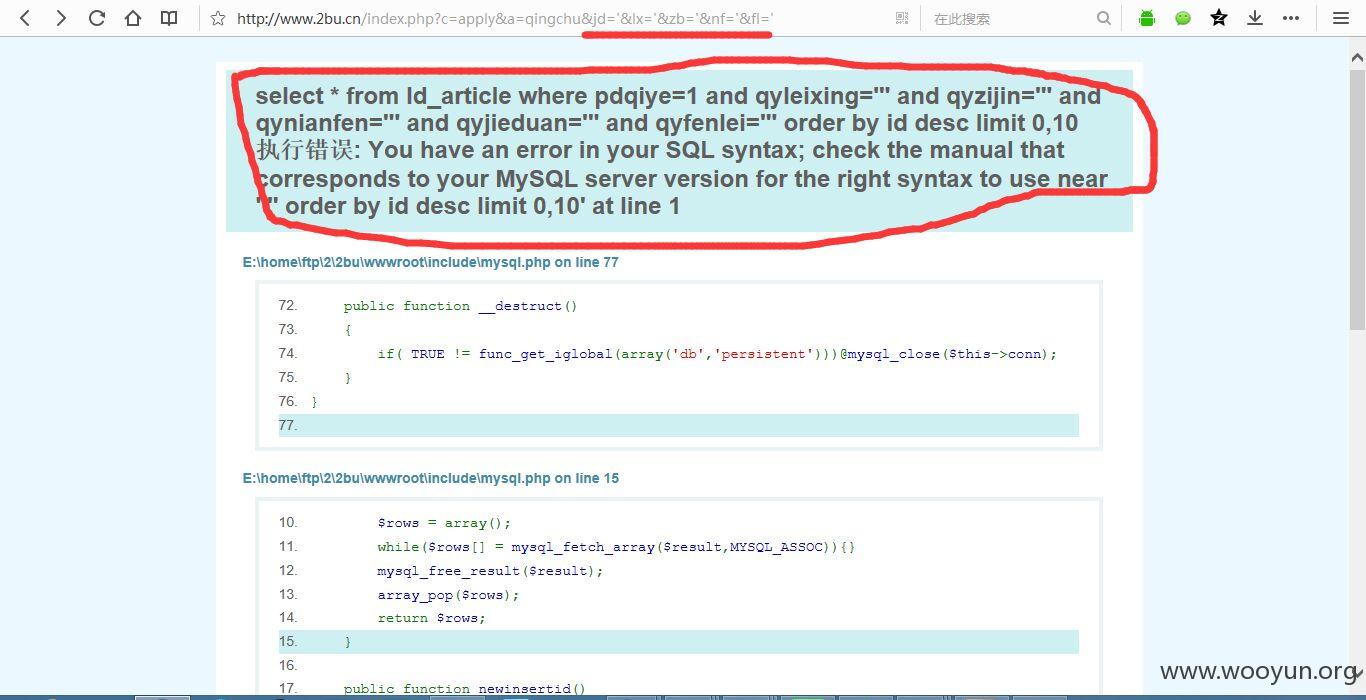
sqlmap测试之结果
注入点4:
账户名处输入:admin'
返回错误信息
抓包,获取POST数据
username参数存在注入
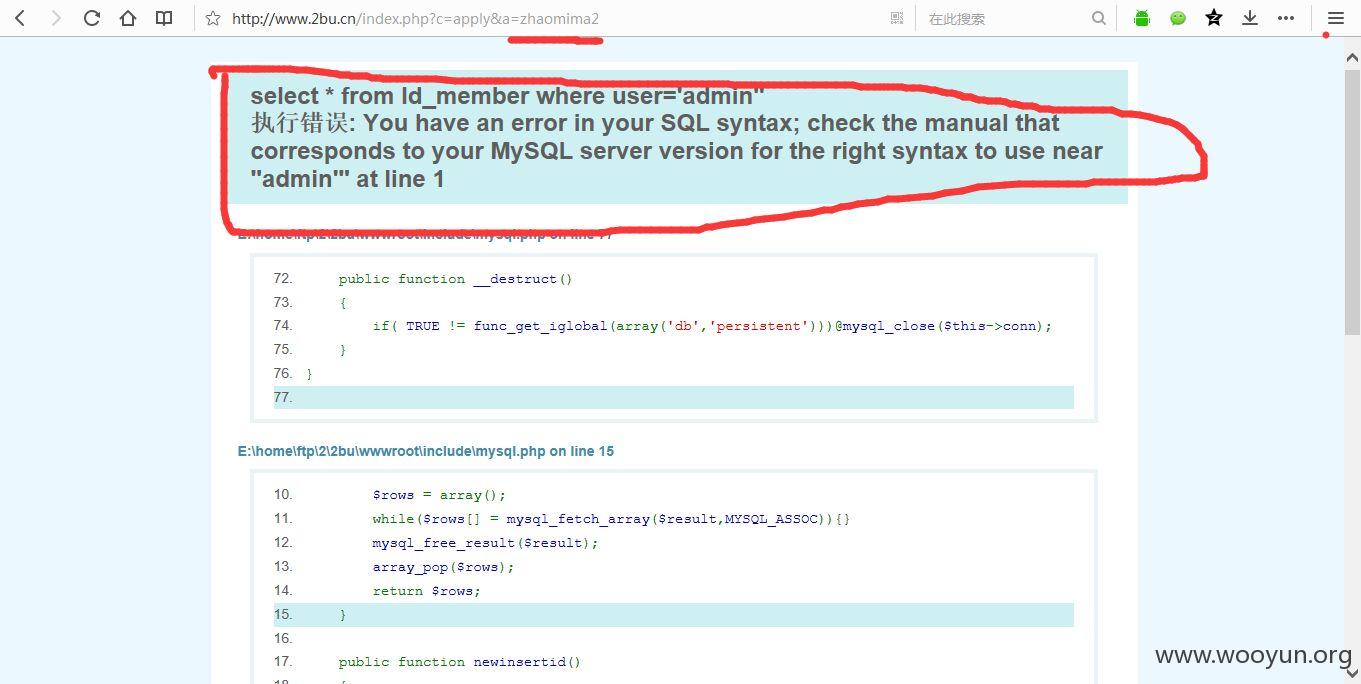
用sqlmap测试
5、验证不严导致可以获取用户信息:
这里,我们可以抓包,然后用大量用户进行测试,获取存在的用户,比如:boxerking(从上面获取的用户信息测试,就不用burpsuite跑用户表了)
输入正确的用户名后
我们随便输入一些数字,提示邮箱不正确,此时看看抓包可以发现返回的数据信息为
那么我们利用抓取到的邮箱,就可以更改用户密码了!~~~






